- Cisco Community
- Technology and Support
- Networking
- Routing
- BGP Multi-homing: need to make my router a Transit AS
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2011 11:45 AM - edited 03-04-2019 01:09 PM
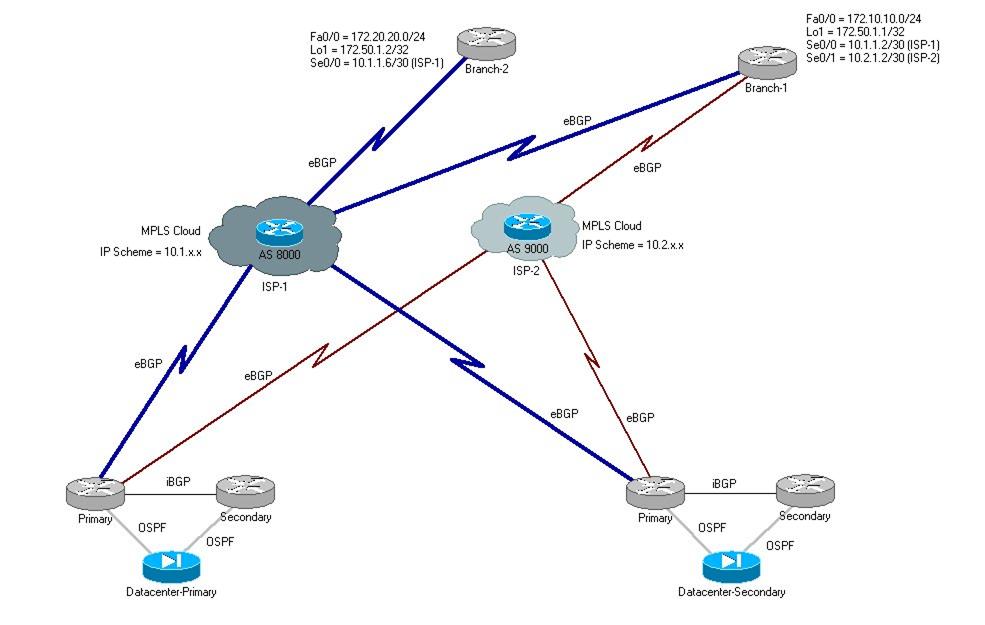
My organization had links to remote branches through one ISP. For redundancy we are going for a second ISP at remote branches. This will be a backup connection.
The thing is that - I don't want to complicate branch end BGP configuration by putting local_pref or pre-pending. I want the branch end to have simple config so that my L1 engineers do not get overwhelmed.
For this reason, I have to do all the manipulation at the Datacenter side. The topology is attached.
Present config are as:
DC1: AS 65501
DC2: AS 65502
Spokes: AS 65503
ISP-1: AS 8000
ISP-2: AS 9000
<Datacenter-1/Primary>
router bgp 65501
neighbor ISP-1 remote-as 8000
neighbor ISP-1 filter-list 1 out
neighbor ISP-2 remote-as 9000
neighbor ISP-2 filter-list 1 out
neighbor ISP-2 prefix-list ISP2-OUT out
network <...>
ip as-path access-list 1 permit ^$
Branch config is pretty basic.
<Branch-1>
router bgp 65503
neighbor ISP-1 remote-as 8000
neighbor ISP-1 filter-list 1 out
neighbor ISP-2 remote-as 9000
neighbor ISP-2 filter-list 1 out
network <....>
ip as-path access-list 1 permit ^$
<Branch-2>
router bgp 65503
neighbor ISP-1 remote-as 8000
neighbor ISP-1 filter-list 1 out
network <....>
ip as-path access-list 1 permit ^$
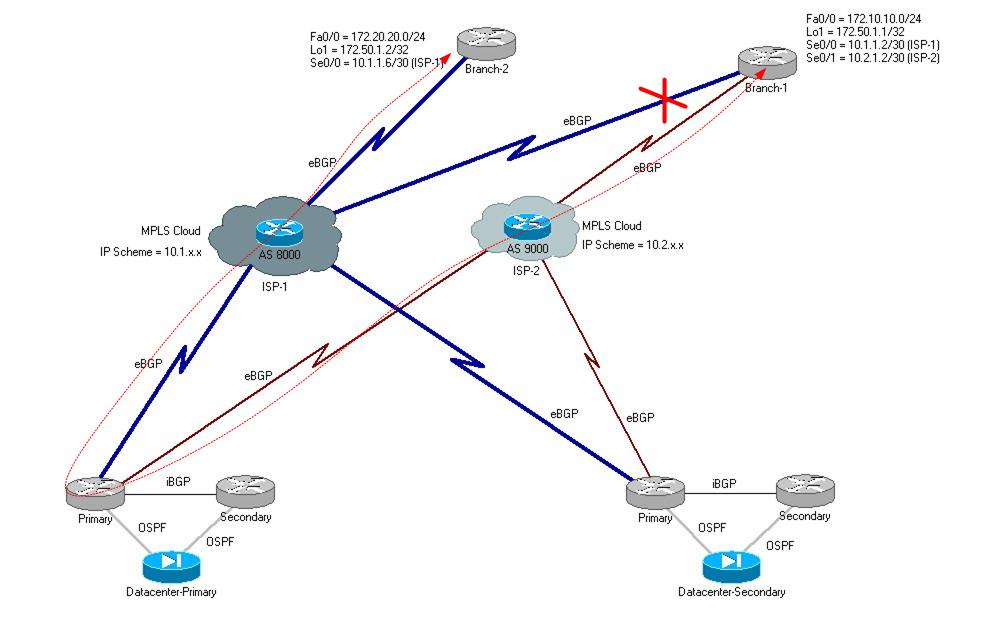
With the current setup the spoke branches are able to reach Datacenter and access the servers. However, inter-branch communication fails if one branch is running on ISP-1 and other on ISP-2 (as depicted in second image).
So, according to my current idea
- configure ISP-1 at DC1 with higher local_pref on inbound traffic
- configure ISP-2 at DC1 with longer pre-pending on outbound
However, still the inter-branch communication is not working. Do I have to modify the as-path ACL?
for ISP-1,
ip as-path access-list 1 permit _9000_
ip as-path access-list 1 permit ^$
for ISP-2,
ip as-path access-list 2 permit _8000_
ip as-path access-list 2 permit ^$
Will this work?
PS: we have a very small allowed prefix limit with ISP-2, hence, we are filtering prefixes at DC.
Solved! Go to Solution.
- Labels:
-
Routing Protocols
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2011 12:24 PM
Hello,
Modifying the as-path access lists on your datacenter location will be necessary. Your suggested changes should be okay. I assume that you do not receive the entire BGP table but rather only the routes in your VPN and thus you are not in the danger of becoming a real transit AS between your ISPs.
However, I see a possible problem with both branches having the same AS and hence not accepting the routes from each other (the basic BGP loop prevention algorithm).
If this is confirmed then there are two solutions to this:
- Ask your ISP 1 and ISP 2 to remove the private AS numbers when they advertise the networks to your primary site
- Or use the neighbor allowas-in command on branch routers to accept routes with the same AS in their AS_PATH list
Best regards,
Peter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2011 12:24 PM
Hello,
Modifying the as-path access lists on your datacenter location will be necessary. Your suggested changes should be okay. I assume that you do not receive the entire BGP table but rather only the routes in your VPN and thus you are not in the danger of becoming a real transit AS between your ISPs.
However, I see a possible problem with both branches having the same AS and hence not accepting the routes from each other (the basic BGP loop prevention algorithm).
If this is confirmed then there are two solutions to this:
- Ask your ISP 1 and ISP 2 to remove the private AS numbers when they advertise the networks to your primary site
- Or use the neighbor allowas-in command on branch routers to accept routes with the same AS in their AS_PATH list
Best regards,
Peter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2011 02:03 PM
Hi Peter,
IMHO, both providers would need to remove private AS numbers when advertising the prefixes to branches, too?
Otherwise when both branches are peering to the same provider via eBGP under normal conditions, they still would not be able to reach each other?
Neighbor allowas-in on branch routers would work fine in any case.
BR,
Milan
,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2011 02:07 PM
Milan,
Good point. Yes, certainly, the situation with a primary ISP advertising the networks to two branches using the same ASN would be just as problematic.
Thank you for pointing that out!
Best regards,
Peter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-05-2011 07:06 AM
Hi, Milan - the ISPs are already doing AS Over Ride, so I am not facing that issue. But, thanks for the tip. I had completely forgot this basic rule.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-05-2011 07:03 AM
Hi Guys, thanks for the support.
I managed to configure the set-up the way I wanted. It is as follows:
ISP-1 - Primary, puts no pfx limit on us. We are currently moving ~5000 pfx around
ISP-2 - Backup, has limit to ~500 pfx max
Branch - Each spoke/branch advertises 4 pfx (WAN-ISP1, WAN-ISP2, Loopback iP, LAN pool)
Datacenter - connects to two ISPs.
router bgp 65501
neighbor ISP-1 remote-as 8000
neighbor ISP-1 filter-list 1 out
neighbor ISP-2 remote-as 9000
neighbor ISP-2 prefix-list ISP2-OUT out
network <...>
ip as-path access-list 1 permit _9000_
ip as-path access-list 1 permit ^$
prefix filter ISP2-OUT is set up to filter specific pfxes and let only the summaries to pass through. It also prevents WAN IPs of ISP-1 to make way into the ISP-2 Cloud. So, overall, we are sending around ~50 pfx across to ISP-2
router bgp 65503
neighbor ISP-1 remote-as 8000
neighbor ISP-1 prefix-list FILTER_WAN_IP_OF_ISP2 out
neighbor ISP-1 filter-list 1 out
neighbor ISP-1 route-map SET_LOCAL_PREF_TO_200 in
neighbor ISP-2 remote-as 9000
neighbor ISP-2 prefix-list FILTER_WAN_IP_OF_ISP1 out
neighbor ISP-2 filter-list 1 out
neighbor ISP-2 route-map SET_AS_PREPEND_3x out
network <....>
ip as-path access-list 1 permit ^$
router bgp 65503
neighbor ISP-1 remote-as 8000
network <....>
So, now everything is working as planned. However, I had some hardship working with prefix filter into a route-map. The gotcha was "double deny"... Like when you say "permit" in pfx filter and stick it into the route-map sequence number which also says "permit" (or something like that). Things don't work. These links made me understand things better: a)
http://www.networking-forum.com/viewtopic.php?t=23544 b)
http://www.cisco.com/en/US/docs/ios/12_0/np1/configuration/guide/1cbgp.html#wp7487
Next task is to make my Datacenter-2 as failover if ISP-2's link to Datacenter-1 goes down. I guess I'll have to just do the same config as Datacenter-1, but prepend outbound pfx 4x times.
Anyway, thanks for pooling in, I will update my progress in the thread. Cheers!
Message was edited by: NA NA
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
