- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: Edge Routing and Firewall Redundancy Design
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-26-2020 11:47 AM
Hi All,
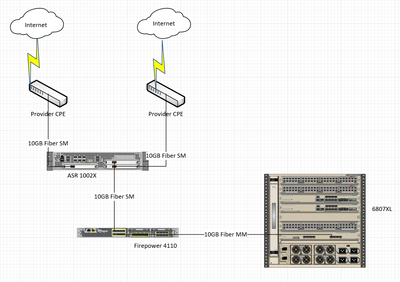
I'm working on a configuration design for a redundant topology. Currently we have geo and carrier diverse paths to the internet, with BGP working such that if one path fails, BGP uses the other path. All BGP is done on the edge ASR 1002-X, and we simply have default routes in the 6807-XL. We do not load balance across the links. This is what the physical topology looks like:
We have recently purchased redundant edge equipment (a 2nd ASR with SPA cards, and a 2nd Firepower). Ideally this would be a redundant/HA scenario, with no load balancing. I realize I'm at a bit of a disadvantage on the Firepower side (wrong forum, I know), because I don't have enough SPA cards for both Firepowers to go to both ASR's. So, I'm not sure how that would work from an HA perspective. I know I may need to use HSRP for the routing side.
Any input is greatly appreciated!
Thanks!
Solved! Go to Solution.
- Labels:
-
ASR 1000 Series
-
Routing Protocols
-
WAN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2020 08:34 AM
Hi,
To be able to trigger failover in all case (interface issues/failure and unit issues/failure), between FTD Active and FTD Standby, you would need the two FTD's to be visible to each other via layer2, on both the inside link (facing the switch) and outside link (facing the ASR). So ideally, you would connect both the ASR's and FTD's through your internal switch (just dedicated inside/outside VLANs with no layer 3 on the switch), and not directly.
This way, any ASR or any FTD going down, you still have network up and running. As for routing convergence, from the switch you have a default route towards the Primary IP address of the FTD on inside, from FTD routes towards the switch, from ASR routes towards the Primary IP address of FTD on outside, from FTD you have a default route pointing to the HSRP VIP of ASR.
Regards,
Cristian Matei.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2020 12:36 AM
Hi,
I would need the following info in order to outline the best option:
- is your FTD(FirePOWER) deployed in routed or transparent mode? do you have VPN's or NAT configured on FTD?
- in case you run routed mode, how is routing done between ASR, FTD and the switch, so on the inside part of the network?
- is a single FTD box, per your current configuration, capable to handle by itself all the traffic?
Regards,
Cristian Matei.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2020 05:35 AM
Hi Cristian,
Thank you for responding!
The FTD is deployed in routed mode. No VPN's, but NAT is configured.
The routes back and forth from the FTD are static.
A single 4110 can indeed handle all of the traffic.
Thank you for your help!
-Mike
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2020 05:37 AM
FWIW, I'm worried about the SPA card slot count in the ASR. I think if I go HA pair, I'll need an uplink from each FTD to each ASR for full redundancy.
Exploring the option of returning the new ASR1002-X and trading in the current ASR1002-X for a ASR1006-X with dual RP's.
-Mike
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2020 08:34 AM
Hi,
To be able to trigger failover in all case (interface issues/failure and unit issues/failure), between FTD Active and FTD Standby, you would need the two FTD's to be visible to each other via layer2, on both the inside link (facing the switch) and outside link (facing the ASR). So ideally, you would connect both the ASR's and FTD's through your internal switch (just dedicated inside/outside VLANs with no layer 3 on the switch), and not directly.
This way, any ASR or any FTD going down, you still have network up and running. As for routing convergence, from the switch you have a default route towards the Primary IP address of the FTD on inside, from FTD routes towards the switch, from ASR routes towards the Primary IP address of FTD on outside, from FTD you have a default route pointing to the HSRP VIP of ASR.
Regards,
Cristian Matei.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2020 08:45 AM
It sounds like our ASR1002-X units are the problem then, since I don't have a fourth slot for the extra FTD. We're OK on the switch side (inside), it appears that outside is going to be an issue.
Thank you for clarifying and helping!
-Mike
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide