- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: Vlan default gateway?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2020 07:13 PM - edited 01-30-2020 07:19 PM
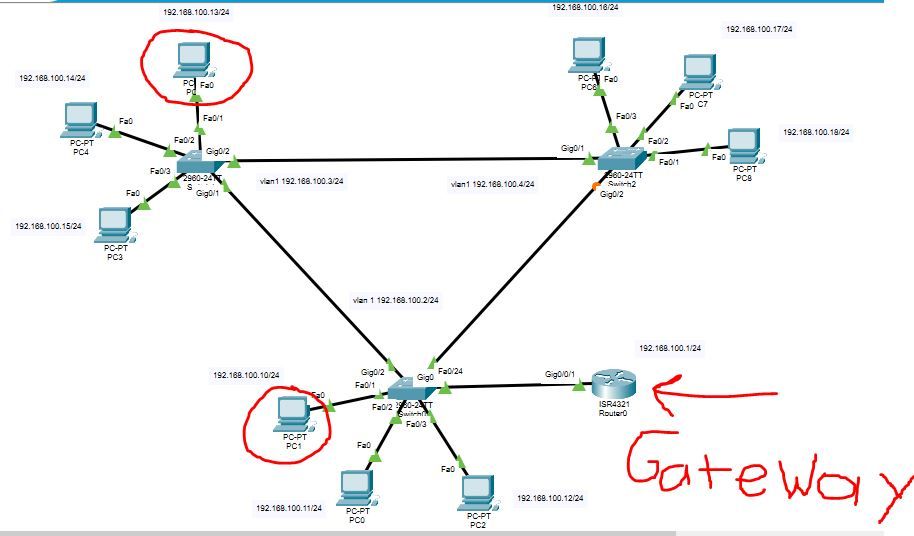
I am missing one little final step here and I can't seem to figure it out. Basically, I created a Vlan 2 and I can't get any client computer that is on that Vlan (Vlan 2) to ping the router. The two clients on Vlan 2 can ping each other but not the router. Clients that are still on Vlan 1 can ping the router. All three switches in the packet tracer image below can ping the router as well.
I'm using Packet Tracer and I'm only using a single subnet (192.168.100.0/24) for both Vlans. I do not want to use more than one subnet for this lab exercise.
I'm going to take a wild guess and ask, do vlans other than the default Vlan 1 need a gateway? If so, the 2960 Cisco switch doesn't allow me to do that.
The two circled computers in the image below are on vlan 2.
Solved! Go to Solution.
- Labels:
-
Other Routing
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2020 01:30 PM
Okay, that makes more sense.
Then you would need to use extended acls ie. you would deny traffic between the vlans/IP subnets but then permit any other traffic so you could access the WAN on the other side of the router.
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2020 05:50 PM - edited 01-31-2020 05:51 PM
Occupying the above configurations, you can deny routing between vlan, simply, with this acl:
access-list 1 deny 192.168.100.0 0.0.0.255
access-list 1 permit any
interface g0/0/1.2
ip access-group 1 out
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2020 09:05 AM - edited 02-01-2020 09:09 AM
You must keep in mind that the communication is like a two-way road, so Router 0 must have a route to the 220.0 network
Router 1 must have a route to network 220.0 and two routes to networks 100.0 and 200.0 for the way back
Finally, Router 2 must have two routes to 100.0 and 200.0 networks as well.
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2020 07:41 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2020 07:58 PM - edited 01-30-2020 08:00 PM
Each vlan must have a different network.
You can try this:
1-Use the 192.168.200.0/24 network for vlan 2
2-Assign an IP of the new network to the Vlan 2 PCs, with the correct mask and ip 192.168.200.1 as the gateway.
3-Be sure to leave the links between switches in trunk mode.
The link that connects the switch to the router must be in trunk mode as well.
4-Make these changes on the router:
R(config)#interface g0/0/1
R(config-if)#no ip address
R(config-if)#exit
R(config)#interface g0/0/1.1
R(config-subif)#encapsulation dot1q 1
R(config-subif)#ip address 192.168.100.1 255.255.255.0
R(config-subif)#exit
R(config)#interface g0/0/1.2
R(config-subif)#encapsulation dot1q 2
R(config-subif)#ip address 192.168.200.1 255.255.255.0
R(config-subif)#exit
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2020 10:16 AM
Why would I create a vlan AND create a new subnet? As far as separating the network, both would accomplish the same thing. Seems like double the work to accomplish the same thing. The whole idea of vlans is to separate/segment the network. It doesn't make since to me to create a whole other subnet as well.
I'm not an expert but it just seems like you should to be able to use ONE subnet with TWO different vlans.
I want to know how to do that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2020 10:32 AM
The idea of the vlans is to have more than one broadcast domain on the same switch.
Without vlans, this would be impossible.
If all devices are on the same network, the concept of vlans loses meaning.
As I mentioned before, the vlan need to have a different network for each one.
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2020 12:45 PM
What is the benefit of having more than one broadcast domain? Would this reduce traffic and reduce latency?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2020 11:06 AM
Vlans create L2 domains and if you want to communicate between vlans you need to route between them which means each vlan needs a L3 interface (which is the client's default gateway in that vlan) and each L3 interface is usually in a different IP subnet.
Bearing that in mind look at your diagram and you should be able to see the issue ie. where is the L3 interface for vlan 2 ?
Luis provided you with a configuration as to how to set this up.
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2020 12:31 PM - edited 01-31-2020 01:24 PM
Thanks for the reply.
The think I should have mentioned before was that I DO NOT want the vlans to communicate between each other. Once the clients are on either vlan (vlan 1 or vlan 2) make the connection back to the router using sub-interfaces, they can communicate with each. How do I block the communication between the vlans?
Should I create a standard access-list on the router to block subnet x.x.x.x that is on vlan 1 from accessing subnet x.x.x.x that is on vlan2?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2020 01:06 PM
Based on your diagram if you do not want the vlans to communicate with each other then not sure what the router is meant to be doing as it does not provide connectivity to anything else.
But yes if you wanted to block access between vlans/IP subnets you can use acls, usually extended acls but again as the router is not providing access to any external networks you could use a standard acl if you wanted to.
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2020 01:23 PM
I haven't finished drawing out the rest of the network diagram yet. Basically, the other side of the router would be the WAN side.
This whole thing came about because I wanted to provide guess (public) with wifi and I wanted to keep them off the production network. By using just vlans alone I thought I could do that, but I'm learning now that I need to create another subnet for the wifi vlan and sub-interfaces for each vlan and an acl on the router.
This is why I don't want the two vlans to communicate with each other. Wanting to keep the public (wifi clients) off the production network.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2020 01:30 PM
Okay, that makes more sense.
Then you would need to use extended acls ie. you would deny traffic between the vlans/IP subnets but then permit any other traffic so you could access the WAN on the other side of the router.
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2020 05:50 PM - edited 01-31-2020 05:51 PM
Occupying the above configurations, you can deny routing between vlan, simply, with this acl:
access-list 1 deny 192.168.100.0 0.0.0.255
access-list 1 permit any
interface g0/0/1.2
ip access-group 1 out
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2020 07:01 AM - edited 02-01-2020 08:40 AM
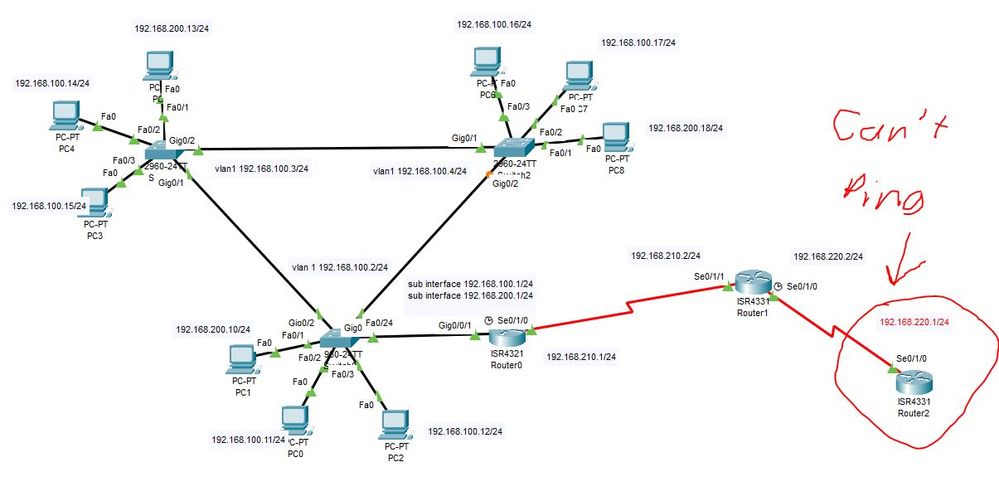
Yes this did work!
How do I get to the next hop? I have added two more routers and want my clients that are on either vlan 1 or vlan 2 to access the added networks (192.168.210.0/24 and 192.168.220.0/24).
How can I get my clients to PING 192.168.220.1?
Running config on Router0
Building configuration...
Current configuration : 1282 bytes
!
version 15.4
no service timestamps log datetime msec
no service timestamps debug datetime msec
no service password-encryption
!
hostname R1
!
!
!
enable secret 5 $1$mERr$AOT12whiezfAY5sfbuKC3.
!
!
!
!
!
!
ip cef
no ipv6 cef
!
!
!
username keith secret 5 $1$mERr$AOT12whiezfAY5sfbuKC3.
!
!
!
!
!
!
!
!
!
!
spanning-tree mode pvst
!
!
!
!
!
!
interface GigabitEthernet0/0/0
no ip address
duplex auto
speed auto
shutdown
!
interface GigabitEthernet0/0/1
no ip address
duplex auto
speed auto
!
interface GigabitEthernet0/0/1.1
encapsulation dot1Q 1 native
ip address 192.168.100.1 255.255.255.0
!
interface GigabitEthernet0/0/1.2
encapsulation dot1Q 2
ip address 192.168.200.1 255.255.255.0
ip access-group 1 out
!
interface Serial0/1/0
ip address 192.168.210.1 255.255.255.0
clock rate 2000000
!
interface Serial0/1/1
no ip address
clock rate 2000000
!
interface Vlan1
no ip address
!
ip classless
ip route 192.168.220.0 255.255.255.0 192.168.210.2
!
ip flow-export version 9
!
!
access-list 1 deny 192.168.100.0 0.0.0.255
access-list 1 permit any
!
banner motd ^C
*********************************************
Welcome to Pizza Planet!!!
*********************************************
^C
!
!
!
!
!
line con 0
login local
!
line aux 0
!
line vty 0 4
login
!
!
!
end
R1#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2020 08:41 AM
You can achieve connection through static routes or a routing protocol, such as ripv2. Using RIPv2 would be something like this:
R0(config)#router rip
R0(config-router)#no auto summary
R0(config-router)#version 2
R0(config-router)#network 192.168.100.0
R0(config-router)#network 192.168.200.0
R0(config-router)#network 192.168.210.0
R1(config)#router rip
R1(config-router)#no auto-summary
R1(config-router)#version 2
R1(config-router)#network 192.168.210.0
R1(config-router)#network 192.168.220.0
R2(config)#router rip
R2(config-router)#no auto-summary
R2(config-router)#version 2
R2(config-router)#network 192.168.220.0
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2020 08:54 AM
I did do a static route, but I'm still not able to PING 192.168.220.1 from any client computer. I can PING from Router0 to 192.168.220.1 successfully.
Command I used:
ip route 192.168.220.0 255.255.255.0 192.168.210.2
I don't want to use any routing protocols yet. I want to do anything manually first so I understand what these routing protocols are doing.
After adding that static route to Router0, why can't my clients PING 192.168.220.1?
I edited the previous post above to show my running config on Router0.
Thanks again for all your help;)
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide