- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: Lab configuration issues
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-21-2021 02:44 PM
Hi everyone,
I'm a bit of a novice in the Cisco world. Taken courses a while back but never fully involved in day to day network design and configuration. I've been working on building a home lab, and my Internet modem is feeding into a PA-220-Lab unit, which is uplinked to a 3750. My house has a centralized wiring closet with minimal space, so I put in a Ubiquity Unifi managed switch and from there I have my server rack connected to a 3650. As the Ubiquity switch products are finicky, I had to leave the default VLAN as 1 and assign it to the 192.168.1.0/24 network.
In building out the 3750, I wanted it to act as my core/distribution switch and have all routing currently occurring on that device with a few SVIs for WiFi (20), Server (50), MGMT(254). When attempting to access these VLANs on the 3560, it seems to be hit or miss for some reason. I can get connectivity from VLAN 20 and VLAN 50, but nothing from VLAN 1 or MGMT (VLAN 254). Some other areas to note, the uplink from the 3750 to the managed Ubiquity switch is configured as a trunk port as I only have a single port in my office going to the wiring closet. The same is true for the 3650 uplink. Currently, I manage the 3750 by hitting the default gateway of the SVI, and I am not sure how to configure something on the 3650 to allow for SSH or remote management, so everything is done via the console cable. I tried setting an IP on the Loopback interface, but I wasn't sure how to add that entry to a route table on the 3750 since it is technically connected over a trunk link.
As a novice in this area, I am a bit confused as to why VLAN1 and VLAN254 are not working on the 3650. I'm also wondering if I am architecting this incorrectly as the Server devices will be directly attached to the 3650 and it may make more sense to just have the Server VLAN on that device. I do want to ensure any device connected to the 3750 is able to reach the server network though. I would also like to be able to remotely manage the 3650 without the need to plug in to the console port for each change.
Does anyone have any architecture advice or suggestions as to the best way to set up this gear to work with my lab environment in a different room?
Solved! Go to Solution.
- Labels:
-
Catalyst Switch
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-22-2021 02:33 PM
not sure how is your Ubiquity configured: make sure ubiquity should be trunk and passing the VLAN.
https://help.ui.com/hc/en-us/articles/222183968
on 3750 change this and see if that works.
interface GigabitEthernet1/0/2
description Uplink to Ubiquity AP Office
switchport trunk encapsulation dot1q
switchport mode trunk
no spanning-tree portfast
switchport trunk native vlan 1 < -- do this same on 3560 also
=====Preenayamo Vasudevam=====
***** Rate All Helpful Responses *****
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-23-2021 04:39 PM
ip routing
at this, not sure is this cause issue - but let's try 2 options (i will review full config later, any other pointers which causing to work)
if this device is a pure layer to
config t
!
no ip routing
!
end
test it
Options 2, if you looking to use ip routing.
config t
!
ip routing
!
no ip default-gateway 192.168.254.1
ip route 0.0.0.0 0.0.0.0 192.168.254.1
!
end
try the above method and let us know.
still issue
post-show ip route from 3560 ?
=====Preenayamo Vasudevam=====
***** Rate All Helpful Responses *****
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-21-2021 03:08 PM
Thank you for a very Long explanation, it would be nice if you can make a small network diagram for us to understand how these are connneted, from what device (IP) you are not able to reach (what device IP destination) ?
=====Preenayamo Vasudevam=====
***** Rate All Helpful Responses *****
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-21-2021 03:28 PM
Hi BB,
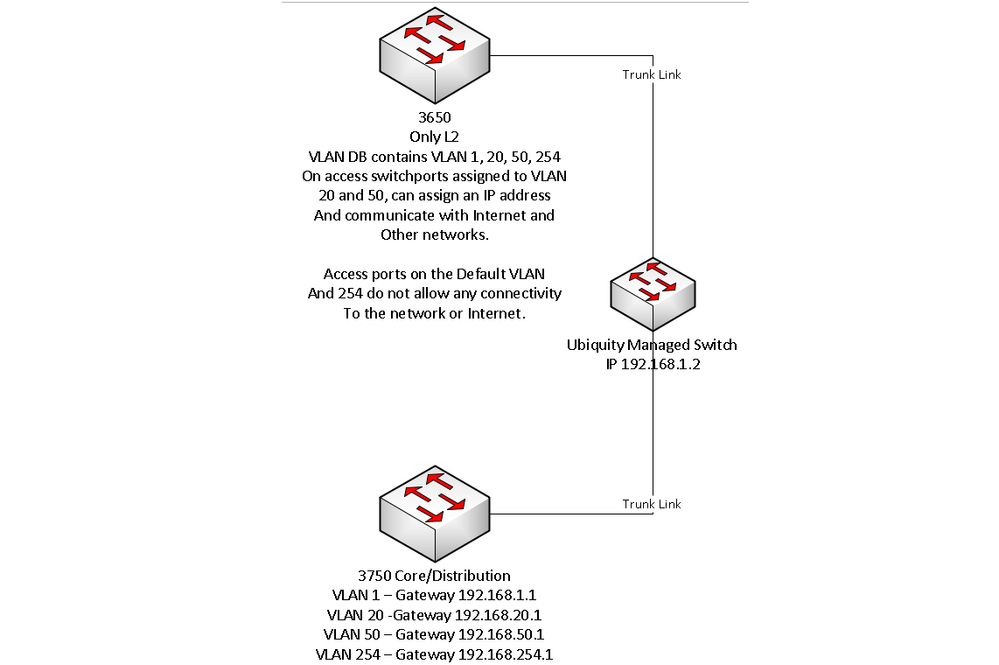
Thank you for the suggestion. Hopefully the image below better illustrates the environment.
Everything functions properly on the 3750...it can speak to all networks as it is handling the SVIs for each. On the 3650 though, if I set a switchport to access VLAN 20 or 50, set the IP address to something within the appropriate network range, I am able to have full network connectivity to any networks and the Internet. If I do the same on the 3650 with the default VLAN or VLAN 254, I have no connectivity if I use an IP within those networks.
I am also not sure about how to setup the 3650 to allow for remote management given its connectivity to the 3750 is over a trunk link. Please let me know if any additional information or config info is needed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-21-2021 04:47 PM
at this stage still not sure what is wrong, can you post the complete config of 3750 ( and you confirmed all VLAN working and getting internet ?)
i was suspecting some routing here..but i can only confirm once we see the config ?
is the ubiquity have all VLANs to pass layer 2?
=====Preenayamo Vasudevam=====
***** Rate All Helpful Responses *****
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-22-2021 10:44 AM
Hello,
Please see the config file from the 3750 below:
Building configuration...
Current configuration : 7941 bytes
!
! Last configuration change at 13:32:42 PDT Sun Jul 11 2021 by admin
! NVRAM config last updated at 13:44:52 PDT Sun Jul 11 2021 by admin
!
version 12.2
no service pad
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname c3750-1
!
boot-start-marker
boot-end-marker
!
!
!
no aaa new-model
clock timezone PST -8
clock summer-time PDT recurring
switch 1 provision ws-c3750x-48
system mtu routing 1500
ip routing
ip dhcp excluded-address 192.168.20.1 192.168.20.19
ip dhcp excluded-address 192.168.1.1 192.168.1.49
ip dhcp excluded-address 192.168.10.1 192.168.10.49
ip dhcp excluded-address 192.168.50.1 192.168.50.10
ip dhcp excluded-address 192.168.50.20 192.168.50.254
!
ip dhcp pool WiFi_VLAN
network 192.168.20.0 255.255.255.0
dns-server 8.8.8.8
default-router 192.168.20.1
lease 2 12
!
ip dhcp pool VPN_VLAN
network 192.168.15.0 255.255.255.0
dns-server 8.8.8.8
!
ip dhcp pool 192.168.1.0/24
network 192.168.1.0 255.255.255.0
dns-server 192.168.1.254 8.8.8.8
default-router 192.168.1.1
!
ip dhcp pool Server_VLAN
network 192.168.50.0 255.255.255.0
dns-server 192.168.1.254 8.8.8.8
default-router 192.168.50.1
!
!
!
!
crypto pki trustpoint TP-self-signed-2309581568
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-2309581568
revocation-check none
rsakeypair TP-self-signed-2309581568
!
!
crypto pki certificate chain TP-self-signed-2309581568
certificate self-signed 01
30820240 308201A9 A0030201 02020101 300D0609 2A864886 F70D0101 04050030
31312F30 2D060355 04031326 494F532D 53656C66 2D536967 6E65642D 43657274
69666963 6174652D 32333039 35383135 3638301E 170D3933 30333031 30303031
32365A17 0D323030 31303130 30303030 305A3031 312F302D 06035504 03132649
4F532D53 656C662D 5369676E 65642D43 65727469 66696361 74652D32 33303935
38313536 3830819F 300D0609 2A864886 F70D0101 01050003 818D0030 81890281
8100A886 E06E769D 834C9AAC 7671395E D82ECBE8 FDE7CEE6 5884E4FF A0B4AD1B
A010A8C3 768E2802 720B6024 62C53F90 9000466A 50140155 1BDA866C A2786802
888B7FC2 1C46BFFE 96FE311F FC1917FD 0CCA7A31 9A768CBD 8D6CAB41 C4AF6918
D9C83526 8435A459 080C3CC9 8348518A 18EB3B46 E8CB05C7 92B9889F 4F30E97B
75CF0203 010001A3 68306630 0F060355 1D130101 FF040530 030101FF 30130603
551D1104 0C300A82 08633337 35302D31 2E301F06 03551D23 04183016 8014B232
57C3A42D 3EB41F2D 6996DE19 85E9DC99 3F85301D 0603551D 0E041604 14B23257
C3A42D3E B41F2D69 96DE1985 E9DC993F 85300D06 092A8648 86F70D01 01040500
03818100 92A6DF49 7DFB02CB D51110D3 8A304C0B 16E0D2DD FC5B990D 4E7F7129
D7CABC35 1B98AAC3 65E4B2F0 590ABB5F 79A57F1E F57E6D08 30B7F65B 12407A8C
525BECBB 3B5C78B7 01F1211F 6A77196A 7563AE02 E44465C5 FABD6BF3 B75F9651
BE6D8FDC 37FAADAD 4C687E59 8D9D8F51 BD9A4DC5 7BB129F9 89D4570F F7FC41A2 AFB10AD5
quit
spanning-tree mode pvst
spanning-tree extend system-id
!
!
!
!
vlan internal allocation policy ascending
!
ip ssh version 2
!
!
interface FastEthernet0
no ip address
no ip route-cache cef
no ip route-cache
no ip mroute-cache
!
interface GigabitEthernet1/0/1
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/2
description Uplink to Ubiquity AP Office
switchport trunk encapsulation dot1q
switchport mode trunk
spanning-tree portfast
!
interface GigabitEthernet1/0/3
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/4
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/5
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/6
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/7
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/8
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/9
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/10
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/11
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/12
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/13
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/14
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/15
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/16
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/17
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/18
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/19
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/20
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/21
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/22
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/23
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/24
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/25
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/26
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/27
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/28
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/29
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/30
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/31
!
interface GigabitEthernet1/0/32
!
interface GigabitEthernet1/0/33
!
interface GigabitEthernet1/0/34
!
interface GigabitEthernet1/0/35
!
interface GigabitEthernet1/0/36
!
interface GigabitEthernet1/0/37
switchport access vlan 10
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/38
!
interface GigabitEthernet1/0/39
!
interface GigabitEthernet1/0/40
!
interface GigabitEthernet1/0/41
!
interface GigabitEthernet1/0/42
!
interface GigabitEthernet1/0/43
switchport access vlan 10
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/44
description description Uplink to PA-220-01 Inside Gi1/2 192.168.5.5
no switchport
ip address 192.168.5.6 255.255.255.252
!
interface GigabitEthernet1/0/45
description Uplink to PA-220-01 MGMT Port
switchport access vlan 254
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/46
description Uplink to 5512 Inside gi0/1
no switchport
ip address 192.168.5.2 255.255.255.252
!
interface GigabitEthernet1/0/47
description Uplink to 3560 gi0/47
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet1/0/48
description Connected to 5512 gi0/2 Trunked for DMZ VLAN 172
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet1/1/1
!
interface GigabitEthernet1/1/2
!
interface GigabitEthernet1/1/3
!
interface GigabitEthernet1/1/4
!
interface TenGigabitEthernet1/1/1
!
interface TenGigabitEthernet1/1/2
!
interface Vlan1
ip address 192.168.1.1 255.255.255.0
!
interface Vlan15
description VPN VLAN
ip address 192.168.15.1 255.255.255.0
!
interface Vlan20
description WiFi Network
ip address 192.168.20.1 255.255.255.0
!
interface Vlan50
description Server Network
ip address 192.168.50.1 255.255.255.0
!
interface Vlan254
description MGMT Network
ip address 192.168.254.1 255.255.255.0
!
ip classless
ip route 0.0.0.0 0.0.0.0 192.168.5.5
ip route 172.16.0.0 255.255.255.0 172.16.0.1
ip http server
ip http secure-server
!
ip sla enable reaction-alerts
!
!
!
ntp clock-period 36027668
ntp server 216.239.35.0
end
I confirmed connectivity on all VLANs on the 3750 with a PC by using the default vlan as well as changing the access vlan to 20, 50, and 254. When setting to 254 I manually configured an IP address in that network. All VLANs were successful on the 3750 in getting out to the Internet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-22-2021 02:33 PM
not sure how is your Ubiquity configured: make sure ubiquity should be trunk and passing the VLAN.
https://help.ui.com/hc/en-us/articles/222183968
on 3750 change this and see if that works.
interface GigabitEthernet1/0/2
description Uplink to Ubiquity AP Office
switchport trunk encapsulation dot1q
switchport mode trunk
no spanning-tree portfast
switchport trunk native vlan 1 < -- do this same on 3560 also
=====Preenayamo Vasudevam=====
***** Rate All Helpful Responses *****
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-22-2021 03:52 PM
Hi BB,
Thank you for the suggestions...indeed the issues revolved around changes I had made on the Ubiquity switch. I had run into issues previously and tried to create a new profile allowing me to set the native VLAN to 10 and pass everything else over the trunk tagged. I had that profile attached still to the port serving the 3650 which likely prevented VLAN 1 from working correctly. I also realized I never input information about VLAN 254 in the Ubiquity config. After doing those two things all of the VLANs are passing traffic properly.
The last piece of my puzzle would be to enable remote management of the 3650. If you have any ideas as to how to set that up I would really appreciate it.
Thank you again for all of your help!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-23-2021 03:12 AM - edited 07-23-2021 03:12 AM
Glad to know suggestion helped to fix your issue .
The last piece of my puzzle would be to enable remote management of the 3650. If you have any ideas as to how to set that up I would really appreciate it.
if you like to have management on 3650
interface Vlan254
description MGMT Network
ip address 192.168.254.X 255.255.255.0 ( X is the free IP address in that subnet)
!
ip default-gateway 192.168.254.1
above should work, if not psot show run from 3650
=====Preenayamo Vasudevam=====
***** Rate All Helpful Responses *****
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-23-2021 09:46 AM
Hi BB,
Thank you for the continued support. Unfortunately making the suggested changes on the 3650 did not result in connectivity. When I configured a port on VLAN 254 and plugged in my laptop to that and assigned it an IP in that network, I could ping the address I set for the interface VLAN 254 (192.168.254.3) on the 3650, however, if I went back to a port on the default VLAN I was unable to ping that address.
The strange thing is from the 3750 I can ping 192.168.254.3; however, from a device on the 3750 also on VLAN 1 I am not able to ping it. From the same device on VLAN 1 on the 3750 I can ping 192.168.254.1 and 192.168.254.2 (the management port of the PA-220) which is directly connected to a port on the 3750. From the laptop on VLAN 1 connected to the 3650, it can also ping 192.168.254.1 and 192.168.254.2, but not 192.168.254.3
Below is the config from the 3650
=~=~=~=~=~=~=~=~=~=~=~= PuTTY log 2021.07.23 09:34:06 =~=~=~=~=~=~=~=~=~=~=~=
sho run
Building configuration...
Current configuration : 6665 bytes
!
version 12.2
no service pad
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname c3650-1
!
boot-start-marker
boot-end-marker
!
!
!
!
no aaa new-model
system mtu routing 1500
authentication mac-move permit
ip subnet-zero
ip routing
!
!
!
!
crypto pki trustpoint TP-self-signed-3493968256
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-3493968256
revocation-check none
rsakeypair TP-self-signed-3493968256
!
!
crypto pki certificate chain TP-self-signed-3493968256
certificate self-signed 01
30820240 308201A9 A0030201 02020101 300D0609 2A864886 F70D0101 04050030
31312F30 2D060355 04031326 494F532D 53656C66 2D536967 6E65642D 43657274
69666963 6174652D 33343933 39363832 3536301E 170D3933 30333031 30303031
33345A17 0D323030 31303130 30303030 305A3031 312F302D 06035504 03132649
4F532D53 656C662D 5369676E 65642D43 65727469 66696361 74652D33 34393339
36383235 3630819F 300D0609 2A864886 F70D0101 01050003 818D0030 81890281
8100BF38 F9AEFB09 80072880 A8DF479D 3C80B3E5 122698D7 E9C4ABFA DFF899F6
11E57ABE 8C7D8ADF 9D6DB3D9 92705759 3D2F768B B0C9B1EE 09C25E87 4E99BF02
3F09C2B2 1A8E5F10 0C972544 EF1E4E0D 1CEC709E 20377119 B7E4C55C 579A6C8B
6C3EB118 3BF9293E DB83DFCE 79D4866A D5103D6B 9043871D 1DF5FAFC 9246D5B4
7FA30203 010001A3 68306630 0F060355 1D130101 FF040530 030101FF 30130603
551D1104 0C300A82 08633336 35302D31 2E301F06 03551D23 04183016 8014A8B4
DA939B67 47A678B3 B5746930 F8CBE63D A8B2301D 0603551D 0E041604 14A8B4DA
939B6747 A678B3B5 746930F8 CBE63DA8 B2300D06 092A8648 86F70D01 01040500
03818100 BE3593CA 87057CD4 68077D25 75A11287 E05BAA07 36A7A7AC 32CEF083
09111F09 7B04E356 5A0DFA71 4C82DB8F 2BE99BA4 4F7D0FEF C605DA6D C491CDA8
2EB66EC6 EA6286CB 37AC1CC9 6C4C8A61 0860658E C0C8B9E5 F10F57B3 6AEE973B
B000224C 2DCD0308 5A0F82D8 6AF6AD22 DF4FA172 259685A3 BED47A9C B5127873 58D17602
quit
spanning-tree mode pvst
spanning-tree etherchannel guard misconfig
spanning-tree extend system-id
!
!
!
!
vlan internal allocation policy ascending
!
!
!
interface FastEthernet0
no ip address
no ip route-cache cef
no ip route-cache
no ip mroute-cache
shutdown
!
interface GigabitEthernet0/1
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet0/2
switchport access vlan 50
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet0/3
switchport access vlan 20
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet0/4
switchport access vlan 50
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet0/5
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet0/6
!
interface GigabitEthernet0/7
switchport access vlan 254
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet0/8
!
interface GigabitEthernet0/9
!
interface GigabitEthernet0/10
!
interface GigabitEthernet0/11
!
interface GigabitEthernet0/12
!
interface GigabitEthernet0/13
!
interface GigabitEthernet0/14
!
interface GigabitEthernet0/15
!
interface GigabitEthernet0/16
!
interface GigabitEthernet0/17
!
interface GigabitEthernet0/18
!
interface GigabitEthernet0/19
!
interface GigabitEthernet0/20
!
interface GigabitEthernet0/21
!
interface GigabitEthernet0/22
!
interface GigabitEthernet0/23
!
interface GigabitEthernet0/24
!
interface GigabitEthernet0/25
description Trunk Port
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet0/26
description Trunk Port
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet0/27
description Trunk Port
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet0/28
description Trunk Port
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet0/29
description Trunk Port
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet0/30
description Trunk Port
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet0/31
description Trunk Port
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet0/32
description Trunk Port
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet0/33
description Trunk Port
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet0/34
description Trunk Port
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet0/35
description Trunk Port
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet0/36
description Trunk Port
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet0/37
description Trunk Port
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet0/38
description Trunk Port
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet0/39
description Trunk Port
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet0/40
description Trunk Port
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet0/41
description Trunk Port
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet0/42
description Trunk Port
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet0/43
description Trunk Port
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet0/44
description Trunk Port
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet0/45
description Trunk Port
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet0/46
description Trunk Port
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet0/47
description Uplink to 3750 gi1/0/47
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet0/48
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet1/1
!
interface GigabitEthernet1/2
!
interface GigabitEthernet1/3
!
interface GigabitEthernet1/4
!
interface TenGigabitEthernet1/1
!
interface TenGigabitEthernet1/2
!
interface Vlan1
no ip address
shutdown
!
interface Vlan254
description MGMT Network
ip address 192.168.254.3 255.255.255.0
!
ip default-gateway 192.168.254.1
ip classless
ip http server
ip http secure-server
!
ip sla enable reaction-alerts
!
!
line con 0
line vty 0 4
login
line vty 5 15
login
!
end
c3650-1#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-23-2021 04:39 PM
ip routing
at this, not sure is this cause issue - but let's try 2 options (i will review full config later, any other pointers which causing to work)
if this device is a pure layer to
config t
!
no ip routing
!
end
test it
Options 2, if you looking to use ip routing.
config t
!
ip routing
!
no ip default-gateway 192.168.254.1
ip route 0.0.0.0 0.0.0.0 192.168.254.1
!
end
try the above method and let us know.
still issue
post-show ip route from 3560 ?
=====Preenayamo Vasudevam=====
***** Rate All Helpful Responses *****
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-23-2021 08:03 PM
All looks good! Thank you so much for all of the help!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-24-2021 02:09 AM
Cheers ! for the feedback. nice to know all working as expecting.
=====Preenayamo Vasudevam=====
***** Rate All Helpful Responses *****
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide