- Cisco Community
- Technology and Support
- Networking
- Switching
- Re: ACL works only for one rule.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2019 12:20 PM
When I configure one rule it works fine, when I add another rule then both rules doesn't work at all.
Both works perfect when I use them as first rule only.(everything is connected, both servers are configured as web servers.)
First rule:
access-list 102 permit tcp host 192.168.1.1 host 192.168.2.2 eq www
Second rule:
access-list 101 permit icmp host 192.168.2.1 host 192.168.1.2 echo-reply
#access-list 101 permit icmp host 192.168.2.1 host 192.168.1.2 echo
Solved! Go to Solution.
- Labels:
-
Branch Router
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2019 02:23 PM
Hi @GuyIttach133 ,
Try this:
access-list 102 permit tcp host 192.168.1.1 host 192.168.2.2 eq www
access-list 102 deny ip host 192.168.1.1 host 192.168.2.2
access-list 102 permit ip any any
interface g1/1
ip access-group 102 in
access-list 101 permit icmp host 192.168.2.1 host 192.168.1.2 echo-reply
access-list 101 permit icmp host 192.168.2.1 host 192.168.1.2 echo
access-list 101 deny ip host 192.168.2.1 host 192.168.1.2
accessc-list 101 permit ip any any
interface g1/0
ip access-group 101 in
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2019 12:33 PM
You can not apply 2 rules on the interface for same direction.
change like below you should be ok. ( test and advise.
First rule:
access-list 102 permit tcp host 192.168.1.1 host 192.168.2.2 eq www
Second rule:
access-list 102 permit icmp host 192.168.2.1 host 192.168.1.2 echo-reply
#access-list 102 permit icmp host 192.168.2.1 host 192.168.1.2 echo
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2019 01:05 PM
what do I have to do so 192.168.1.1 can only browse in 192.168.2.2 http
and 192.168.2.1 can only do pings to 192.168.1.2?
i did what you've said, then configured both on interface Gig0/0 out and Gig0/1 in
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2019 01:51 PM
Can you post the full configuration and expllain the direction of the interface you like to apply this ACL.
so we can suggest you better
show access-list (post the output also).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-11-2019 10:17 AM
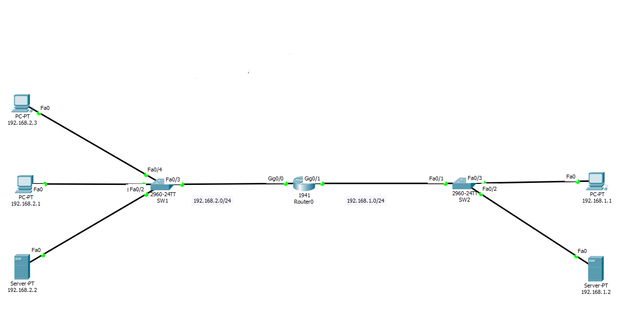
Added the typology.
ACL:
Extended:
1. Permit PC 192.168.1.1 to browse in 192.168.2.2 http and deny pinging him.
2. Permit PC 192.168.2.1 to ping 192.168.1.2 and deny browsing his http.
Standart:
1. Deny for PC 192.168.2.3 to communicate with any PC out of his LAN.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2019 01:01 PM
1 ACL per Interface per Direction per Protocol
see https://learningnetwork.cisco.com/message/706374#706374
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2019 02:23 PM
Hi @GuyIttach133 ,
Try this:
access-list 102 permit tcp host 192.168.1.1 host 192.168.2.2 eq www
access-list 102 deny ip host 192.168.1.1 host 192.168.2.2
access-list 102 permit ip any any
interface g1/1
ip access-group 102 in
access-list 101 permit icmp host 192.168.2.1 host 192.168.1.2 echo-reply
access-list 101 permit icmp host 192.168.2.1 host 192.168.1.2 echo
access-list 101 deny ip host 192.168.2.1 host 192.168.1.2
accessc-list 101 permit ip any any
interface g1/0
ip access-group 101 in
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2019 03:08 PM - edited 08-10-2019 03:08 PM
God bless you man, thanks.
I probably missed the last rules u added.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide