- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: ASA not Able to Ping Routed Network
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ASA not Able to Ping Routed Network
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-24-2023 09:36 AM
Hey Guys,
I've been banging my head against the wall for a few days, so I figured I'd ask the experts.
I currently have an issue where I can't connect to subnets on the other side of a L3 switch it is a SG300 updated to the latest firmware. From the switch I can ping the firewall and the inside networks but for the life of me I can't figure out how to get a connection from the ASA to the networks. Here are my configs, is there something I am missing?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-24-2023 09:42 AM
only do
inspection icmp under the global-policy
that what you need for icmp to pass through
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-24-2023 10:14 AM - edited 02-24-2023 10:23 AM
That didn't work good catch, I would have kicked myself if it did LOL. Thank you for the quick response.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-24-2023 03:08 PM
OK
can you use packet tracer and share result here ??
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2023 12:06 PM
Phase: 1
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f8d2a1bf960, priority=1, domain=permit, deny=false
hits=5, user_data=0x0, cs_id=0x0, l3_type=0x8
src mac=0000.0000.0000, mask=0000.0000.0000
dst mac=0000.0000.0000, mask=0100.0000.0000
input_ifc=TRANS_DMZ_INT, output_ifc=any
Phase: 2
Type: ROUTE-LOOKUP
Subtype: No ECMP load balancing
Result: ALLOW
Config:
Additional Information:
Destination is locally connected. No ECMP load balancing.
Found next-hop 192.168.44.2 using egress ifc TRANS_DMZ_INT
Phase: 3
Type: ACCESS-LIST
Subtype:
Result: DROP
Config:
Implicit Rule
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f8d29a92320, priority=501, domain=permit, deny=true
hits=1, user_data=0x7, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=192.168.44.1, mask=255.255.255.255, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=TRANS_DMZ_INT, output_ifc=any
Result:
input-interface: TRANS_DMZ_INT
input-status: up
input-line-status: up
Action: drop
Drop-reason: (acl-drop) Flow is denied by configured rule, Drop-location: frame 0x000055556562d33f flow (NA)/NA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2023 01:52 PM
Can I see the packet tracer you use here?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
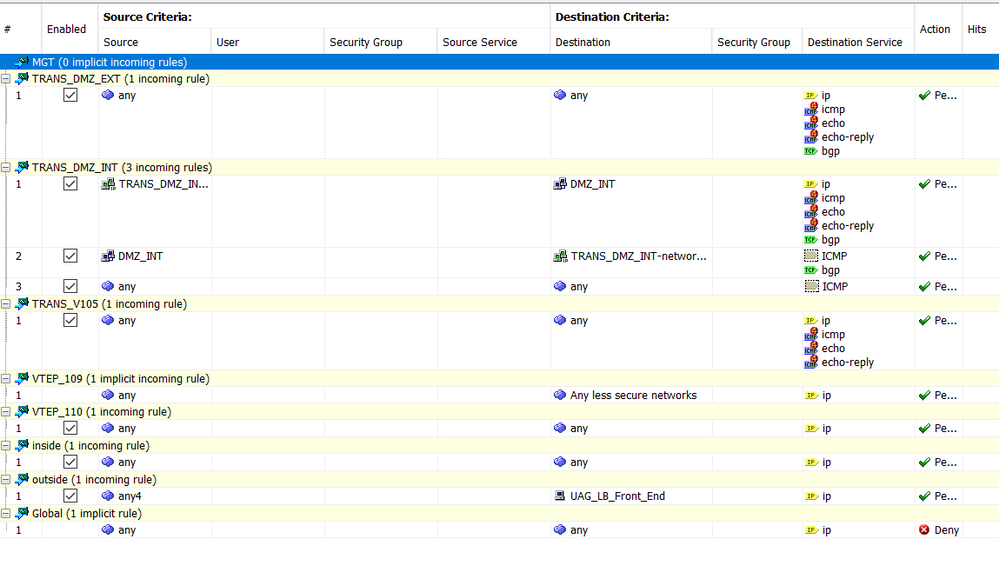
02-25-2023 12:30 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2023 01:42 AM - edited 02-25-2023 01:43 AM
Hello
To allow traffic in/out of the same interface or between interface with the same security level you need to allow it this manually.
same-security-traffic inter-interface
nat (inside,outside) after-auto source dynamic any interface
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2023 11:54 AM
Thanks for the response. Still can't get through.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-26-2023 01:28 AM
Hello
Phase: 3
Type: ACCESS-LIST
Subtype:
Result: DROP
Apply the following and test:
policy-map global_policy
class inspection_default
inspect icmp
access-group TRANS_DMZ_INT_access_in out interface TRANS_DMZ_INT
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-26-2023 09:30 AM
Didn't work.
packet-tracer input TRANS_DMZ_INT icmp 10.4.44.1 8 0 192.168.44.1 detailed
Phase: 1
Type: ROUTE-LOOKUP
Subtype: No ECMP load balancing
Result: ALLOW
Config:
Additional Information:
Destination is locally connected. No ECMP load balancing.
Found next-hop 192.168.44.1 using egress ifc identity
Phase: 2
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f8d2967b880, priority=120, domain=permit, deny=false
hits=36, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=1
src ip/id=0.0.0.0, mask=0.0.0.0, icmp-type=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, icmp-code=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=TRANS_DMZ_INT, output_ifc=identity
Phase: 3
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f8d2904f510, priority=0, domain=nat-per-session, deny=true
hits=88743, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=any, output_ifc=any
Phase: 4
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f8d2967dde0, priority=0, domain=inspect-ip-options, deny=true
hits=6959, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=TRANS_DMZ_INT, output_ifc=any
Phase: 5
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f8d2967b880, priority=120, domain=permit, deny=false
hits=36, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=1
src ip/id=0.0.0.0, mask=0.0.0.0, icmp-type=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, icmp-code=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=TRANS_DMZ_INT, output_ifc=identity
Phase: 6
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f8d2904f510, priority=0, domain=nat-per-session, deny=true
hits=88744, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=any, output_ifc=any
Phase: 7
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f8d2967dde0, priority=0, domain=inspect-ip-options, deny=true
hits=6959, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=TRANS_DMZ_INT, output_ifc=any
Phase: 8
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f8d2967b880, priority=120, domain=permit, deny=false
hits=36, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=1
src ip/id=0.0.0.0, mask=0.0.0.0, icmp-type=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, icmp-code=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=TRANS_DMZ_INT, output_ifc=identity
Phase: 9
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f8d2904f510, priority=0, domain=nat-per-session, deny=true
hits=88744, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=any, output_ifc=any
Phase: 10
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f8d2967dde0, priority=0, domain=inspect-ip-options, deny=true
hits=6960, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=TRANS_DMZ_INT, output_ifc=any
Phase: 11
Type: CLUSTER-REDIRECT
Subtype: cluster-redirect
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f8d29a92210, priority=208, domain=cluster-redirect, deny=false
hits=1, user_data=0x0, cs_id=0x0, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=TRANS_DMZ_INT, output_ifc=identity
Phase: 12
Type: INSPECT
Subtype: np-inspect
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f8d2967c640, priority=66, domain=inspect-icmp, deny=false
hits=1, user_data=0x7f8d293de1a0, cs_id=0x0, use_real_addr, flags=0x0, protocol=1
src ip/id=0.0.0.0, mask=0.0.0.0, icmp-type=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, icmp-code=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=TRANS_DMZ_INT, output_ifc=identity
Phase: 13
Type: INSPECT
Subtype: np-inspect
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f8d2967d5f0, priority=66, domain=inspect-icmp-error, deny=false
hits=1, user_data=0x7f8d2a215da0, cs_id=0x0, use_real_addr, flags=0x0, protocol=1
src ip/id=0.0.0.0, mask=0.0.0.0, icmp-type=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, icmp-code=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=TRANS_DMZ_INT, output_ifc=any
Phase: 14
Type: FLOW-CREATION
Subtype:
Result: ALLOW
Config:
Additional Information:
New flow created with id 93117, packet dispatched to next module
Module information for forward flow ...
snp_fp_inspect_ip_options
snp_fp_inspect_icmp
snp_fp_adjacency
snp_fp_fragment
snp_fp_tracer_drop
snp_ifc_stat
Module information for reverse flow ...
snp_fp_inspect_ip_options
snp_fp_inspect_icmp
snp_fp_adjacency
snp_fp_fragment
snp_fp_tracer_drop
snp_ifc_stat
Phase: 15
Type: NEXTHOP-LOOKUP-FROM-OUTPUT-ROUTE-LOOKUP
Subtype: Lookup Nexthop on interface
Result: ALLOW
Config:
Additional Information:
Found next-hop 0.0.0.0 using egress ifc identity
Phase: 16
Type: ADJACENCY-LOOKUP
Subtype: Resolve Nexthop IP address to MAC
Result: ALLOW
Config:
Additional Information:
Found adjacency entry for Next-hop 0.0.0.0 on interface identity
Adjacency :Active
MAC address 0000.0000.0000 hits 48743 reference 1
Result:
input-interface: TRANS_DMZ_INT
input-status: up
input-line-status: up
output-interface: NP Identity Ifc
Action: allow
packet-tracer input TRANS_DMZ_INT icmp 192.168.44.2 8 0 10.4.44.1 detailed
Phase: 1
Type: INPUT-ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
Found next-hop 192.168.44.2 using egress ifc TRANS_DMZ_INT
Phase: 2
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group DMZ_INT_444_access_in in interface TRANS_DMZ_INT
access-list DMZ_INT_444_access_in extended permit object-group DM_INLINE_SERVICE_2 192.168.44.0 255.255.255.0 object DMZ_INT
object-group service DM_INLINE_SERVICE_2
service-object ip
service-object icmp
service-object icmp echo
service-object icmp echo-reply
service-object tcp destination eq bgp
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f8d2a2e7ea0, priority=13, domain=permit, deny=false
hits=1, user_data=0x7f8d12714280, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=192.168.44.0, mask=255.255.255.0, port=0, tag=any
dst ip/id=10.4.44.0, mask=255.255.255.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=TRANS_DMZ_INT, output_ifc=any
Phase: 3
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f8d2904f510, priority=0, domain=nat-per-session, deny=true
hits=88939, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=any, output_ifc=any
Phase: 4
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f8d2967dde0, priority=0, domain=inspect-ip-options, deny=true
hits=6984, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=TRANS_DMZ_INT, output_ifc=any
Phase: 5
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group DMZ_INT_444_access_in in interface TRANS_DMZ_INT
access-list DMZ_INT_444_access_in extended permit object-group DM_INLINE_SERVICE_2 192.168.44.0 255.255.255.0 object DMZ_INT
object-group service DM_INLINE_SERVICE_2
service-object ip
service-object icmp
service-object icmp echo
service-object icmp echo-reply
service-object tcp destination eq bgp
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f8d2a2e7ea0, priority=13, domain=permit, deny=false
hits=1, user_data=0x7f8d12714280, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=192.168.44.0, mask=255.255.255.0, port=0, tag=any
dst ip/id=10.4.44.0, mask=255.255.255.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=TRANS_DMZ_INT, output_ifc=any
Phase: 6
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f8d2904f510, priority=0, domain=nat-per-session, deny=true
hits=88940, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=any, output_ifc=any
Phase: 7
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f8d2967dde0, priority=0, domain=inspect-ip-options, deny=true
hits=6984, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=TRANS_DMZ_INT, output_ifc=any
Phase: 8
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group DMZ_INT_444_access_in in interface TRANS_DMZ_INT
access-list DMZ_INT_444_access_in extended permit object-group DM_INLINE_SERVICE_2 192.168.44.0 255.255.255.0 object DMZ_INT
object-group service DM_INLINE_SERVICE_2
service-object ip
service-object icmp
service-object icmp echo
service-object icmp echo-reply
service-object tcp destination eq bgp
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f8d2a2e7ea0, priority=13, domain=permit, deny=false
hits=1, user_data=0x7f8d12714280, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=192.168.44.0, mask=255.255.255.0, port=0, tag=any
dst ip/id=10.4.44.0, mask=255.255.255.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=TRANS_DMZ_INT, output_ifc=any
Phase: 9
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f8d2904f510, priority=0, domain=nat-per-session, deny=true
hits=88940, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=any, output_ifc=any
Phase: 10
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f8d2967dde0, priority=0, domain=inspect-ip-options, deny=true
hits=6985, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=TRANS_DMZ_INT, output_ifc=any
Phase: 11
Type: QOS
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f8d29441510, priority=70, domain=qos-per-class, deny=false
hits=155478, user_data=0x7f8d294438f0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=any, output_ifc=any
Phase: 12
Type: INSPECT
Subtype: np-inspect
Result: ALLOW
Config:
class-map inspection_default
match default-inspection-traffic
policy-map global_policy
class inspection_default
inspect icmp
service-policy global_policy global
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f8d298ea190, priority=70, domain=inspect-icmp, deny=false
hits=1, user_data=0x7f8d2963abf0, cs_id=0x0, use_real_addr, flags=0x0, protocol=1
src ip/id=0.0.0.0, mask=0.0.0.0, icmp-type=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, icmp-code=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=TRANS_DMZ_INT, output_ifc=any
Phase: 13
Type: INSPECT
Subtype: np-inspect
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f8d2967d5f0, priority=66, domain=inspect-icmp-error, deny=false
hits=2, user_data=0x7f8d2a215da0, cs_id=0x0, use_real_addr, flags=0x0, protocol=1
src ip/id=0.0.0.0, mask=0.0.0.0, icmp-type=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, icmp-code=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=TRANS_DMZ_INT, output_ifc=any
Phase: 14
Type: QOS
Subtype:
Result: ALLOW
Config:
Additional Information:
Reverse Flow based lookup yields rule:
in id=0x7f8d29441510, priority=70, domain=qos-per-class, deny=false
hits=155479, user_data=0x7f8d294438f0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=any, output_ifc=any
Phase: 15
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Reverse Flow based lookup yields rule:
in id=0x7f8d2904f510, priority=0, domain=nat-per-session, deny=true
hits=88941, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=any, output_ifc=any
Phase: 16
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Reverse Flow based lookup yields rule:
in id=0x7f8d2967dde0, priority=0, domain=inspect-ip-options, deny=true
hits=6986, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=TRANS_DMZ_INT, output_ifc=any
Phase: 17
Type: FLOW-CREATION
Subtype:
Result: ALLOW
Config:
Additional Information:
New flow created with id 93333, packet dispatched to next module
Module information for forward flow ...
snp_fp_inspect_ip_options
snp_fp_inspect_icmp
snp_fp_adjacency
snp_fp_fragment
snp_fp_tracer_drop
snp_ifc_stat
Module information for reverse flow ...
snp_fp_inspect_ip_options
snp_fp_inspect_icmp
snp_fp_adjacency
snp_fp_fragment
snp_fp_tracer_drop
snp_ifc_stat
Phase: 18
Type: INPUT-ROUTE-LOOKUP-FROM-OUTPUT-ROUTE-LOOKUP
Subtype: Resolve Preferred Egress interface
Result: ALLOW
Config:
Additional Information:
Found next-hop 192.168.44.2 using egress ifc TRANS_DMZ_INT
Phase: 19
Type: ADJACENCY-LOOKUP
Subtype: Resolve Nexthop IP address to MAC
Result: ALLOW
Config:
Additional Information:
Found adjacency entry for Next-hop 192.168.44.2 on interface TRANS_DMZ_INT
Adjacency :Active
MAC address 0050.568b.4aac hits 18 reference 1
Result:
input-interface: TRANS_DMZ_INT
input-status: up
input-line-status: up
output-interface: TRANS_DMZ_INT
output-status: up
output-line-status: up
Action: allow
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-26-2023 11:14 AM
Hello
192.168.44.1 8 0 10.4.44.1 - failed
10.4.44.1 8 0 192.168.44.1 - works
suggest a you need a reverse acl to accommodate the above
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-26-2023 08:53 PM
That didn't work, I appreciate your time. This is a green field deployment I have no issue blowing out the config. If you have any configuration ideas that you would suggest I am all ears. Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-26-2023 10:22 AM
packet-tracer input TRANS_DMZ_INT icmp 192.168.44.1 8 0 10.4.44.1 detailed
Phase: 1
Type: INPUT-ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
Found next-hop 192.168.44.2 using egress ifc TRANS_DMZ_INT
Phase: 2
Type: ACCESS-LIST
Subtype:
Result: DROP
Config:
Implicit Rule
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f8d29a92320, priority=501, domain=permit, deny=true
hits=6, user_data=0x7, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=192.168.44.1, mask=255.255.255.255, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=TRANS_DMZ_INT, output_ifc=any
Result:
input-interface: TRANS_DMZ_INT
input-status: up
input-line-status: up
output-interface: TRANS_DMZ_INT
output-status: up
output-line-status: up
Action: drop
Drop-reason: (acl-drop) Flow is denied by configured rule, Drop-location: frame 0x000055556562d33f flow (NA)/NA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-27-2023 01:59 AM
packet-tracer input TRANS_DMZ_INT icmp 192.168.44.1 8 0 10.4.44.1 detailed <<-
are you use IP of interface ?? you must not use IP of interface of ASA
change the IP and send to me the packet tracer again
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide