- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: Performance Xconnect with l2tp over wan
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-05-2023 08:05 AM
Hi, I have two isr4331 with isp channel about 300 mbit, and I needed to connect two vlans, I decided to use xconnect over l2tpv3 with ipsec and after configuring and testing I noticed that with 100 mbit traffic qfp = 70-80%, is it normal for xconnect? Because via dmvpn/flexvpn between them with the same ipsec policy for 100 mbit performance qfp = about 30% Maybe xconnect isn't optimize?
Solved! Go to Solution.
- Labels:
-
ISR 4000 Series
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-06-2023 05:51 AM
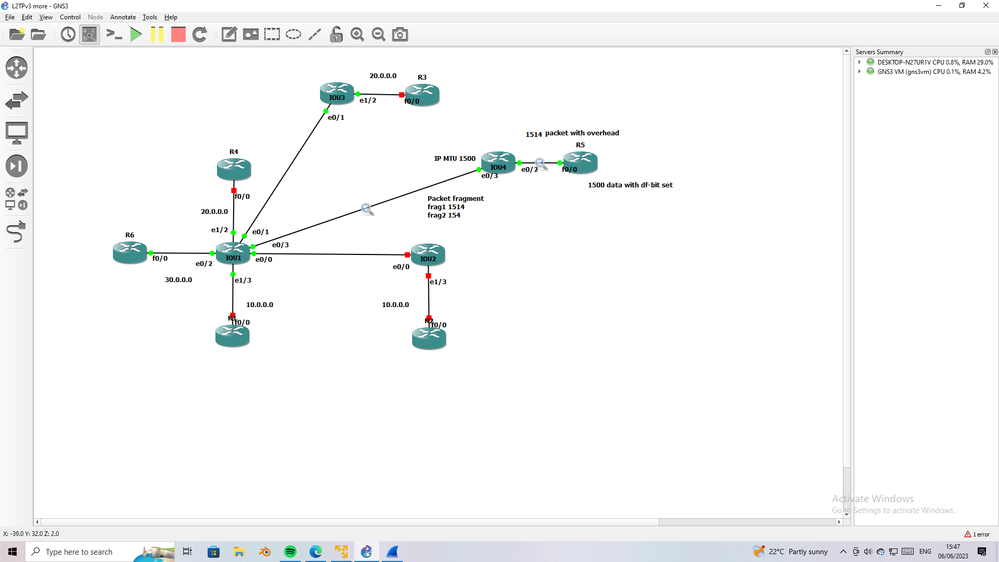
ping from R5 to R6 though l2tpv3 over VTI (protect by IPsec) the traffic frag and second fragment is big 154 (- new IP header 20)
so the traffic of 1500 is overhead with around 145 bytes.
hope this info. help you
thanks
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-05-2023 08:31 AM - edited 06-05-2023 08:38 AM
I recall xconnect can suffer from fragmentation. That might account for some of the throughput reduction.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-05-2023
08:48 AM
- last edited on
06-07-2023
03:12 AM
by
Translator
![]()
On the transport tunnel I have
ip mtu
1400 and
tcp adjust mss
1360, actual
mtu for this tunnel 1454 (sh int tunnel 100 | i mtu), over wan
mtu= 1500
without fragmentation. What do you think? Maybe gre will be more useful?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-05-2023 11:08 AM
If you can use GRE, it could be better because you can utilize IP MTU and TCP adjust-mss on tunnel interface.
If there's an IP interface in the end-to-end path, you might take advantage of the aforementioned commands, but, I believe, not on the xconnect interface itself (as it's L2).
BTW, did you see the reference I provided in my edited prior reply? It well discusses the l2tp fragmentation issue, including possible mitigation approaches.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-05-2023
04:09 PM
- last edited on
06-07-2023
03:08 AM
by
Translator
![]()
I've already have
ip mtu
and
tcp mss
on my tunnel 100 — it's tunnel between two offices with ipsec
My config is almost same - https://www.byteworks.com/xconnect-over-ipsec/ I only added on the tunnel
ip mtu
and
tcp mss
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-05-2023 06:52 PM
Suspect it does not help on a VTI transporting l2tp.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-05-2023 08:53 AM
as @Joseph W. Doherty mention
the L3 interface can deal with packet higher than egress interface but if you use xconnect then you bridge traffic and there is no L3 interface can frag/defrag the packet/frame pass though.
I think under the pseudowire-class you config the MTU which must least than the MTU of interface you use to connect two router
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-05-2023
08:58 AM
- last edited on
06-07-2023
03:04 AM
by
Translator
![]()
I tried to use command
ip pmtu
under the pseudowire but with it everythink worked badly
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-05-2023
09:02 AM
- last edited on
06-07-2023
03:05 AM
by
Translator
![]()
Dont use
pmtu
you can directly
config mtu.
Try and check
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-05-2023
09:07 AM
- last edited on
06-07-2023
03:06 AM
by
Translator
![]()
Under pseudowire? If I remember correctly there isn't command
mtu
...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-05-2023
09:17 AM
- last edited on
06-07-2023
02:55 AM
by
Translator
![]()
True
MTU Handling
It is important that you configure a Maximum Transmission Unit (MTU) appropriate for each L2TPv3 tunneled link. The configured MTU size ensures the following:
-
The lengths of the tunneled Layer 2 frames fall below the MTU of the destination attachment circuit.
-
The tunneled packets are not fragmented, which forces the receiving PE to reassemble them.
L2TPv3 handles the MTU as follows:
-
The default behavior is to fragment packets that are larger than the session MTU.
-
If you enable the
ip dfbit set
command in the pseudowire class, the default MTU behavior changes so that any packets that cannot fit within the tunnel MTU are dropped.
-
If you enable the ip pmtu command in the pseudowire class, the L2TPv3 control channel participates in the path MTU (PMTU) discovery.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-05-2023 10:00 AM
Set df bit under pseudowire broke my traffic
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-05-2023 10:08 AM
the guide I share is recommend not use df bit, I share it if you use stop that.
but this give use indication that the issue is really the MTU here
the l3tpv3 overhead is approximant 74-80 add to that there is IPsec which also can more overhead, it hard to calculate the MTU here so I will run lab check the best mtu size.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-06-2023 05:51 AM
ping from R5 to R6 though l2tpv3 over VTI (protect by IPsec) the traffic frag and second fragment is big 154 (- new IP header 20)
so the traffic of 1500 is overhead with around 145 bytes.
hope this info. help you
thanks
MHM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide