A set of interface access rules can cause the Cisco Adaptive Security Appliance to permit or deny a designated host to access another particular host with a specific network application (service). When there is only one client, one host and one service, you need only a minimum number of lines in an interface rule set. However, as the number of clients, servers, and services increases, the number of rules that you need for each individual access type can increase and become unmanageable.
A better approach is to introduce object grouping. This solution allows you to arbitrarily group hosts, resources, or services that share the same policy, which optimizes the access rules.
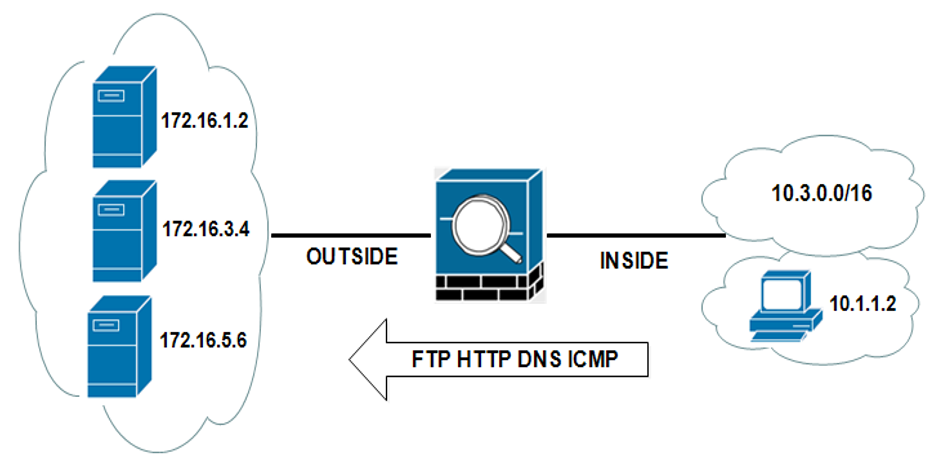
In this scenario the ASA controls traffic between an internal enterprise network that is connected over the inside interface and an external network that is connected over the outside interface.
The internal subnet 10.3.0.0/16 and the internal client 10.1.1.2 should both have permanent HTTP,FTP,DNS and ICMP access to a group of external servers (172.16.1.2, 172.16.3.4 and 172.16.5.6)
Creates a network object for the the network 10.3.0.0/16 and the host 10.1.1.2:
object network NETWORK-CLIENT
subnet 10.3.0.0 255.255.255.0
!
object network PC-CLIENT
host 10.1.1.2
Creates a network object for the external servers:
object network SERVER-A
host 172.16.1.2
!
object network SERVER-B
host 172.16.3.4
!
object network SERVER-C
host 172.16.5.6
Creates a network object group for the clients:
object-group network INTERNAL
network-object object NETWORK-CLIENT
network-object object PC-CLIENT
Creates a network object group for the servers:
object-group network EXTERNAL-SERVERS
network-object object SERVER-A
network-object object SERVER-B
network-object object SERVER-C
Creates a service object group:
object-group service CLIENT-SERVICES
service-objecticmp echo
service-objecttcp destination eq ftp
service-objecttcp destination eq http
service-object udp destination eq domain
Configure an ACL that uses network and service object groups:
access-list INSIDE-ACL extended permit object-group CLIENT-SERVICES object-group INTERNAL Object-group EXTERNAL-SERVERS
Apply the ACL inbound of the inside interface:
access-group INSIDE-ACL in interface inside
Verify the ACL configuration:
ciscoasa# show run object
object network NETWORK-CLIENT
subnet 10.3.0.0 255.255.255.0
object network PC-CLIENT
host 10.1.1.2
object network SERVER-A
host 172.16.1.2
object network SERVER-B
host 172.16.3.4
object network SERVER-C
host 172.16.5.6
ciscoasa#
ciscoasa# show run object-group
object-group network INTERNAL
network-object object NETWORK-CLIENT
network-object object PC-CLIENT
object-group network EXTERNAL-SERVERS
network-object object SERVER-A
network-object object SERVER-B
network-object object SERVER-C
object-group service CLIENT-SERVICES
service-objecticmp echo
service-objecttcp destination eq ftp
service-objecttcp destination eq www
service-objectudp destination eqdomain
ciscoasa#
ciscoasa# show run access-list
access-list INSIDE-ACL extended permit object-group CLIENT-SERVICES object-group INTERNAL object-group EXTERNAL-SERVERS
ciscoasa#
ciscoasa# show access-list
access-list cached ACL log flows: total 0, denied 0 (deny-flow-max 4096)
alert-interval 300
access-list INSIDE-ACL; 24 elements; name hash: 0x4b2b493b
access-list INSIDE-ACL line 1 extended permit object-group CLIENT-SERVICES object-group INTERNAL object-group EXTERNAL-SERVERS 0x3c82b1d6
access-list INSIDE-ACL line 1 extended permit icmp 10.3.0.0 255.255.255.0 host 172.16.1.2 echo (hitcnt=0) 0xa64ba2fc
access-list INSIDE-ACL line 1 extended permit icmp 10.3.0.0 255.255.255.0 host 172.16.3.4 echo (hitcnt=0) 0x3cfa64ef
access-list INSIDE-ACL line 1 extended permit icmp 10.3.0.0 255.255.255.0 host 172.16.5.6 echo (hitcnt=0) 0xc5bda599
access-list INSIDE-ACL line 1 extended permit icmp host 10.1.1.2 host 172.16.1.2 echo (hitcnt=0) 0xe0cb1c42
access-list INSIDE-ACL line 1 extended permit icmp host 10.1.1.2 host 172.16.3.4 echo (hitcnt=0) 0x7a9a7e95
access-list INSIDE-ACL line 1 extended permit icmp host 10.1.1.2 host 172.16.5.6 echo (hitcnt=0) 0x625ddc45
access-list INSIDE-ACL line 1 extended permit tcp 10.3.0.0 255.255.255.0 host 172.16.1.2 eq ftp (hitcnt=0) 0x825f4688
access-list INSIDE-ACL line 1 extended permit tcp 10.3.0.0 255.255.255.0 host 172.16.3.4 eq ftp (hitcnt=0) 0xe60dc66d
access-list INSIDE-ACL line 1 extended permit tcp 10.3.0.0 255.255.255.0 host 172.16.5.6 eq ftp (hitcnt=0) 0xf206fa2b
access-list INSIDE-ACL line 1 extended permit tcp host 10.1.1.2 host 172.16.1.2 eq ftp (hitcnt=0) 0xd2619215
access-list INSIDE-ACL line 1 extended permit tcp host 10.1.1.2 host 172.16.3.4 eq ftp (hitcnt=0) 0xbe035dd7
access-list INSIDE-ACL line 1 extended permit tcp host 10.1.1.2 host 172.16.5.6 eq ftp (hitcnt=0) 0x9765b56a
access-list INSIDE-ACL line 1 extended permit tcp 10.3.0.0 255.255.255.0 host 172.16.1.2 eq www (hitcnt=0) 0x66519ccd
access-list INSIDE-ACL line 1 extended permit tcp 10.3.0.0 255.255.255.0 host 172.16.3.4 eq www (hitcnt=0) 0xab7a7aa5
access-list INSIDE-ACL line 1 extended permit tcp 10.3.0.0 255.255.255.0 host 172.16.5.6 eq www (hitcnt=0) 0x45dfac83
access-list INSIDE-ACL line 1 extended permit tcp host 10.1.1.2 host 172.16.1.2 eq www (hitcnt=0) 0x76b5bcfb
access-list INSIDE-ACL line 1 extended permit tcp host 10.1.1.2 host 172.16.3.4 eq www (hitcnt=0) 0xa9d3cba7
access-list INSIDE-ACL line 1 extended permit tcp host 10.1.1.2 host 172.16.5.6 eq www (hitcnt=0) 0xf246dd28
access-list INSIDE-ACL line 1 extended permit udp 10.3.0.0 255.255.255.0 host 172.16.1.2 eq domain (hitcnt=0) 0x97263557
access-list INSIDE-ACL line 1 extended permit udp 10.3.0.0 255.255.255.0 host 172.16.3.4 eq domain (hitcnt=0) 0x17e22a7b
access-list INSIDE-ACL line 1 extended permit udp 10.3.0.0 255.255.255.0 host 172.16.5.6 eq domain (hitcnt=0) 0xdd781f05
access-list INSIDE-ACL line 1 extended permit udp host 10.1.1.2 host 172.16.1.2 eq domain (hitcnt=0) 0x8f7f997c
access-list INSIDE-ACL line 1 extended permit udp host 10.1.1.2 host 172.16.3.4 eq domain (hitcnt=0) 0xd49d3212
access-list INSIDE-ACL line 1 extended permit udp host 10.1.1.2 host 172.16.5.6 eq domain (hitcnt=0) 0xc734f373
ciscoasa#
ciscoasa# show run access-group
access-group INSIDE-ACL in interface inside
ciscoasa#
