- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: Setting up site to site IPSec VPN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Setting up site to site IPSec VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-01-2019 09:27 AM
Hello everyone!
I need help to set up my IPSec VPN.
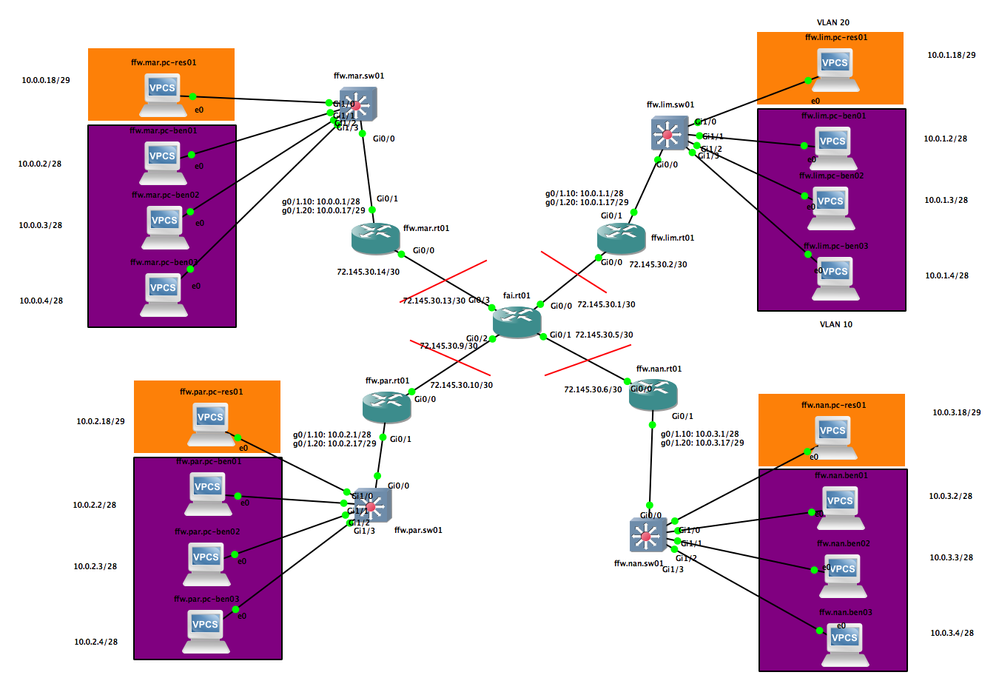
Here is my topology in GNS3:
I'm trying to setup a VPN between ffw.par.rt01 and each of the other router (mar,lim,nan). Meaning every VPCS can access the ffw.par.* VPCS via the VPN, and the ffw.par.* VPCS can access the other VPCS via the VPN.
First, I'm trying to set up the VPN between ffw.par.rt01 and ffw.mar.rt01.
Config on the routers before setting up the VPN:
ffw.par.rt01#sh running-config Building configuration... Current configuration : 4075 bytes ! version 15.6 service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption ! hostname ffw.par.rt01 ! boot-start-marker boot-end-marker ! ! ! no aaa new-model ethernet lmi ce ! ! ! no process cpu autoprofile hog mmi polling-interval 60 no mmi auto-configure no mmi pvc mmi snmp-timeout 180 ! ! ! ! ! no ip icmp rate-limit unreachable ! ! ! ! ! ! no ip domain lookup ip cef no ipv6 cef ! multilink bundle-name authenticated ! ! ! ! ! redundancy ! no cdp log mismatch duplex no cdp run ! ip tcp synwait-time 5 ! ! ! ! ! ! ! ! ! ! ! ! ! interface GigabitEthernet0/0 ip address 72.145.30.10 255.255.255.252 ip nat outside ip virtual-reassembly in duplex auto speed auto media-type rj45 no cdp enable ! interface GigabitEthernet0/1 no ip address duplex auto speed auto media-type rj45 no cdp enable ! interface GigabitEthernet0/1.10 encapsulation dot1Q 10 ip address 10.0.2.1 255.255.255.240 ip access-group 110 in ip nat inside ip virtual-reassembly in no cdp enable ! interface GigabitEthernet0/1.20 encapsulation dot1Q 20 ip address 10.0.2.17 255.255.255.248 ip access-group 120 in ip nat inside ip virtual-reassembly in no cdp enable ! interface GigabitEthernet0/2 no ip address shutdown duplex auto speed auto media-type rj45 no cdp enable ! interface GigabitEthernet0/3 no ip address shutdown duplex auto speed auto media-type rj45 no cdp enable ! ip forward-protocol nd ! ! no ip http server no ip http secure-server ip nat inside source list 1 interface GigabitEthernet0/0 overload ip route 72.145.30.0 255.255.255.252 72.145.30.9 ip route 72.145.30.4 255.255.255.252 72.145.30.9 ip route 72.145.30.12 255.255.255.252 72.145.30.9 ! ! ! access-list 1 permit 10.0.2.0 0.0.0.15 access-list 1 permit 10.0.2.16 0.0.0.7 access-list 110 deny ip 10.0.2.0 0.0.0.15 10.0.2.16 0.0.0.7 access-list 110 permit ip any any access-list 120 deny ip 10.0.2.16 0.0.0.7 10.0.2.0 0.0.0.15 access-list 120 permit ip any any ! control-plane ! banner exec ^C ************************************************************************** * IOSv is strictly limited to use for evaluation, demonstration and IOS * * education. IOSv is provided as-is and is not supported by Cisco's * * Technical Advisory Center. Any use or disclosure, in whole or in part, * * of the IOSv Software or Documentation to any third party for any * * purposes is expressly prohibited except as otherwise authorized by * * Cisco in writing. * **************************************************************************^C banner incoming ^C ************************************************************************** * IOSv is strictly limited to use for evaluation, demonstration and IOS * * education. IOSv is provided as-is and is not supported by Cisco's * * Technical Advisory Center. Any use or disclosure, in whole or in part, * * of the IOSv Software or Documentation to any third party for any * * purposes is expressly prohibited except as otherwise authorized by * * Cisco in writing. * **************************************************************************^C banner login ^C ************************************************************************** * IOSv is strictly limited to use for evaluation, demonstration and IOS * * education. IOSv is provided as-is and is not supported by Cisco's * * Technical Advisory Center. Any use or disclosure, in whole or in part, * * of the IOSv Software or Documentation to any third party for any * * purposes is expressly prohibited except as otherwise authorized by * * Cisco in writing. * **************************************************************************^C ! line con 0 exec-timeout 0 0 privilege level 15 logging synchronous line aux 0 exec-timeout 0 0 privilege level 15 logging synchronous line vty 0 4 login transport input none ! no scheduler allocate ! end
ffw.mar.rt01#sh run Building configuration... Current configuration : 4077 bytes ! version 15.6 service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption ! hostname ffw.mar.rt01 ! boot-start-marker boot-end-marker ! ! ! no aaa new-model ethernet lmi ce ! ! ! no process cpu autoprofile hog mmi polling-interval 60 no mmi auto-configure no mmi pvc mmi snmp-timeout 180 ! ! ! ! ! no ip icmp rate-limit unreachable ! ! ! ! ! ! no ip domain lookup ip cef no ipv6 cef ! multilink bundle-name authenticated ! ! ! ! ! redundancy ! no cdp log mismatch duplex no cdp run ! ip tcp synwait-time 5 ! ! ! ! ! ! ! ! ! ! ! ! ! interface GigabitEthernet0/0 ip address 72.145.30.14 255.255.255.252 ip nat outside ip virtual-reassembly in duplex auto speed auto media-type rj45 no cdp enable ! interface GigabitEthernet0/1 no ip address duplex auto speed auto media-type rj45 no cdp enable ! interface GigabitEthernet0/1.10 encapsulation dot1Q 10 ip address 10.0.0.1 255.255.255.240 ip access-group 110 in ip nat inside ip virtual-reassembly in no cdp enable ! interface GigabitEthernet0/1.20 encapsulation dot1Q 20 ip address 10.0.0.17 255.255.255.248 ip access-group 120 in ip nat inside ip virtual-reassembly in no cdp enable ! interface GigabitEthernet0/2 no ip address shutdown duplex auto speed auto media-type rj45 no cdp enable ! interface GigabitEthernet0/3 no ip address shutdown duplex auto speed auto media-type rj45 no cdp enable ! ip forward-protocol nd ! ! no ip http server no ip http secure-server ip nat inside source list 1 interface GigabitEthernet0/0 overload ip route 72.145.30.0 255.255.255.252 72.145.30.13 ip route 72.145.30.4 255.255.255.252 72.145.30.13 ip route 72.145.30.8 255.255.255.252 72.145.30.13 ! ! ! access-list 1 permit 10.0.0.0 0.0.0.15 access-list 1 permit 10.0.0.16 0.0.0.7 access-list 110 deny ip 10.0.0.0 0.0.0.15 10.0.0.16 0.0.0.7 access-list 110 permit ip any any access-list 120 deny ip 10.0.0.16 0.0.0.7 10.0.0.0 0.0.0.15 access-list 120 permit ip any any ! control-plane ! banner exec ^C ************************************************************************** * IOSv is strictly limited to use for evaluation, demonstration and IOS * * education. IOSv is provided as-is and is not supported by Cisco's * * Technical Advisory Center. Any use or disclosure, in whole or in part, * * of the IOSv Software or Documentation to any third party for any * * purposes is expressly prohibited except as otherwise authorized by * * Cisco in writing. * **************************************************************************^C banner incoming ^C ************************************************************************** * IOSv is strictly limited to use for evaluation, demonstration and IOS * * education. IOSv is provided as-is and is not supported by Cisco's * * Technical Advisory Center. Any use or disclosure, in whole or in part, * * of the IOSv Software or Documentation to any third party for any * * purposes is expressly prohibited except as otherwise authorized by * * Cisco in writing. * **************************************************************************^C banner login ^C ************************************************************************** * IOSv is strictly limited to use for evaluation, demonstration and IOS * * education. IOSv is provided as-is and is not supported by Cisco's * * Technical Advisory Center. Any use or disclosure, in whole or in part, * * of the IOSv Software or Documentation to any third party for any * * purposes is expressly prohibited except as otherwise authorized by * * Cisco in writing. * **************************************************************************^C ! line con 0 exec-timeout 0 0 privilege level 15 logging synchronous line aux 0 exec-timeout 0 0 privilege level 15 logging synchronous line vty 0 4 login transport input none ! no scheduler allocate ! end
Now, the VPN configuration. Below I have listed the steps I used on each router:
ffw.par.rt01(config)#crypto isakmp policy 5 ffw.par.rt01(config-isakmp)#hash sha ffw.par.rt01(config-isakmp)#authentication pre-share ffw.par.rt01(config-isakmp)#group 2 ffw.par.rt01(config-isakmp)#lifetime 86400 ffw.par.rt01(config-isakmp)#encryption 3des ffw.par.rt01(config-isakmp)#exit ffw.par.rt01(config)#crypto isakmp key cisco@123 address 72.145.30.14 ffw.par.rt01(config)#crypto ipsec transform-set MY-SET esp-aes 128 esp-md5-hmac ffw.par.rt01(cfg-crypto-trans)#crypto ipsec security-association lifetime seconds 3600 ffw.par.rt01(config)#ip access-list extended VPN-TRAFFIC ffw.par.rt01(config-ext-nacl)#permit ip 10.0.2.0 0.0.0.255 10.0.0.0 0.0.0.255 ffw.par.rt01(config-ext-nacl)#permit ip 10.0.2.0 0.0.0.255 10.0.1.0 0.0.0.255 ffw.par.rt01(config-ext-nacl)#permit ip 10.0.2.0 0.0.0.255 10.0.3.0 0.0.0.255 ffw.par.rt01(config)#crypto map IPSEC-SITE-TO-SITE-VPN 10 ipsec-isakmp ffw.par.rt01(config-crypto-map)#match address VPN-TRAFFIC ffw.par.rt01(config-crypto-map)#set peer 72.145.30.14 ffw.par.rt01(config-crypto-map)#set transform-set MY-SET ffw.par.rt01(config)#int g0/0 ffw.par.rt01(config-if)#crypto map IPSEC-SITE-TO-SITE-VPN # Exclude VPN traffic from NAT Overload ffw.par.rt01(config)#ip access-list extended 1 ffw.par.rt01(config-ext-nacl)#deny ip 10.0.2.0 0.0.0.255 10.0.0.0 0.0.0.255 ffw.par.rt01(config-ext-nacl)#deny ip 10.0.2.0 0.0.0.255 10.0.1.0 0.0.0.255 ffw.par.rt01(config-ext-nacl)#deny ip 10.0.2.0 0.0.0.255 10.0.3.0 0.0.0.255 ffw.par.rt01(config-ext-nacl)#permit ip 10.0.2.0 0.0.0.255 any ffw.par.rt01(config-ext-nacl)#exit ffw.par.rt01(config)#ip nat inside source list 101 interface gigabitEthernet 0/0 overload
ffw.mar.rt01(config)#crypto isakmp policy 5 ffw.mar.rt01(config-isakmp)#hash sha ffw.mar.rt01(config-isakmp)#authentication pre-share ffw.mar.rt01(config-isakmp)#group 2 ffw.mar.rt01(config-isakmp)#lifetime 86400 ffw.mar.rt01(config-isakmp)#encryption 3des ffw.mar.rt01(config-isakmp)#exit ffw.mar.rt01(config)#crypto isakmp key cisco@123 address 72.145.30.10 ffw.mar.rt01(config)#crypto ipsec transform-set MY-SET esp-aes 128 esp-md5-hmac ffw.mar.rt01(cfg-crypto-trans)#crypto ipsec security-association lifetime seconds 3600 ffw.mar.rt01(config)#ip access-list extended VPN-TRAFFIC ffw.par.rt01(config-ext-nacl)#permit ip 10.0.0.0 0.0.0.255 10.0.1.0 0.0.0.255 ffw.par.rt01(config-ext-nacl)#permit ip 10.0.0.0 0.0.0.255 10.0.2.0 0.0.0.255 ffw.par.rt01(config-ext-nacl)#permit ip 10.0.0.0 0.0.0.255 10.0.3.0 0.0.0.255 ffw.mar.rt01(config)#crypto map IPSEC-SITE-TO-SITE-VPN 10 ipsec-isakmp ffw.mar.rt01(config-crypto-map)#match address VPN-TRAFFIC ffw.mar.rt01(config-crypto-map)#set peer 72.145.30.10 ffw.mar.rt01(config-crypto-map)#set transform-set MY-SET ffw.mar.rt01(config)#int g0/1 ffw.mar.rt01(config-if)#crypto map IPSEC-SITE-TO-SITE-VPN ffw.mar.rt01(config)#ip access-list extended 101 ffw.par.rt01(config-ext-nacl)#deny ip 10.0.0.0 0.0.0.255 10.0.1.0 0.0.0.255 ffw.par.rt01(config-ext-nacl)#deny ip 10.0.0.0 0.0.0.255 10.0.2.0 0.0.0.255 ffw.par.rt01(config-ext-nacl)#deny ip 10.0.0.0 0.0.0.255 10.0.3.0 0.0.0.255 ffw.par.rt01(config-ext-nacl)#permit ip 10.0.0.0 0.0.0.255 any ffw.mar.rt01(config-ext-nacl)#exit ffw.par.rt01(config)#ip nat inside source list 101 interface gigabitEthernet 0/0 overload
OK. So far no error.
Now let's try pinging par from mar:
VPCS> ping 72.145.30.10 84 bytes from 72.145.30.10 icmp_seq=1 ttl=253 time=50.915 ms 84 bytes from 72.145.30.10 icmp_seq=2 ttl=253 time=24.942 ms 84 bytes from 72.145.30.10 icmp_seq=3 ttl=253 time=27.652 ms 84 bytes from 72.145.30.10 icmp_seq=4 ttl=253 time=46.881 ms ^C VPCS> ping 10.0.2.1 *10.0.0.1 icmp_seq=1 ttl=255 time=24.070 ms (ICMP type:3, code:1, Destination host unreachable) *10.0.0.1 icmp_seq=2 ttl=255 time=18.625 ms (ICMP type:3, code:1, Destination host unreachable) *10.0.0.1 icmp_seq=3 ttl=255 time=45.900 ms (ICMP type:3, code:1, Destination host unreachable) ^C VPCS> ping 10.0.2.2 *10.0.0.1 icmp_seq=1 ttl=255 time=71.359 ms (ICMP type:3, code:1, Destination host unreachable) *10.0.0.1 icmp_seq=2 ttl=255 time=24.515 ms (ICMP type:3, code:1, Destination host unreachable) *10.0.0.1 icmp_seq=3 ttl=255 time=18.195 ms (ICMP type:3, code:1, Destination host unreachable) *10.0.0.1 icmp_seq=4 ttl=255 time=48.356 ms (ICMP type:3, code:1, Destination host unreachable) *10.0.0.1 icmp_seq=5 ttl=255 time=25.838 ms (ICMP type:3, code:1, Destination host unreachable)
As you can see I can't access the VPCS.
What did I miss? Is it about the access-lists? I tried to be careful about NAT but it's easy to mess up...
Thanks for your help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-01-2019 10:44 AM - edited 06-01-2019 10:53 AM
Hello,
remove the access lists on your subinterfaces (no access-group 110/120), and use the VPN and NAT access lists below:
ffw.par.rt01
ip access-list extended VPN-TRAFFIC
permit ip 10.0.2.0 0.0.0.255 10.0.0.0 0.0.0.255
ip access-list extended 101
deny ip 10.0.2.0 0.0.0.255 10.0.0.0 0.0.0.255
permit ip 10.0.2.0 0.0.0.255 any
ffw.mar.rt01
ip access-list extended VPN-TRAFFIC
permit ip 10.0.0.0 0.0.0.255 10.0.2.0 0.0.0.255
ip access-list extended 101
deny ip 10.0.0.0 0.0.0.255 10.0.2.0 0.0.0.255
permit ip 10.0.0.0 0.0.0.255 any
EDIT: it would be easier to troubleshoot your configs if you would post the full running configs including all the VPN stuff...a consolidated config so to speak.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-02-2019 03:15 PM
First of all, thank you for your answer.
Here is my config after setting up the VPN + applying your suggested changes (which apparently did not help):
ffw.par.rt01#sh running-config Building configuration... Current configuration : 4795 bytes ! ! Last configuration change at 22:06:55 UTC Sun Jun 2 2019 ! version 15.6 service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption ! hostname ffw.par.rt01 ! boot-start-marker boot-end-marker ! ! ! no aaa new-model ethernet lmi ce ! ! ! no process cpu autoprofile hog mmi polling-interval 60 no mmi auto-configure no mmi pvc mmi snmp-timeout 180 ! ! ! ! ! no ip icmp rate-limit unreachable ! ! ! ! ! ! no ip domain lookup ip cef no ipv6 cef ! multilink bundle-name authenticated ! ! ! ! ! redundancy ! no cdp log mismatch duplex no cdp run ! ip tcp synwait-time 5 ! ! ! ! ! crypto isakmp policy 5 encr 3des authentication pre-share group 2 crypto isakmp key cisco@123 address 72.145.30.14 ! ! crypto ipsec transform-set MY-SET esp-aes esp-md5-hmac mode tunnel ! ! ! crypto map IPSEC-SITE-TO-SITE-VPN 10 ipsec-isakmp set peer 72.145.30.14 set transform-set MY-SET match address VPN-TRAFFIC ! ! ! ! ! interface GigabitEthernet0/0 ip address 72.145.30.10 255.255.255.252 ip nat outside ip virtual-reassembly in duplex auto speed auto media-type rj45 no cdp enable crypto map IPSEC-SITE-TO-SITE-VPN ! interface GigabitEthernet0/1 no ip address duplex auto speed auto media-type rj45 no cdp enable ! interface GigabitEthernet0/1.10 encapsulation dot1Q 10 ip address 10.0.2.1 255.255.255.240 ip access-group 110 in ip nat inside ip virtual-reassembly in no cdp enable ! interface GigabitEthernet0/1.20 encapsulation dot1Q 20 ip address 10.0.2.17 255.255.255.248 ip access-group 120 in ip nat inside ip virtual-reassembly in no cdp enable ! interface GigabitEthernet0/2 no ip address shutdown duplex auto speed auto media-type rj45 no cdp enable ! interface GigabitEthernet0/3 no ip address shutdown duplex auto speed auto media-type rj45 no cdp enable ! ip forward-protocol nd ! ! no ip http server no ip http secure-server ip nat inside source list 1 interface GigabitEthernet0/0 overload ip nat inside source list 101 interface GigabitEthernet0/0 overload ip route 72.145.30.0 255.255.255.252 72.145.30.9 ip route 72.145.30.4 255.255.255.252 72.145.30.9 ip route 72.145.30.12 255.255.255.252 72.145.30.9 ! ip access-list extended VPN-TRAFFIC permit ip 10.0.2.0 0.0.0.255 10.0.0.0 0.0.0.255 permit ip 10.0.2.0 0.0.0.255 10.0.1.0 0.0.0.255 permit ip 10.0.2.0 0.0.0.255 10.0.3.0 0.0.0.255 ! ! ! access-list 1 permit 10.0.2.0 0.0.0.15 access-list 1 permit 10.0.2.16 0.0.0.7 access-list 101 deny ip 10.0.2.0 0.0.0.255 10.0.0.0 0.0.0.255 access-list 101 deny ip 10.0.2.0 0.0.0.255 10.0.1.0 0.0.0.255 access-list 101 deny ip 10.0.2.0 0.0.0.255 10.0.3.0 0.0.0.255 access-list 101 permit ip 10.0.2.0 0.0.0.255 any ! control-plane ! banner exec ^C ************************************************************************** * IOSv is strictly limited to use for evaluation, demonstration and IOS * * education. IOSv is provided as-is and is not supported by Cisco's * * Technical Advisory Center. Any use or disclosure, in whole or in part, * * of the IOSv Software or Documentation to any third party for any * * purposes is expressly prohibited except as otherwise authorized by * * Cisco in writing. * **************************************************************************^C banner incoming ^C ************************************************************************** * IOSv is strictly limited to use for evaluation, demonstration and IOS * * education. IOSv is provided as-is and is not supported by Cisco's * * Technical Advisory Center. Any use or disclosure, in whole or in part, * * of the IOSv Software or Documentation to any third party for any * * purposes is expressly prohibited except as otherwise authorized by * * Cisco in writing. * **************************************************************************^C banner login ^C ************************************************************************** * IOSv is strictly limited to use for evaluation, demonstration and IOS * * education. IOSv is provided as-is and is not supported by Cisco's * * Technical Advisory Center. Any use or disclosure, in whole or in part, * * of the IOSv Software or Documentation to any third party for any * * purposes is expressly prohibited except as otherwise authorized by * * Cisco in writing. * **************************************************************************^C ! line con 0 exec-timeout 0 0 privilege level 15 logging synchronous line aux 0 exec-timeout 0 0 privilege level 15 logging synchronous line vty 0 4 login transport input none ! no scheduler allocate ! end
ffw.mar.rt01#sh running-config Building configuration... *Jun 2 22:10:08.517: %SYS-5-CONFIG_I: Configured from console by console Current configuration : 4797 bytes ! ! Last configuration change at 22:10:08 UTC Sun Jun 2 2019 ! version 15.6 service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption ! hostname ffw.mar.rt01 ! boot-start-marker boot-end-marker ! ! ! no aaa new-model ethernet lmi ce ! ! ! no process cpu autoprofile hog mmi polling-interval 60 no mmi auto-configure no mmi pvc mmi snmp-timeout 180 ! ! ! ! ! no ip icmp rate-limit unreachable ! ! ! ! ! ! no ip domain lookup ip cef no ipv6 cef ! multilink bundle-name authenticated ! ! ! ! ! redundancy ! no cdp log mismatch duplex no cdp run ! ip tcp synwait-time 5 ! ! ! ! ! crypto isakmp policy 5 encr 3des authentication pre-share group 2 crypto isakmp key cisco@123 address 72.145.30.10 ! ! crypto ipsec transform-set MY-SET esp-aes esp-md5-hmac mode tunnel ! ! ! crypto map IPSEC-SITE-TO-SITE-VPN 10 ipsec-isakmp set peer 72.145.30.10 set transform-set MY-SET match address VPN-TRAFFIC ! ! ! ! ! interface GigabitEthernet0/0 ip address 72.145.30.14 255.255.255.252 ip nat outside ip virtual-reassembly in duplex auto speed auto media-type rj45 no cdp enable ! interface GigabitEthernet0/1 no ip address duplex auto speed auto media-type rj45 no cdp enable crypto map IPSEC-SITE-TO-SITE-VPN ! interface GigabitEthernet0/1.10 encapsulation dot1Q 10 ip address 10.0.0.1 255.255.255.240 ip access-group 110 in ip nat inside ip virtual-reassembly in no cdp enable ! interface GigabitEthernet0/1.20 encapsulation dot1Q 20 ip address 10.0.0.17 255.255.255.248 ip access-group 120 in ip nat inside ip virtual-reassembly in no cdp enable ! interface GigabitEthernet0/2 no ip address shutdown duplex auto speed auto media-type rj45 no cdp enable ! interface GigabitEthernet0/3 no ip address shutdown duplex auto speed auto media-type rj45 no cdp enable ! ip forward-protocol nd ! ! no ip http server no ip http secure-server ip nat inside source list 1 interface GigabitEthernet0/0 overload ip nat inside source list 101 interface GigabitEthernet0/0 overload ip route 72.145.30.0 255.255.255.252 72.145.30.13 ip route 72.145.30.4 255.255.255.252 72.145.30.13 ip route 72.145.30.8 255.255.255.252 72.145.30.13 ! ip access-list extended VPN-TRAFFIC permit ip 10.0.0.0 0.0.0.255 10.0.1.0 0.0.0.255 permit ip 10.0.0.0 0.0.0.255 10.0.2.0 0.0.0.255 permit ip 10.0.0.0 0.0.0.255 10.0.3.0 0.0.0.255 ! ! ! access-list 1 permit 10.0.0.0 0.0.0.15 access-list 1 permit 10.0.0.16 0.0.0.7 access-list 101 deny ip 10.0.0.0 0.0.0.255 10.0.1.0 0.0.0.255 access-list 101 deny ip 10.0.0.0 0.0.0.255 10.0.2.0 0.0.0.255 access-list 101 deny ip 10.0.0.0 0.0.0.255 10.0.3.0 0.0.0.255 access-list 101 permit ip 10.0.0.0 0.0.0.255 any ! control-plane ! banner exec ^C ************************************************************************** * IOSv is strictly limited to use for evaluation, demonstration and IOS * * education. IOSv is provided as-is and is not supported by Cisco's * * Technical Advisory Center. Any use or disclosure, in whole or in part, * * of the IOSv Software or Documentation to any third party for any * * purposes is expressly prohibited except as otherwise authorized by * * Cisco in writing. * **************************************************************************^C banner incoming ^C ************************************************************************** * IOSv is strictly limited to use for evaluation, demonstration and IOS * * education. IOSv is provided as-is and is not supported by Cisco's * * Technical Advisory Center. Any use or disclosure, in whole or in part, * * of the IOSv Software or Documentation to any third party for any * * purposes is expressly prohibited except as otherwise authorized by * * Cisco in writing. * **************************************************************************^C banner login ^C ************************************************************************** * IOSv is strictly limited to use for evaluation, demonstration and IOS * * education. IOSv is provided as-is and is not supported by Cisco's * * Technical Advisory Center. Any use or disclosure, in whole or in part, * * of the IOSv Software or Documentation to any third party for any * * purposes is expressly prohibited except as otherwise authorized by * * Cisco in writing. * **************************************************************************^C ! line con 0 exec-timeout 0 0 privilege level 15 logging synchronous line aux 0 exec-timeout 0 0 privilege level 15 logging synchronous line vty 0 4 login transport input none ! no scheduler allocate ! end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-03-2019 12:01 AM
Hello,
there are still numerous misconfigurations which cause the VPN to malfunction. Make sure that the access lists, NAT and route statements, and the interface configurations look exactly like the below:
ffw.par.rt01
crypto isakmp policy 5
encr 3des
authentication pre-share
group 2
crypto isakmp key cisco@123 address 72.145.30.14
!
crypto ipsec transform-set MY-SET esp-aes esp-md5-hmac
mode tunnel
!
crypto map IPSEC-SITE-TO-SITE-VPN 10 ipsec-isakmp
set peer 72.145.30.14
set transform-set MY-SET
match address VPN-TRAFFIC
!
interface GigabitEthernet0/0
ip address 72.145.30.10 255.255.255.252
ip nat outside
ip virtual-reassembly in
duplex auto
speed auto
media-type rj45
no cdp enable
crypto map IPSEC-SITE-TO-SITE-VPN
!
interface GigabitEthernet0/1.10
encapsulation dot1Q 10
ip address 10.0.2.1 255.255.255.240
ip nat inside
ip virtual-reassembly in
no cdp enable
!
interface GigabitEthernet0/1.20
encapsulation dot1Q 20
ip address 10.0.2.17 255.255.255.248
ip nat inside
ip virtual-reassembly in
no cdp enable
!
ip nat inside source list 101 interface GigabitEthernet0/0 overload
ip route 0.0.0.0 0.0.0.0 72.145.30.9
!
ip access-list extended VPN-TRAFFIC
permit ip 10.0.2.0 0.0.0.255 10.0.0.0 0.0.0.255
!
access-list 101 deny ip 10.0.2.0 0.0.0.255 10.0.0.0 0.0.0.255
access-list 101 permit ip 10.0.2.0 0.0.0.255 any
ffw.mar.rt01#
crypto isakmp policy 5
encr 3des
authentication pre-share
group 2
crypto isakmp key cisco@123 address 72.145.30.10
!
crypto ipsec transform-set MY-SET esp-aes esp-md5-hmac
mode tunnel
!
crypto map IPSEC-SITE-TO-SITE-VPN 10 ipsec-isakmp
set peer 72.145.30.10
set transform-set MY-SET
match address VPN-TRAFFIC
!
interface GigabitEthernet0/0
ip address 72.145.30.14 255.255.255.252
ip nat outside
ip virtual-reassembly in
duplex auto
speed auto
media-type rj45
no cdp enable
crypto map IPSEC-SITE-TO-SITE-VPN
!
interface GigabitEthernet0/1.10
encapsulation dot1Q 10
ip address 10.0.0.1 255.255.255.240
ip nat inside
ip virtual-reassembly in
no cdp enable
!
interface GigabitEthernet0/1.20
encapsulation dot1Q 20
ip address 10.0.0.17 255.255.255.248
ip nat inside
ip virtual-reassembly in
no cdp enable
!
ip nat inside source list 101 interface GigabitEthernet0/0 overload
ip route 0.0.0.0 0.0.0.0 72.145.30.14
!
ip access-list extended VPN-TRAFFIC
permit ip 10.0.0.0 0.0.0.255 10.0.2.0 0.0.0.255
!
access-list 101 deny ip 10.0.0.0 0.0.0.255 10.0.2.0 0.0.0.255
access-list 101 permit ip 10.0.0.0 0.0.0.255 any
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-03-2019 04:23 PM
Here is my current config:
ffw.par.rt01
crypto isakmp policy 5 encr 3des authentication pre-share group 2 crypto isakmp key cisco@123 address 72.145.30.14 ! ! crypto ipsec transform-set MY-SET esp-aes esp-md5-hmac mode tunnel ! ! ! crypto map IPSEC-SITE-TO-SITE-VPN 10 ipsec-isakmp set peer 72.145.30.14 set transform-set MY-SET match address VPN-TRAFFIC ! ! ! ! ! interface GigabitEthernet0/0 ip address 72.145.30.10 255.255.255.252 ip nat outside ip virtual-reassembly in duplex auto speed auto media-type rj45 no cdp enable crypto map IPSEC-SITE-TO-SITE-VPN ! interface GigabitEthernet0/1 no ip address duplex auto speed auto media-type rj45 no cdp enable ! interface GigabitEthernet0/1.10 encapsulation dot1Q 10 ip address 10.0.2.1 255.255.255.240 ip access-group 110 in ip nat inside ip virtual-reassembly in no cdp enable ! interface GigabitEthernet0/1.20 encapsulation dot1Q 20 ip address 10.0.2.17 255.255.255.248 ip access-group 120 in ip nat inside ip virtual-reassembly in no cdp enable ! interface GigabitEthernet0/2 no ip address shutdown duplex auto speed auto media-type rj45 no cdp enable ! interface GigabitEthernet0/3 no ip address shutdown duplex auto speed auto media-type rj45 no cdp enable ! ip forward-protocol nd ! ! no ip http server no ip http secure-server ip nat inside source list 101 interface GigabitEthernet0/0 overload ip route 0.0.0.0 0.0.0.0 72.145.30.9 ! ip access-list extended VPN-TRAFFIC permit ip 10.0.2.0 0.0.0.255 10.0.0.0 0.0.0.255 ! ! ! access-list 101 deny ip 10.0.2.0 0.0.0.255 10.0.0.0 0.0.0.255 access-list 101 permit ip 10.0.2.0 0.0.0.255 any
ffw.mar.rt01
crypto isakmp policy 5 encr 3des authentication pre-share group 2 crypto isakmp key cisco@123 address 72.145.30.10 ! ! crypto ipsec transform-set MY-SET esp-aes esp-md5-hmac mode tunnel ! ! ! crypto map IPSEC-SITE-TO-SITE-VPN 10 ipsec-isakmp set peer 72.145.30.10 set transform-set MY-SET match address VPN-TRAFFIC ! ! ! ! ! interface GigabitEthernet0/0 ip address 72.145.30.14 255.255.255.252 ip nat outside ip virtual-reassembly in duplex auto speed auto media-type rj45 no cdp enable ! interface GigabitEthernet0/1 no ip address duplex auto speed auto media-type rj45 no cdp enable crypto map IPSEC-SITE-TO-SITE-VPN ! interface GigabitEthernet0/1.10 encapsulation dot1Q 10 ip address 10.0.0.1 255.255.255.240 ip access-group 110 in ip nat inside ip virtual-reassembly in no cdp enable ! interface GigabitEthernet0/1.20 encapsulation dot1Q 20 ip address 10.0.0.17 255.255.255.248 ip access-group 120 in ip nat inside ip virtual-reassembly in no cdp enable ! interface GigabitEthernet0/2 no ip address shutdown duplex auto speed auto media-type rj45 no cdp enable ! interface GigabitEthernet0/3 no ip address shutdown duplex auto speed auto media-type rj45 no cdp enable ! ip forward-protocol nd ! ! no ip http server no ip http secure-server ip nat inside source list 101 interface GigabitEthernet0/0 overload ip route 0.0.0.0 0.0.0.0 72.145.30.13 ! ip access-list extended VPN-TRAFFIC permit ip 10.0.0.0 0.0.0.255 10.0.2.0 0.0.0.255 ! ! ! access-list 101 deny ip 10.0.0.0 0.0.0.255 10.0.2.0 0.0.0.255 access-list 101 permit ip 10.0.0.0 0.0.0.255 any
My ACLs were quite a mess, and this configuration makes sense. But now my VPCS test timeouts:
ffw.mar.pc-res01
VPCS> ping 72.145.30.10 84 bytes from 72.145.30.10 icmp_seq=1 ttl=253 time=33.305 ms 84 bytes from 72.145.30.10 icmp_seq=2 ttl=253 time=17.636 ms 84 bytes from 72.145.30.10 icmp_seq=3 ttl=253 time=13.641 ms 84 bytes from 72.145.30.10 icmp_seq=4 ttl=253 time=35.256 ms 84 bytes from 72.145.30.10 icmp_seq=5 ttl=253 time=15.862 ms VPCS> ping 10.0.2.1 10.0.2.1 icmp_seq=1 timeout 10.0.2.1 icmp_seq=2 timeout 10.0.2.1 icmp_seq=3 timeout 10.0.2.1 icmp_seq=4 timeout 10.0.2.1 icmp_seq=5 timeout VPCS> ping 10.0.2.2 10.0.2.2 icmp_seq=1 timeout 10.0.2.2 icmp_seq=2 timeout 10.0.2.2 icmp_seq=3 timeout 10.0.2.2 icmp_seq=4 timeout 10.0.2.2 icmp_seq=5 timeout
On the router:
ffw.mar.rt01#ping 10.0.2.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.0.2.2, timeout is 2 seconds:
UUUUU
Success rate is 0 percent (0/5)
ffw.mar.rt01#show ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
Gateway of last resort is 72.145.30.13 to network 0.0.0.0
S* 0.0.0.0/0 [1/0] via 72.145.30.13
10.0.0.0/8 is variably subnetted, 4 subnets, 3 masks
C 10.0.0.0/28 is directly connected, GigabitEthernet0/1.10
L 10.0.0.1/32 is directly connected, GigabitEthernet0/1.10
C 10.0.0.16/29 is directly connected, GigabitEthernet0/1.20
L 10.0.0.17/32 is directly connected, GigabitEthernet0/1.20
72.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 72.145.30.12/30 is directly connected, GigabitEthernet0/0
L 72.145.30.14/32 is directly connected, GigabitEthernet0/0The routes seem correct, so I assume this is an issue with the VPN?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-06-2019 06:09 AM
Does anyone have an idea?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-06-2019 06:20 AM
ffw.par.rt01#show crypto session
Crypto session current status
Interface: GigabitEthernet0/0
Session status: DOWN
Peer: 72.145.30.14 port 500
IPSEC FLOW: permit ip 10.0.2.0/255.255.255.0 10.0.0.0/255.255.255.0
Active SAs: 0, origin: crypto map
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-06-2019 06:29 AM
I applied the crypto map on g0/1 on ffw.mar.rt01 instead of g0/0.
It's working now!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide