UPDATE: In October 2020, the Cisco Product Security Incident Response Team (PSIRT) received reports of attempted exploitation of one of the vulnerabilities described in this support article in the wild, CVE-2020-3118.
Cisco recommends that customers upgrade to a fixed Cisco IOS XR Software release to remediate this vulnerability.
The external report can be found here: https://media.defense.gov/2020/Oct/20/2002519884/-1/-1/0/CSA_CHINESE_EXPLOIT_VULNERABILITIES_UOO179811.PDF
On February 5, 2020, the Cisco Product Security Incident Response Team (PSIRT) disclosed multiple vulnerabilities in the Cisco Discovery Protocol implementation of several Cisco products, along with software fix information and mitigations where available. These vulnerabilities were found by Armis Security and were referred to them as "CDPwn". Cisco is committed to transparency. More than twenty years ago, we launched the Cisco PSIRT, with the goal of communicating clearly about security vulnerabilities so we can work closely with our customers and partners to help mitigate any impact. We maintain a very open relationship with the security research community, like the team at Armis, and view this collaboration as vital to helping protect our customers’ networks.
Cisco has released software updates that address all of these vulnerabilities. The following table provides a summary list of these vulnerabilities:
Cisco Discovery Protocol Details and Vulnerability Access Vector
The Cisco Discovery Protocol is a Layer 2 protocol that runs on Cisco devices and enables networking applications to learn about directly connected devices nearby. This protocol facilitates the management of Cisco devices by discovering these devices, determining how they are configured, and allowing systems using different network-layer protocols to learn about each other.
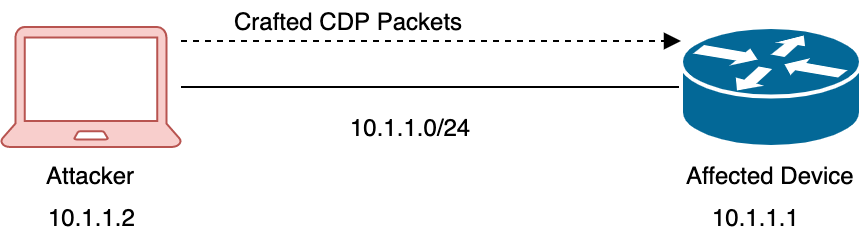
A few facts about these vulnerabilities are as follows:
- An attacker must be in the same broadcast domain or subnet as the affected device (“Layer-2” adjacent) in order to exploit the vulnerabilities, as shown in the diagram below. These vulnerabilities cannot be exploited from the Internet or from a different broadcast domain/subnet.
- Devices running Cisco IOS and Cisco IOS-XE Software are not affected by any of these vulnerabilities.
- Cisco ASA, Cisco Firepower 1000 Series, and Cisco Firepower 2100 Series are not affected by any of these vulnerabilities.
- Cisco FXOS Software, Cisco IP Camera Firmware, Cisco IP Phone Firmware, Cisco IOS-XR Software, Cisco NX-OS Software, and Cisco UCS Fabric Interconnects are affected by one or more of these vulnerabilities.
- Cisco Discovery Protocol is disabled by default in Cisco IOS XR Software.
- Cisco Discovery Protocol is enabled by default in Cisco FXOS Software, Cisco IP Camera Firmware, Cisco IP Phone Firmware, Cisco NX-OS Software and on Cisco UCS Fabric Interconnect. In Cisco FXOS Software releases 2.1 and later this vulnerability is exploitable only via the management (mgmt0) port. In these releases Cisco Discovery Protocol is never actually enabled on front-panel ports, even if it is configured. Csco Discovery Protocol can be enabled on front-panel ports in Cisco FXOS Software versions earlier than 2.1 only.
-
Cisco Discovery Protocol cannot be disabled completely on Cisco UCS Fabric Interconnects.
Cisco Discovery Protocol can be disabled on server ports and appliance ports on Cisco UCS Fabric Interconnects, but it cannot be disabled on Ethernet uplink ports, Ethernet port channel members, FCoE uplink ports or management ports.
- A well-known security best practice is to disable Cisco Discovery Protocol on all interfaces that are connected to untrusted networks. (A list of security best practices by operating system can be found on Network Infrastructure Device Hardening, Forensics, and Integrity Assurance Procedures) Each security advisory provides detailed information on how to determine if Cisco Discovery Protocol is enabled in your device and how to disable it. For those products that must run CDP for certain functionality, customers are encouraged to follow best practices on network segmentation to avoid untrusted devices from sending CDP packets or ultimately upgrade those devices with the available software fixes.
The following table summarizes the commands to disable Cisco Discovery Protocol in Cisco FXOS, Cisco IOS-XR, Cisco NX-OS, and Cisco UCS Fabric Interconnect:
|
Device Operating System
|
Disabling Cisco Discovery Protocol on an Interface
|
Disabling Cisco Discovery Protocol Globally
|
|
Cisco NX-OS
|
Use the no cdp enable command in interface configuration mode.
|
Use the no cdp enable command in global configuration mode.
|
|
Cisco FXOS
|
Use the disable cdp command in every nw-ctrl-policy that is applied to an interface.
|
Not applicable
|
|
Cisco IOS-XR
|
Use the no cdp command in interface configuration mode.
Cisco Discovery Protocol is disabled by default in Cisco IOS-XR devices.
|
Use the no cdp command in global configuration mode.
Cisco Discovery Protocol is disabled by default in Cisco IOS-XR devices.
|
|
Cisco IP Camera Firmware
|
Disabling Cisco Discovery Protocol may impact device functionality. Customers are encouraged to follow best practices on network segmentation to avoid untrusted devices from sending CDP packets or ultimately upgrade those devices with the available software fixes. Please see the security advisory for details on fixed software availability. (CVE-2020-3110)
|
|
Cisco IP Phone Firmware
|
Disabling Cisco Discovery Protocol may impact device functionality. Customers are encouraged to follow best practices on network segmentation to avoid untrusted devices from sending CDP packets or ultimately upgrade those devices with the available software fixes. Please see the security advisory for details on fixed software availability. (CVE-2020-3111)
|
|
Cisco UCS Fabric Interconnect
|
Use the disable cdp command in every nw-ctrl-policy that is applied to an interface.
|
Not applicable
|
Cisco has released software updates that address all of these vulnerabilities and each security advisory provides detailed information about how to obtain fixed software.
