- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: Cisco 2811 NAT Issues
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-02-2011 07:59 PM - edited 03-04-2019 10:56 AM
Having some problems with NAT between our Office and Co-Location. I have attached the details.
Basically we have 2 cisco 2811 routers connected over a bonded T1 connection. Private IP addresses on each end 10.58.0.2/30 <-> 10.58.0.1/30 . We have NAT enabled at the 10.58.0.2/30 router to get out to the internet and for access back into our servers using static nat . The problem is when we ping a device from the 10.58.0.2 to 10.58.0.1 it returns a public IP address instead of the private 10.58.3.0/24 that we want.
I can not turn off NAT on the 10.58.3.0/24 interface otherwise we lose internet connectivity and outside access in.
Can someone please help? How can we stop the translation in that direction?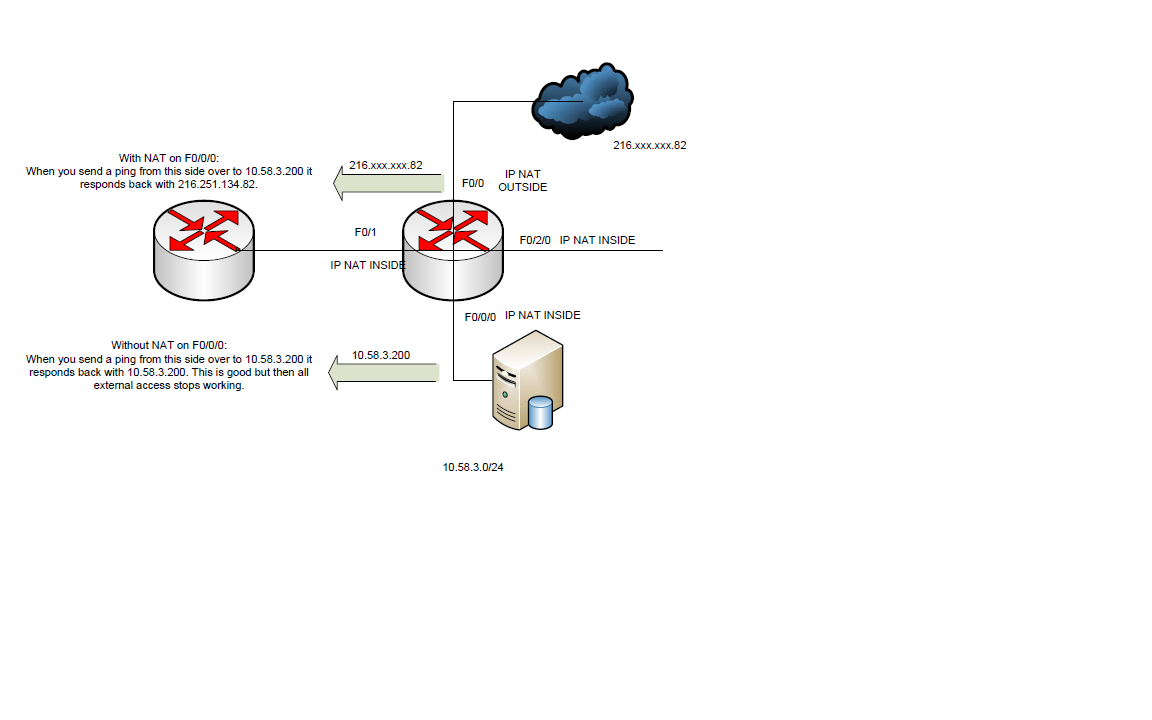
Solved! Go to Solution.
- Labels:
-
Other Routing
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-02-2011 09:21 PM
Hello,
You can try denying nat-ing the trafic between 10.58.x.x traffic :
no ip nat inside source list 1 interface FastEthernet0/0 overload
ip nat inside source list NAT interface FastEthernet0/0 overload
ip access-list ex NAT
deny ip 10.58.0.0 0.0.255.255 10.58.0.0 0.0.255.255
permit ip 10.58.0.0 0.0.255.255 any
Dan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-02-2011 08:48 PM
Here is the Config:
ip name-server 216.251.xxx.xxx
ip name-server 216.251.xxx.xxx
no ipv6 cef
!
multilink bundle-name authenticated
!
!
!
!
!
!
!
!
!
!
voice-card 0
!
!
!
license udi pid CISCO2811 sn FHK1446F2CP
!
redundancy
!
!
!
!
!
!
!
!
!
!
interface FastEthernet0/0
description $ETH-WAN$
ip address 216.251.xxx.xxx 255.255.255.240 secondary
ip address 216.251.xxx.xxx 255.255.255.240 secondary
ip address 216.251.xxx.xxx 255.255.255.240 secondary
ip address 216.251.xxx.xxx 255.255.255.240 secondary
ip address 216.251.xxx.xxx 255.255.255.240 secondary
ip address 216.251.xxx.xxx 255.255.255.240 secondary
ip address 216.251.xxx.xxx 255.255.255.240 secondary
ip address 216.251.xxx.xxx 255.255.255.240 secondary
ip address 216.251.xxx.xxx 255.255.255.240 secondary
ip address 216.251.xxx.xxx 255.255.255.240
ip nat outside
ip virtual-reassembly
duplex auto
speed auto
!
!
interface FastEthernet0/1
ip address 10.58.0.1 255.255.255.252
ip nat inside
ip virtual-reassembly
duplex auto
speed auto
!
!
interface FastEthernet0/0/0
ip address 10.58.3.1 255.255.255.0
ip nat inside
ip virtual-reassembly
duplex auto
speed auto
!
!
interface FastEthernet0/2/0
description $ES_LAN$
ip address 10.58.8.1 255.255.255.0
ip nat inside
ip virtual-reassembly
duplex auto
speed auto
!
!
ip default-gateway 216.251.xxx.xxx
ip forward-protocol nd
ip http server
ip http secure-server
!
!
ip nat inside source list 1 interface FastEthernet0/0 overload
ip route 0.0.0.0 0.0.0.0 216.251.xxx.xxx
ip route 10.58.0.0 255.255.192.0 FastEthernet0/1
ip route 10.58.66.0 255.255.255.0 FastEthernet0/1
ip route 10.58.68.0 255.255.255.0 FastEthernet0/1
!
access-list 1 remark SDM_ACL Category=2
access-list 1 permit 10.58.0.0 0.0.0.3
access-list 1 permit 10.58.3.0 0.0.0.255
access-list 1 permit 10.58.8.0 0.0.0.255
access-list 1 permit 10.58.66.0 0.0.0.255
access-list 1 permit 10.58.68.0 0.0.0.255
!
!
!
!
!
!
control-plane
!
!
!
!
!
!
!
!
!
line con 0
line aux 0
line vty 0 4
privilege level 15
transport input telnet ssh
line vty 5
transport input telnet ssh
!
scheduler allocate 20000 1000
end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-02-2011 09:21 PM
Hello,
You can try denying nat-ing the trafic between 10.58.x.x traffic :
no ip nat inside source list 1 interface FastEthernet0/0 overload
ip nat inside source list NAT interface FastEthernet0/0 overload
ip access-list ex NAT
deny ip 10.58.0.0 0.0.255.255 10.58.0.0 0.0.255.255
permit ip 10.58.0.0 0.0.255.255 any
Dan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-03-2011 09:52 PM
Thank you Dan! That worked.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
