- Cisco Community
- Technology and Support
- Networking
- Routing
- May I ask what kind of kind
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-18-2017 11:56 PM - edited 03-05-2019 08:22 AM
Please see the attached layout:
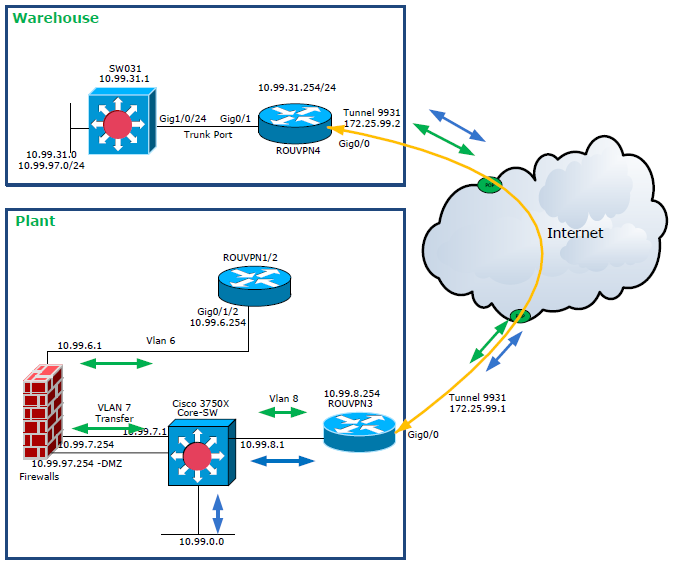
VLAN 97(DMZ) Default Gateway is on Firewall and i want allow whole subnet IP address(10.99.97.0/24) on warehouse via VPN but its not working.(cant ping from firewall.....traffic is not passing via FW)
Please provide me the guidance or solution to do it!!!
Thanks in advance
Solved! Go to Solution.
- Labels:
-
LAN Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2017 10:10 PM
Thanks.
We did create a ACL to restrict the vlan 32 to not access all other DATA vlans on core switch except DMZ!!
1. Now what should i do to forward the traffic of vlan 32 to DMZ interface.
2. What kind of rules or config I must ask to my security colleague to do on FW to allow vlan 32.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2017 12:42 AM
Are you able to ping the DMZ interface on the firewall from vlan 32?
you just need to ask the firewall admin to allow communication between 10.99.32.0/24 and 10.99.97.0/24. Also make sure that firewall has a route to 10.99.32.0/24 unless it has a default route back to the core switch
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2017 01:26 AM
Ok, I will ask security guy to allow the communication between and let you know.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2017 11:33 PM
No I cant ping. I asked FW admin to allow the communication between 10.99.32.0/24 &10.99.97.0/24 and vice versa.
If the FW admin allow communication between these VLANs then what should I do further so that my whole traffic from vlan 32 pass through the DMT interface connected on core switch ?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-27-2017 05:54 AM
ping 10.99.97.254 source 10.99.32.254. - This works
ping 10.99.21.254 source 10.99.32.254 - This doesn't work
What is 10.99.21.254?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-27-2017 06:46 AM
its a data VLAN in plant.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-27-2017 07:29 AM
Remember the ACL you applied. You will need to add the ACL entry in red and make sure it's above the deny entry.
ip access-list extended 150
permit ip10.99.32.0 0.0.0.255 10.99.97.0 0.0.0.255
permit ip 10.99.32.0 0.0.0.255 10.99.21.0 0.0.0.255
deny ip 10.99.32.0 0.0.0.255 any
permit ip any any
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-27-2017 10:14 PM
But I don't want that VLAN21 communicate with VLAN 32 and vice versa.
Means our Old ACL is perfect in my case.
Now I want that all traffic from VLAN32 should pass through DMZ interface.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-28-2017 03:57 AM
Is it not passing through DMZ interface? Per that ACL the only destination network vlan 32 is allowed to talk to is 10.99.97.0/24. Please explain more what's not working ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-28-2017 04:03 AM
I think on switch/router side we cant do much. Now Firewall/security guy must create rules to forward the traffic to outside!! I will inform you once its done.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-27-2017 12:02 AM
I can ping now.
ROUVPN4#ping 10.99.97.254 source 10.99.32.254
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.99.97.254, timeout is 2 seconds:
Packet sent with a source address of 10.99.32.254
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 8/11/12 ms
!
ROUVPN4#ping 10.99.21.254 source 10.99.32.254
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.99.21.254, timeout is 2 seconds:
Packet sent with a source address of 10.99.32.254
.U.U.
Success rate is 0 percent (0/5)
ROUVPN4#
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2017 07:03 AM
I configured it on Core-Switch with VLAN 8 interface and now i cant ping Plant DATA VLANs ip from VLAN 32.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2017 06:01 AM
You are right about the problem at the edge router, this will not work because you cannot route to the same subnet.
However it is not clear if the traffic would even get there to be honest.
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2017 06:20 AM
May I ask what kind of kind of tunnel is it
Its a IPSEC tunnel.
is included in the ACL that is used to trigger the tunnel
There is no ACL used to trigger tunnel.
I am trying to think how would it work because you are traversing another network when you hit edge router at site plant before you hit the gateway for 10.99.97.0/24
That is correct... but is there any possibility to make it work?
If you have any idea then please share it..
Thanks
- « Previous
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide