The "cloud” and virtualization are driving the way data centers are being architected. Everyone knows that server virtualization is the key for consolidation, power savings and cost reduction. However, what about isolation, monitoring, and policy enforcement? How can these be done efficiently? In the past, firewalls, intrusion prevention systems (IPS), and other policy enforcement mechanisms in the network have acted as the first line of defense against security threats on the network. Is it the same for virtualized environments? Probably? Probably not…
As you know, virtualized environments are very dynamic in nature. There are frequent additions, deletions, and changes across virtual machines (VMs) and tenants. In the past, each physical server was connected to an access port on a switch. Subsequently, all traffic between servers or to the corporate network traveled through a physical access switch and firewalls, IPS devices, load balancers, etc. However, traffic flows within virtualized environments sometimes do not even touch physical devices. For example, traffic between the following VMs do not even leave the physical hardware.
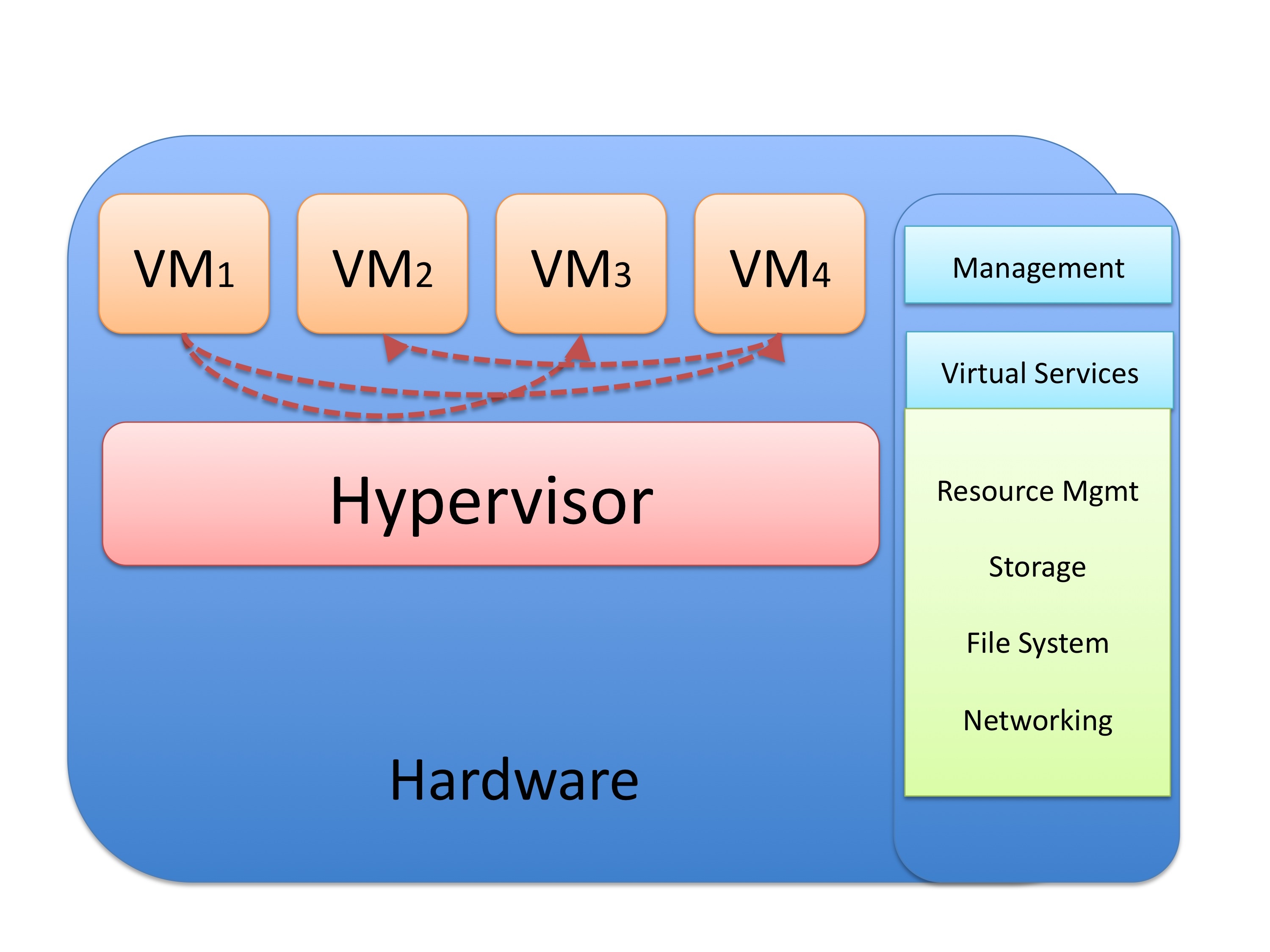
So how do we provide segmentation, policy enforcement and other security services? Cisco has introduced the Cisco Virtual Security Gateway (VSG) for the Cisco Nexus 1000V Series. It is a virtual firewall that allows you to enforce policy and segmentation virtual and cloud environments. The Cisco VSG operates in conjunction with the Cisco Nexus 1000V (and vPath) in order to support a dynamic VM environment. All security profiles are associated to a Cisco Nexus 1000V port profile. These are authored on the Cisco Nexus 1000V Virtual Supervisor Module and published to the VMWare Virtual Center. A tenant is created with the Cisco VSG and on the Cisco Virtual Network Management Center (VNMC). All associated security profiles are configured to include trust zone definitions and access control rules. When a new VM is instantiated, you assign the respective port profile to the virtual Ethernet port of the VM.
When a vMotion events occurs, VMs move across physical servers. The Cisco Nexus 1000V ensures that port profile policies and associated security profiles follow the VMs. Security enforcement and monitoring remain transparent to vMotion events. The Cisco VSG operates with the Cisco Nexus 1000V distributed virtual switch in the VMWare vSphere hypervisor. The Cisco VSG leverages the virtual network service data path (vPath) that is embedded in the Cisco Nexus 1000V Virtual Ethernet module (VEM). vPath steers traffic, whether external-to-VM or VM-to-VM, to the Cisco VSG of a tenant. A split-processing model is applied where initial packet processing occurs in the Cisco VSG for policy evaluation and enforcement. After the policy decision is made, the Cisco VSG off-loads policy enforcement of remaining packets to vPath.
Well, you can learn more of this at http://cisco.com/go/vsg
What happens to the firewall and security administrators? They have to collaborate more than ever with the switch and the server administrators. In small-to-medium organizations this may be the same team. However, in large enterprises these are often separate teams; and sometimes, their rational will be a LOT different. Collaboration between security, switching and server teams is crucial! Specially, since they are always forced to maintain administrative separation and reduce errors via a consistent and repeatable deployment model. How can we achieve that with this complex environment and across different mentalities?
*Coordination and correlation for programmatic provisioning and management of security policies is not an easy task unless you use strong APIs and (again) complete collaboration within teams. The good news is that provides several visual and programmatic controls /APIs to manage security policies. However, is this sufficient? This is where processes, metrics, and technology need to meet. You can have the most sophisticated security device/software and if you do not have the appropriate processes in place you will fail. Let's take a look at a few metrics that can help you evaluate if you have the correct processes in place for both, the physical and virtualized world within your infrastructure.
How long *does it take for you to positively identify that a virtual "device" is compromised in comparison to how long does it take when a physical device is compromised? Have you ever made that comparison?
What is the frequency of audits conducted against your "virtual infrastructure"? How can you maintain visibility into network operations? You must adjust your processes and procedures and audit the virtualized environment the same way you do for your physical network. By doing these audits/checks you will *reveal important errors or omissions *in the virtualized environment that probably are not present in the legacy physical world. What is the the average (mean) time elapsing between audits of the firewall systems and rules (for both virtual and physical firewalls)?
Additionally, what is the *percent of the virtualized network that is documented and understood *by the security team? The lack of virtual topologies will contribute to delays in the incident response process, if/when your virtual network is compromised.
May I challenge you a little further? Measure* how long does it take for you to detect an event *occurring on the physical network vs. in the virtualized environment. I am assuming that you already have complete visibility of both, physical and virtual devices. How long does it take for you to obtain and correlate alerts that originate from software, hardware, or human observation?
You may think that this does not have anything to do about security, but it does. *What is the number or ratio of physical and virtual devices that do not confirm to a standard build template? *Go ahead and compare both of them. You should have standard build templates for all physical and virtual assets with all the respective security considerations.
Please share what are some other processes or metrics that security administrators should pay attention in this "somewhat-new virtualized world".
