- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: S2S VPN Configuration
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
S2S VPN Configuration
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2023 06:45 AM
Hi,
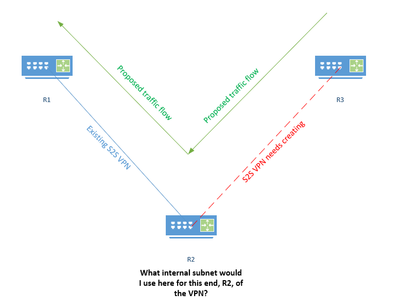
I want to route traffic through 2 firewalls, via S2SVPN connections, one of the VPNs, R1 to R2 already exists, but the other, R1 to R2 doesn't, so I need to create it.
I am unsure about what IP address/subnet to use for router B? Do I create one that will only be used just for this purpose? or do I use an interface of R2?
I hope the attached diagram makes sense of what I am trying to achieve
- Labels:
-
Other Routers
-
Other Routing
-
WAN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2023 06:58 AM
What device is this ? ASA or Routers
if router what model of the router and IOS Code running here ?
As i understand you looking to flow the traffic between R1 to R2 or R2 to R1 (via R3) - Do you have any other path for R1 to reach to R2 ?
i do not see any issue, as long as you have routing in place and ACL created correctly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2023 07:12 AM
What issue, I think it work
Make another s2s vpn
Acl of this new vpn s2s is permit from spoke2 lan router to spoke1 lan router not from spoke2 lan to hub lan.
In spoke1 you need to be sure that it have route to spoke2 lan pass through hub
In hub you must sure you have route to spoke2 lan.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2023 07:21 AM
Sorry forgot to mention, R2 is non Cisco and needs a local subnet in order to connect the VPN.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2023 07:35 AM
That is fine, what is the challange you facing here. that solution is feasible with cisco and 3rd party routers(if they support VPN features)
needs a local subnet in order to connect the VPN. - is this new setup ? you can use any RFC 1918 address, (which is not using in R1 or R3 lan side - not to conflict)
basic need to setup a VPN, Public (if over internet to be reachable) each other agree the VPN settings to form VPN.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2023 02:50 PM
R3
crypto isakmp policy 10
hash md5
authentication pre-share
crypto isakmp key mhm address 0.0.0.0 0.0.0.0
!
!
crypto ipsec transform-set mhm ah-md5-hmac esp-des
!
crypto map mhm 10 ipsec-isakmp
set peer 100.0.0.1
set transform-set mhm
match address 110
!
crypto map mhm1 10 ipsec-isakmp
! Incomplete
!
crypto map mhm2 10 ipsec-isakmp
set peer 110.0.0.2
set transform-set mhm
match address 100
!
interface Serial1/0
ip address 100.0.0.3 255.255.255.0
serial restart-delay 0
crypto map mhm
!
!
interface Serial1/1
ip address 110.0.0.3 255.255.255.0
serial restart-delay 0
crypto map mhm2
!
ip route 10.0.0.0 255.255.255.0 Serial1/0
ip route 20.0.0.0 255.255.255.0 Serial1/1
!
access-list 100 permit ip 10.0.0.0 0.0.0.255 20.0.0.0 0.0.0.255
access-list 110 permit ip 20.0.0.0 0.0.0.255 10.0.0.0 0.0.0.255
R1
crypto isakmp policy 10
hash md5
authentication pre-share
crypto isakmp key mhm address 0.0.0.0 0.0.0.0
!
!
crypto ipsec transform-set mhm ah-md5-hmac esp-des
!
crypto map mhm 10 ipsec-isakmp
set peer 100.0.0.3
set transform-set mhm
match address 100
!
interface FastEthernet0/0
ip address 10.0.0.1 255.255.255.0
duplex half
!
interface Serial1/0
ip address 100.0.0.1 255.255.255.0
serial restart-delay 0
crypto map mhm
!
ip route 0.0.0.0 0.0.0.0 Serial1/0
!
access-list 100 permit ip 10.0.0.0 0.0.0.255 20.0.0.0 0.0.0.255
R2
crypto isakmp policy 10
hash md5
authentication pre-share
crypto isakmp key mhm address 0.0.0.0 0.0.0.0
!
!
crypto ipsec transform-set mhm ah-md5-hmac esp-des
!
crypto map mhm 10 ipsec-isakmp
set peer 110.0.0.3
set transform-set mhm
match address 100
!
interface FastEthernet0/0
ip address 20.0.0.2 255.255.255.0
duplex half
!
!
interface Serial1/0
no ip address
shutdown
serial restart-delay 0
!
!
interface Serial1/1
ip address 110.0.0.2 255.255.255.0
serial restart-delay 0
crypto map mhm
!
ip route 0.0.0.0 0.0.0.0 Serial1/1
!
access-list 100 permit ip 20.0.0.0 0.0.0.255 10.0.0.0 0.0.0.255
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide