- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: ASA Firewall - OSPF Routing between different VLAN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ASA Firewall - OSPF Routing between different VLAN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-18-2019 08:31 PM
Hi all,
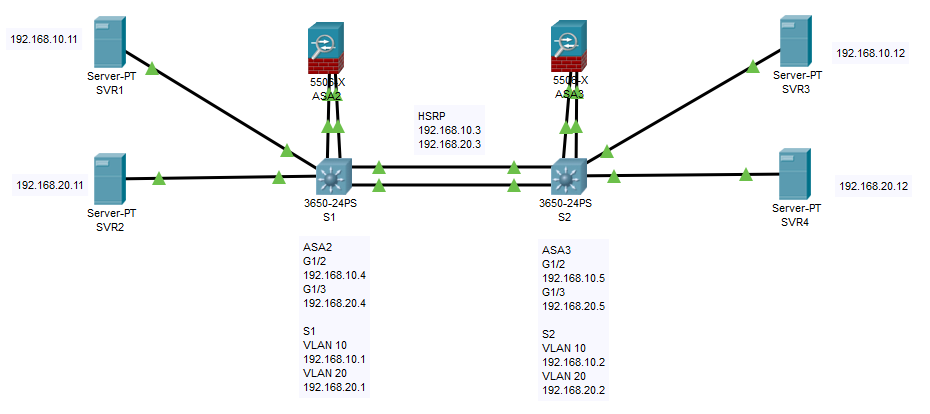
Based on the diagram below, I would like to achieve the following,
- When SVR1 (VLAN10) need to communicate with SVR2 (VLAN20), it will have to go through S1 and ASA2
- When SVR3 (VLAN10) need to communicate with SVR3 (VLAN20), it will have to go through S2 and ASA3
Can this 2 be achieved? If yes, how could I configure to achieve this?
My current configuration is in the attachment.
Please advise
Thank You
Peter
- Labels:
-
Routing Protocols
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-19-2019 02:36 AM - edited 06-19-2019 02:42 AM
Hello Peter,
with your current configuration traffic between Vlan 10 and Vlan 20 never needs to go via either ASA2 or ASA3.
From the point of view of Switches S1 and S2 both Vlans are in the same routing table and they simply perform inter Vlan routing.
Using OSPF does not provide alone a way to go through the firewalls as a connected route is always preferred over an OSPF route for the lower admin distance.
To have traffic to go via the firewalls you should :
introduce VRFs on the switches S1 and S2 so that Vlan 10 will belong to vrf RED and Vlan 20 to vrf BLUE.
You will need additional vlans for switches to firewall communications in each VRF.
For example
vlan 912 will provide connectivity between S1 and ASA2 in VRF RED
vlan 913 will provide connectivity between S1 and ASA3 in VRF RED
vlan 952 will provide connectivity between S1 and ASA2 in VRF BLUE
vlan 953 will provide connectivity between S1 and ASA3 in VRF BLUE
The same for S2 to ASA2 and ASA3:
vlan 922 will provide connectivity between S2 and ASA2 in VRF RED
vlan 923 will provide connectivity between S2 and ASA3 in VRF RED
vlan 962 will provide connectivity between S2 and ASA2 in VRF BLUE
vlan 963 will provide connectivity between S2 and ASA3 in VRF BLUE
You can use appropriate /30 IP subnets on each vlan 9xy and you can run OSPF in the vrf RED/BLUE over them.
However, all this does only provide a way for traffic to be sent and received via one of the firewalls.
To achieve the most specific achievements that you would like to see in your network you need also policy based routing applied inbound (on rx side ) on SVI interface vlan 10 ( mapped to VRF RED) and on SVI vlan 20 (mapped to VRF BLUE).
So for example to be able to send traffic from specific server 192.168.10.10 to server 192.168.20.10 via ASA2 you need the following:
On S1 and S2 both you need to configure PBR using the specific next-hops in vlan 912 and vlan 922 respectively.
access-list 111 permit ip host 192.168.10.10 host 192.168.20.10
access-list 115 permit ip host 192.168.10.11 host 192.168.20.11
route-map PBR-S1-VL10 permit 10
match address 111
set ip next-hop <ASA2-IP-vlan912>
route-map PBR-S1-VL10 permit 20
match address 115
set ip next-hop <ASA3-IP-vlan913>
To be noted you need to configure PBR on both S1 and S2 because you are running HSRP in each Vlan and you need to be sure that whatever is the current HSRP Active router in Vlan 10 the PBR actions are performed.
So on switch S2 you will have a similar setup just using different IP next-hops in PBR set commands
S2:
access-list 111 permit ip host 192.168.10.10 host 192.168.20.10
access-list 115 permit ip host 192.168.10.11 host 192.168.20.11
route-map PBR-S2-VL10 permit 10
match address 111
set ip next-hop <ASA2-IP-vlan922>
route-map PBR-S2-VL10 permit 20
match address 115
set ip next-hop <ASA3-IP-vlan923>
To be noted being ASA2 and ASA3 indipendent stateful firewalls they must see both directions of a flow to allow it to pass (you need to avoid asymmetric routing).
So PBR needs to be configured on S1 and S2 also on Vlan 20 in vrf BLUE using appropriate ACLs and route-maps.
access-list 121 permit ip host 192.168.20.10 host 192.168.10.10
access-list 125 permit ip host 192.168.20.11 host 192.168.10.11
route-map PBR-S1-VL20 permit 10
match address 121
set ip next-hop <ASA2-ip-Vl952>
route-map PBR-S1-VL20 permit 20
match address 125
set ip next-hop <ASA3-IP-VL953>
you apply the appropriate route-map with
int vlan 10
ip policy route-map PBR-S1-VL10
int vlan 20
ip policy route-map PBR-S1-VL20
For supporting VRFs you may need to change the SDM template on the C3560 switches.
It is really important to provide symmetric paths for all traffic flows.
All traffic not matched by PBR route-maps is routed by destination. (key point).
So the best way is to tune OSPF costs so that ASA2 is the primary path both directions on the appropriate vlan 9x3 you can use ip ospf cost 100 on S1, S2 and ASA3 devices.
Hope to help
Giuseppe
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-19-2019 06:27 PM
Hi Giuseppe,
Thank you for your reply. Can the VRF and the other steps you posted previous be done on Packet Tracer?
Is there any easier way to fuilfill this requirement?
Please advise
Thank You
Peter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-20-2019 01:58 AM - edited 06-20-2019 02:04 AM
Hello Peter,
I don't know if packet tracer supports VRFs the real devices should with the appropriate SDM template (use show sdm prefer to see current settings if you need to change the SDM template you need to reload the switch before the change is effective as the SDM template changes the use of the TCAM table that is the key component of hardware based CEF forwarding and routing).
VRFs are needed until both switches S1 and S2 are connected at the same time to Vlan 10 AND Vlan 20.
Without the VRFs with S1, S2 connected to both Vlan10, Vlan 20 traffic will never go to the firewalls.
You could try to use only PBR on S1 and S2 as explained in my post with a change in setting the IP next-hop per your network diagram, however, you would need PBR deployed on both S1 and S2 on both Vlans (for the HSRP ) as firewalls need to see both directions of the flow.
All traffic flows not redirected by PBR will bypass the firewalls and will go directly via S1 or S2 to the other Vlan.
I don't know if this is an acceptable solution for your needs.
If you need to put the firewalls in the path for all traffic flows I would go to use VRFs or you need to remove vlan 20 from S1 and vlan 10 from S2 (but this will break redundancy provided by HSRP).
Edit:
Here I mean removing the L3 configuration of Vlan20 on S1 with
S1:
interface vlan 20
shutdown
S2:
int vlan 10
shutdown
Vlan 10 and vlan 20 are still both needed at OSI layer 2 as hosts are connected to both switches.
Hope to help
Giuseppe
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-23-2019 09:58 PM
Hi Giuseppe,
I have tested and VRF is not supported in the Packet Tracer. However, I have drafted the command as according to your guide. I have attached the draft command in the attachment. Kindly let me know if there is anything i missed out.
And how do I adjust the OSPF cost for S1, S2, ASA2 and ASA3 device?
Please advise
Thank You
Peter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-23-2019 10:59 PM - edited 06-23-2019 11:00 PM
Hello Peter,
I have reviewed your configuration templates.
The following notes apply:
a) VRF configuration
I think you need to set the route-distinguisher when you create a vrf
ip vrf RED
rd 65000:1
exit
ip vrf BLUE
rd 65000:2
exit
Be aware that a more modern syntax for vrf exists that is multiprotocol IPv4/IPv6.
In this newer syntax the commands become
vrf definition RED
address-family ipv4
rd 65000:1
vrf definition BLUE
address-family ipv4
rd 65000:2
When you associate an interface to a VRF
old syntax
int vlan 912
ip vrf forwarding RED
ip address ...
new syntax
int vlan 912
vrf forwarding RED
ip address ...
B) Also SVI vlan 10 ans SVI vlan 20 have to be associated to respective VRFs
please note that when you associate an interface to a VRF the IP address is removed and you need to retype it.
C) OSPF
OSPF cost tuning in the paths S1 - ASA3 - S2 can be performed by using the command
ip ospf cost 100
under appropriate interfaces S1 vlan 913, S1 vlan 953 and S2 vlan 923 and vlan 963. Also on ASA3 you can use the same command under the corresponding interfaces.
The most important aspect of the OSPF configuration is that you need two OSPF processes on the S1, S2 switches one associated to vrf RED and one associated to VRF BLUE.
router ospf 10 vrf RED
ospf router-id 1.1.1.1
! appropriate network commands for Vlans 10, 912, 913 in area 0
! the following command is needed to accept LSAs generated by other VRF aware OSPF router
capability vrf-lite
router ospf 20 vrf 20
ospf router-id 1.1.1.2
network commands for Vlans 20, 952, 953 in area 0
! the following command is needed to accept LSAs generated by other VRF aware OSPF router
capability vrf-lite
The capability vrf-lite disables the check of the DN bit that is set on LSAs generated by a PE node.
In your case this command may be not needed, but if you see that in VRF RED you are not learning the Vlan 20 IP prefix this trick is needed.
Equivalent commands have to be perfomed on S2 switch:
router ospf 10 vrf RED
ospf router-id 2.2.2.1
! appropriate network commands for Vlans 10, 922, 923 in area 0
! the following command is needed to accept LSAs generated by other VRF aware OSPF router
capability vrf-lite
router ospf 20 vrf 20
ospf router-id 2.2.2.2
network commands for Vlans 20, 962, 963 in area 0
! the following command is needed to accept LSAs generated by other VRF aware OSPF router
capability vrf-lite
Note : also for OSPF support in VRF there is a newer feature / syntax. I have reported here the old syntax using a dedicated OSPF process for each VRF.
Hope to help
Giuseppe
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide