- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: PAT interfers with Web Server Access over L2 tunnel (thought that is was solved)
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2019 01:32 PM - edited 03-05-2019 11:09 AM
I posted this already but my mistake, it is not solved.
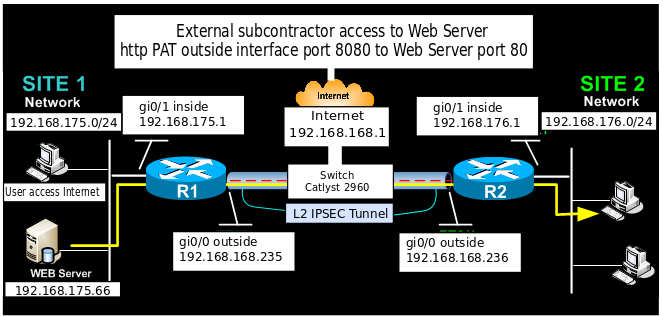
I'm working on a network to accomplish 3 things:
1) NAT overload to the internet
2) L2 tunnels to remote users
3) PAT subcontractors to the Web server on the outside interface with port mapping
PROBLEM STATEMENT
Everything is working except the PAT (ip nat inside source static tcp 192.168.175.66 80 interface GigabitEthernet0/0 8080) stops the remote user (over the L2 tunnel) from accessing the web server. If I remove t he PAT, Web access for the remote user is good. See the tcpdump on the Web Server showing http coming in but not getting out (note length 0 shows that the hand-shake fails).
QUESTION
How can I change to PAT to allow normal access to the Web Server over L2.
This is the test configuration I'm using to simulate the WAN. Attached are the two configurations and the tcpdump.
Solved! Go to Solution.
- Labels:
-
vEdge Routers
-
WAN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2019 10:15 AM
Hello
yes I am -
however change your nat access list to allow the nat subnet don’t use any any also
for testing purposes remove that ingress acl on the rtrs wan interface
lastly your web server is open on port 80 but your trying to connect via the static nat statement on port 8080 can you change this so they both are the same
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2019 01:35 PM
Hello,
I had already posted this but deleted it after seeing that the problem was apparently solved. Either way, try this:
Replace:
ip nat inside source static tcp 192.168.175.66 80 interface GigabitEthernet0/0 8080
with
ip nat inside source static tcp 192.168.175.66 80 192.168.168.235 8080 extendable
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2019 05:12 AM - edited 01-07-2019 06:22 AM
Hi Georg, Thanks for your help, it didn't work. I changed to (((ip nat inside source static tcp 192.168.175.66 80 192.168.168.235 8080 extendable))) but I still can't browse from the other end of the tunnel. If I remove the PAT it works... And what is this from nat translations (((tcp 192.168.168.235:8080 192.168.175.66:80 --- ---))) it looks suspicious????
localrtr#sh ip nat translations
Pro Inside global Inside local Outside local Outside global
tcp 192.168.168.235:8080 192.168.175.66:80 192.168.168.140:45062 192.168.168.140:45062
tcp 192.168.168.235:8080 192.168.175.66:80 192.168.168.140:45064 192.168.168.140:45064
tcp 192.168.168.235:8080 192.168.175.66:80 192.168.176.3:49304 192.168.176.3:49304 <--------- Client Browser
tcp 192.168.168.235:8080 192.168.175.66:80 192.168.176.3:49305 192.168.176.3:49305
tcp 192.168.168.235:8080 192.168.175.66:80 --- ---
udp 192.168.168.235:33696 192.168.175.66:33696 192.168.168.1:53 192.168.168.1:53
udp 192.168.168.235:36444 192.168.175.66:36444 192.168.168.1:53 192.168.168.1:53
udp 192.168.168.235:38106 192.168.175.66:38106 192.168.168.1:53 192.168.168.1:53
udp 192.168.168.235:42617 192.168.175.66:42617 192.168.168.1:53 192.168.168.1:53
udp 192.168.168.235:52788 192.168.175.66:52788 192.168.168.1:53 192.168.168.1:53
udp 192.168.168.235:53998 192.168.175.66:53998 192.168.168.1:53 192.168.168.1:53
localrtr#
localrtr#
localrtr#sh run | i ip nat
ip nat inside source list 100 interface GigabitEthernet0/0 overload
ip nat inside source static tcp 192.168.175.66 80 192.168.168.235 8080 extendable
localrtr#
!
interface GigabitEthernet0/0
description OUTSIDE
ip address 192.168.168.235 255.255.255.0
ip access-group REMOTE_OUTSIDE_IN_ACL in
ip nat outside
crypto map CMAP
!
interface GigabitEthernet0/1
description INSIDE
ip address 192.168.175.1 255.255.255.0
ip nat inside
!
crypto isakmp policy 1
encr 3des
hash md5
authentication pre-share
group 2
crypto isakmp key firewallcx address 192.168.168.236
!
crypto ipsec transform-set TS esp-3des esp-md5-hmac
mode tunnel
!
crypto map CMAP 10 ipsec-isakmp
set peer 192.168.168.236
set transform-set TS
match address VPN_TRAFFIC
!
localrtr#sh ip access-lists
Extended IP access list 100
10 deny ip 192.168.175.0 0.0.0.255 192.168.176.0 0.0.0.255 (484 matches)
20 permit ip 192.168.175.0 0.0.0.255 any (20656 matches)
Extended IP access list REMOTE_OUTSIDE_IN_ACL
10 permit tcp host 192.168.168.140 host 192.168.168.235 eq 8080 (223 matches)
20 deny tcp any host 192.168.168.235 eq 8080 (560 matches)
30 deny udp any host 192.168.168.235 eq 8080
40 permit ip any any (825837 matches)
Extended IP access list VPN_TRAFFIC
5 permit tcp 192.168.175.0 0.0.0.255 192.168.176.0 0.0.0.255 (345 matches)
10 permit ip 192.168.175.0 0.0.0.255 192.168.176.0 0.0.0.255 (128 matches)
localrtr#
-------------========TCP DUMP http can't get back to the client=======---------------------
[root@apache myuser]#
[root@apache myuser]#
[root@apache myuser]# tcpdump -i enp0s3 | grep 192.168.176
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on enp0s3, link-type EN10MB (Ethernet), capture size 262144 bytes
07:48:13.464392 IP 192.168.176.3.49304 > apache.myco.com.http: Flags [S], seq 2932346125, win 8192, options [mss 1460,nop,wscale 2,nop,nop,sackOK], length 0
07:48:13.464496 IP apache.myco.com.http > 192.168.176.3.49304: Flags [S.], seq 4211489711, ack 2932346126, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
07:48:13.720489 IP 192.168.176.3.49305 > apache.myco.com.http: Flags [S], seq 3727124658, win 8192, options [mss 1460,nop,wscale 2,nop,nop,sackOK], length 0
07:48:13.720567 IP apache.myco.com.http > 192.168.176.3.49305: Flags [S.], seq 768665342, ack 3727124659, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
07:48:14.673224 IP apache.myco.com.http > 192.168.176.3.49304: Flags [S.], seq 4211489711, ack 2932346126, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
07:48:15.073290 IP apache.myco.com.http > 192.168.176.3.49305: Flags [S.], seq 768665342, ack 3727124659, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
07:48:16.465079 IP 192.168.176.3.49304 > apache.myco.com.http: Flags [S], seq 2932346125, win 8192, options [mss 1460,nop,wscale 2,nop,nop,sackOK], length 0
07:48:16.465151 IP apache.myco.com.http > 192.168.176.3.49304: Flags [S.], seq 4211489711, ack 2932346126, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
07:48:16.730187 IP 192.168.176.3.49305 > apache.myco.com.http: Flags [S], seq 3727124658, win 8192, options [mss 1460,nop,wscale 2,nop,nop,sackOK], length 0
07:48:16.730244 IP apache.myco.com.http > 192.168.176.3.49305: Flags [S.], seq 768665342, ack 3727124659, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
07:48:18.677095 IP apache.myco.com.http > 192.168.176.3.49304: Flags [S.], seq 4211489711, ack 2932346126, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
07:48:19.084050 IP apache.myco.com.http > 192.168.176.3.49305: Flags [S.], seq 768665342, ack 3727124659, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
07:48:21.164092 IP apache.myco.com.47256 > 192.168.176.66.http: Flags [S], seq 3607212259, win 29200, options [mss 1460,sackOK,TS val 334722438 ecr 0,nop,wscale 7], length 0
07:48:21.349101 IP apache.myco.com.47258 > 192.168.176.66.http: Flags [S], seq 1758793583, win 29200, options [mss 1460,sackOK,TS val 334722624 ecr 0,nop,wscale 7], length 0
07:48:22.471386 IP 192.168.176.3.49304 > apache.myco.com.http: Flags [S], seq 2932346125, win 8192, options [mss 1460,nop,nop,sackOK], length 0
07:48:22.471464 IP apache.myco.com.http > 192.168.176.3.49304: Flags [S.], seq 4211489711, ack 2932346126, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
07:48:22.736315 IP 192.168.176.3.49305 > apache.myco.com.http: Flags [S], seq 3727124658, win 8192, options [mss 1460,nop,nop,sackOK], length 0
07:48:22.736372 IP apache.myco.com.http > 192.168.176.3.49305: Flags [S.], seq 768665342, ack 3727124659, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
07:48:26.723182 IP apache.myco.com.http > 192.168.176.3.49304: Flags [S.], seq 4211489711, ack 2932346126, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
07:48:27.124027 IP apache.myco.com.http > 192.168.176.3.49305: Flags [S.], seq 768665342, ack 3727124659, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
07:48:34.743275 IP apache.myco.com.http > 192.168.176.3.49304: Flags [S.], seq 4211489711, ack 2932346126, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
07:48:35.143317 IP apache.myco.com.http > 192.168.176.3.49305: Flags [S.], seq 768665342, ack 3727124659, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
07:48:44.937456 IP 192.168.176.3.49306 > apache.myco.com.http: Flags [S], seq 4239052407, win 8192, options [mss 1460,nop,wscale 2,nop,nop,sackOK], length 0
07:48:44.937599 IP apache.myco.com.http > 192.168.176.3.49306: Flags [S.], seq 2977885853, ack 4239052408, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
07:48:45.201477 IP 192.168.176.3.49307 > apache.myco.com.http: Flags [S], seq 1495742835, win 8192, options [mss 1460,nop,wscale 2,nop,nop,sackOK], length 0
07:48:45.201588 IP apache.myco.com.http > 192.168.176.3.49307: Flags [S.], seq 3459673006, ack 1495742836, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
07:48:46.173175 IP apache.myco.com.http > 192.168.176.3.49306: Flags [S.], seq 2977885853, ack 4239052408, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
07:48:46.773159 IP apache.myco.com.http > 192.168.176.3.49307: Flags [S.], seq 3459673006, ack 1495742836, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
07:48:47.946554 IP 192.168.176.3.49306 > apache.myco.com.http: Flags [S], seq 4239052407, win 8192, options [mss 1460,nop,wscale 2,nop,nop,sackOK], length 0
07:48:47.946644 IP apache.myco.com.http > 192.168.176.3.49306: Flags [S.], seq 2977885853, ack 4239052408, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
07:48:48.211829 IP 192.168.176.3.49307 > apache.myco.com.http: Flags [S], seq 1495742835, win 8192, options [mss 1460,nop,wscale 2,nop,nop,sackOK], length 0
07:48:48.211951 IP apache.myco.com.http > 192.168.176.3.49307: Flags [S.], seq 3459673006, ack 1495742836, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
07:48:50.174761 IP apache.myco.com.http > 192.168.176.3.49306: Flags [S.], seq 2977885853, ack 4239052408, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
07:48:50.783119 IP apache.myco.com.http > 192.168.176.3.49307: Flags [S.], seq 3459673006, ack 1495742836, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
07:48:50.783201 IP apache.myco.com.http > 192.168.176.3.49304: Flags [S.], seq 4211489711, ack 2932346126, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
07:48:51.393981 IP apache.myco.com.http > 192.168.176.3.49305: Flags [S.], seq 768665342, ack 3727124659, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
07:48:53.952860 IP 192.168.176.3.49306 > apache.myco.com.http: Flags [S], seq 4239052407, win 8192, options [mss 1460,nop,nop,sackOK], length 0
07:48:53.953011 IP apache.myco.com.http > 192.168.176.3.49306: Flags [S.], seq 2977885853, ack 4239052408, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
07:48:54.218054 IP 192.168.176.3.49307 > apache.myco.com.http: Flags [S], seq 1495742835, win 8192, options [mss 1460,nop,nop,sackOK], length 0
07:48:54.218191 IP apache.myco.com.http > 192.168.176.3.49307: Flags [S.], seq 3459673006, ack 1495742836, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
07:48:58.465896 IP apache.myco.com.http > 192.168.176.3.49307: Flags [S.], seq 3459673006, ack 1495742836, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
07:48:58.466008 IP apache.myco.com.http > 192.168.176.3.49306: Flags [S.], seq 2977885853, ack 4239052408, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
07:49:06.523947 IP apache.myco.com.http > 192.168.176.3.49307: Flags [S.], seq 3459673006, ack 1495742836, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
07:49:06.524066 IP apache.myco.com.http > 192.168.176.3.49306: Flags [S.], seq 2977885853, ack 4239052408, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
07:49:22.633963 IP apache.myco.com.http > 192.168.176.3.49307: Flags [S.], seq 3459673006, ack 1495742836, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
07:49:22.634087 IP apache.myco.com.http > 192.168.176.3.49306: Flags [S.], seq 2977885853, ack 4239052408, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
[root@apache myuser]#
[root@apache myuser]#
[root@apache myuser]#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2019 06:22 AM
Just ran a test with FTP. Stood-up a VSFTP VM on the inside and tested with and without the PAT.
Somehow to PAT interferes with the service when accessing it from the remote end of the tunnel....
=======================RTR FTP PAT ==============================
ip nat inside source static tcp 192.168.175.67 21 192.168.168.235 2121 extendable
=======================FTP from OUTSIDE 192.168.168.140 to FTP 2121===============
allan@allandesk ~ $ ftp 192.168.168.235 2121
Connected to 192.168.168.235.
220 (vsFTPd 3.0.2)
Name (192.168.168.235:allan): myuser
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 180 Jan 07 13:22 GOODBYE
226 Directory send OK.
ftp> quit
221 Goodbye.
allan@allandesk ~ $
=============FTP REMOTE PEER L2 TUNNEL CLIENT 192.168.176.4===========
------------WITH PORT 2121 PAT-------------------
[root@vsftp myuser]# cat vsftp_test_client.txt
vmuser@studio1:~$ ping 192.168.175.67
PING 192.168.175.67 (192.168.175.67) 56(84) bytes of data.
64 bytes from 192.168.175.67: icmp_seq=1 ttl=62 time=1.87 ms
64 bytes from 192.168.175.67: icmp_seq=2 ttl=62 time=2.00 ms
^C
--- 192.168.175.67 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1001ms
rtt min/avg/max/mdev = 1.872/1.937/2.003/0.078 ms
vmuser@studio1:~$ ftp 192.168.175.67
ftp: connect: Connection timed out
ftp> quit
------------WITHOUT PORT 2121 PAT-------------------
vmuser@studio1:~$ ftp 192.168.175.67
Connected to 192.168.175.67.
220 (vsFTPd 3.0.2)
Name (192.168.175.67:vmuser): myuser
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 180 Jan 07 13:22 GOODBYE
226 Directory send OK.
ftp>
ftp>
[root@vsftp myuser]#
=========FTP SERVER TCPDUMP with PAT in place CAN"T GAT BACK TO CLIENT==============
[root@vsftp myuser]# tcpdump -i enp0s3 | grep 192.168.176
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on enp0s3, link-type EN10MB (Ethernet), capture size 262144 bytes
08:31:47.718995 IP 192.168.176.4.45840 > vsftp.myco.com.ftp: Flags [S], seq 2453901311, win 29200, options [mss 1460,sackOK,TS val 375867575 ecr 0,nop,wscale 7], length 0
08:31:47.719073 IP vsftp.myco.com.ftp > 192.168.176.4.45840: Flags [S.], seq 3854527014, ack 2453901312, win 28960, options [mss 1460,sackOK,TS val 247128637 ecr 375867575,nop,wscale 7], length 0
08:31:47.720619 IP 192.168.176.4.45840 > vsftp.myco.com.ftp: Flags [R], seq 2453901312, win 0, length 0
08:31:48.741748 IP 192.168.176.4.45840 > vsftp.myco.com.ftp: Flags [S], seq 2453901311, win 29200, options [mss 1460,sackOK,TS val 375868598 ecr 0,nop,wscale 7], length 0
08:31:48.741821 IP vsftp.myco.com.ftp > 192.168.176.4.45840: Flags [S.], seq 3870507508, ack 2453901312, win 28960, options [mss 1460,sackOK,TS val 247129660 ecr 375868598,nop,wscale 7], length 0
08:31:48.743352 IP 192.168.176.4.45840 > vsftp.myco.com.ftp: Flags [R], seq 2453901312, win 0, length 0
08:31:50.757743 IP 192.168.176.4.45840 > vsftp.myco.com.ftp: Flags [S], seq 2453901311, win 29200, options [mss 1460,sackOK,TS val 375870614 ecr 0,nop,wscale 7], length 0
08:31:50.757816 IP vsftp.myco.com.ftp > 192.168.176.4.45840: Flags [S.], seq 3902007417, ack 2453901312, win 28960, options [mss 1460,sackOK,TS val 247131676 ecr 375870614,nop,wscale 7], length 0
08:31:50.759234 IP 192.168.176.4.45840 > vsftp.myco.com.ftp: Flags [R], seq 2453901312, win 0, length 0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2019 06:28 AM
Will this problem persist if I change to an L3 tunnel?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2019 06:49 AM - edited 01-07-2019 07:25 AM
I tried this but it the PAT still interferes with the FTP service from the L2 tunnel. Just a wild guess....
ip nat inside source static tcp 192.168.175.67 21 192.168.168.235 2121 extendable no-alias no-payload
Funny thing is that if I put to Web Server on the distant end of the L2 tunnel and keep the PAT in place, the inside network can browse the that Web server. Two way http communucation works if the Web Serve is on the other end. It's like the PAT won't let the inside Web Server set up a session.... Oh it is maybe not letting the inside Web Server setup the http session handshake when it get to the rendez-vous at a high port number.
This is what it looks like from the inside Web Server when it browses to the Web Server at the L2 distant end.
myuser@apache ~ $ netstat -n | grep -i estab
tcp 0 0 192.168.175.66:38668 192.168.176.66:80 ESTABLISHED
tcp 0 0 192.168.175.66:38664 192.168.176.66:80 ESTABLISHED
tcp 0 0 192.168.175.66:38666 192.168.176.66:80 ESTABLISHED
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2019 07:12 AM
Hello,
just for clarification, what is the IP address of the remote users ? It must be on the 192.168.176.0/24 subnet...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2019 07:54 AM
Yes the other end of the L2 Tunnel is 192.168.176.0/24. The external Internet access for the PAT is simulated with our local office network 192.168.168.0/24. I know that the Port Mapping is insecure but it's legacy. I'm trying to get rid of it.... But right now I have to keep it around.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2019 07:35 AM - edited 01-07-2019 07:37 AM
Hello
Given that you are using ipsec and also the nat order of preference regards inside/outside nat
Suggest instead to use domain-less nat and try again.
interface GigabitEthernet0/0
no ip nat outside
ip nat enable
interface GigabitEthernet0/1
no ip nat inside
ip nat enable
ip nat source list 100 interface GigabitEthernet0/0 overload
ip nat source static tcp 192.168.175.66 xx interface GigabitEthernet0/0 xx
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2019 07:56 AM - edited 01-07-2019 09:35 AM
Skip me
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2019 08:10 AM - edited 01-07-2019 08:22 AM
Hello
clyde.a.huffman.ctr@mail.mil wrote:
Already tried that and the same thing happens.
ip nat
insidesource list 100 interface GigabitEthernet0/0 overload
ip natinsidesource static tcp 192.168.175.66 80 interface GigabitEthernet0/0 8080
ip route 0.0.0.0 0.0.0.0 192.168.168.1
ip route 192.168.176.0 255.255.255.0 192.168.168.236
!
Not Domain-Based nat ( ip inside/outside) but Domain-less NAT ( ip nat enable)
Also i can see you have an acl ingress on you wan facing interface for that rtr allowing only port tcp 8080, so you need to make sure these two hosts are correctly communicating on this port only.
ip access-list extended REMOTE_OUTSIDE_IN_ACL
permit tcp host 192.168.168.140 host 192.168.168.235 eq 8080
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2019 09:02 AM - edited 01-07-2019 10:06 AM
Hi Paul, sorry that I missed your recommendation the first time :-/
Just changing to Not Domain_based did not work. Both the overload and PAT failed.
- ip nat inside source list 100 interface GigabitEthernet0/0 overload
- ip nat inside source static tcp 192.168.175.66 80 interface GigabitEthernet0/0 8080
Are you saying that I should use a virtual interface on VLAN 175 (using vlan 175 on the inside switch) like this?
!
interface GigabitEthernet0/0
description OUTSIDE
ip address 192.168.168.235 255.255.255.0
ip nat enable
!
interface GigabitEthernet0/1
description INSIDE
no ip address
ip nat enable
!
interface GigabitEthernet0/1.175
description INSIDE_175
encapsulation dot1Q 175
ip address 192.168.175.1 255.255.255.0
ip nat enable
!
ip nat source list 175 interface GigabitEthernet0/0 overload
ip nat source static tcp 192.168.175.66 80 interface GigabitEthernet0/0 8080
ip route 0.0.0.0 0.0.0.0 GigabitEthernet0/0 192.168.168.1
!
access-list 175 permit any
!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2019 10:15 AM
Hello
yes I am -
however change your nat access list to allow the nat subnet don’t use any any also
for testing purposes remove that ingress acl on the rtrs wan interface
lastly your web server is open on port 80 but your trying to connect via the static nat statement on port 8080 can you change this so they both are the same
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2019 11:30 AM - edited 01-07-2019 01:30 PM
Hi Paul, got ping on the inside to work. Had to remove sw tr native 175
Still working on the NAT on gi0/1.175
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2019 12:52 PM
Hello
How come the topology has change since your OP ?
You now have sub-interfaces, Not so sure what/why this has change when everything was working apart from the PAT/NAT towards you web server?
FYI -Your switch should be acting as host switch, no routing should be on it, Would you be able to post the config of the following please:
Rtr1/Rtr 2 and switch
FYI - I was able to quickly lab this up and I have it working , so i am assuming there is some mis-configuration with your set-up.
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide