- Cisco Community
- Technology and Support
- Networking
- Routing
- disabling inter-VRF routing on IOS router
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-22-2020 08:26 AM - edited 02-22-2020 08:27 AM
Hi All,
I am trying to setup a router (1921) with two VRFs in my lab and having problem with disabling inter-VRF routing on it.
Configuration:
Current configuration : 2049 bytes ! ! Last configuration change at 15:32:42 UTC Sat Feb 22 2020 ! version 15.7 service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption ! hostname Router ! boot-start-marker boot-end-marker ! ! ! no aaa new-model ! ! ! ! ! ! ! ! ! ip vrf VRF0 rd 65000:0 ! ip vrf VRF1 rd 65000:1 ! ! ! ! ip cef no ipv6 cef ! multilink bundle-name authenticated ! ! ! license udi pid CISCO1921/K9 sn FJC1922E0AT ! ! ! redundancy ! ! ! ! ! ! ! ! ! ! ! ! ! ! ! interface Tunnel0 ip vrf forwarding VRF0 ip address 1.1.1.1 255.255.255.252 tunnel source GigabitEthernet0/0 tunnel destination 192.168.140.51 tunnel vrf VRF0 ! interface Tunnel1 ip vrf forwarding VRF1 ip address 1.1.1.2 255.255.255.252 tunnel source GigabitEthernet0/1 tunnel destination 192.168.120.51 tunnel vrf VRF1 ! interface Embedded-Service-Engine0/0 no ip address shutdown ! interface GigabitEthernet0/0 ip vrf forwarding VRF0 ip address 192.168.120.51 255.255.255.0 duplex auto speed auto ! interface GigabitEthernet0/1 ip vrf forwarding VRF1 ip address 192.168.140.51 255.255.255.0 duplex auto speed auto ! interface GigabitEthernet0/0/0 no ip address ! interface GigabitEthernet0/0/1 no ip address ! interface GigabitEthernet0/0/2 no ip address ! interface GigabitEthernet0/0/3 no ip address ! interface Vlan1 no ip address ! ip forward-protocol nd ! no ip http server no ip http secure-server ! no ip route static inter-vrf ip route vrf VRF0 0.0.0.0 0.0.0.0 192.168.120.254 ip route vrf VRF1 0.0.0.0 0.0.0.0 192.168.140.254 ! ! ! ! control-plane ! ! vstack ! line con 0 line aux 0 line 2 no activation-character no exec transport preferred none transport output pad telnet rlogin lapb-ta mop udptn v120 ssh stopbits 1 line vty 0 4 login transport input none ! scheduler allocate 20000 1000 ! end
Both interfaces of the router are connected to the same L3 switch that performs inter-VLAN routing. I enabled some debugs and captures on the L3 switch and when pinging between router's Gig0/0 and Gig0/1 it does not traverse the L3 switch. Also when pinging GRE tunnel IPs I cannot see the traffic on the L3 switch so to me it seems that the traffic goes directly. Any idea how can I stop this and force the traffic between VRFs to flow through L3 switch all the time?
Thanks!
Solved! Go to Solution.
- Labels:
-
Routing Protocols
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-26-2020 01:15 PM - edited 02-27-2020 01:23 AM
It could be because when you ping the SVI the packets need to be switched in software so the debugs show them whereas when you ping between routers assuming the packets are going via the switch they are hardware switched so the debugs may not pick them up.
Why not just apply an inbound acl on the one of the SVIs on the L3 switch blocking ICMP and then try pinging and see if it works.
If it doesn't then remove the acl and if then works you can be pretty sure your traffic is going via the switch which looking at your topology it should be.
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-22-2020 12:16 PM
Hello,
not sure what you are asking...by default, VRFs cannot talk to each other.
Can you post the configuration of the layer 3 switch ? What exactly are you trying to accomplish ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-23-2020 04:47 AM - edited 02-23-2020 04:48 AM
That was my understanding but when trying to ping between Gig0/0 and Gig0/1 IP addresses and running the debug ip icmp on L3 switch I cannot see it. I can see the packets when pinging SVI IP address though so debug seems to be working.
I would expect that when running:
Router#ping vrf VRF0 192.168.140.51
it would go to the L3 switch, be routed between VLANs, and then reach the router via Gig0/1. Is that correct or my understanding is incorrect? Ping is going through but it does not show in the debug run on the switch.
L3 switch configuration below.
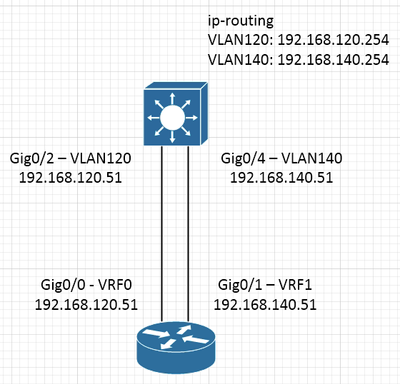
Router's Gig0/0 is connected to Gig0/2 on the switch.
Router's Gig0/1 is connected to Gig0/4 on the switch.
[...] ip routing ! ! ! ! ! ! ! ! port-channel load-balance src-dst-ip ! spanning-tree mode rapid-pvst spanning-tree extend system-id ! vlan internal allocation policy ascending ! vlan 110,120,130,140,150,160,1610,1620,3210,3220 ! ip ssh version 2 ! class-map match-all disabled ! ! ! ! interface GigabitEthernet0/2 switchport access vlan 120 switchport trunk encapsulation dot1q switchport mode access switchport nonegotiate power inline never ! interface GigabitEthernet0/4 switchport access vlan 140 switchport trunk encapsulation dot1q switchport mode access switchport nonegotiate power inline never ! interface Vlan120 ip address 192.168.120.254 255.255.255.0 ip helper-address 172.16.10.1 ip helper-address 172.16.10.2 ! interface Vlan140 ip address 192.168.140.254 255.255.255.0 ip helper-address 172.16.10.1 ip helper-address 172.16.10.2 !
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-26-2020 04:48 AM
Anyone? Maybe they way I am verifying this is incorrect but I cannot see the traffic between VRFs traversing L3 switch.
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-26-2020 06:28 AM
Hello,
I think either your setup or your question is unclear. You cannot ping between VRFs. How is the layer 3 switch involved here ? Post a diagram showing your topology...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-26-2020 07:02 AM
Diagram below. I can ping and I would expect it should traverse the L3 switch but looking at "debug ip icmp" it doesn't look like it is traversing it.
Debug IP ICMP on the switch is not showing the traffic.
Is there other way I should be verifying this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-26-2020 01:15 PM - edited 02-27-2020 01:23 AM
It could be because when you ping the SVI the packets need to be switched in software so the debugs show them whereas when you ping between routers assuming the packets are going via the switch they are hardware switched so the debugs may not pick them up.
Why not just apply an inbound acl on the one of the SVIs on the L3 switch blocking ICMP and then try pinging and see if it works.
If it doesn't then remove the acl and if then works you can be pretty sure your traffic is going via the switch which looking at your topology it should be.
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-26-2020 08:26 PM
Thank you. That was what made me thinking the traffic does not flow through the switch but adding the ACL on the switch resulted in ping not going through so that confirms it actually goes via the switch as expected.
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-26-2020 01:13 PM
Hi,
This command (no ip route static inter-vrf) will make the router ignore any inter-vrf routing achieved via static routes; the routes can be configured, but are not used. What you're doing is something else:
- first of all your static routes are configured for intra-vrf routing, not inter-vrf routing
- you're achieving VRF leaking because you make use of an external L3 device where VRF's have not been extended
- since you ping between the router's interfaces in different VRF's, the switch will CEF switch your ICMP packets, it's expected you see nothing on debug icmp
Regards,
Cristian Matei.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide