- Cisco Community
- Technology and Support
- Networking
- Routing
- Cisco Support Community: Expert Lab Session - MPLS VPN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco Support Community: Expert Lab Session - MPLS VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-08-2013 04:55 AM - edited 03-04-2019 08:23 PM
Welcome to the Cisco Support Community Expert Lab session.
I am Hitesh Kumar (CCIE SP #38757) and I work for the High Touch Technical Support (HTTS) team in Cisco. Along with me Rahul Rammanohar (CCIE R&S, SP #13015), Vinay Kumar (CCIE R&S #35210) and Ruchir Jain (CCIE R&S #26911) will be active on this thread to discuss the challenges you run into while configuring mpls vpn setup. We will try our best to resolve your queries by providing supporting documents. If needed, we can setup a live interactive session to respond to the queries based on your inputs.
Please provide your inputs/queries by replying to this discussion thread.
Introduction & Topology Description:
Many Service Providers use MPLS/VPN as a technology to provide connectivity between multiple sites for customers. We would like you to look through the topology and let us know what doubts you might have on configuring the various protocols/features, working of the various protocols in this scenario, manipulation of the traffic flows and the MPLS packet forwarding.
The MPLS/VPN topology provided depicts a typical section of a Service Provider network. The routers in the cloud belong to the Service Provider and are used to provide MPLS/VPN services to customers. Customer routers (CE) connect to the edge routers (PE) of the Service Provider cloud. The Service Provider uses Route Reflectors (RR) to minimize the number of BGP neighborships within the core and they use 2 or more RRs to provide redundancy.
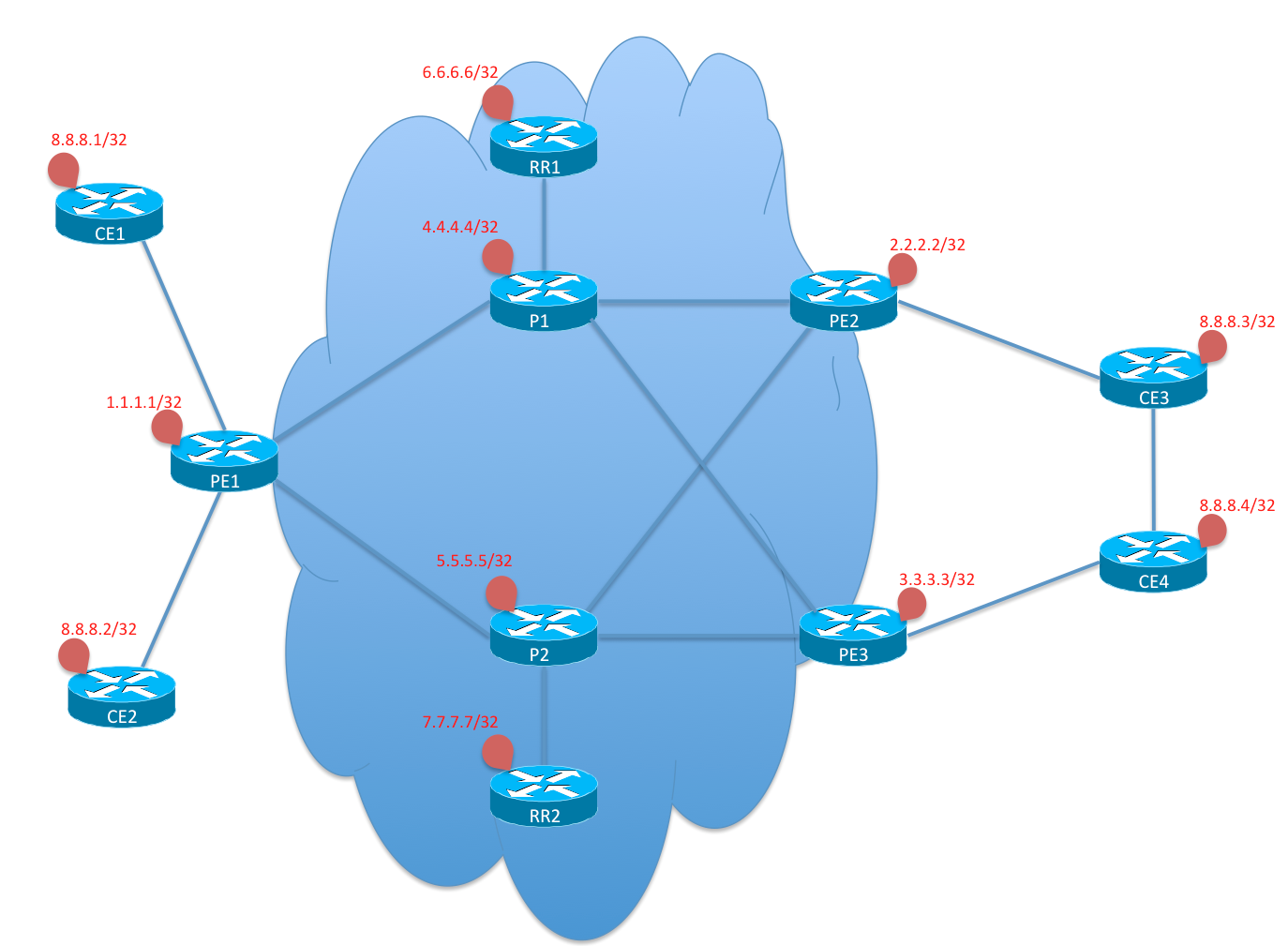
In this scenario, a Service Provider is using 7 routers of which, 2 routers are RRs, 2 routers are Core routers (P) that do not connect to any customer and 3 PE routers that connect to the 4 different sites of a customer (say ABC). Customer ABC has 2 Hub sites (on the right side of the diagram) and 2 Spoke sites (on the left side of the diagram). The hub sites can talk to each other via the service provider link or via a backdoor link. The spoke routers cannot talk to each other directly, but need to talk via either of the hub sites only. The customer has configured OSPF as the IGP within his network and the Service Provider has configured ISIS.
Additional Reference:
- Labels:
-
Other Routing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-18-2013 07:42 AM
Hi gents
This is very interesting session, CSC always look for innovations
ok let me do the ice breaking in this session
if there is voice traffic need to be given priority and FRR within about 50ms using MPLS-TE FRR
where to place the TE ends between PEs or Ps ? and will be using DS-TE combined with CBTS in this case ? will the back up tunnel to be used/configured manually or automatic?
also how and where MPLS-TE one hope primary and back can be applicable in this topology
can we use LFA and where combined with MPLS-TE in this topology ( is it best practice )
Thanks
Marwan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-19-2013 03:45 AM
Thanks Marwan. Appreciate you starting the discussion. Please find below answers to questions you posted:
Q. If there is voice traffic need to be given priority and FRR within about 50ms using MPLS-TE FRR
where to place the TE ends between PEs or Ps ?
In our topology if we want we would be having TE tunnels between PE devices. However, in general it
depends upon network and design requirements where we put TE tunnels. If number of PE routers are
considerable then it is easier to configure and manage P-to-P tunnels. Here is a comparison of the
two approaches:
1. PE-to-PE tunnels: The number of TE tunnels increase in this case but you get more control on
traffic forwarding. Also, you do not need to run LDP in core as the tunnels are full mesh.
2. P-to-P tunnels: Number of tunnels are less compared to PE-to-PE but we loose granularity in
traffic forwarding. It would require LDP over TE tunnels and you might have deeper label stack
in core.
Q. And will be using DS-TE combined with CBTS in this case ? Will the back up tunnel to be
used/configured manually or automatic?
Definitely a good option. However in our topology we have not planned to but if you have any queries
regarding it we can try our best to incorporate it.
Q. Also how and where MPLS-TE one hop primary and backup can be applicable in this topology.
We intended this topology for MPLS L3 VPN setup hence there are only two P routers. In such a
topology if we wish to use TE tunnels best would be to have PE-to-PE tunnels. The primary tunnel
can go through one P box and the backup via the other.
Q. Can we use LFA and where combined with MPLS-TE in this topology ( is it best practice )
LFA with TE-FRR can indeed be used. It reduces number of TE tunnels required but it adds another
protocol to troubleshoot which increases complexity.
Regards,
Hitesh, Rahul, Ruchir, Vinay
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-19-2013 04:54 AM
Thanks for this detailed response
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-19-2013 05:23 AM
Hi All
We have added the configuration of all the devices in above mentioned topology based on the described scenario with PE1 being XR.
Kindly let us know in case of any queries.
Regards,
Hitesh, Rahul, Ruchir, Vinay
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-19-2013 01:13 AM
Hi - would someone be able to explain the use behind the pseudo-wire control word please?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide