- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: Strange Routing Issue to Internet
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2021 09:17 PM
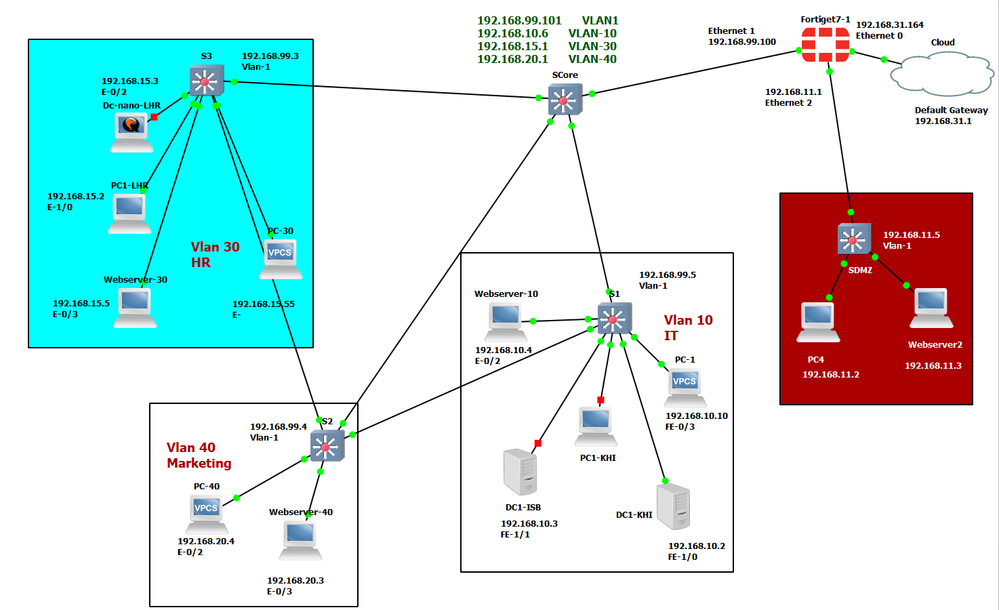
Above is my network setup, I have a DMZ zone and then the rest of the LAN. The DMZ is directly connected to fortigate and the rest of the LAN is connected with VLAN 1 of the switch to fortigate, the situation is as below:
- None of the Client PCS can ping or access the Internet.
- None of the clients can access 192.168.99.100(The ip of the Fortigate interface on the LAN side.
- All of the PCS can access 192.168.99.101(The Vlan 1 ip of Core Switch).
- All of the switches can access Internet as well as 192.168.99.100
- All of the PCs can access other PCs on other Vlans.
- The Core Switch Has a default route to 192.168.99.100
- The Other Switches Have default route to 192.168.99.101(Vlan 1 ip of Core Switch)
- All PCs have default routes to their respective VLAN ip on Core Switch.
- The DMZ network PCS can access the Internet perfectly without any issue but the LAN network PCs cant.
I doubt this can be a Fortigate issue as the Switches can access the WAN fine with their 99.0 subnets and they are in the same policy as the rest of the LAN subnets.
How can I allow access to the Internet to LAN Pcs.
Any help is appreciated as I am stuck in this for 2 days and going crazy.
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-18-2021 04:46 AM - edited 09-18-2021 04:50 AM
Hello
what makes you think it’s NOT the firewall - if your switchs can access the internet but you vlan clients cannot but can ping each other then it does seem to suggest to be the FW -
I assume the fw is performing NAT if so does it’s nat policy include the client vlans
Also does the FW have routing knowledge of the client vlans?
edited - lastly fyi icmp echo-reply could be disabled on the FW so even if you had correct routing you may be not able to ping the FW
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2021 10:39 PM
Hello,
can you post the running config of the Cisco core switch, as well as the config file of the Fortigate ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2021 11:02 PM
Here is the config of core switch
version 15.2 service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption service compress-config ! hostname SCore ! boot-start-marker boot-end-marker ! ! ! no aaa new-model ! ! ! ! ! ! ! ! ip cef no ipv6 cef ! ! ! spanning-tree mode pvst spanning-tree extend system-id ! vlan internal allocation policy ascending lldp run ! ! ! ! ! ! ! ! ! ! ! ! ! ! interface GigabitEthernet0/0 switchport mode access media-type rj45 duplex full no negotiation auto ! interface GigabitEthernet0/1 switchport trunk encapsulation dot1q switchport mode trunk media-type rj45 duplex full no negotiation auto ! interface GigabitEthernet0/2 switchport trunk encapsulation dot1q switchport mode trunk media-type rj45 duplex full no negotiation auto ! interface GigabitEthernet0/3 switchport trunk encapsulation dot1q switchport mode trunk media-type rj45 duplex full no negotiation auto ! interface GigabitEthernet1/0 media-type rj45 duplex full no negotiation auto ! interface GigabitEthernet1/1 media-type rj45 duplex full no negotiation auto ! interface GigabitEthernet1/2 media-type rj45 duplex full no negotiation auto ! interface GigabitEthernet1/3 media-type rj45 duplex full no negotiation auto ! interface Vlan1 ip address 192.168.99.101 255.255.255.0 ! interface Vlan10 ip address 192.168.10.6 255.255.255.0 ! interface Vlan30 ip address 192.168.15.1 255.255.255.0 ! interface Vlan40 ip address 192.168.20.1 255.255.255.0 ! ip forward-protocol nd ! no ip http server no ip http secure-server ! ip route 0.0.0.0 0.0.0.0 192.168.99.100 ! ! ! ! ! control-plane !
as for fortigate config do you need the output of show full-configuration???? sorry i am a noob at fortigate.
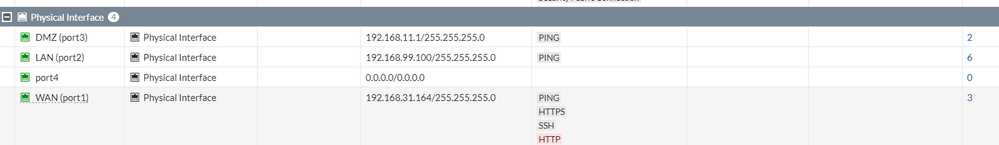
I have attached images in the original post of the interfaces etc.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2021 11:30 PM
Hello,
which switch model is this ? Usually, a layer 3 switch would have a line 'ip routing' in the config, do you have that enabled ?
Score#conf t
Score(config)#ip routing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2021 11:36 PM
It's is an old l3 image of a Cisco switch and yes the IP routing is enabled but not showing up in the config, it also doesn't show the switchport access vlan command but it works.
As I said in the original post all the vlans are able to connect to each other through this switch using IP routing.
All the switches also can ping and access internet using vlan 1 ips just not the client pcs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-18-2021 12:53 AM
Hello,
can you ping the Fortigate from any of the other SVIs configured on the Cisco ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-18-2021 01:12 AM
How do you propose I do that, as the default route that is connected to fortigate is through vlan 1 ips i.e. .90.0. and to check other svis I might have to define a new route maybe?
Other switches can also access the Fortigate but they are also on vlan 1 so that doesn't count I think.
Sorry but I am still learning so it might be a bit frustrating for you but I am eager to learn.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-18-2021 02:10 AM
Hello
on the core switch, type:
ping 192.168.99.100 source vlan x
That basically pings the Fortigate from other vlans. Do you get a response ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-18-2021 03:46 AM
Just checked and no the other SVIs cant ping the 99.100 interface.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-18-2021 04:46 AM - edited 09-18-2021 04:50 AM
Hello
what makes you think it’s NOT the firewall - if your switchs can access the internet but you vlan clients cannot but can ping each other then it does seem to suggest to be the FW -
I assume the fw is performing NAT if so does it’s nat policy include the client vlans
Also does the FW have routing knowledge of the client vlans?
edited - lastly fyi icmp echo-reply could be disabled on the FW so even if you had correct routing you may be not able to ping the FW
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-18-2021 05:09 AM - edited 09-18-2021 05:23 AM
Thank you for the reply, I will try to answer your questions in bold below"
What makes you think it’s NOT the firewall - if your switchs can access the internet but you vlan clients cannot but can ping each other then it does seem to suggest to be the FW -
The subnets of the switches vlan 1 as well as the other vlans are in the same policy definition on the firewall so if one is working the others should too thats why I think its an internal LAN issue.
I assume the fw is performing NAT if so does it’s nat policy include the client vlans
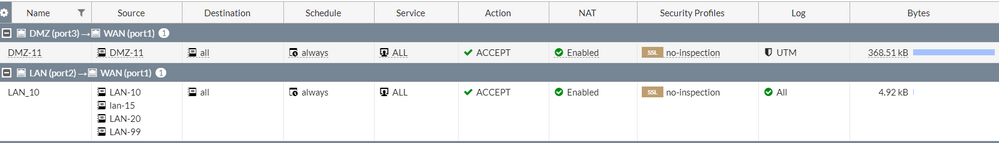
As stated above yes, I am attaching a pic of the LAN policy and DMZ
Also does the FW have routing knowledge of the client vlans?
The firewall only has 2 simple policy defined, 1 is allowing Lan(All 4 subnets of LAN) to Access Wan and the other is allowing DMZ to allow WAN, the policy is is working for DMZ and the .90.X subnet of LAN but not for anything else
edited - lastly fyi icmp echo-reply could be disabled on the FW so even if you had correct routing you may be not able to ping the FW
No I have specifically allowed ping request in the policy, pic attached below
EDIT: Also adding another picture of the policy allowing the 99.x series subnet
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-18-2021 05:48 AM
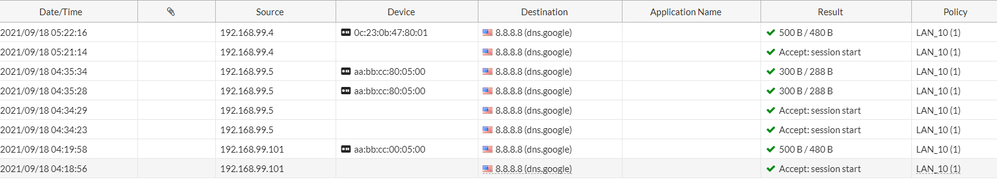
I Ran a wireshark trace and saw that the packets were getting rejected as they couldnt find the LAN subnets, add a static route back to the LAN ips on fortigate and solved the problem.
Thanks for the help guys.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-18-2021 08:58 AM
Hello
congratulations and thanks for the update
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-18-2021 09:48 AM
Hello @samipk1234 ,
thanks for your feedback that provides an happy end to your issue rated as it deserves.
Yes the Fortigate firewall needs static routes for internal LAN subnets with next-hop the core switch IP address on the common IP subnet ( 192.168.99.0 I guess and the next-hop to core switch should be 192.168.99.101)
Best Regards
Giuseppe
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide