- Cisco Community
- Technology and Support
- Networking
- Routing
- VPN redundant design
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
VPN redundant design
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-03-2012 12:37 AM - edited 03-04-2019 03:53 PM
Hi ,
I would like to implement at a customer a redundant VPN design .
The situation goes like this
Branch office . 1 ISP line - 1 Router
Headquarters - 2 ISP lines - 1 Router 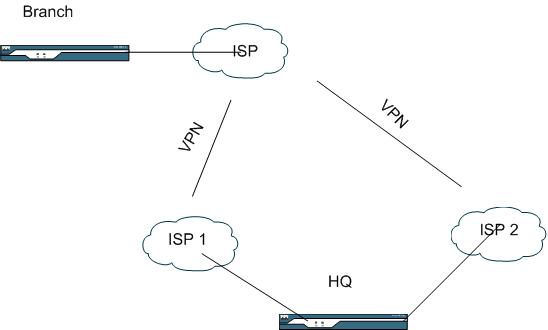
( I usualy have 2 ISP in the branch and 2 Routers in the HQ and provide tunnel redundancy with OSPF but the customer in this case doesn`t have the resources )
How is the best aproach ?
Thanks
- Labels:
-
Other Routing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-03-2012 06:34 PM
There is a very simple solution to this. Here it is:
- on the branch router side:
1) your configuration is a very straight forward IPSec tunnel, nothing special.
- on the HQ router side:
1) assign loopback0 with a public IP address that is reachable over the Internet,
2) configure eBGP on the HQ routers with ISP1 and ISP2 and advertise loopback0 to them. This again is also a simple task. Take a look at http://wiki.imagestream.com/wiki/BGP/Examples/Example_1:One_router_with_two_peers
3) configure IPSec on the HQ router, again this is a very straight forward IPSec configuration with one exception. You need to add the command "crypto map local-address loopback0" or something to that effect. That will source the IPSec peering point from the loopback interface. After that, go ahead and apply the "crypto map vpn" both physical interfaces facing ISP1 and ISP2 on the HQ router.
Once you've confirmed that VPN is up and running between branch and HQ, go ahead and "admin" down one of the eBGP peers on either ISP1 or ISP2 on the HQ router and your VPN tunnel will NOT go down because your loopback 0 interface is still reachable by the branch router.
Easy right?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-03-2012 11:14 PM
Hi ,thanks for your answer ,
Easy if the client had BGP connections , but we are talking about standard ISP connections , one fixed IP per ISP , two different ISP`s.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-04-2012 12:30 AM
Hi,
On the branch router have you tried confiuring two peers under your crypto map?
One is configured as the preferred peer and the other backup.
For example
crypto map XYZ 10 ipsec-isakmp
set transform-set ABC
set peer 10.1.1.1 prefer
set peer 10.1.1.2
match address 101
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-04-2012 10:05 AM
Since BGP is not an option for you. Here is another option to think about:
on the branch router:
create loopback0 with a public IP address
create loopback1 with a public IP address
On the HQ router:
create loopback0 with a public IP address
static route for branch router loopback0 with next hop of ISP1
static route for branch router loopback1 with next hop of ISP2
on the branch router:
create a GRE tunnel between branch router lo0 and HQ router loopback0
create a GRE tunnel between branch router lo1 and HQ router loopback0
Now encapsulate GRE inside with your IPsec
Now run ospf inside the GRE tunnel
On the HQ router:
create a GRE tunnel between HQ router lo0 and branch router using loopback0
create a GRE tunnel between HQ router lo0 and branch router using loopback1
now encapsulate GRE inside your IPSec tunnel
Now run OSPF inside the GRE tunnel
Now you have multiple VPN tunnels between branch router and HQ. shutdown either
ISP1 or ISP2 will have NO impact for connecivity between branch router and HQ.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
