- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: Getting warning IP nat pool too small
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-15-2023
04:51 PM
- last edited on
06-07-2023
10:34 PM
by
Translator
![]()
I want to NAT single inside IP to multiple outbound IP's based up on the destination subnet. For example :
My appserver should be natted to 10.10.1.10 for packets tx/rx toward customer1
My appserver should be natted to 10.10.2.10 for packets tx/rx toward customer2
My appserver should be natted to 10.10.3.10 for packets tx/rx toward customer3.
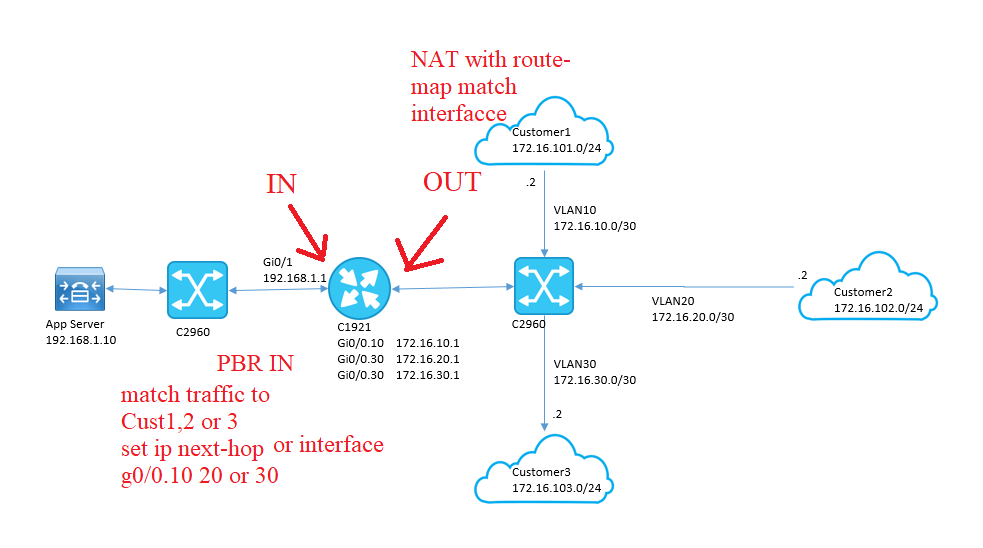
I have a router Cisco1921 with Gi0/1 configured with
ip 192.168.1.1
I have an app server with IP address 192.168.1.10 and gateway 192.168.1.1
I have three customers connected to us using three private point to point circuits.
All the three circuits are connected to my layer 2 Ethernet switch C2960.
On Ethernet switch customer1 is in VLAN 10, customer 2 is in VLAN 20 and customer3 is on VLAN 30.
Cisco router 1921 Gi0/0 has three sub interfaces, one for each customer.I was thinking that I wll create three
ACL
and
NAT POOL
for each customer and use the
ACL
to assign the
seperate pool for each customer. I hit a road block,
ip NAT pool
gives me a warning when I try to create a pool with single ip it is asking for atleast netmask .252 and giving the following warning
Pool NAT-POOL-CUST3 mask 255.255.255.255 too small; should be at least 255.255.255.252
How can I NAT my single inside IP to multiple outbound IP's based upon the destination subnet?
!
interface GigabitEthernet0/1
description LOCAL INTERFACE
ip address 192.168.1.1 255.255.255.0
ip nat inside
ip virtual-reassembly in
duplex auto
speed auto
!
interface GigabitEthernet0/0.10
description CUSTOMER1
encapsulation dot1Q 10
ip address 172.16.10.1 255.255.255.252
ip nat outside
ip virtual-reassembly in
!
interface GigabitEthernet0/0.20
description CUSTOMER2
encapsulation dot1Q 20
ip address 172.16.20.1 255.255.255.252
ip nat outside
ip virtual-reassembly in
!
interface GigabitEthernet0/0.30
description CUSTOMER3
encapsulation dot1Q 30
ip address 172.16.30.1 255.255.255.252
ip nat outside
ip virtual-reassembly in
!
ip route 172.16.101.0 255.255.255.0 172.16.10.2
ip route 172.16.102.0 255.255.255.0 172.16.20.2
ip route 172.16.103.0 255.255.255.0 172.16.30.2
!
ip access-list extended ACL-NAT-CUST1
permit ip host 192.168.1.10 172.16.101.0 0.0.0.255
!
ip access-list extended ACL-NAT-CUST2
permit ip host 192.168.1.10 172.16.102.0 0.0.0.255
!
ip access-list extended ACL-NAT-CUST3
permit ip host 192.168.1.10 172.16.103.0 0.0.0.255
!
!
ip nat pool NAT-POOL-CUST1 10.10.1.10 10.10.1.10 netmask 255.255.255.255
ip nat pool NAT-POOL-CUST2 10.10.2.10 10.10.2.10 netmask 255.255.255.255
ip nat pool NAT-POOL-CUST3 10.10.3.10 10.10.3.10 netmask 255.255.255.255
##I get the warning got the above three commands##
If I get past the warning then I was planning to use the following:
!
ip nat outside source list ACL-CUST1 pool NAT-POOL-CUST1 add-route
ip nat outside source list ACL-CUST2 pool NAT-POOL-CUST2 add-route
ip nat outside source list ACL-CUST3 pool NAT-POOL-CUST3 add-route
!
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2023 07:57 AM - edited 05-17-2023 07:59 AM
Agreed - that will route the packets but not NAT them.
To NAT them you use NAT with route-maps. Use static NAT with route-map - each static NAT will then only match the desired traffic and do 1to1 translation on the IP.
Take a look at this example: https://www.ciscozine.com/using-route-maps-for-conditional-nat/
FYI: in your config the ACL names don't match the names of ACLs used with NAT.
Please click Helpful if this post helped you and Select as Solution (drop down menu at top right of this reply) if this answered your query.
------------------------------
TAC recommended codes for AireOS WLC's and TAC recommended codes for 9800 WLC's
Best Practices for AireOS WLC's, Best Practices for 9800 WLC's and Cisco Wireless compatibility matrix
Check your 9800 WLC config with Wireless Config Analyzer using "show tech wireless" output or "config paging disable" then "show run-config" output on AireOS and use Wireless Debug Analyzer to analyze your WLC client debugs
Field Notice: FN63942 APs and WLCs Fail to Create CAPWAP Connections Due to Certificate Expiration
Field Notice: FN72424 Later Versions of WiFi 6 APs Fail to Join WLC - Software Upgrade Required
Field Notice: FN72524 IOS APs stuck in downloading state after 4 Dec 2022 due to Certificate Expired
- Fixed in 8.10.196.0, latest 9800 releases, 8.5.182.12 (8.5.182.13 for 3504) and 8.5.182.109 (IRCM, 8.5.182.111 for 3504)
Field Notice: FN70479 AP Fails to Join or Joins with 1 Radio due to Country Mismatch, RMA needed
How to avoid boot loop due to corrupted image on Wave 2 and Catalyst 11ax Access Points (CSCvx32806)
Field Notice: FN74035 - Wave2 APs DFS May Not Detect Radar After Channel Availability Check Time
Leo's list of bugs affecting 2800/3800/4800/1560 APs
Default AP console baud rate from 17.12.x is 115200 - introduced by CSCwe88390
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-19-2023 10:33 AM
I think it should work. Depends on inside/outside direction but assuming it's inside -> outside then the crypto map ACL should match the IP after NAT I believe. But as always - test to confirm.
https://www.cisco.com/c/en/us/support/docs/ip/network-address-translation-nat/6209-5.html
ps. also never had trouble with sending NATed packets up VPN.
Please click Helpful if this post helped you and Select as Solution (drop down menu at top right of this reply) if this answered your query.
------------------------------
TAC recommended codes for AireOS WLC's and TAC recommended codes for 9800 WLC's
Best Practices for AireOS WLC's, Best Practices for 9800 WLC's and Cisco Wireless compatibility matrix
Check your 9800 WLC config with Wireless Config Analyzer using "show tech wireless" output or "config paging disable" then "show run-config" output on AireOS and use Wireless Debug Analyzer to analyze your WLC client debugs
Field Notice: FN63942 APs and WLCs Fail to Create CAPWAP Connections Due to Certificate Expiration
Field Notice: FN72424 Later Versions of WiFi 6 APs Fail to Join WLC - Software Upgrade Required
Field Notice: FN72524 IOS APs stuck in downloading state after 4 Dec 2022 due to Certificate Expired
- Fixed in 8.10.196.0, latest 9800 releases, 8.5.182.12 (8.5.182.13 for 3504) and 8.5.182.109 (IRCM, 8.5.182.111 for 3504)
Field Notice: FN70479 AP Fails to Join or Joins with 1 Radio due to Country Mismatch, RMA needed
How to avoid boot loop due to corrupted image on Wave 2 and Catalyst 11ax Access Points (CSCvx32806)
Field Notice: FN74035 - Wave2 APs DFS May Not Detect Radar After Channel Availability Check Time
Leo's list of bugs affecting 2800/3800/4800/1560 APs
Default AP console baud rate from 17.12.x is 115200 - introduced by CSCwe88390
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-15-2023
11:02 PM
- last edited on
06-07-2023
11:03 PM
by
Translator
![]()
The warning you are receiving is because the subnet mask you specified for the
NAT pool
is too small. In order to
NAT
your single inside IP to multiple outbound IPs based on the destination subnet, you need to make a few adjustments to your configuration. First, you need to modify the subnet masks of your subinterfaces on the router to accommodate larger subnets. Change the subnet masks from /30 to /29 or larger. For example:
interface GigabitEthernet0/0.10
description CUSTOMER1
encapsulation dot1Q 10
ip address 172.16.10.1 255.255.255.248
ip nat outside
ip virtual-reassembly in
!
interface GigabitEthernet0/0.20
description CUSTOMER2
encapsulation dot1Q 20
ip address 172.16.20.1 255.255.255.248
ip nat outside
ip virtual-reassembly in
!
interface GigabitEthernet0/0.30
description CUSTOMER3
encapsulation dot1Q 30
ip address 172.16.30.1 255.255.255.248
ip nat outside
ip virtual-reassembly in
Next, modify your ACLs to match the correct destination subnets for each customer:
ip access-list extended ACL-NAT-CUST1
permit ip host 192.168.1.10 172.16.10.0 0.0.0.7
!
ip access-list extended ACL-NAT-CUST2
permit ip host 192.168.1.10 172.16.20.0 0.0.0.7
!
ip access-list extended ACL-NAT-CUST3
permit ip host 192.168.1.10 172.16.30.0 0.0.0.7
Finally, update your NAT pool configuration to use the correct subnet masks:
ip nat pool NAT-POOL-CUST1 10.10.1.10 10.10.1.10 netmask 255.255.255.248
ip nat pool NAT-POOL-CUST2 10.10.2.10 10.10.2.10 netmask 255.255.255.248
ip nat pool NAT-POOL-CUST3 10.10.3.10 10.10.3.10 netmask 255.255.255.248
With these modifications, you should be able to
NAT
your single inside IP to multiple outbound IPs based on the destination subnets for each customer.
M.
-- Each morning when I wake up and look into the mirror I always say ' Why am I so brilliant ? '
When the mirror will then always repond to me with ' The only thing that exceeds your brilliance is your beauty! '
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-16-2023
02:01 PM
- last edited on
06-07-2023
11:05 PM
by
Translator
![]()
Hi Mark, thanks fir your time and assistance.
I can not change the
netmask
for the WAN interfaces because it also requires the change to be made at far end.
I only need one IP address in the pool per customer. What is the significance
netmask
in the pool?
What will be the impact if I change the
netmask
to .252 ? This way the warning goes away and I still have one IP address per pool.
ip nat pool NAT-POOL-CUST1 10.10.1.10 10.10.1.10 netmask 255.255.255.252
ip nat pool NAT-POOL-CUST2 10.10.2.10 10.10.2.10 netmask 255.255.255.252
ip nat pool NAT-POOL-CUST3 10.10.3.10 10.10.3.10 netmask 255.255.255.252
Using this solution, can the traffic originate from outside to inside?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-15-2023
11:14 PM
- last edited on
06-07-2023
11:16 PM
by
Translator
![]()
The warning you're encountering is due to the fact that you're specifying a single IP address as the
NAT pool
, which requires a
netmask of at least /30 (255.255.255.252)
. However, since you want to map a single inside IP to multiple outbound IPs based on the destination subnet, you need to use a different approach.
Instead of using traditional
NAT pools
, you can achieve your desired
NAT
behavior using Policy-Based NAT (PBR) and route-maps. Here's an example configuration that should work for your scenario:
ip access-list extended ACL-NAT-CUST1
permit ip host 192.168.1.10 172.16.101.0 0.0.0.255
ip access-list extended ACL-NAT-CUST2
permit ip host 192.168.1.10 172.16.102.0 0.0.0.255
ip access-list extended ACL-NAT-CUST3
permit ip host 192.168.1.10 172.16.103.0 0.0.0.255
route-map RM-NAT-CUST1 permit 10
match ip address ACL-NAT-CUST1
set ip next-hop 10.10.1.10
route-map RM-NAT-CUST2 permit 10
match ip address ACL-NAT-CUST2
set ip next-hop 10.10.2.10
route-map RM-NAT-CUST3 permit 10
match ip address ACL-NAT-CUST3
set ip next-hop 10.10.3.10
interface GigabitEthernet0/0.10
ip policy route-map RM-NAT-CUST1
interface GigabitEthernet0/0.20
ip policy route-map RM-NAT-CUST2
interface GigabitEthernet0/0.30
ip policy route-map RM-NAT-CUST3
In this configuration, we're using PBR to match the source traffic based on the corresponding access list for each customer. Then, we set the next-hop IP address to the appropriate outbound IP for
NAT.
Make sure to remove the previous
NAT pool
configurations and the
ip nat outside source
commands you mentioned earlier.
Note that this configuration assumes that the outbound IP addresses (10.10.1.10, 10.10.2.10, 10.10.3.10) are already configured on the router and reachable. Also, ensure that the necessary routing is in place for the next-hop addresses.
Remember to test the configuration thoroughly to ensure it meets your requirements and functions as expected in your specific network environment.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-16-2023 01:31 PM
Hi Mr. Khan,
Appreciare your response. Your answer does not fit my requirements but it is good to know about this possibility in case If I need this in future.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2023 07:57 AM - edited 05-17-2023 07:59 AM
Agreed - that will route the packets but not NAT them.
To NAT them you use NAT with route-maps. Use static NAT with route-map - each static NAT will then only match the desired traffic and do 1to1 translation on the IP.
Take a look at this example: https://www.ciscozine.com/using-route-maps-for-conditional-nat/
FYI: in your config the ACL names don't match the names of ACLs used with NAT.
Please click Helpful if this post helped you and Select as Solution (drop down menu at top right of this reply) if this answered your query.
------------------------------
TAC recommended codes for AireOS WLC's and TAC recommended codes for 9800 WLC's
Best Practices for AireOS WLC's, Best Practices for 9800 WLC's and Cisco Wireless compatibility matrix
Check your 9800 WLC config with Wireless Config Analyzer using "show tech wireless" output or "config paging disable" then "show run-config" output on AireOS and use Wireless Debug Analyzer to analyze your WLC client debugs
Field Notice: FN63942 APs and WLCs Fail to Create CAPWAP Connections Due to Certificate Expiration
Field Notice: FN72424 Later Versions of WiFi 6 APs Fail to Join WLC - Software Upgrade Required
Field Notice: FN72524 IOS APs stuck in downloading state after 4 Dec 2022 due to Certificate Expired
- Fixed in 8.10.196.0, latest 9800 releases, 8.5.182.12 (8.5.182.13 for 3504) and 8.5.182.109 (IRCM, 8.5.182.111 for 3504)
Field Notice: FN70479 AP Fails to Join or Joins with 1 Radio due to Country Mismatch, RMA needed
How to avoid boot loop due to corrupted image on Wave 2 and Catalyst 11ax Access Points (CSCvx32806)
Field Notice: FN74035 - Wave2 APs DFS May Not Detect Radar After Channel Availability Check Time
Leo's list of bugs affecting 2800/3800/4800/1560 APs
Default AP console baud rate from 17.12.x is 115200 - introduced by CSCwe88390
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2023
01:53 PM
- last edited on
06-07-2023
11:18 PM
by
Translator
![]()
Rich,
Appreciate your help, this is exactly what I was looking for. I had done a slightly different implementation. I had used route-maps with loop back interfaces instead of
nat pools:
!
interface Loopback1
description USED-FOR-NAT-INTERFACE-CUST1
ip address 10.10.1.10 255.255.255.255
!
interface Loopback2
description USED-FOR-NAT-INTERFACE-CUST2
ip address 10.10.2.10 255.255.255.255
!
interface Loopback3
description USED-FOR-NAT-INTERFACE-CUST3
ip address 10.10.3.10 255.255.255.255
!
!
route-map RM-CUST1 permit 10
match ip address ACL-NAT-CUST1
!
route-map RM-CUST2 permit 10
match ip address ACL-NAT-CUST2
!
route-map RM-CUST3 permit 10
match ip address ACL-NAT-CUST3
!
ip nat inside source route-map RM-CUST1 interface Loopback1 overload reversible
ip nat inside source route-map RM-CUST2 interface Loopback2 overload reversible
ip nat inside source route-map RM-CUST3 interface Loopback3 overload reversible
!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2023
01:59 PM
- last edited on
06-07-2023
11:19 PM
by
Translator
![]()
I Dont get it' if you direct traffic to lo1 then you dont need any route-map'
This conditional
NAT
for
multi ISP.
Here I dont see any reason you use it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2023 10:02 AM
sorry dont get what you want here,
there are three VLAN and you need static NAT for these VLAN subnet ?
can you more elaborate ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2023 01:56 PM
MHM,
My requirement was as explained in this article.https://www.ciscozine.com/using-route-maps-for-conditional-nat/
Appreciate your time.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2023
02:15 PM
- last edited on
06-07-2023
11:26 PM
by
Translator
![]()
friend I know exactly what it conditional
NATing
interface Loopback1
description USED-FOR-NAT-INTERFACE-CUST1
ip address 10.10.1.10 255.255.255.255
route-map RM-CUST1 permit 10
match ip address ACL-NAT-CUST1
ip nat
inside source route-map RM-CUST1 interface Loopback1 overload reversible
from OUTside ping to INside using the LO1, here what is idea of using the route-map
route-map using to match egress interface for
multi ISP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2023
02:34 PM
- last edited on
06-07-2023
11:31 PM
by
Translator
![]()
MHM,
I have no doubt on your expertise. In fact, I have a great respect for you because I have benefited from your responses to various posts.
This article explains the different between access-list vs route-map and decided to use route-map based on this article. Even though it was written for ISO 12.x and we are on 15.x and I assume it still applies.
https://www.cisco.com/c/en/us/support/docs/ip/network-address-translation-nat/13739-nat-routemap.html
Three customer sites privately connected to us and wants to use the services hosted on the same server. Because of various reasons (security, overlapping subnets etc...) each customer want us to use customer provided IP address on our server. Instead of configuring multiple IP's on our server, we decided to do the policy
NAT
as you referred as
conditional NAT
.
While I have your attention, I would appreciate your help with following:
What would you recommend, using the loopback interface as I explained above or using the static
natting
as explained in ciscozone above article.
Natting should be work in both directions, server can also initiate a request going towards customers and customer can also initiate request coming in into server.
How many
natting
translations can be supported by this method?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2023
05:03 PM
- last edited on
06-07-2023
11:35 PM
by
Translator
![]()
Whichever way works best for you - if they both work then it's a matter of preference. Some of the
NAT
features (like DNS ALG) can behave differently depending on how it's configured but if you're not relying on any of those then probably doesn't matter.
How many translations? That will depend on platform, IOS version and memory. If it's a hardware based switching platform (like ASR1K for example) then it will depend on TCAM in the FP. Basically check the specs for what you're using and test. Realistically, unless you're planning to have millions of translations you'll probably be ok.
Please click Helpful if this post helped you and Select as Solution (drop down menu at top right of this reply) if this answered your query.
------------------------------
TAC recommended codes for AireOS WLC's and TAC recommended codes for 9800 WLC's
Best Practices for AireOS WLC's, Best Practices for 9800 WLC's and Cisco Wireless compatibility matrix
Check your 9800 WLC config with Wireless Config Analyzer using "show tech wireless" output or "config paging disable" then "show run-config" output on AireOS and use Wireless Debug Analyzer to analyze your WLC client debugs
Field Notice: FN63942 APs and WLCs Fail to Create CAPWAP Connections Due to Certificate Expiration
Field Notice: FN72424 Later Versions of WiFi 6 APs Fail to Join WLC - Software Upgrade Required
Field Notice: FN72524 IOS APs stuck in downloading state after 4 Dec 2022 due to Certificate Expired
- Fixed in 8.10.196.0, latest 9800 releases, 8.5.182.12 (8.5.182.13 for 3504) and 8.5.182.109 (IRCM, 8.5.182.111 for 3504)
Field Notice: FN70479 AP Fails to Join or Joins with 1 Radio due to Country Mismatch, RMA needed
How to avoid boot loop due to corrupted image on Wave 2 and Catalyst 11ax Access Points (CSCvx32806)
Field Notice: FN74035 - Wave2 APs DFS May Not Detect Radar After Channel Availability Check Time
Leo's list of bugs affecting 2800/3800/4800/1560 APs
Default AP console baud rate from 17.12.x is 115200 - introduced by CSCwe88390
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2023 05:08 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-19-2023
09:10 AM
- last edited on
06-07-2023
11:36 PM
by
Translator
![]()
Guys,
Appreciate all the help. One more question. I also have to apply the crypto map to the outside interface lets say gi0/0.10. The crypto map ACL should include the pre-
NATsource IP or post-NAT source IP?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide