- Cisco Community
- Technology and Support
- Networking
- Routing
- Routing in switch (ip default-gateway command)
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-07-2022
11:27 AM
- last edited on
12-14-2022
09:43 PM
by
Translator
![]()
Hello,
I have router 1111 and Switch 1000, between them is trunk with 5 VLANs,
default gateways
sitting on the router. Just two VLANs have Internet access (VLAN 10 - via VPN to core router, and VLAN 99 local NAT) -
Switch has
default gateway
command in config
(ip default-gateway 10.10.10.1)
switch itself 10.10.10.2, and i use this IP for access to switch.
i added one more VLAN 99, and configure test interface 10.10.99.2 on switch (10.10.99.1 is router). This network has NAT and internet access.
i would like to keep -
ip default-gateway 10.10.10.1
but in this case 10.10.99.1 doesnt have internet access, when i change to
ip default-gateway 10.10.99.1
everything works, but this config doesnt work for me, because i have to put some ACLs to VLAN99.
looks weird for me...
Solved! Go to Solution.
- Labels:
-
ISR 1000 Series
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-08-2022
03:18 PM
- last edited on
12-14-2022
09:52 PM
by
Translator
![]()
Hello
The router is performing the intervlan routing, So I assume it has the L3 addressing for all the vlans (including the new guest vlan)
The has switch has mgt addressing on vlan 10 (no ip routing but using a
default-gateway
of vlan 10 L3 address on rtr) so that switch becomes a host switch.
All you need to do is create the l2 vlans on the switch that related to the L3 routed interfaces on the router and then assign the access-port to the relevant vlans lasty attach end nodes to those access-posts
Example
SW
int vlan 10
ip addres 10.10.10.2 255.255.255.0
no shut
exit
no ip routing
ip default-gateway 10.10.10.1
vlan 10,20,99 etc...
exit
int x/x
Description link to router
switchport mode trunk
int x/x
Description access port vlan 10
switchport mode access
switchport access vlan 10
int x/x
Description access port vlan 20
switchport mode access
switchport access vlan 20
int x/x
Description access port vlan 99
switchport mode access
switchport access vlan 99
etc...
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-11-2022
10:11 AM
- last edited on
12-14-2022
09:57 PM
by
Translator
![]()
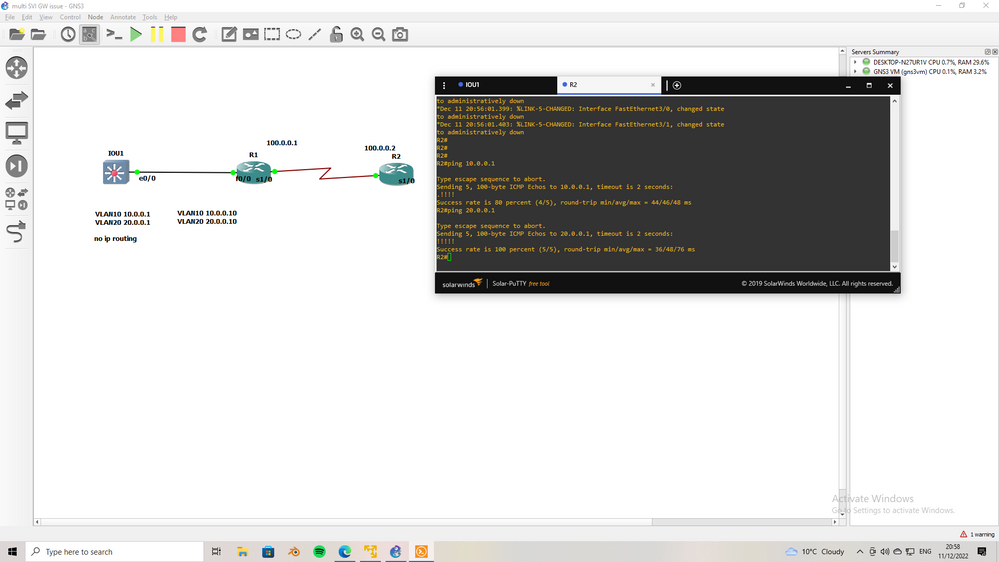
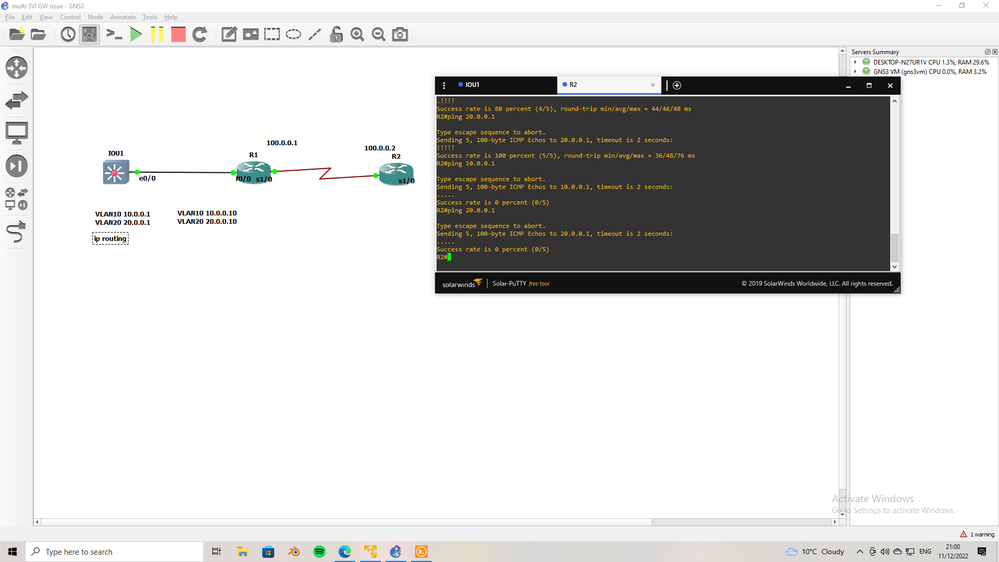
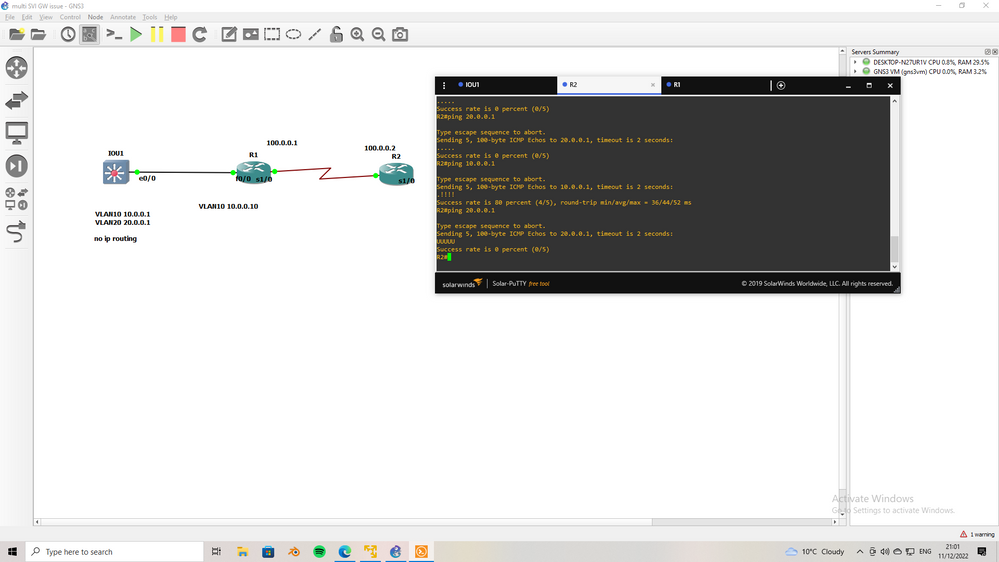
Case1
two SVI in IOU1
VLAN10 10.0.0.1
VLAN20 20.0.0.1
no ip routing <<- this L2 SW
ip default-gateway 10.0.0.10
the R1 have two subinterface f0/0.10 10.0.0.10, f0/0.20 20.0.0.10
You can see from R2 we can ping both SVI in SW even if GW in SW is toward 10.0.0.10 we can ping 20.0.0.1 in SW
Case2
two SVI in IOU1
VLAN10 10.0.0.1
VLAN20 20.0.0.1
ip routing <<- this L3 SW
ip default-gateway 10.0.0.10
the R1 have two subinterface f0/0.10 10.0.0.10, f0/0.20 20.0.0.10
You can see from R2 we can NOT ping any SVI in SW since NOW the SW is L3 not L2
Case3
two SVI in IOU1
VLAN10 10.0.0.1
VLAN20 20.0.0.1
no ip routing <<- this L2 SW
ip default-gateway 10.0.0.10
the R1 have two subinterface f0/0.10 10.0.0.10 ONLY
You can see from R2 we can ping SVI of VLAN10 but can not ping VLAN20 even if have VLAN20 SVI in IOU1
what I want to clear here of SW is L2 and you have multi VLAN SVI you need only one GW in SW point to any SVI next-hop.
@sergo777 your issue not GW your issue is router interface and I think NAT.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-07-2022
11:34 AM
- last edited on
12-14-2022
09:45 PM
by
Translator
![]()
IP default gateway
used for Layer 2 device as mentioned.
Just create vlan 99 in the switch ( allow this VLAN 99 in Trunk)
create a sub interface or create Layer 3 SVI in Router ( add same subnet to NAT, so get internet)
on the switch ( where you looking to connect device with VLAN 99) make that port access port vlan 99)
you do not need to create interface on the switch.
what ACL you looking to Put, is this not possible doing on Router ? you want to do this in switch ? when you need make Layer3 switch enabling ip routing.
=====Preenayamo Vasudevam=====
***** Rate All Helpful Responses *****
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-07-2022 11:39 AM
Thanks. Yeah i know, i created interface on switch side just for test purposes. I dont need any IPs on switch side, its L2 (just one for management)
ACLs - i need to block access to internal networks, because VLAN99 will be like Guest network with internet only
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-07-2022
11:44 AM
- last edited on
12-14-2022
09:46 PM
by
Translator
![]()
You can create same ACL in VLAN interface in Router - example :
access-list 100 source deny vlan99 ip destination other vlan IP
access0list 100 permit any any
interface vlan 99 - apply acl in
=====Preenayamo Vasudevam=====
***** Rate All Helpful Responses *****
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-07-2022 12:07 PM
right. but in this case i will block my management IP 10.10.99.2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-07-2022 11:52 AM
Hmm, Nice Q.
I will lab tonight figure out how we can solve this issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-08-2022
02:11 AM
- last edited on
12-14-2022
09:47 PM
by
Translator
![]()
I try lab yesterday, but it hard
you have two link
one via WAN
one via internet
access via internet need public IP so the VLAN must be 99 (NAT)
access via WAN need private IP so the VLAN can 99 or 10 (NO NAT)
am I right ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-07-2022
11:31 PM
- last edited on
12-14-2022
09:49 PM
by
Translator
![]()
Hello
The reason why it doesn’t work from the switch is the switch itself is ONLY a host device just like any pc will be so as soon as you give it a
default-gateway
of the new vlan it works.
Going forward you just need to create a new guest L2 vlan and trunk it down to the switch and assign access ports to it .
If you do not wish for any other vlan to speak to it you have two ways to accomplish this:
1 -
access-list
on the guest vlan residing on thr router denying all other vlans but permitting any
2- put the Guest L3 vlan interface on the rtr in a VRF
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-08-2022
09:25 AM
- last edited on
12-14-2022
09:50 PM
by
Translator
![]()
Thanks Paul, i tried to switch it to normal L3
(removed ip def-gw)
and create 0.0.0.0 -> gw it also doesnt work... my understanding - 10.10.99.1 should be default GW for .99 network and after that it should reach 10.10.10.0 network...
Paul, do you mean i need like "service/transit" VLAN and it should be default GW?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-08-2022
03:18 PM
- last edited on
12-14-2022
09:52 PM
by
Translator
![]()
Hello
The router is performing the intervlan routing, So I assume it has the L3 addressing for all the vlans (including the new guest vlan)
The has switch has mgt addressing on vlan 10 (no ip routing but using a
default-gateway
of vlan 10 L3 address on rtr) so that switch becomes a host switch.
All you need to do is create the l2 vlans on the switch that related to the L3 routed interfaces on the router and then assign the access-port to the relevant vlans lasty attach end nodes to those access-posts
Example
SW
int vlan 10
ip addres 10.10.10.2 255.255.255.0
no shut
exit
no ip routing
ip default-gateway 10.10.10.1
vlan 10,20,99 etc...
exit
int x/x
Description link to router
switchport mode trunk
int x/x
Description access port vlan 10
switchport mode access
switchport access vlan 10
int x/x
Description access port vlan 20
switchport mode access
switchport access vlan 20
int x/x
Description access port vlan 99
switchport mode access
switchport access vlan 99
etc...
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-09-2022 07:13 AM
Thanks Paul, yes, its classic config, i have it everywhere ... not sure why it doesnt work for this switch.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-09-2022 07:53 AM
@paul driver how he access SW if he dont have svi and default gateway?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-09-2022 11:25 AM
Hello
Hum... he does have SVI & D/G on switch? (vlan 10)
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-09-2022 11:28 AM - edited 12-09-2022 11:28 AM
And that issue this vlan is not access by internet via NAT in router only vlan have internet access is vlan 99.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-11-2022
05:56 AM
- last edited on
12-14-2022
09:54 PM
by
Translator
![]()
Hello
whatever mgt address and related default gateway the switch uses it’s still a host switch unless ip routing is enabled as such its irrelevant if access from any additional subnet(vlan) from an access-port off the same switch is required what will be required are the l2 vlans for those additional vlans which will need to allowed traverse the trunk connecting to the roas interface - as for any vlan not gaining internet access that will be down to the nat policy on the L3 servicing the routing
In any case changing the
default-gateway
of a mgt interface of the switch has no bearing for users located off that switch to gain internet access - however it would have if remote-access to that switch is required.
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide