- Cisco Community
- Technology and Support
- Networking
- Routing
- WAN & LAN Configurations
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-16-2018 07:18 PM - edited 03-05-2019 10:59 AM
Hello,
I need to configure my network to have an internal LAN and an external WAN, but am hitting a wall about how to do so. I created VLANs for the different departments and now I think I need to configure the external link to the ISP via EIGRP, OSPF, or BGP, but am not sure how to. Also the different nodes on different VLANs cannot ping to each other, is that supposed to be like that?
Attaching project file below.
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2018 01:24 PM
Hello
See attached Packet-tracer using NAT
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2018 04:34 AM
If your ISP told you to use 1.1.1.1/24, they should have also indicated an IP for their router and if a dynamic routing protocol is being used (EIGRP, OSPF, BGP), they should have provided you information on how to peer with them. (Often, for Internet access, you just use a default static route.)
As to different VLAN hosts being unable to ping each other, you need to route between the VLAN networks (you've only mentioned 192.168.1.0/24, did you subnet this or do you have other private networks for those VLANs?) and you should insure the hosts have a gateway IP.
PS:
If the above is "greek" to you, might want to obtain some (paid) network consultation to help configure your network. That said, your ISP might provide further assistance and you can often obtain lots of assistance on these forums too.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2018 06:30 AM
That did sound greek to me so I might need to resort to network consultation here! Is there a certain thread to do that in?
To go to/from a private IP address space, your LAN 192.168.1.0/24, to/from the Internet, you need to NAT.
NAT through the CLI through R1?
If your ISP told you to use 1.1.1.1/24, they should have also indicated an IP for their router and if a dynamic routing protocol is being used (EIGRP, OSPF, BGP), they should have provided you information on how to peer with them. (Often, for Internet access, you just use a default static route.)
How do you just use a default static route?
As to different VLAN hosts being unable to ping each other, you need to route between the VLAN networks (you've only mentioned 192.168.1.0/24, did you subnet this or do you have other private networks for those VLANs?) and you should insure the hosts have a gateway IP.
The VLANS are on their own private networks right now! The hosts meaning the PCs? Is the gateway IP usually the IP of the Ethernet port they are connected to?
Can't thank you enough for your help!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2018 07:06 AM
Not sure if there's a better thread. Cisco used to have a separate learner's forum site, but I believe it's been merged with this site's.
"NAT through the CLI through R1?"
I've not seen your topology, but if R1 is your Internet connected router, that's usually where you would perform NAT. Using the CLI to configure it would be one way, although Cisco might have some configuration tools (NB: I'm unsure about such tools still being available, haven't used any, myself, in years) that would allow you to configure it without using NAT.
"The hosts meaning the PCs? Is the gateway IP usually the IP of the Ethernet port they are connected to?"
Host would be any devices with IPs. The gateway IP is the IP for the router/L3-switch for getting to other networks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2018 05:05 AM - edited 10-17-2018 07:10 AM
Hello
All you configuration is incorrect, you have duplicate L3 interfaces on your access switches and your hosts are not in the correct ip address range of any vlan you have specified.
Attached is an updated packet tracker without using NAT
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2018 06:26 AM - edited 10-17-2018 10:18 AM
Paul Driver,
Thank you! So now I need to basically configure NAT on R1 in order to interface with the ISP router? And create a static IP for the routers that converts it to 1.1.1.1 some how? Once I figure out how to set up the WAN protocols I should be able to ping to the hosts on the LAN right?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2018 07:29 AM - edited 10-17-2018 07:31 AM
Hello
@BSK922 wrote:
Paul Driver,
Thank you! So now I need to basically configure NAT on R1 in order to interface with the ISP router? And create a static IP for the routers that converts it to 1.1.1.1 some how? Once I figure out how to set up the WAN protocols I should be able to ping to the hosts on the LAN right? And all the hosts have to ping to each other so I think I also need to add intervlan routing.
No you don't need to NAT if you don't want to however it all depends on what exactly you wish to accomplish. - You configuration was incorrect, what i have done in the amend packet tracker file doesn't use NAT:
1) Changed the end hosts ip addressing to relate to the 3 vlans subnets you had already created and added those hosts to these vlans on the access switches
2) removed all the l3 interfaces on all the access switch, which were all running the exact same ip address
3) Created an additional L3 interface ( vlan 12) on your core switch so to connect to its upstream rtr, and added its related interface to that vlan
Created a static default route on the core switch to point to its upstream rtr
4) On first upstream rtr, added 3 x static routes pointing back to your core switch for vlan 10--20-30 subnets
Created a bgp peer with the upsteam isp router and advertised its connected interfaces and redistributed the static routes towards this ISP router
5) On the ISP router , Changed the interface attaching the web server to the correct subnet of the webserver, advertised this into bgp
6) Changed webserver default gateway to point to the isp router.
At this point the webserver began to communicate with all yours hosts in vlan 10.20.30 and vice versa
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2018 08:23 AM
Thank you so much you are a life saver! I do have to do NAT though, do you know the commands needed to configure NAT?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2018 01:24 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2018 08:16 AM
Hi,
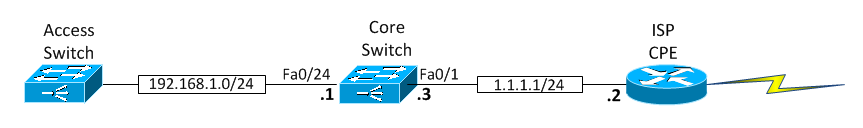
Here you go a design based on your requirement.
Hypothesis: you hav a core switch (Layer 3 switch) and the core switch connects to the ISP router on port Fa0/1, ISP router agree to use IP 1.1.1.2/24 and core switch will use the 1.1.1.3/24 on WAN side.
Access Switch connected on the port Fa0/24 of Core Switch. Fa0/24 will be in TRUNK and VLAN 50 is to be created for LAN 192.168.1.0/24.
Ask ISP to implement EIGRP 10 on their router as dynamic routing and provide the IP address 1.1.1.2 mask 255.255.255.0.
Here is the configuration that you will put in the Core Switch (the configuration might need to be reviewed based on the model/IOS version of your core switch if you have one):
vlan 50
name LAN
Interface vlan 50
description LAN_USER
ip address 192.168.1.1 255.255.255.0
no shut
Interface Fa0/24
switchport
switchport trunk allowed vlan 50
switchport mode trunk
switchport trunk encapsulation dot1q
no shut
Interface F0/1
description
no switchport
ip address 1.1.1.3 255.255.255.0
router eigrp 10
network 192.168.1.0 0.0.0.255
network 1.1.1.0 0.0.0.255
passive-interface default
no passive-interface Fa0/24
no passive-interface Fa0/1
HTH,
Mazzz
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2018 08:17 AM
show ip route
show ip eigrp topology
show ip route eigrp
etc....
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide