- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: Cisco Router 1801 - How to route switch port traffic through L3 port on same router.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco Router 1801 - How to route switch port traffic through L3 port on same router.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-14-2019 09:23 AM - edited 03-14-2019 10:40 AM
Hi everyone.
This is my first question on the Cisco Learning Network and I am currently teaching myself how to configure Cisco routers and switches.
Currently I am learning on a Cisco 1801 (1800 Series) router that has an 8 port switch module installed. My aim is to use the onboard FA0 Layer 3 port to connect to my home router and to route all the traffic to the L2 switch ports which are on the same VLAN. So far I have been unsuccessful as any device on the switch ports cannot reply ping. If I connect the home router directly to these switch ports I will get the internet and I can ping the devices.
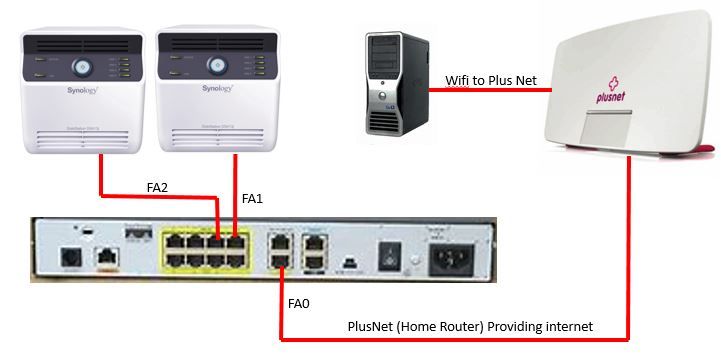
I have a small diagram here to explain the setup:

FA0 – Is connected to my Home router (layer3)
FA1 – Is connected to Server 1 (Layer2)
FA2 – Is connected to Server 2 (Layer2)
I can switch port VLAN to FA1 and FA2 no problem. I cannot however add VLAN to FA0 with the switchport command as it is a layer 3 port. Because of this, I am not able to reach the Servers. I am using my computer via wifi on the home router.
Any suggestions how I can get FA0 to talk to all the switch ports? Reason being it will allow me to utilize all 8 ports rather than just 7.
Thanks in advance
- Labels:
-
Other Routers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-14-2019 05:46 PM
You have described an environment but have not provided any detail to help us understand what is going on. A good starting place would be to provide the current running config of your 1801.
You have said this
I can switch port VLAN to FA1 and FA2 no problem
but I do not understand what this is supposed to tell us. Can you clarify?
It has been a very long time since I worked with an 1801 but I believe that this is the way that it should work:
- your routed layer 3 port connects to a subnet that provides outside connectivity.
- your layer 2 ports belong a a vlan (or perhaps to several vlans if you have configured more than one vlan for the switched ports)
- you should have configured a vlan interface (something like interface vlan 1) and configured an IP address on that vlan interface (or multiple vlan interfaces if you have configured multiple vlans)
- this would allow your router to route from your vlans to the subnet of the routed port (and from the subnet of your routed port to the subnet(s) of your vlan(s).
- you should have configured (or learned) a default route.
- you should have configured address translation for the subnets of your vlans as they attempt to access outside networks.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-14-2019 06:06 PM
Hello
When you sat "home router" do you mean ISP router or just another router?
Can you post the configuration of this router and also if applicable your "home" router
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-18-2019 10:16 AM
Thanks for the feedback guys,
There is no config to upload as I have now started again with a 256mb CF card. Instead I have created a clearer diagram:
So from the above diagram, I am unable to communicate from the desktop machine (Connected to the home router) to the Servers that are connected via FA1 and FA2 switch ports. From the above setup, how can I get this to work?
What I have previously tried to configure:
Homne router is generic 192.168.1.x
Port FA0 cannot do Switchport as it is an L3 port. So I assigned it the same IP range: 192.168.1.x
I enabled IP routing and pointed at VLAN 2.
I enabled IP helper-address and pointed it at the home router.
I setup a VLAN2 and assigned them to FA1 and FA2 on the same IP range as 192.168.2.x (Had to be different range as it gives an error saying 'This is overlaping FA0'.
From the Desktop computer I could not Ping the servers and could not access them. If I changed from FA0 and put it on FA8 and assigned VLAN2. I can ping the servers no problem and access them.
How can I get FA0 to do the job so I can keep all 8 switch ports available for use?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-18-2019 10:29 AM
Hi,
Let's try this configuration:
Interface FastEthernet 0
no shut
IP address 192.168.1.X 255.255.255.0
ip nat outside
exit
!
!
Interface VLAN 2
ip nat inside
Ip address 192.168.2.1 255.255.255.0
exit
!
!
ip access-list standard 1 permit ip any
!
IP route 0.0.0.0 0.0.0.0 FastEthernet0
!
!
ip nat inside source list 1 fastEthernet 0 overload
!
!
interface range fastethernet 1-2
switchport mode access
swicthport access vlan 2
!
!
Regards,
Deepak Kumar
Deepak Kumar,
Don't forget to vote and accept the solution if this comment will help you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-18-2019 11:10 AM
Let us start the response by reviewing a fundamental aspect of the 1801 router. FA0 is a routed interface and will have an IP address in some subnet. The other FA interfaces are switch ports and will belong to one or more vlans. Each of the vlans configured on the router can have a vlan interface which will have an IP address. The addresses on the vlan interfaces must be in subnets that are different from the subnet of FA0.
Starting with the easy one, let us think about what is happening when you connect PlusNet to a router interface other than FA0. In this case PlusNet is connected into the vlan subnet and all devices connected to PlusNet should be able to communicate successfully with devices connected to 1801. I believe that your post confirms that this is the case.
When you connect PlusNet to FA0 then there are several things that must happen.
1) the address configured on FA0 must be in the same subnet used for computers connected to PlusNet.
2) the address configured on the vlan interface (for FA1, FA2, etc) must be in a subnet that is different from FA0.
3) the servers connected in the vlan must have a default gateway that is the 1801 vlan address.
4) the 1801 must have a default route that has the PlusNet address as its next hop.
5) PlusNet must have a route for the subnet used by 1801 vlan and the next hop for this route must be the IP of FA0. (this is a very important requirement)
If you do these things then there should be connectivity between the computers connected on PlusNet and the servers connected on 1801.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-18-2019 11:20 AM
Hello,
on a side note, and you probably have a good reason, but why do you want to use the layer 3 port on the 1801 ? You basically introduce another potential bottleneck that will slow your Internet connection down, and you will have to use double NAT (as described in Deepak's last post), which will effectively disable anything UPnP, as well as any kind of port forwarding...
So why not use just the layer 2 switchports ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-18-2019 11:36 AM
Why to use the routed port rather than just using switch ports is an interesting question. I can think of several possible answers:
- perhaps, having obtained a router rather than a switch, they want to gain experience with configuration of a router.
- perhaps they want to isolate the servers connected to 1801 from the broadcast traffic of the devices connected to PlusNet.
- perhaps they want to be able to control who communicates with the servers. With the routed port they can configure access lists to control what goes through.
- perhaps there is a plan that at some point in the future there is need to establish another group of devices that require some isolation. With the routed port there is possibility of multiple vlans each logically separated from the others.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2019 06:13 AM
Hi all,
Thanks for being patient.
I have followed through with both Deepak Kumar configuration and Richard Burts understanding of the configuration.
The PlusNet has no ability to add any route tables. It can port forward which is not necessary for this to work.
Deepaks configuration is all there is on the router right now.
Unfortunatly I am still unable to see the server. The server I can confirm points to the FA0 port.
Any more ideas?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2019 09:25 AM
If there is not possibility of adding an entry to the routing table on PlusNet then my suggestion about implementing a routing solution on the 1801 routing between the subnets for the servers and the subnet for PlusNet will not work. So I believe that you have 2 alternatives to consider.
1) implement the subnet for the servers on the 1801 and configure address translation for the server addresses so that the PlusNet does not see a remote subnet. This would be sort of like but not quite the same as the solution suggested by Deepak.
2) implement a solution using the switch ports of the 1801 but not using the routed port FA0 as has been suggested earlier in this discussion.
In terms of the alternative with address translation I will say that for purposes of this discussion there are 2 types of address translation. (some of my colleagues may want to say that there are more than 2 but for this discussion we need to consider only 2). We are familiar with dynamic address translation in which you configure an interface as nat inside and configure another interface as nat outside, and then translate using the router outside interface with overload. This is essentially the solution that Deepak suggests. This works very well to allow devices from inside to initiate traffic to outside and to receive responses from outside. But it does not work to allow devices from outside to initiate traffic to inside. So in your situation the servers could initiate traffic to the PCs but the PCs could not initiate traffic to the servers.
So you will need the second type of address translation, which is static translation. For static translation you translate each address of the inside network (each server address) into an address reachable in the outside network).
The address translation could be done but it gets complex to implement. Unless there are reasons we do not yet know to want the routed solution, I would suggest that it will be easier if you implement the solution using only the switch ports of the 1801.
HTH
Rick
Rick
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide