- Cisco Community
- Technology and Support
- Networking
- Routing
- Hey, thanks for the reply!
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2014 03:58 AM - edited 03-04-2019 11:01 PM
Hello all, I've been searching forums for about 6 hours trying everything and anything, not to mention slowly working on this for a few weeks now, but I have failed so I am turning to anyone willing to help, thank you in advance!
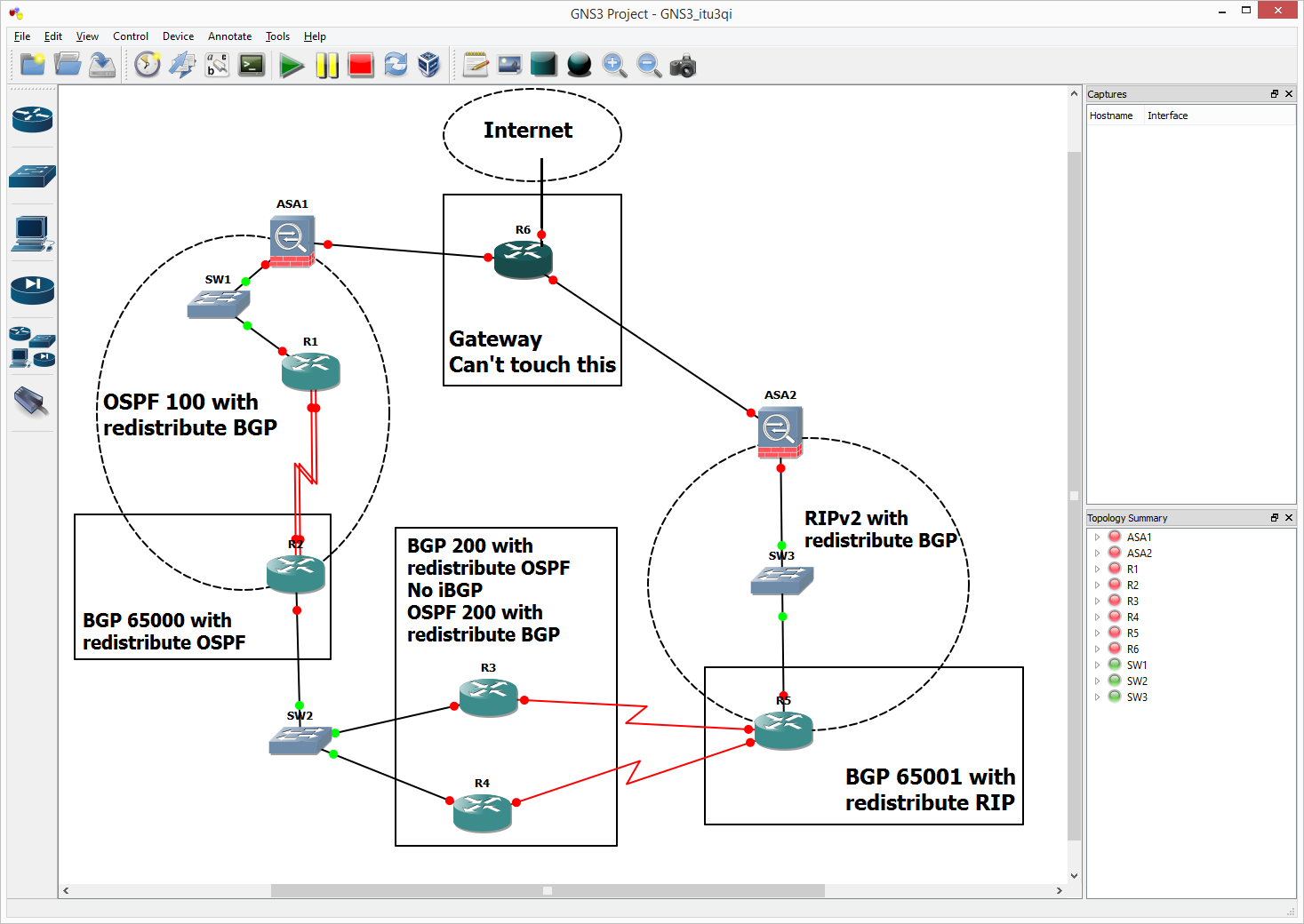
Above is my network topology. Without posting 20,000 pages of code, I just need some advice on what to do.
- I have to advertise default routes ONLY from ASA1 (OSPF) and ASA2 (RIPv2) somehow into their internal protocols and have that propagate throughout the whole network via BGP...but if ASA1 or ASA2 inside/outside interface goes down, or if the ASA just doesn't work, the default route can no longer be there (Yes with iBGP this would be relatively easy :/ )
- I cannot use iBGP
- I can't mess with the gateway router
- No BGP on ASA1, R1, or ASA 2
- If ASA1 goes down, everything can access internet through ASA2, and vice versa.
OSPF is already redistributed into BGP, and vice versa
RIP is already redistributed into BGP, and vice versa
R2, R3, R4, R5 have BGP and have eBGP neighbors
I haven't been able to get default routes from ASA1 or ASA3 via IGP (default-information originate) to propagate into BGP and out to neighbors
Every route knows about every route and can reach every address in the diagram via every path (I can post configs if needed but it's a lot, right now I'm using a lot of BGP default originate and some static routes just for testing)
What I have tried:
1. I knew this wasn't going to work but:
R2# router bgp 65000
neighbor (both in AS 000) default originate route-map METRIC <--Metric=222
R5# router bgp 65001
neighbor (both in AS 100) default originate route-map METRIC <--metric=333
It doesn't matter if ASA 1 or ASA 2 is up or down, R2 and R5 will still remain the default routes regardless...not what I want
2.
ASA1# router ospf 100
default-information originate always
R2# router bgp 65000
redistribute ospf metric 100 match internal external.
The routes did not propagate into BGP and the neighbors never get the default route from eBGP.
3. Floating static routes but again came the problem with the network knowing that ASA1 or ASA3 is down and choosing the other path.
4. I tried so many other things I can't even remember them all :(
I appreciate anyone taking their time to respond, this is literally driving me nuts. I obviously must have missed something in my Cisco IP Routing (ROUTE) book...
Solved! Go to Solution.
- Labels:
-
Routing Protocols
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2014 11:36 PM
instead of redistributing, try advertising via the network statement. e.g. network 0.0.0.0 because generally speaking it will advertise out if it has it in its routing table.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2014 07:02 AM
Please take note that Internet router should advetised default routes to ASA1 then only default-information originate inject default route into ospf process 100.
Use network command and agg. network command in bgp on ASA1 router to advertised routes of IGP (OSPF 100) instead or redistribution from ospf to bgp.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2014 11:57 AM
I should have made a better network diagram in GNS 3, no BGP on ASA1 or ASA 3, only static and OSPF on ASA1 and RIP on ASA2 and I can't touch the gateway router :(
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2014 10:36 PM
bUMP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2014 11:13 PM
Hello, this could be straight forward right? Set up IP SLA on the ASA's for ICMP-ECHO to the internet. Set a track for the reachability on this IP SLA. Configure a static default route towards the internet with track key word in command. Then use your routing protocols OSPF, RIP to default originate.
The usage here is that the track command combined with SLA will trigger injecting/withdrawing the static route in to the global routing table. If the internet connection is lost to 8.8.8.8 then the static route will be withdrawn from the routing table. This will then result in the routing protocols to stop advertising the default route in its routing protocol respectively. Vice versa when internet access is gained and reachability is up, the default route comes back and therefore default originate will inject the default back in to its routing domain.
e.g. (but not 100% accurate since I don't know ASA's extremely well, further config might be required to achieve this)
sla monitor 1
type echo protocol ipIcmpEcho 8.8.8.8 interface outside <------- address on the internet
sla monitor schedule 1 life forever start-time now
!
track 1 rtr 1 reachability
route outside 0.0.0.0 0.0.0.0 x.x.x.x track 1 <--------- default route to next hop for internet access
!
router ospf 1 / router rip
default-information originate
hth
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2014 11:19 PM
Hey, thanks for the reply! Since nothing has been on my mind but solving this, I was thinking about SLA all day today. Here's my big problem though, how do I get those routes into BGP 100? If I do BGP default originate on R2 and R5, it won't matter if the route is up or down it will still be default route. Even so, without worrying about the SLA, I can't get my default routes via IGP to propagate from OSPF->BGP->eBGP neighbor and RIP->BGP->eBGP neighbor, even when I try to have BGP redistribute OSPF match external.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2014 11:36 PM
instead of redistributing, try advertising via the network statement. e.g. network 0.0.0.0 because generally speaking it will advertise out if it has it in its routing table.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-24-2014 12:12 AM
Hmmm, I actually did not try this because I didn't think it would advertise default routes it learned through IGP. I will have to give it a shot, thanks for the suggestion, I will see if it works.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide