- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: Cisco IR829 Routing / NAT configuration
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2019 08:09 AM - edited 09-17-2019 08:15 AM
Hello All,
We have an IR829GW router. I need to use it as a typical old school NAT router such that whatever devices are behind it use a NAT IP for the traffic that's going outbound ( for Internet access). For now, we just want to give devices behind it, access to internet using PAT.
The GE0 GigabitEthernet0 interface has the WAN/Internet uplink connection. Our NAT IP is 10.100.0.50, which i have assigned to this interface. All the internal devices are connected to a L2 switch that in turn is connected to the GigabitEthernet1 interface of this IR829. Please refer to the attached running config file for my current config.
If i assign my internal device an ip-address out of the 192.168.5.0/24 block , it can ping the default gateway 192.168.5.1 which is the IP of the vlan1 interface but nothing beyond that. I still can't get out to internet or ping any external facing stuff.
Also, i tried running the below commands to make GigabitEthernet1 part of vlan 1 membership to see if this makes any difference but these don't take effect or get saved despite doing a "wr mem".
interface GigbitEthernet1
switchport access vlan 1 switchport mode access
Can somebody please advise where am i going wrong ? All i need is my internal devices which are out of 192.168.5.0/24 block (access list 1) to be able to NAT while making any outbound requests using the GE0 interface ip-address (10.100.0.50)
Thanks in advance.
Solved! Go to Solution.
- Labels:
-
Other Routers
-
WAN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2019 08:35 AM
Hello
Your nat config looks okay so make sure you l2 switch doesnt have ip routing enabled and your clients have the correct default-gateway of the router SVI vlan 1 interface
Could also possible make a slight amendment to your default route
no ip route 0.0.0.0 0.0.0.0 GigabitEthernet0
ip route 0.0.0.0 0.0.0.0 GigabitEthernet0 10.100.0.x (ip of next hop address)
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2019 08:35 AM
Hello
Your nat config looks okay so make sure you l2 switch doesnt have ip routing enabled and your clients have the correct default-gateway of the router SVI vlan 1 interface
Could also possible make a slight amendment to your default route
no ip route 0.0.0.0 0.0.0.0 GigabitEthernet0
ip route 0.0.0.0 0.0.0.0 GigabitEthernet0 10.100.0.x (ip of next hop address)
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2019 09:16 AM
Hi Paul, Thank you for taking the time to review my config. I did what you suggested but still cant get my internal devices to go out. I am checking other things .
Quick question , Do you know why is that if i run the below command on Interface GigabitEthernet1, they have no effect or don't show up in the "show run" output underneath GigabitEthernet1 ? Is it because it is assumed that vlan1 is the default membership ?
switchport access vlan 1
switchport mode access
On the contrary, i tried creating another vlan 2 and if i do a "switchport access vlan 2" for the interface GigabitEthernet1 , this takes effect as in it it reflects in the show run output.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2019 09:28 AM
Hello
Yes you are correct,Access port default to vlan 1 so if you apply switchport access vlan 1 is wont show up as it default to that vlan anyway.
Can you ping the outside network sourced from your nat outside interface?
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2019 11:39 AM
Hello,
10.100.0.50/24 is not a valid public IP address. Do you have a cable modem connected to GigabitEthernet0 ?
Try and use the config below (changes marked in bold):
Current configuration : 4597 bytes
!
! Last configuration change at 15:04:46 UTC Tue Sep 17 2019
!
version 15.5
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
service internal
service unsupported-transceiver
!
hostname IR800
!
boot-start-marker
boot system flash:ir800-universalk9-mz.SPA.155-3.M2
boot-end-marker
!
!
no logging console
enable secret 5 $1$Zfod$zB180NdZ1tWPQChJAzWMe/
enable password cisco
!
no aaa new-model
ethernet lmi ce
service-module wlan-ap 0 bootimage autonomous
!
ignition off-timer 20
!
ip domain name IR800.lan.lab
ip inspect WAAS flush-timeout 10
ip cef
no ipv6 cef
!
multilink bundle-name authenticated
!
chat-script lte "" "AT!CALL" TIMEOUT 20 "OK"
!
crypto pki trustpoint TP-self-signed-422713650
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-422713650
revocation-check none
rsakeypair TP-self-signed-422713650
!
crypto pki certificate chain TP-self-signed-422713650
certificate self-signed 01
30820229 30820192 A0030201 02020101 300D0609 2A864886 F70D0101 05050030
30312E30 2C060355 04031325 494F532D 53656C66 2D536967 6E65642D 43657274
69666963 6174652D 34323237 31333635 30301E17 0D313930 39313631 35353833
345A170D 32303031 30313030 30303030 5A303031 2E302C06 03550403 1325494F
532D5365 6C662D53 69676E65 642D4365 72746966 69636174 652D3432 32373133
36353030 819F300D 06092A86 4886F70D 01010105 0003818D 00308189 02818100
BD274C2D 879C282F 3479CAEC 7AA7A0B4 2A12C42C 9C7FF63B A7CCF883 1B9E1737
6ED45124 8FCCC1E1 75254143 EE71A9A5 C1EF9661 6F277249 68D4A189 CAC0F58E
CF6E84BD 409F20B8 9F55E4F1 E7D8069E FD06B31E EA5BAF42 081158FA 8EC0FA66
DC6C43E8 331B8763 F5110D13 11EAF87B C0DF8FA4 6566A659 91003E08 F49B4715
02030100 01A35330 51300F06 03551D13 0101FF04 05300301 01FF301F 0603551D
23041830 1680148E 08D636AC 44A8D2A4 CAB690E3 81C1BCEF BF4AEF30 1D060355
1D0E0416 04148E08 D636AC44 A8D2A4CA B690E381 C1BCEFBF 4AEF300D 06092A86
4886F70D 01010505 00038181 005412F1 5C31E1D8 0E854176 086C625B 3C1AD39A
924E80D3 C711C119 BC1A9167 6923EE64 0C54CE88 8D069A14 4D3C8089 6E748120
F7B32E47 93BE91D8 2698AF1E 4DA017FE E5A9DEA5 FBED1B55 AFAB5DD8 BC4F52E7
E7BC3D2C 64499724 F9CFB1BE 69D63FF1 BDAADF4D 893F08A1 238D6F9C FBA0D54E
8138CE44 D90FE9B3 2F420125 66
quit
license udi pid IR829GW-LTE-NA-AK9 sn FTX2033801T
!
username icsuser01 password 0 cisco
!
redundancy
notification-timer 120000
!
controller Cellular 0
lte sim max-retry 0
lte failovertimer 0
lte modem link-recovery rssi onset-threshold -110
lte modem link-recovery monitor-timer 20
lte modem link-recovery wait-timer 10
lte modem link-recovery debounce-count 6
!
interface GigabitEthernet0
description Uplink to Testbed-LAN
ip address dhcp
ip nat outside
ip virtual-reassembly in
no mop enabled
!
interface wlan-ap0
no ip address
arp timeout 0
no mop enabled
no mop sysid
!
interface GigabitEthernet1
no ip address
!
interface GigabitEthernet2
no ip address
shutdown
!
interface GigabitEthernet3
no ip address
shutdown
!
interface GigabitEthernet4
no ip address
shutdown
!
interface Wlan-GigabitEthernet0
no ip address
!
interface GigabitEthernet5
no ip address
shutdown
duplex auto
speed auto
!
interface Cellular0
no ip address
encapsulation slip
dialer in-band
dialer string lte
!
interface Cellular1
no ip address
encapsulation slip
!
interface Vlan1
ip address 192.168.5.1 255.255.255.0
ip nat inside
ip virtual-reassembly in
!
interface Async0
no ip address
encapsulation scada
!
interface Async1
no ip address
encapsulation scada
!
ip forward-protocol nd
!
ip http server
ip http secure-server
!
ip nat inside source list 1 interface GigabitEthernet0 overload
ip route 0.0.0.0 0.0.0.0 GigabitEthernet0 dhcp
!
access-list 1 permit 192.168.5.0
!
control-plane
!
line con 0
stopbits 1
line 1 2
stopbits 1
line 3
script dialer lte
no exec
transport preferred lat pad telnet rlogin lapb-ta mop udptn v120 ssh
transport output lat pad telnet rlogin lapb-ta mop udptn v120 ssh
line 4
no activation-character
no exec
transport preferred none
no exec
transport preferred none
transport input all
transport output lat pad telnet rlogin lapb-ta mop udptn v120 ssh
line 8
no exec
transport preferred lat pad telnet rlogin lapb-ta mop udptn v120 ssh
transport output lat pad telnet rlogin lapb-ta mop udptn v120 ssh
line 1/3 1/6
transport preferred none
transport output none
stopbits 1
line vty 0 4
password ##$@$$$
login local
transport input ssh
!
no scheduler max-task-time
!
end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2019 12:35 PM - edited 09-17-2019 12:57 PM
Hi Georg, Our environment is such that i need to use that 10.x.x.50 private ip to NAT all the traffic originating from this internal network going outbound to a different corporate network. Typically we use public IP's for NAT yes but in our case, this is a NAT from one internal department to another.
This 10.100.0.50 ip-address is coming from a 10.100.0.0/24 network that is configured on a Cisco ASA Router/firewall in the destination network. The ASA has an interface defined with ip-address 10.100.0.1.
Please see below diagram for reference
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2019 12:45 PM
So the ASA is the Internet edge device, with the public IP address ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2019 12:59 PM
Georg, Yes ASA is the edge device which has the public ip-address. But to get to the ASA from that internal network in question i need to use the 10.100.x.x network as i also need connectivity to work between the 192.168.5.x network and 10.100.x.x network of the ASA.
Please see my diagram if it helps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2019 01:17 PM
Hello
@NeerajS can you ping to the external network - meaning can you reach the asa outside interface from the rtrs “wan” interface which would be the same subnet of the asa inside lan facing interface
if not then initiate a packet tracer from the asa and post its results
Example:
packet tracer input icmp 10.100.0.50 10.100.0.X detailed
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2019 01:41 PM
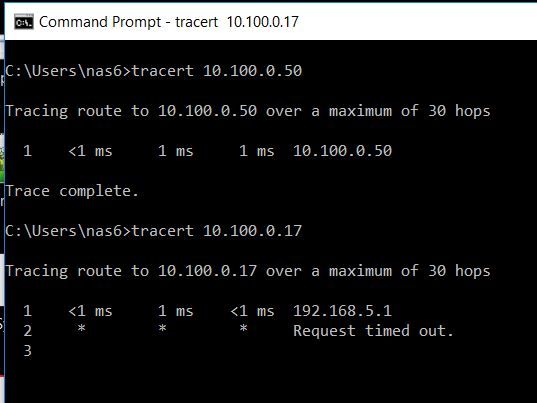
Hi Paul, yes i am able to ping the ASA interface 10.100.0.1 from the IR829 WAN interface . I can also ping other devices that are in the 10.100.0.x network which are behind the ASA from this IR829 cli console.
But i can't ping this ASA interface 10.100.0.1 or any further devices in the 10.100.0.x network from a device in the 192.168.5.x network which is behind the IR829.
Below is a screenshot from a device in 192.168.5.x network:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2019 02:22 PM
Hello
I would like to see a ping from 10.100.0.50 to 10.100.0.x please Also a packet tracer readout from
packet tracer input icmp 10.100.0.50 to 10.100.0.x
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-18-2019 07:20 AM - edited 09-18-2019 07:21 AM
HI Paul, thanks for the heads up. After checking further, i see that i cannot ping the ASA (10.100.0.1) from the GigabitEthernet0 interface of the IR829 even though the ip-address of this GE0 interface is 10.100.0.50 (within the same subnet) and the default-gateway is set to10.100.0.1.
However f i just do a "ping 10.100.0.1" on the cli console of IR829 without mentioning any source interface , that goes thru successfully. If i use source interface as GigabitEthernet0 , then it doesn't ping. Not sure which interface is the IR829 using then when it is able to ping.
I think the problem is here itself.
Thanks for all your help so far.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-18-2019 07:28 AM
Hello,
in your drawing, on the right side there is a 'device with IP address 10.100.0.x, what interface (on the ASA I assume) is that device connected to ?
Again, post the full configuration of the ASA, I have a feeling the problem is in there...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-18-2019 08:30 AM - edited 09-18-2019 08:31 AM
Hello Georg, I am working on getting the asa config from a different dept. Will update . Thank you very much for your help as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-18-2019 09:00 AM
@Georg Pauwen Pls find attached ASA running config. I have obscured our public ip in the running config as x.x . Please ignore that. This ASA is managed by a Cisco FMC virtual appliance.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide