- Cisco Community
- Technology and Support
- Networking
- Routing
- i can ping to the gateway of
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-10-2017 11:11 AM - edited 03-05-2019 08:41 AM
I want to block 192.168.3.0 network from reaching network 192.168.2.129 of Router 3
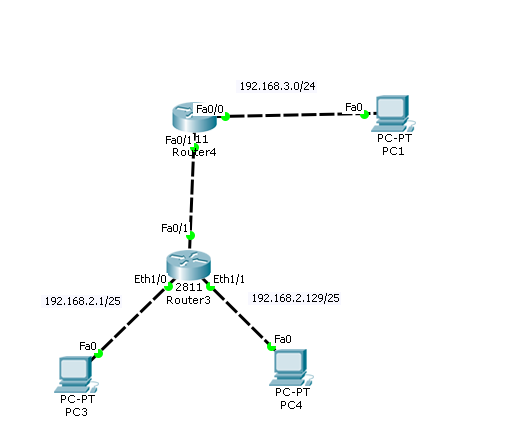
I tried below acl on R3
access-list 51 deny 192.168.3.0 0.0.0.255
access-list 51 permit any
Interface eth1/1 =ip access-group 51 in
still 192.168.3.0 can reach my network. how to solve issue here ?
Solved! Go to Solution.
- Labels:
-
Routing Protocols
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-11-2017 12:51 AM
Hello,
that is the way IOS is designed: an ACL can never block packets generated by the router itself, it can only block packets which transit through the router, not packets generated by the router.
I have uploaded a working pkt (see attachment).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-10-2017 11:42 AM
Hello,
try:
access-list 101 deny ip 192.168.3.0 0.0.0.255 192.168.2.0 0.0.0.127
access-list 101 permit ip any any
and apply the access list 'out':
Interface eth1/1 =ip access-group 101 out
If that doesn't work, post the Packet Tracer file (ZIP it first, otherwise you cannot upload it).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-10-2017 12:11 PM
Is it possible in a standard ACL,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-10-2017 12:16 PM
Hello,
standard ACL should work, try and apply it out:
Interface eth1/1 =ip access-group 51 out
That said, it SHOULD work. Post the zipped .pkt file, there might be something in your configuration that causes problems.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-10-2017 12:21 PM
Standard ACL seems working, but i can ping to the gateway interface of of router R3,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-10-2017 12:24 PM
Hello,
with the standard access list applied out, you can ping from where to where ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-10-2017 12:38 PM
i can ping to the gateway of network 192.168.2.128 in R3 but not to that network. i thought that acl will block everything for that network
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-10-2017 12:58 PM
Hello,
where are you pinging from ?
Your access list blocks access from 192.168.3.0/24 to 192.168.2.128/25, since it is applied to Ethernet1/1.
Post the .pkt file, that will make it easier to explain.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-11-2017 12:51 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-11-2017 12:30 PM
If i want to block reaching to that interface here, Ethernet 1/1 of router R3 can i create another access list for reaching that interface in R3. does that make sense.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-11-2017 02:54 PM
Hello,
to block traffic to Ethernet1/1 on router 3, you would need to configure local policy routing. This would look as following:
ip local policy route-map LOCAL_TRAFFIC_TO_NULL
!
access-list 101 permit ip 192.168.2.128 0.0.0.127 192.168.3.0 0.0.0.255
!
route-map LOCAL_TRAFFIC_TO_NULL permit 10
match ip address 101
set interface Null0
However, Packet Tracer does not support the commands required, if you know and use GNS3, you can try and test it.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide