Site-to-site VPN to VLAN interface not working
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-05-2016 02:57 AM - edited 03-05-2019 07:36 AM
Heya,
Current situation:
- I got multiple customers connected with their hosts directly to the switch module of the router.
- Each customer has its own public IP block.
- Each customer has its own VLAN for his public IP block.
- Each customer has its own VLAN for their internal hosts wich need to communicate through their own site-to-site VPN tunnel.
- I got a ISR 4431 routers with 2 NIM-8 ports switch modules.
- On the router i got active BGP working.
Scenario:
I got a customer on VLAN 2 with a public IP adres of 18.x.x.2 which servers as one end of the VPN tunnel.
i got VLAN 22 with a private IP address of 192.168.237.254 which servers as the gateway for the hosts behind it for the traffic through the tunnel.
I got the IPSEC tunnel working as in it is active. However i can not seem to pass any traffic over it.
Goal:
I want each customer to be able to setup a site-to-site VPN connection towards their own public IP range and from there be able to access their own private IP range. Different customers could have the same internal private IP range.
My questions are:
Am i doing it right the way i am doing it now and the way i have configured it now and if so, why can't i pass any traffic over it (encaps and decaps stays 0), if i am doing it wrong, what would be the right way to achieve the goal?
Is my goal even possible with this hardware setup or am i obligated to use a different hardware setup? If so what setup should i better use?
Is it even possible to let different customers use the same internal private IP range or should i make sure every customer has its own private IP range?
If there are any further questions, please ask.
The config of router A is:
crypto isakmp policy 1
encr aes 256
hash sha512
authentication pre-share
group 14
lifetime 7800
crypto isakmp key secretpassword address 77.x.x.1
!
!
crypto ipsec transform-set TS esp-aes 256 esp-sha512-hmac
mode tunnel
!
!
!
crypto map MYMAP 1 ipsec-isakmp
set peer 77.x.x.1
set transform-set TS
set pfs group14
match address VPN
!
interface GigabitEthernet0/0/0
description This is the uplink
ip address 1.1.1.1 255.255.255.252
negotiation auto
!
interface Vlan2
description CUSTOMER1
ip address 18.x.x.2 255.255.255.192
crypto map MYMAP
!
interface Vlan22
description CUSTOMER1_INTERNAL
ip address 192.168.237.254 255.255.255.0
!
router bgp 2
bgp log-neighbor-changes
network 18.x.x.0 mask 255.255.252.0
rest output omitted
!
ip route 18.x.x.0 255.255.252.0 Null0
!
ip access-list extended VPN
permit ip 192.168.237.0 0.0.0.255 192.168.240.0 0.0.0.255
Output of different show commands router A:
RouterA#sh crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
18.x.x.2 77.x.x.1 QM_IDLE 1072 ACTIVE
RouterA#sh crypto ipsec sa
interface: Vlan2
Crypto map tag: MYMAP, local addr 18.x.x.2
protected vrf: (none)
local ident (addr/mask/prot/port): (192.168.237.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.240.0/255.255.255.0/0/0)
current_peer 77.x.x.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 18.x.x.2, remote crypto endpt.: 77.x.x.1
plaintext mtu 1422, path mtu 1500, ip mtu 1500, ip mtu idb Vlan2
current outbound spi: 0x577AC939(1467664697)
PFS (Y/N): Y, DH group: group14
inbound esp sas:
spi: 0x85C38CCD(2244185293)
transform: esp-256-aes esp-sha512-hmac ,
in use settings ={Tunnel, }
conn id: 2199, flow_id: ESG:199, sibling_flags FFFFFFFF80000048, crypto map: MYMAP
sa timing: remaining key lifetime (k/sec): (4608000/970)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x577AC939(1467664697)
transform: esp-256-aes esp-sha512-hmac ,
in use settings ={Tunnel, }
conn id: 2200, flow_id: ESG:200, sibling_flags FFFFFFFF80000048, crypto map: MYMAP
sa timing: remaining key lifetime (k/sec): (4608000/970)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
RouterA#sh crypto session
Crypto session current status
Interface: Vlan2
Session status: UP-ACTIVE
Peer: 77.x.x.1 port 500
Session ID: 0
IKEv1 SA: local 18.x.x.2/500 remote 77.x.x.1/500 Active
IPSEC FLOW: permit ip 192.168.237.0/255.255.255.0 192.168.240.0/255.255.255.0
Active SAs: 2, origin: crypto map
Any help is much appreciated, thanks in advance.
With kind regards,
Stefan
- Labels:
-
LAN Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-05-2016 09:24 AM
Hello,
which device is at the other side ? Can you post the full configs of both ends ? Do you have any NAT configured on the 4331 ??
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-05-2016 10:34 AM
Heya,
The device on the other side is a Sophos UTM 210, so not very handy to give a config of. Though i pulled of a screenshot on the settings to give you an idea:
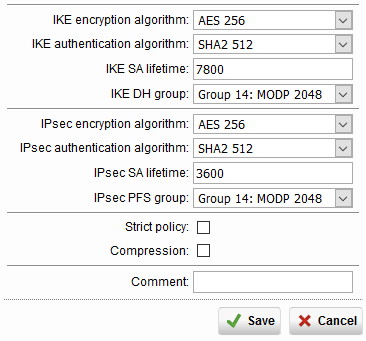
The log of the Sophos when i enable the VPN on that side:
The full config of the 4431 is as followed:
RouterA#sh run
Building configuration...
Current configuration : 5673 bytes
!
! Last configuration change at 11:45:52 GMT Mon Dec 5 2016 by x
!
version 15.5
service timestamps debug datetime msec
service timestamps log datetime msec
service password-encryption
no platform punt-keepalive disable-kernel-core
!
hostname RouterA
!
boot-start-marker
boot-end-marker
!
!
vrf definition Mgmt-intf
!
address-family ipv4
exit-address-family
!
address-family ipv6
exit-address-family
!
enable secret 5 sdfljkh24308dfsdl97
!
no aaa new-model
clock timezone GMT 1 0
clock summer-time GMT recurring
!
!
!
!
!
!
!
!
!
!
!
ip name-server 8.8.8.8 8.8.4.4
ip domain name x.com
!
!
!
!
!
!
!
!
!
!
subscriber templating
!
multilink bundle-name authenticated
!
!
!
!
license udi pid ISR4431/K9 sn Fxxxx3xxxxx
license boot level appxk9
!
spanning-tree extend system-id
!
username x secret 5 dsfljsdfkl239847kfjs89fnksdfn
!
redundancy
mode none
!
!
!
!
!
vlan internal allocation policy ascending
!
!
!
!
!
!
!
!
crypto isakmp policy 1
encr aes 256
hash sha512
authentication pre-share
group 14
lifetime 7800
crypto isakmp key secretpassword address 77.x.x.1
!
!
crypto ipsec transform-set TS esp-aes 256 esp-sha512-hmac
mode tunnel
!
!
!
crypto map MYMAP 1 ipsec-isakmp
set peer 77.x.x.1
set transform-set TS
set pfs group14
match address VPN
!
!
!
!
!
!
!
!
!
!
!
!
interface Loopback0
no ip address
!
interface GigabitEthernet0/0/0
description This is the uplink
ip address 1.1.1.1 255.255.255.252
negotiation auto
!
interface GigabitEthernet0/0/1
no ip address
shutdown
negotiation auto
!
interface GigabitEthernet0/0/2
no ip address
shutdown
negotiation auto
!
interface GigabitEthernet0/0/3
no ip address
shutdown
negotiation auto
!
interface GigabitEthernet0/1/0
switchport mode trunk
!
interface GigabitEthernet0/1/1
switchport mode trunk
!
interface GigabitEthernet0/1/2
switchport mode trunk
!
interface GigabitEthernet0/1/3
switchport mode trunk
!
interface GigabitEthernet0/1/4
switchport mode trunk
!
interface GigabitEthernet0/1/5
switchport mode trunk
!
interface GigabitEthernet0/1/6
switchport access vlan 2
switchport mode access
!
interface GigabitEthernet0/1/7
switchport access vlan 22
switchport mode access
!
interface GigabitEthernet0/2/0
shutdown
!
interface GigabitEthernet0/2/1
shutdown
!
interface GigabitEthernet0/2/2
shutdown
!
interface GigabitEthernet0/2/3
shutdown
!
interface GigabitEthernet0/2/4
shutdown
!
interface GigabitEthernet0/2/5
shutdown
!
interface GigabitEthernet0/2/6
shutdown
!
interface GigabitEthernet0/2/7
shutdown
!
interface GigabitEthernet0
vrf forwarding Mgmt-intf
no ip address
negotiation auto
!
interface Vlan1
no ip address
!
interface Vlan2
description CUSTOMER1
ip address 18.x.x.2 255.255.255.192
crypto map MYMAP
!
interface Vlan22
description CUSTOMER1_INTERNAL
ip address 192.168.237.254 255.255.255.0
!
router bgp 2
bgp log-neighbor-changes
network 18.x.x.0 mask 255.255.252.0
neighbor 1.1.1.2 remote-as 1
neighbor 1.1.1.2 prefix-list AS2-PREFIXES out
!
ip forward-protocol nd
no ip http server
no ip http secure-server
ip tftp source-interface GigabitEthernet0
ip route 18.x.x.0 255.255.252.0 Null0
ip ssh logging events
ip ssh version 2
!
!
ip access-list extended VPN
permit ip 192.168.237.0 0.0.0.255 192.168.240.0 0.0.0.255
ip access-list extended SSH_ACCESS
permit ip 192.168.240.0 0.0.0.255 any
permit ip 192.168.237.0 0.0.0.255 any
permit ip host 77.x.x.1 any
permit ip host 18.x.x.8 any
!
!
ip prefix-list AS2-PREFIXES seq 5 permit 18.x.x.0/22
!
!
control-plane
!
banner login ^C
#############################################################################
# This device is protected by law. Unauthorized access is prohibited. #
# If you notice any kind of abuse against this system please report #
# this to: x@x.nl. #
# #
# This device is property of company X #
#############################################################################
^C
!
line con 0
logging synchronous
history size 256
stopbits 1
line aux 0
stopbits 1
line vty 0 4
access-class SSH_ACCESS in
no motd-banner
logging synchronous
login local
history size 256
monitor
transport input ssh
!
!
end
No i have no NAT configured on the Cisco, i have NAT configured on the Sophos, because the office needs internet through it.
I prefer to solve it without enabling NAT on the Cisco, due to performance.
Greetings Stefan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-05-2016 12:26 PM
Stefan,
I just asked about NAT because if you NAT, you would need to exclude VPN traffic from the interesting traffic that needs to be translated. Either way, I think the problem is with your BGP configuration:
Your Vlan2 interface has a /26 mask, however, in BGP, you are advertising a /22 mask:
interface Vlan2
description CUSTOMER1
ip address 18.x.x.2 255.255.255.192
crypto map MYMAP
!
router bgp 2
bgp log-neighbor-changes
network 18.x.x.0 mask 255.255.252.0
neighbor 1.1.1.2 remote-as 1
neighbor 1.1.1.2 prefix-list AS2-PREFIXES out
That means neighbor 1.1.1.2 never receives the route. Try and change the network statement to:
network 18.x.x.0 mask 255.255.255.192
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2016 12:00 AM
Heya,
Thanks for your input.
I do not quite understand your answer.
If BGP is wrong, how is it possible that the VPN connection itself works?
As extra info: If i put a host behind VLAN 2 with for example ip 18.x.x.10, that host has internet connection and traffic flows from/to that host without problem.
Greetings Stefan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2016 12:10 AM
Hello Stefan,
I don't know, honestly, since I don't know exactly how the other sides handles the incoming traffic.
On your 4331, can you issue the following command:
'sh ip bgp neighbors 1.1.1.2 advertised routes'
The output should look like this:
R1#sh ip bgp neighbors 1.1.1.2 ad
R1#sh ip bgp neighbors 1.1.1.2 advertised-routes
BGP table version is 2, local router ID is 1.1.1.1
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
*> 18.1.1.0/26 0.0.0.0 0 32768 i
Total number of prefixes 1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2016 12:38 AM
Heya,
The ouput is as followed:
RouterA#sh ip bgp neighbors 1.1.1.2 advertised-routes
BGP table version is 4952446, local router ID is 1.1.1.1
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
*> 18.x.x.0/22 0.0.0.0 0 32768 i
Total number of prefixes 1
PS: I can not advertise anything lower then a /24 towards my ISP, so advertising a /26 is not an option.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2016 01:25 AM
Hello Stefan,
my bad. The idea was that you can only advertise in BGP what is in the routing table. You have the Null route configured with a /22 mask to take care of that, I overlooked that.
Either way, the problem remains that no traffic is passed over the VPN. I wonder if the 'mode tunnel' in your transform set configuration is causing that. Can you take that out ?