- Cisco Community
- Technology and Support
- Networking
- Routing
- DHCP is not working in Cisco 876 Router
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
DHCP is not working in Cisco 876 Router
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-07-2022 01:47 AM
DHCP is not working in my Cisco 867 router, no systems getting IP address. DHCP configuration is given below,
ip dhcp pool LAN-POOL
network 10.x.x.0 255.255.255.0
default-router 10.x.x.2
domain-name xyz.net
dns-server 10.x.x.x
- Labels:
-
Routing Protocols
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-07-2022 01:55 AM
- Show (full) router config ,
M.
-- Each morning when I wake up and look into the mirror I always say ' Why am I so brilliant ? '
When the mirror will then always repond to me with ' The only thing that exceeds your brilliance is your beauty! '
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-07-2022 02:33 AM
version 15.5
!
!
!
!
ip dhcp excluded-address 10.x.x.x
ip dhcp excluded-address 10.x.x.x
ip dhcp excluded-address 10.x.x.x
ip dhcp excluded-address 10.x.x.x
ip dhcp excluded-address 10.x.x.x
ip dhcp excluded-address 10.x.x.x
ip dhcp excluded-address 10.x.x.x
!
ip dhcp pool ccp-pool
import all
network 10.x.x.x 255.255.255.248
default-router 10.x.x.x
lease 0 2
!
ip dhcp pool LAN-POOL
network 10.x.x.0 255.255.255.0
default-router 10.x.x.2
domain-name 10.x.x.x
dns-server 10.x.x.0
!
!
!
no ip bootp server
ip domain xxxxxx
ip name-server 8.8.8.8
ip name-server 4.2.2.2
ip cef
login on-failure log
login on-success log
no ipv6 cef
!
!
archive
log config
logging enable
logging size 200
notify syslog contenttype plaintext
hidekeys
object-group service ALLOWED_PORT
tcp eq 587
tcp eq 995
tcp-udp eq 67
udp eq domain
udp eq isakmp
udp eq non500-isakmp
icmp
tcp-udp eq 123
tcp eq 443
tcp eq 21112
!
object-group network SSL_VPN_NETWORK
host x.x.x.x
host x.x.x.x
host x.x.x.x
host x.x.x.x
!
object-group network TRUSTED_NETWORK
10.0.0.0 x.x.x.x
x.x.x.x 255.255.255.0
host x.x.x.x
x.x.x.x 255.255.240.0
x.x.x.x 255.255.252.0
x.x.x.x 255.255.240.0
x.x.x.x 255.248.0.0
host x.x.x.x
host x.x.x.x
!
!
controller VDSL 0
shutdown
no cdp run
!
track 1 list boolean or
object 4
object 5
object 6
object 7
!
track 4 ip sla 1
delay down 3 up 6
!
track 5 ip sla 2
delay down 3 up 6
!
track 6 ip sla 3
delay down 3 up 6
!
track 7 ip sla 4
delay down 3 up 6
!
track 8 ip sla 5
delay down 3 up 6
!
track 12 interface GigabitEthernet0 line-protocol
!
!
class-map match-all HTTP_CLASS
match access-group name HTTPLLIST
class-map match-all IP_CAM_CLASS
description <<Class mapp matching the upload traffic>>
match access-group name IP_CAM_UPLD
class-map match-all MAIL_TRAFFIC
description <<Class mapp matching the MAIL_TRAFFIC traffic>>
match access-group name MAIL_TRAFFIC
class-map match-all VMS_CLASS_2
match access-group name VMS_ACL_2
class-map match-all VMS_CLASS_1
match access-group name VMS_ACL_1
class-map match-all IPCAM_CLASS
match access-group name IPCAM_FILTER
class-map match-all CONTROL_TRAFFIC
description <<Class mapp matching the CONTROL_TRAFFIC traffic>>
match access-group name CONTROL_TRAFFIC
!
policy-map IPCAM_Policy
class IPCAM_CLASS
conform-action transmit
exceed-action drop
policy-map TRAFFIC_CNTRL
class VMS_CLASS_1
shape peak 64000
class VMS_CLASS_2
shape peak 64000
class IP_CAM_CLASS
shape average 64500
class HTTP_CLASS
priority
class CONTROL_TRAFFIC
shape average 16000
class MAIL_TRAFFIC
shape average 64000
class class-default
shape average 64000
!
!
!
!
!
interface ATM0
no ip address
shutdown
no atm ilmi-keepalive
!
interface Ethernet0
description <<Connected to Switch - LAN PORT>>
no ip address
shutdown
!
interface FastEthernet0
no ip address
!
interface FastEthernet1
description <<Connected to Switch - LAN PORT>>
switchport access vlan 3
no ip address
!
interface FastEthernet2
description <<Connected to Switch - LAN PORT>>
switchport access vlan 3
no ip address
!
interface FastEthernet3
description <<Connected to Switch - LAN PORT>>
switchport access vlan 3
no ip address
!
interface GigabitEthernet0
description <<Connected to 3G Combo router>>
switchport access vlan 2
no ip address
!
interface GigabitEthernet1
description <<Connected to Modem on Bridge Mode>>
no ip address
no ip redirects
no ip proxy-arp
duplex auto
speed auto
no cdp enable
pppoe-client dial-pool-number 1
!
interface Vlan1
description $ETH_LAN$
ip address 10.x.x.x 255.x.x.x
ip tcp adjust-mss 1452
!
interface Vlan2
ip address dhcp
no ip redirects
no ip proxy-arp
!
interface Vlan3
description <<LAN GATEWAY>>
ip address x.x.x.x 255.x.x.x
ip access-group WSA_PROD in
no ip redirects
no ip proxy-arp
ip nat inside
ip virtual-reassembly in
ip tcp adjust-mss 1100
crypto map cmap
!
interface Dialer1
mtu 1492
ip address negotiated
no ip redirects
no ip proxy-arp
ip nat outside
ip virtual-reassembly in
encapsulation ppp
ip tcp adjust-mss 1452
dialer pool 1
dialer-group 1
no cdp enable
ppp authentication pap chap callin
ppp chap hostname XXXXXXXXXXX
ppp chap password 7 XXXXXXXXXXX
ppp pap sent-username XXXXXXXXXXX password XXXXX
ppp ipcp dns request
crypto map cmap
!
ip forward-protocol nd
no ip http server
ip http access-class 23
ip http authentication local
no ip http secure-server
ip http timeout-policy idle 60 life 86400 requests 10000
!
!
ip ssh source-interface Vlan3
ip ssh version 2
!
permit tcp any any eq 443
ip radius source-interface Vlan3
ip sla auto discovery
ip sla 1
icmp-echo XXXXXXXXXXX source-interface Dialer1
frequency 6
ip sla schedule 1 life forever start-time now
ip sla 2
icmp-echo XXXXXXXXXXX source-interface Dialer1
frequency 6
ip sla schedule 2 life forever start-time now
ip sla 3
icmp-echo XXXXXXXXXXX source-interface Dialer1
frequency 6
ip sla schedule 3 life forever start-time now
ip sla 4
icmp-echo XXXXXXXXXXX source-interface Dialer1
frequency 6
ip sla schedule 4 life forever start-time now
ip sla 5
icmp-echo XXXXXXXXXXX source-interface Vlan2
frequency 5
ip sla schedule 5 life forever start-time now
ip sla 6
icmp-echo XXXXXXXXXXX source-interface Vlan3
frequency 5
ip sla schedule 6 life forever start-time now
ip sla 7
icmp-echo XXXXXXXXXXX source-interface Vlan3
frequency 20
ip sla schedule 7 life forever start-time now
ip sla 8
icmp-echo XXXXXXXXXXX source-interface Vlan3
frequency 180
ip sla schedule 8 life forever start-time now
ip sla 9
icmp-echo XXXXXXXXXXX source-interface Vlan3
frequency 180
ip sla schedule 9 life forever start-time now
ip sla 10
icmp-echo XXXXXXXXXXX source-interface Vlan3
frequency 5
ip sla schedule 10 life forever start-time now
ip sla 11
icmp-echo XXXXXXXXXXX source-interface Vlan3
frequency 5
ip sla schedule 11 life forever start-time now
logging history informational
logging facility syslog
logging source-interface Vlan3
mac-address-table aging-time 10
!
route-map EzVPN1 permit 1
match ip address 103
match interface Dialer1
!
route-map EzVPN_sec permit 1
match ip address 103
match interface Vlan2
!
snmp-server group V3User v3 auth
snmp-server group V3Group v3 auth read V3Read
snmp-server group V3Group v3 priv read V3Read
snmp-server group WHTSAPP v3 auth
snmp-server group WHTSAPGroup v3 auth read WHTSAPRead
snmp-server group WHTSAPGroup v3 priv read WHTSAPRead
snmp-server view V3Read iso included
snmp-server view V3Read mib-2 included
snmp-server view WHTSAPRead iso included
snmp-server view WHTSAPRead mib-2 included
snmp-server trap-source Vlan3
snmp-server system-shutdown
snmp-server enable traps snmp authentication linkdown linkup coldstart warmstart
snmp-server enable traps config
snmp-server enable traps entity
snmp-server host x.x.x.x version 3 priv V3User
snmp-server host x.x.x.x version 3 priv V3User
snmp-server host x.x.x.x version 3 auth WHTSAPP
access-list 20 remark ***//SNMP_ACL//***
access-list 20 permit x.x.x.x
access-list 20 permit x.x.x.x
access-list 20 deny any log
access-list 23 permit x.x.x.x log
access-list 23 permit x.x.x.x log
access-list 23 permit x.x.x.x log
access-list 23 permit x.x.x.x log
access-list 23 permit x.x.x.x log
access-list 23 permit x.x.x.x log
access-list 23 permit x.x.x.x log
access-list 23 permit x.x.x.x log
access-list 23 permit x.x.x.x 0.0.0.255 log
access-list 23 deny any log
access-list 103 deny ip x.x.x.x 0.0.0.255 x.x.x.x 0.0.0.255
access-list 103 deny ip any host x.x.x.x
access-list 103 deny ip x.x.x.x 0.0.0.255 x.x.x.x 0.0.0.255
access-list 103 deny ip any x.x.x.x 0.255.255.255
!
!
radius server RAS
address ipv4 x.x.x.x auth-port 1812 acct-port XX
!
!
!
line con 0
exec-timeout 5 0
no modem enable
line aux 0
no exec
line vty 0 4
access-class 23 in
exec-timeout 5 0
privilege level 15
transport input ssh
transport output telnet
!
scheduler allocate 60000 1000
ntp authentication-key xxxx
ntp authenticate
ntp server x.x.x.x source Vlan3
time-range ipcam_limit
periodic daily 8:00 to 20:30
!
!
end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-07-2022 02:45 AM
Hello,
post the full running configuration (show run) with 'x' - ing out all IP addresses. It is impossible to figure out what you have configured without seeing the actual IP addresses. These are all private space IP addresses anyway.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-07-2022 01:57 AM
Hello,
does your LAN interface have IP address 10.x.x.2 255.255.255.0 ?
Also, make sure your DHCP service is enabled:
867#conf t
867(config)#service dhcp
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-07-2022 02:39 AM
Hi,
DHCP service is enabled, Also IP is showing when we checking "sh ip dhcp binding", but not pinging to the IPs also communication is not happening
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-07-2022 02:44 AM
but not pinging to the IPs also communication is not happening
need more information here - from what IP not pining from where (that means what is source IP and what is destination IP ?)
If you looking to setup Multiple Lan, all VLAN should also configure inside nat to go internet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-07-2022 02:50 AM
issue with DHCP or with connectivity ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-07-2022 02:53 AM
If we put manual IP in system, it will work. Otherwise not working. Suspecting issue with DHCP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-07-2022 03:05 AM
interface Vlan1
description $ETH_LAN$
ip address 10.x.x.x 255.x.x.x <<- MUST MATCH
ip tcp adjust-mss 1452
!
ip dhcp pool LAN-POOL
network 10.x.x.0 255.255.255.0 <<- MUST MATCH
default-router 10.x.x.2
domain-name 10.x.x.x
dns-server 10.x.x.0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-07-2022 03:35 AM
Hi,
We have tagged Vlan3 in interface FE2, please find the configuration,
ip dhcp pool LAN-POOL
network 10.x.x.0 255.255.255.0
default-router 10.x.x.2
domain-name xxxxxx
dns-server 10.x.x.0
interface Vlan3
description <<LAN GATEWAY>>
ip address 10.x.x.2 255.255.255.0
ip access-group WSA_PROD in
no ip redirects
no ip proxy-arp
ip nat inside
ip virtual-reassembly in
ip tcp adjust-mss 1100
crypto map cmap
interface FastEthernet2
description <<Connected to Switch - LAN PORT>>
switchport access vlan 3
no ip address
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-07-2022 04:05 AM
Hello,
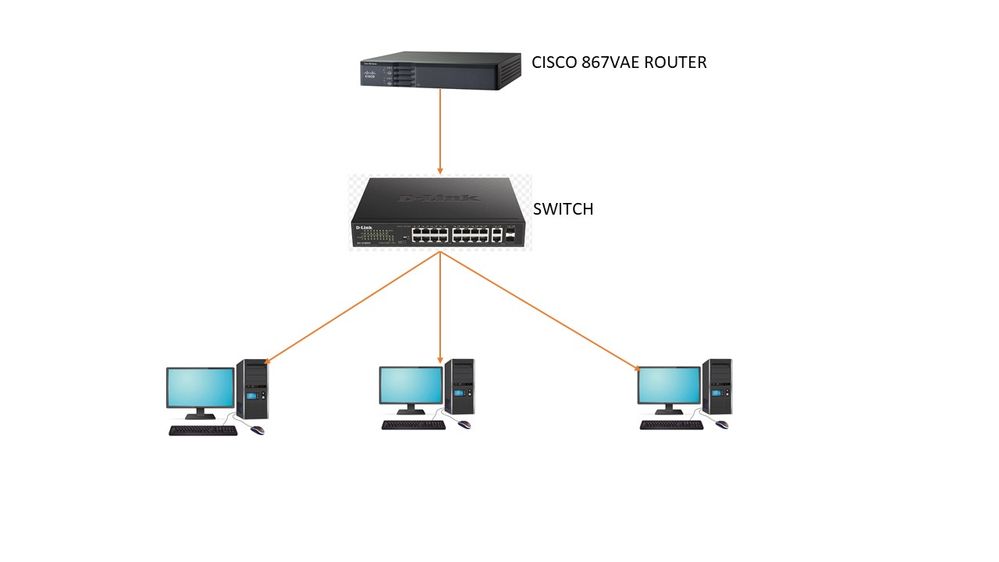
why is there a crypto map applied to a LAN (VLAN3) interface ? I would suggest that you post a detailed drawing of your entire network, as there seem to be a lot of 'unknowns' in your topology, one or several of which are causing your problem(s).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-08-2022 07:33 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-07-2022 04:24 AM
ip access-WSA_PROD in <<- can I see this ACL ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-08-2022 01:06 AM
ip access-list extended WSA_PROD
permit udp any eq bootpc any eq bootps
permit object-group ALLOWED_PORT 10.x.x.0 0.0.0.255 any log
permit ip 10.x.x.0 0.0.0.255 object-group TRUSTED_NETWORK log
permit ip 10.x.x.0 0.0.0.255 10.x.x.0 0.0.0.255
permit tcp host 10.x.x.1 host 10.x.x.2 eq 22
permit tcp 10.x.x.0 0.0.0.255 object-group SSL_VPN_NETWORK eq 443
permit udp 10.x.x.0 0.0.0.255 host 4.2.2.2 eq domain
permit udp 10.x.x.0 0.0.0.255 host 8.8.8.8 eq domain
deny ip any any
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide