- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: Curious if I need Port Forwarding on a Switch running (2) PBR’s
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2022 12:53 PM
Hello
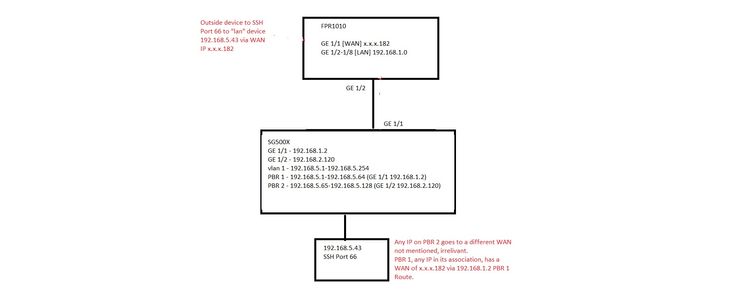
I have a SG500X with 2 PBR’s.
LAN 192.168.5.1-32 use GE 1/1 192.168.1.2 for Internet Access
LAN 192.168.5.33-64 use GE 1/2 10.0.2.2 for Internet Access.
LAN Subnet 192.168.5.0, regardless of their Internet access communicate via same Subnet.
GE 1/1 on SG500X connects to GE 1/2 on an FPR1010 which has a Subnet 192.168.1.0 and has a WAN of x.x.x.182.
So, anything on SG500X 192.168.5.1-32 will route to 192.168.1.2 which will route to x.x.x.182 for Internet.
Being that Host 192.168.5.55 would actually be on the 2nd PBR (10.0.2.2) for Internet access, it’s still on the 192.168.5.0 that also shares PBR 1 (192.168.1.2). Can I create a NAT on the FPR then a Port Forward on the Switch?
So for example, I want to SSH in to x.x.x.182 Port 66 and create a NAT /ACL to redirect that Port 66 to 192.168.1.2 and then on the FPR, being 192.168.5.55 is non the PBR2, create a Port Forward to that IP?
I have created NAT and ACL in every fashion to allow (outside) to SSH to x.x.x.182 which would NAT to 192.168.1.2 (I even tried to NAT to 192.168.5.55 and also added a static route to 192.168.5.0 via 192.168.1.2) but nothing I do allows me to connect.
Am I right to assume it is because the 192.168.5.55 is on PBR2 and not PBR1, 192.168.1.2 which leads back to x.x.x.182, and therefore has to INCOMING path to it?
So I was wondering if on SG500X I would need to make a port forward “incoming port 66 ssh goes to 192.168.5.55”
Hopefully what I am attempting makes sense enough to get some guidance.
Solved! Go to Solution.
- Labels:
-
LAN Switching
-
Routing Protocols
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-04-2022 01:56 PM
can you share the PBR config
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-05-2022
08:51 AM
- last edited on
09-19-2022
02:01 AM
by
Translator
![]()
I am pretty sure this is what I have, offhand. I also wonder, by looking at this would this explain why no access is allowed in from WAN side? And to mention, I have yet added the new PBR you suggested at this point but here it is;
access list 101 permit ip 192.168.5.0 0.0.0.63 any
access list 102 permit ip 192.168.5.65 0.0.0.63 any
route-map tointernet permit 10
match ip address 101
set ip next-hop 192.168.1.1
route-map tointernet permit 11
match ip address 102
set up next-hop 192.168.2.1
interface vlan
ip policy route-map tointernet
Now, I do have the next hops of the end Router IP, not the local Ethernet IP's. I assume it would know that to get to 192.168.1.1 it would use 192.168.1.7 (GE 1/1) for example for PBR 1. My meaning is, would next hop be the destination router or the Local IP that connects to the destination ip.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-05-2022
09:02 AM
- last edited on
09-19-2022
02:02 AM
by
Translator
![]()
next-hop
is IP of not connect LOCAL in your SW, it IP of the destination L3 device connect to your SW.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-05-2022
09:27 AM
- last edited on
09-19-2022
02:03 AM
by
Translator
![]()
I am sorry I am unsure of what you mean. Do you mean that
next-hop
is the destination IP so 192.168.1.1 PBR1 and 192.168.2.1 PBR2 is correct?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-05-2022
03:22 PM
- last edited on
09-19-2022
02:03 AM
by
Translator
![]()
R1-R2
when we config the PBR
set ip next-hop <R2 IP>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-05-2022 05:51 PM
In my scenario;
PBR 1 allocates 192.168.5.1-192.168.5.64 to use 192.168.1.1 (via 192.168.1.7 GE 1/1) to access Internet on that router
PBR 2 allocates 192.168.5.65-192.168.5.128 to use 192.168.2.1 (via 192.168.2.7 GE 1/2) to access Internet (different Internet)
That is the only configuration on the SG500X, and I am wondering why a device in the 192.168.5.0 (.1-.128) can not access 192.168.5.1 unless I remove the Gateway on the Host trying to connect. I am wondering if it is due to the PBR? I won't be removing my PBR's so if it is impossible, I will deal with it.
Aside from that, now seeing my PBR's and it's setup, can you see any obvious reason why Host 192.168.5.43 (On PBR1) would not be able to receive SSH Connectivity via WAN Side?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-07-2022 11:15 AM - edited 08-07-2022 01:10 PM
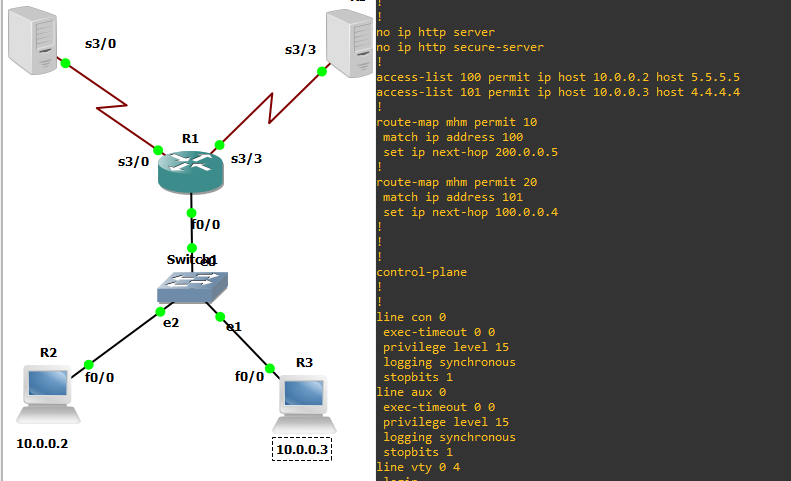
R1 in my lab is you SG500X and One Server is represent FPR.
I already do small Lab and test config of route-map for two host in same subnet and I success.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-07-2022 12:26 PM
I am not having issues from lan to lan as everything is on same subnet. My issue is that I can not get anyone from WAN side, internet, to connect.
It is fine, never mind. I thank you for your assistance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-07-2022 12:35 PM - edited 08-07-2022 12:50 PM
two host in same subnet,
the Router R1 will forward any traffic from host 10.0.0.2 to server connect via S3/3 using PBR
the Router R1 will forward any traffic from host 10.0.0.3 to server connect via S3/0 using PBR
I am not talking about connect host in same subnet.
NOTE:- the default GW in both host is same 10.0.0.1
NOTE:- the return traffic must config in both Server.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-09-2022
06:26 AM
- last edited on
09-19-2022
02:14 AM
by
Translator
![]()
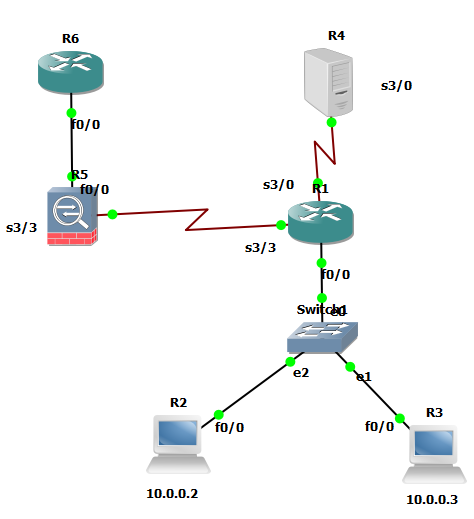
R6 in my lab represent the PC you use to SSH to R2 (10.0.0.2)
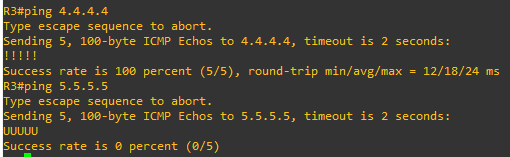
the R1 config with PBR and we can success ping from R2 to LO 5.5.5.5 in R5 (FW icon)
until now everything is OK config
but we assign from the PC conenct to R5 (FW icon),
so we need port-forwarding
ip nat inside source static tcp R2(10.0.0.2) 23 interface R5-interface f0/0 223
WHY THE PORT IS DIFFERNT ?
because if you run SSH in R5 then the R5 will handle the traffic as it send to it not send to R2(10.0.0.2)
after that I can easy telnet the R2(10.0.0.2) from R6 no issue at all.
NOTE:- R6 no need to now the route toward 10.0.0.2 because it use the R5-interface f0/0 to access not 10.0.0.2
the power of NAT
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-09-2022 11:16 AM
Hello
So I think I am grasping this more, but I have a few questions (more when I post my configs for FPR and SG500.
1.) You mention I need a 'port forward', is this done on the FPR or the SG500X?
2.) Do I need both NAT and ACL on the FPR to "direct" incoming Port 66 to destination Port 23?
I assume I need an ACL to PERMIT the traffic, and then a NAT to "forward" incoming (x.x.x.182) 66 to destination (192.168.5.43) 23).
Is that the port forwarding you speak of? Or in addition to, or just yours and Not NAT?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-09-2022 11:24 AM - edited 08-09-2022 11:25 AM
1.) Do I need both NAT and ACL on the FPR to "direct" incoming Port 66 to destination Port 23? YES
I assume I need an ACL to PERMIT the traffic, and then a NAT to "forward" incoming (x.x.x.182) 66 to destination (192.168.5.43) 23). YES YES
you need ACL to permit the traffic and you need NAT to forward traffic.
2.) You mention I need a 'port forward', is this done on the FPR or the SG500X? NO NEED in SG500X
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-16-2022 01:52 PM - edited 09-17-2022 10:36 AM
Well I still have not been able top make this work, and believe you me, I have tried every variation.
What puzzles me is that my server has 6 STATIC WAN IP's; The FPR1010 itself is x.x.x.182 but I also have .177 - .181. I have Static NAT on, for example, x.x.x.177 to 192.168.5.55 and SSH works fine from 'outside'. I have x.x.x.178 to 192.168.5.56 and SSH works fine from outside but NOTHING will allow me to connect to SSH on 192.168.5.43 which I have made a NAT for and ACL's etc.
Being that x.x.x.182 is the FPR itself, is SH by default blocked or disabled on the FPR? Could that be blocking it? I have set up the SSH on 192.168.5.43/x.x.x.182 exactly as I have the others but nothing works. Something has to be disabling/blocking it. Why else would 2 Static IP's work and the FPR not unless it itself was blocking it?
Long story short; Even though I have NAT and an ACL, could the FPR itself have SSH Disabled/Blocked in a different configuration tab? And being that the other 2 STATIC NAT's that do work, could it be because they are not the FPR address and is bypassing the FPR default SSH being disabled?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2022 08:48 PM
Well after so many months I finally realized my problem! I did now allow SSH Access on the FPR1010 through the Management settings.
Now, it works.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-18-2022 03:17 AM
I am so happy your issue solve finally,
can you share how allow SSH access through management
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide