- Cisco Community
- Technology and Support
- Networking
- Switching
- Re: A problem with port security
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
A problem with port security
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-09-2019 05:31 AM - edited 07-09-2019 05:45 AM
Hi everyone,
I'm kinda new to r&s and just started learning through cbt nuggets and got to port security and I have a question:
I made with Packet Tracer a model of normalSwitch-normalPC and "evil" switch-"evil" PC, as the name suggests- it is evil.
so i configured the normal switch's port security with max:1 ,MAC sticky , violation: shutdown so no one else should connect through that port and when I disconnected the normal PC and replaced it with evilSwitch it worked as expected.
BUT when i change violation to restrict the colors between the normal switch and "evil" switch are turning green (!) and no warning is on my console.
Isn't the sticky MAC should disable the evil switch from connecting ? And why there is no warning on the screen ?
Thanks, Eli !
- Labels:
-
Catalyst 2000
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-09-2019 05:44 AM
I dont use PT but it could just be an emulator issue that its not dropping the packets , regarding screen output if your over vty port you need terminal monitor configured , if over console logging console should be enabled to be able to see the issues as they occur or alerts
is the security violation even incrementing when you check the PS status for that port when the bad PC is connected ?
show port-security interface | i Viol
switchport port-security violation
To set the action to be taken when a security violation is detected, use the switchport port-security violation command. To revert to the default settings, use the no form of this command.
switchport port-security violation { protect | restrict | shutdown }
no switchport port-security violation { protect | restrict | shutdown }
Syntax Description
protect
Drops all the packets from the insecure hosts at the port-security process level but does not increment the security-violation count.
restrict
Drops all the packets from the insecure hosts at the port-security process level and increments the security-violation count.
shutdown
Shuts down the port if there is a security violation.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-09-2019 05:52 AM - edited 07-09-2019 05:55 AM
Thanks for the comment,
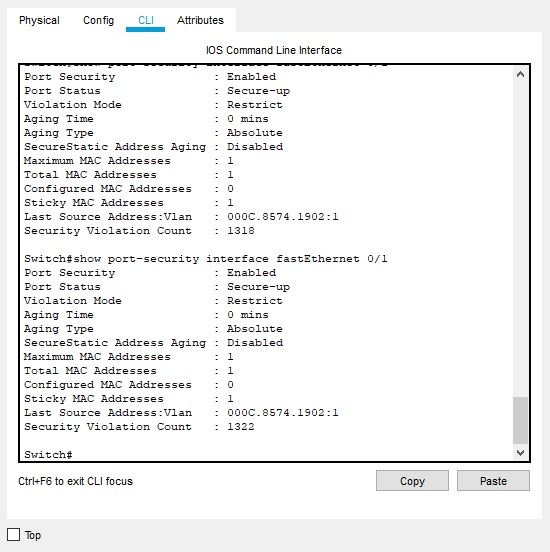
The security violation count jumped to astronomous amounts- 700~ ! and later on even to 1000~...
(checked by "show port-security interface fa 0/1")
By your explanation it seems i've done everything right...
Edit: Added a screenshot
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-09-2019 06:11 AM
PT is very good tool to start out with but you should look at IOU and GNS3 too as they run full images and you can run into less emulator issues but what your seeing looks fine
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-09-2019 07:11 AM - edited 07-09-2019 07:24 AM
Appearently there's a bug in pt that doesnt allow me to trace a packet. I'm starting to think I've done everything right.
By the way the counter is incrementing automatically even with no action to trigger it... seems odd...
EDIT: I tried installing gns3 because solving this issue is important to me but this program is REALLY annoying....
Got tons of questions in the installing process and now it wants to connect to a server and fails. this is so fraustrating....
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-09-2019 06:07 AM
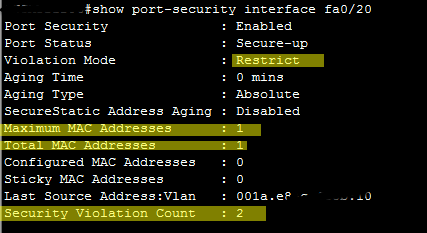
- switchport port-security violation protect -> does not allow only the amount of MAC defined
- switchport port-security violation restrict -> does not allow the violation and generates an alert
- switchport port-security violation shutdown -> puts the interface in shutdown state when the violation happens
The commands below have been run on a Cisco Catalyst 2960 device and help with port-security troubleshooting. I can not be sure if they all work on the packet tracer.

---
Everton
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-09-2019 07:07 AM
I just did the switchport port-security to make sure it's enabled and still everything the same.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-09-2019 06:19 AM
Hello
Did you save the running config after you enabled port sec mac sticky otherwise the dynamically learn mac isn’t saved to the cam table and it will then have to be relearnt so it’s possible why it allowed you to add a different device
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-09-2019 07:06 AM
Actually at first I didn't save the config but now I did and still I am able to replace the PC with the evil-switch with no warning on console or red lights...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-25-2023 12:11 PM
I've had a similar issue, but on my end on PT restrict mode drops packets as desired but does not increment the violation counter at all. I'm still at 0 violation count despite being in restrict mode and sending about 12 different pings from an unauthorized MAC address. Definitely looking into GNS3 now.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide