- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- IP Phone SSL VPN to ASA using AnyConnect
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
05-05-2010 08:06 AM - edited 08-28-2017 10:14 PM
- Purpose
- Functional Overview
- CUCM Places ASA Certificate Hash and VPN URL in Phone Config
- Phone Connects to ASA
- Software Versions
- Phone Models
- CUCM Configuration
- Phone Configuration
- ASA Configuration
- Additional Requirements:
- Troubleshooting Steps
- Common Issues
Purpose
Starting in CUCM 8.0.1 and IP Phone Firmware 9.X, IP Phones are now able to directly connect to an ASA using the AnyConnect VPN. This document will help address some common issues encountered during intial configuration. This guide will act as a supplement to the Official IP Phone VPN Documentation.
Functional Overview
Before we get into versions and model numbers let's look at how the feature works.
CUCM Places ASA Certificate Hash and VPN URL in Phone Config
Before the phone is ready for VPN, it must first be provisioned using the internal network. This requires direct access to the CUCM TFTP server.
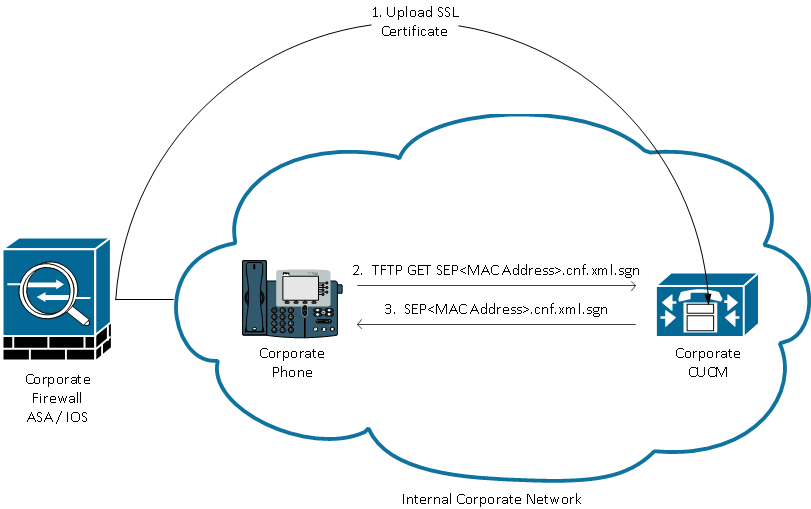
The first step after the ASA is fully configured is to take the ASA HTTPS Certificate and upload it to the CUCM server. This allows the CUCM server to build an IP phone config file that tells the phone how to get to the ASA. The CUCM requires some additional configuration to associate the uploaded certificate with a VPN Profile that can be assigned to the phone.
Here is an example of the IP Phone VPN section of a phone's config file after performing the required configuration:
jasburns@jasburns-gentoo /home/jasburns $ tftp 14.48.44.80 tftp> get SEP0011215A1AE3.cnf.xml.sgn Received XXXX bytes in 0.0 seconds jasburns@jasburns-gentoo /home/jasburns $ cat SEP0011215A1AE3.cnf.xml.sgn .......... <vpnGroup> [Some Lines Omitted] <addresses> <url1>https://X.X.X.X/PhoneVPN</url1>
</addresses>
<credentials>
<hashAlg>0</hashAlg>
<certHash1>1eD9l3VEI9DGWQGKlNBGE1bRhUg=</certHash1>
</credentials>
</vpnGroup>
Note that the URL is printed exactly as entered on the VPN Gateway Configuration page in CUCM. Make sure the IP Phone can resolve this address.
Even more interesting is the Cert Hash. The IP phone configuration does not contain the entire certificate, merely a SHA1 Base64 encoded hash of the certificate.
You can compare the certificate hash in the IP phone configuration file to the cert hash of the actual file on the ASA or CUCM if you copy it to a computer running OpenSSL (either Windows, Linux, or Mac)
$ cat r2800.cisco.com.pem
-----BEGIN CERTIFICATE-----
<Base64 value of the cert omitted>
-----END CERTIFICATE-----
openssl x509 -in r2800.cisco.com.pem -noout -fingerprint
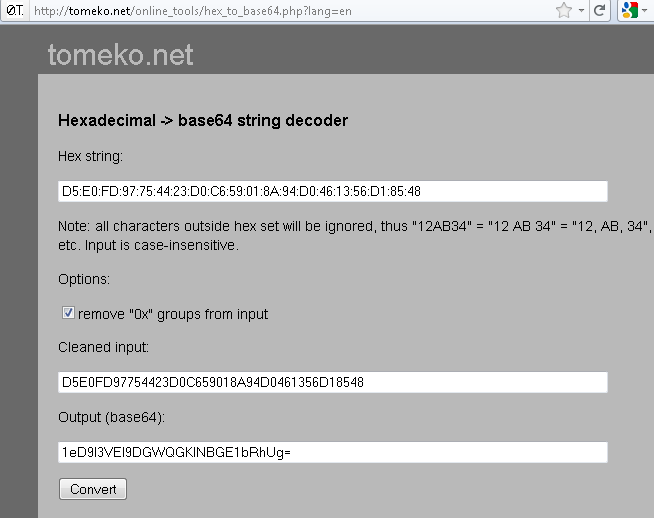
SHA1 Fingerprint=D5:E0:FD:97:75:44:23:D0:C6:59:01:8A:94:D0:46:13:56:D1:85:48
This is the SHA1 Fingerprint in Hexadecimal form. In the configuration file this value is instead printed as the Base64 value. I used the following website to convert from Hex to Base64:
http://tomeko.net/online_tools/hex_to_base64.php
This method can be used to verify the certificate loaded onto and presented by the ASA matches the certificate hash loaded into the phone.
Phone Downloads Configuration
This part is extremely important. The phone must download the configuration (including the certificate hash in Base64) while it is inside the network and has direct access to the CUCM TFTP server.
The phone has to be provisioned inside the network before it can be moved outside the network and use the VPN feature.
Phone Connects to ASA
After internal provisioning has been completed, the phone can be moved to the external network for VPN access. Here the Corporate Phone has been moved to a Home location.
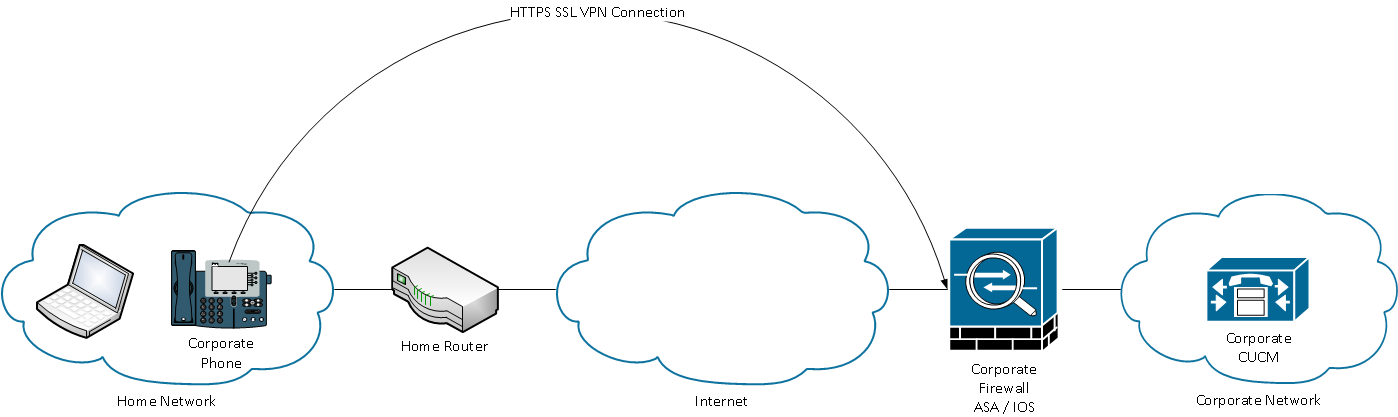
Depending on the phone's configuration it will either automatically attempt to connect to the VPN gateway, or will connect once manually initiated. If auto network detect is enabled, the phone will try to ping the TFTP server. If there is no response to this ping request the phone will automatically bring up the VPN process on the phone.
The phone connects on TCP port 443 over HTTPS to the ASA. The ASA responds back with the configured certificate, hopefully the same certificate uploaded to CUCM. In additional TCP 443 (Transport Layer Security, or TLS), the phone will also connect on UDP 443 for DTLS (Datagram Transport Layer Security).
Phone Verifies Presented Certificate
The phone console logs show us the hash of the certificate that the ASA presents in Hex form:
3943: INF 18:10:22.354209 VPNC: vpnc_save_to_file: wrote: </tmp/leaf.crt>, 479 bytes
3944: NOT 18:10:22.355351 VPNC: cert_vfy_cb: peer cert saved: /tmp/leaf.crt
3945: NOT 18:10:22.361892 SECD: Leaf cert hash = D5E0FD97754423D0C659018A94D0461356D18548
3946: NOT 18:10:22.362574 SECD: Hash was found in the trust list
3947: NOT 18:10:22.400294 VPNC: VPN cert chain trusted
These messages show us that the phone was able to validate the certificate that the ASA presented. The cert presented matched the hash in the configuration file.
At this point the phone will establish an SSL session with the ASA and continue setting up the VPN tunnel.
All communication will now flow between the phone and the ASA in an encrypted tunnel. Once the traffic reaches the ASA it will be decrypted and forwarded along to any location in the network that the phone would like to connect to.
The beauty of this solution is that the phone obtains an address on the Internal network that is typically not filtered. The phone can connect using SCCP, SIP, HTTP, HTTPS to any server inside the Corporate Network. This allows advanced phone services and features to function that might not work through ASA Phone Proxy.
Software Versions
CUCM >= 8.0.1.100000-4
IP Phone >= 9.0(2)SR1S - SCCP
ASA >= 8.0.4
Anyconnect VPN Pkg >= 2.4.1012
Note: A "Premium" license and an "AnyConnect for Cisco VPN Phone" license is required. The part number for the "AnyConnect for Cisco VPN Phone" is L-ASA-AC-PH-55XX= where XX = 05,10,20,40,50,80.
Phone Models
7942 / 7962 / 7945 / 7965 / 7975 / 8961 / 9951 / 9971. For a complete list of supported phones in your CUCM version go to:
https://<CUCM Server IP Address>:8443/cucreports/systemReports.do
Unified CM Phone Feature List
Generate a new report
Feature: Virtual Private Network
http://www.cisco.com/en/US/docs/voice_ip_comm/cucm/security/8_5_1/secugd/secuvpn.html
CUCM Configuration
The following document provides a complete set of configuration tasks required to configure CUCM for this feature:
http://www.cisco.com/en/US/docs/voice_ip_comm/cucm/security/8_5_1/secugd/secuvpn.html
Note: Please make sure the URL for the VPN Gateway contains the full and correct address to reach the IP Phone VPN tunnel-group on the ASA.
Phone Configuration
- Use a supported phone model per the CUCM Supported Models / Features report.
- Register the phone to the CUCM server on the Internal network
- Configure the IP phone with a TFTP server manually.
- Move the phone to the external network.
ASA Configuration
Configure Anyconnect VPN access on ASA to provide network access.
See http://www.cisco.com/en/US/products/ps6120/products_configuration_example09186a00808efbd2.shtml for example configuration.
The lateset CUCM Security Guide also provides sample ASA configuration.
Additional Requirements:
- The ASA must have the AnyConnect for Cisco VPN Phone Licensed feature enabled. Licensing info can be found using show version command.
- Group-policy must not be configured with split tunnel or split exclude. Only tunnel all is the supported tunneling policy
- The tunnel-group used can not be the DefaultWEBVPNGroup. Create another tunnel-group and use "group-url https://x.x.x.x/phonevpn enable to map to the correct tunnel-group.
- DTLS must be enabled and negotiated for operation. This requires both tcp/443 and udp/443 to be open and allowed on all devices between the ASA and the phone.
Troubleshooting Steps
- Plug the phone into the internal network. This will test whether the phone's configuration works prior to adding VPN.
- Connect with AnyConnect on a PC from the outside to the ASA. This will confirm that the ASA is configured correctly for Anyconnect
- From the connected PC try to ping the TFTP server and CUCM server. This will test basic ip connectivity to the two servers.
- From the PC try to download the TFTP config file for the phone in question "tftp -i <TFTP Server> GET SEP<Mac Address>.cnf.xml" This will test that the tftp service is reachable and serving files.
- From the PC try to telnet to TCP Port 2000 on the CUCM server "telnet <CUCM IP> 2000". This should immediately come back with a new line and a blank cursor. This will test connectivity to the CUCM SCCP port, for SIP registrations use port 5060 instead.
Common Issues
- One-way or no voice. The phone registers and makes calls but no audio is heard. Confirm routing between the two phone/rtp stream endpoints.
- Auto Network Detect does not reliably work in IP Phone Firmware 9.0(2), but does work as expected in 9.2(1).
- Auto Network Detect allows the phone to detect whether it is inside or outside the network. If outside it will bring up the VPN, if inside, it will connect directly.
- The phone uses a series of pings to the TFTP server to determine whether it is outside the network. If pings to the TFTP server fail, the VPN GUI will be brought up on the phone and the phone will attempt to access the VPN URL.
- Username and Password authentication from the phone does NOT support the SPACE character in either the username or the password.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Error "'webvpn=' not found in cookie" successfully solved with TAC. group-url in tunnel-group
webvpn-attributes must match the URL configured for phone SSL access in CUCM vpn gateway configuration.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Question,
I have the SSL VPN phone working with a 9971 model, but when I make changes to phone (extension) the phone then loses connection and doesn't re-register. I can still connect with the SSL VPN on the 9971 it just doesn't register after changing the phone extension.
Do I need to bring the remote phones back to office for any configuration change?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
When you make a change to the phone's configuration (even things like an upgrade) this should work over the VPN tunnel.
It sounds like you're having some other problem, either with the TFTP / HTTP download of the phone's configuration file (UDP 69 or TCP 6970 to TFTP Server), or with the TVS authentication of the downloaded configuration (TCP 2445 to CUCM Server).
I'd take a look at the phone's web page for "Debug Display", "Status Messages", and "Console Logs". The phone may tell you what it's having a problem performing.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks Jason.
I did get it to finally take the change, I blanked out the alternarte TFTP setting then added it back and it asked me to erase the CTL file which I did then a few minutes later it sorted itself out and had the changed configuration. I will check into the items you mentioned.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
So, is there any known workaround to configure remote users' phones WITHOUT bringing them inside the network. For multinationals, this could prove to be a HUGE headache.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Sam,
If you can get a copy of the new phone config file and put it on a tftp that is accessible via the internet, then you can just point the phone to the tftp server (alternate tftp server option). It will go and grab the new config file.
-Jay
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
this sounds great (Thank you Jay) but it sounds easy... too easy. Is there a procedure we need to follow that is documented we can follow?
(Pardon my lack of specific technical knowledge, I'm in management)
-Sam
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Sam,
I don't believe there is a doc. In essence you install tftp service (google for tftpd32) on a computer the phone can access (whether it be a laptop in the same subnet or on a public facing server) then go into the options on the phone and re-configure the tftp server to be the computer you just setup.
-Jay
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I have completely configured the ASA and CUCM 8. The phone now is connecting to the call manager but I have the issue that the the voice does not appear to be able to send to another side. I can hear the voice from another side. I have a look on your recommendation. However, I don't know where to have a look in details on
"
- One-way or no voice. The phone registers and makes calls but no audio is heard. Confirm routing between the two phone/rtp stream endpoints."
Please help.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello,
VoIP works by sending UDP/RTP traffic between the two end devices. The traffic flow *should* be symmetric but because UDP is used it doesn't necessarily mean it will. As a result it is possible that packets from X can be delivered to Y, but not vice-versa. In this case the voice of person at phone X will be heard by the person at phone Y, but not the other way around.
So it means check the network path between the phones to ensure packets are routed and not filtered (ACLs, etc).
Hope that helps.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks, I got it work by using route tunneled.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello,
I have got a question about the licensing, is the Cisco SSL Premium license (l-asa-ssl-XX=) mandatory or should the Phone VPN also work when you have the AnyConnect VPN Phone License and the two AnyConnect Premium Peers that come with the security plus license ?
Because we would like to use that for testing and later upgrade with a SSL Premium license.
Best regards,
Thomas
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thomas,
The feature requires you to use the "premium license" along with the "VPN phone license". With the box you get 2 Premium license included for exactly what you are trying to do "test out features". As long as you don't have the Essentials license installed and "essentials" configured under webvpn then you should be good to go.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thank you for the document - I've been able to successfully configure and use a 7942G (firmware 9.2.3), connecting to an ASA5520 and registering with CUCM 8.5
However - before I deploy these to end-users, I'd like to know if anyone has seen (and solved) these issues:
1) When plugging the phone into a non-corporate network ( end-user home network or other network with DHCP ), if the DHCP server is sending option 150 ( or option 66 ), the phone tries this TFTP server repeatedly. The TFTP server will respond to ping properly, so the "auto network detection" feature doesn't bring up the VPN client -- even though this TFTP server is not the "correct" server from the standpoint of our configuration. The phone just keeps trying to register over and again, but we realize it will never register with this "foreign" TFTP server.
2) VPN persistence: How can we get the phone to automatically reconnect VPN when/if it drops? We are purposefully testing a failure on VPN ( by using ASDM to logout the phone session ), to see how the phone handles this situation. So far, the phone drops back into "registering" but the only way to re-establish VPN ( that we've seen ) is to *disable* then *enable* VPN on the security settings of the phone. Is there any way for this to automatically reconnect? ( We have enabled "save username/password" for VPN )
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello,
As far as TFTP is concerned, it's indicated in Phone Configuration , 3. "Configure the IP phone with a TFTP server manually."
Do I need to setup a fake TFTP ip address in order to launch the VPN process ?
Or the real CUCM TFTP ip address that I have internally in my network ?
Or an external existing TFTP ?
Also, is it recommended to setup one internal and one external TFTP ip address in the 2 fields of Alternate TFTP ?
JC,
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: