- Cisco Community
- Technology and Support
- Networking
- Switching
- Re: Can vlan # change from device to device?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2021 09:19 AM
On Switch 1 I have 10.0.1.0 in vlan 10 and 10.0.2.0 vlan 11.
Can I, on Switch 2, have a vlan 25 10.0.1.0 and vlan 35 10.0.2.0 and 35 talk to 11 (obviously if connected from both switches via Ethernet) and have the [same] subnets communicate or does (for example) subnet 10.0.2.0 need to be same vlan on every Switch/device it’s connected to to see each other?
Solved! Go to Solution.
- Labels:
-
LAN Switching
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2021 11:31 AM
Hello,
It's getting a little confusing as to what was enabled where and under what VLANs - so pardon me if I only stay at a generic comment level.
Even if you enabled an IP address on your switches in the 10.0.1.0/24 and 10.0.2.0/24 networks, there are requirements to be met:
- The hosts in 10.0.1.0/24 must be configured to use 10.0.1.x as their default gateway (assuming 10.0.1.x is the IP address of one of your switches)
- The hosts in 10.0.2.0/24 must be configured to use 10.0.2.y as their default gateway (assuming 10.0.2.y is the IP address of one of your switches)
- There must be a contiguous VLAN (hence, no VLAN ID mixup) between hosts 10.0.1.0/24 and their default gateway 10.0.1.x
- There must be a contiguous VLAN (hence, no VLAN ID mixup) between hosts 10.0.2.0/24 and their default gateway 10.0.2.y
- The switches owning the IP addresses 10.0.1.x and 10.0.2.y must be Layer 3 switches capable of IP routing
Also, even if all these conditions were met, the 10.0.1.0/24 hosts in VLAN 10 would be unable to talk to 10.0.1.0/24 hosts in VLAN 25. This is because from the IP perspective, they are all in the same IP subnet, meaning they can talk to each other directly, without routing. But since there is a VLAN boundary (VLAN 10 vs. VLAN 25), there is no possibility for the VLAN 10 fraction to talk to the VLAN 25 fraction, even if IP thinks it is possible - because the underlying connectivity does not exist.
As always, please feel welcome to ask further!
Best regards,
Peter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-31-2021 12:01 PM
You are welcome about comments about vlan needed or not. Sometimes we need to be careful about assumptions that we are making - and this was certainly one of those times. Your point was spot on that vlans were not needed and an IP address configured on the switch interface (with no switchport) was sufficient.
I do not think that DHCP would be particularly helpful in what you are planning to do. With DHCP addresses are assigned dynamically and there is some chance that, over time, a device might get a different IP address from what it had before. You need to be clear which devices go to D-Link for Internet and which devices go to ASA for Internet. I believe that manual configuration of devices would be safer than DHCP.
I am not sure what documentation you have been looking at for PBR. Let me give you some explanation and if you need more than what I give I will find some documentation that might be more simple and helpful.
Basically PBR uses a Policy that provides an over ride of normal IP routing logic in the routing table. PBR uses a route map to identify traffic and to specify how to forward that traffic that is different from what is found in the ip routing table. The route map uses an access list to identify the traffic that is to have special forwarding. The route map is assigned to the interface where the traffic enters the switch/router (a very common mistake is to assign the route map to the exit interface, which seems logical since we want to change how the packet gets out of the router).
This is a brief example of what you would need to do:
1) create 2 extended access lists (one will identify traffic going to D-Link and the other will identify traffic going to ASA). In this case the access list will match on source address. For this example I will assume that devices going to D-Link are using IP addresses 192.168.5.1 through 192.168.5.15 and devices going to ASA are using IP addresses 192.168.5.32 through 192.168.5.47. Of course your situation will probably be different.
access-list 101 permit ip 192.168.5.0 0.0.0.15 any
access-list 102 permit ip 192.168.5.32 0.0.0.15 any
2) configure a route map that will identify traffic and will specify how to forward it
ip policy ToInternet permit 10
match ip address 101
set ip next-hop 10.0.2.1
ip policy ToInternet permit 20
match ip address 102
set ip next-hop 192.168.1.1
3) assign the route map to the vlan interface where traffic enters the switch
interface vlan 12
ip policy route-map ToInternet
That should do it. If you want additional documentation let me know.
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2021 09:26 AM
Hi,
if its same network and need to connect between them, most recommended and suitable method is to have same VLAN ID in same switch network.
in advanced setups, you need have NAT capable router/ L3 switch with some advanced configurations to achieve this.
for your requirement, most suitable is to have same VLAN ID between switches for same network.
Good luck
rate this and mark as answer if this solved your concern.
KB
Good luck
KB
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2021 09:36 AM
Hello,
It is technically doable but it's violating the best practices quite badly.
There are higher-end switches that support VLAN mapping on trunks - in other words, they allow you to rewrite incoming and outgoing VLAN tags. This way, on Switch1, you could rewrite the outgoing tag 11 to 35 and vice versa for the incoming traffic. However, this VLAN mapping feature is not universally supported. The target audience for these VLAN tricks are service provider environments (where two networks with different ownerships need to connect together) and data centers (where often, servers run by different teams have to interface with switches run by different teams again, or when two dissimilar data centers need to be connected together).
You could also dedicate a pair of access ports between these two switches for each non-congruent pair of VLANs you want to extend. In other words, you would connect an access port in VLAN 11 on Switch1 to an access port in VLAN 35 on Switch2. You'd do the same trick for VLANs 10 and 25 using another pair of dedicated access ports. Essentially, you would create a native VLAN mismatch on access ports.
Without doing this, frames coming over a trunk from Switch1 to Switch2 tagged with VLAN 10 would be processed strictly in VLAN 10 on Switch2 and no other VLAN. If VLAN 10 does not exist on Switch2, the frames would be blackholed.
IP networking itself is oblivious of VLANs and VLAN numbering. To IP, all that is needed is a contiguous broadcast domain. A broadcast domain is an IP network. If you provide the broadcast domain using the VLAN technology, that's perfect, but the boundary of that IP network is exactly where the boundary of the VLAN is.
I would personally strongly advise against doing these things of having dissimilar VLANs on neighboring switches and doing some cool magic to map them to each other. It can work but it creates an environment that is very cumbersome and difficult to maintain.
Please feel welcome to ask further!
Best regards,
Peter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2021 09:59 AM
This is very helpful and I will look into these options more detailed. I am by default in agreement with vlans staying same across the network as I prefer consistency and order. I had no intent to purposely change the vlan # but was curious to myself if this was why my communication was being blocked. My PC connects to vlan 35 on SG Switch which connects to vlan 11 on Catalyst. Both subnet 10.0.2.0.
When I eliminate the SG and simply use vlan 10,vlan 11 (10.0.1.0 and 10.0.2.0) my subnets can communicate. When I add the SG Switch, and also made 2 new vlans but same subnets, the 10.0.2.0 no longer sees 10.0.1.0. I’m assuming cause I have no “advanced” setting as well as different vlans.
Why I even changed them, no idea. I think I was practicing but this has to be why communication ceases to exist.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2021 10:12 AM - edited 09-25-2021 10:14 AM
Hello @fbeye ,
Oh, definitely, that must be the reason why your two PCs cannot communicate. In fact, that is the whole point of having two distinct VLANs: They each are a standalone and isolated broadcast domain. Traffic in one of them must not leak under any circumstances to the other one. So even if you used the same IP range but one switch used VLAN 10 while the other used VLAN 25, the hosts on those two switches were absolutely expected to be unable to communicate with each other, because on the Layer 2, they were separate by means of different VLANs. IP assumes contiguous Layer 2 connectivity between the hosts in the same IP subnet - it does not provide it or make up for it.
But this is a wonderful exercise to reinforce the understanding of what two different VLANs truly mean - two separate neighborship environments (neighbors in Layer2 sense). I can talk on Layer2 to anyone in my own VLAN, but to no one else in any other VLAN. If I need to talk to someone outside of my VLAN, I need routing, and for that, I need Layer 3 addressing that is unique for my VLAN and the other VLANs, too.
Please feel welcome to ask further!
Best regards,
Peter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2021 10:21 AM
Alright I am keeping up with this. But to add to this, you mention L3 Switching. I want to mention, I did enable vlan 25 IP address of the 10.0.1.0 subnet and a vlan 35 IP address of the 10.0.2.0 subnet…. Even with the L3 vlan interface it’s still a NO GO on talking to the vlan 10 and 11 of the other switch cause as you said, different.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2021 11:31 AM
Hello,
It's getting a little confusing as to what was enabled where and under what VLANs - so pardon me if I only stay at a generic comment level.
Even if you enabled an IP address on your switches in the 10.0.1.0/24 and 10.0.2.0/24 networks, there are requirements to be met:
- The hosts in 10.0.1.0/24 must be configured to use 10.0.1.x as their default gateway (assuming 10.0.1.x is the IP address of one of your switches)
- The hosts in 10.0.2.0/24 must be configured to use 10.0.2.y as their default gateway (assuming 10.0.2.y is the IP address of one of your switches)
- There must be a contiguous VLAN (hence, no VLAN ID mixup) between hosts 10.0.1.0/24 and their default gateway 10.0.1.x
- There must be a contiguous VLAN (hence, no VLAN ID mixup) between hosts 10.0.2.0/24 and their default gateway 10.0.2.y
- The switches owning the IP addresses 10.0.1.x and 10.0.2.y must be Layer 3 switches capable of IP routing
Also, even if all these conditions were met, the 10.0.1.0/24 hosts in VLAN 10 would be unable to talk to 10.0.1.0/24 hosts in VLAN 25. This is because from the IP perspective, they are all in the same IP subnet, meaning they can talk to each other directly, without routing. But since there is a VLAN boundary (VLAN 10 vs. VLAN 25), there is no possibility for the VLAN 10 fraction to talk to the VLAN 25 fraction, even if IP thinks it is possible - because the underlying connectivity does not exist.
As always, please feel welcome to ask further!
Best regards,
Peter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2021 11:43 AM
My explanation was confusing but you responded as I needed. Thank you.
Same but side note. Do either Router, hosting R1 10.0.1.0 or R2 hosting 10.0.2.0 need any static routes or will the Switch, with ip routing enabled as well as having vlan IP’s handle that itself? Also does the Switch need any static routes?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2021 12:06 PM
Hi,
You are welcome! : )
The routers are new elements here you haven't mentioned so far so again, there's too much uncertainty about their config and placement, but let me try again to respond in a way that hopefully hits the nail.
For simplicity purposes, let's assume we don't have those mixed VLANs across two switches, and instead, we have only VLAN 10 for 10.0.1.0/24, and VLAN 20 for 10.0.2.0/24 on both switches.
If at least one of those switches is a multilayer switch, meaning it can do Layer 3 routing, then you would configure interface Vlan10 and interface Vlan20 on that switch like, for example, this:
interface Vlan10 ip address 10.0.1.1 255.255.255.0 ! interface Vlan20 ip address 10.0.2.1 255.255.255.0
Then you would configure all hosts in 10.0.1.0/24 to use 10.0.1.1 as their default gateway, and all hosts in 10.0.2.0/24 to use 10.0.2.1 as their default gateway. And that would be it. No need for static routes and no need for external routes. To the multilayer switch, both 10.0.1.0/24 and 10.0.2.0/24 would be directly connected networks. Any router or a multilayer switch automatically knows about its own directly connected networks and has them placed in its routing table. Therefore, you don't need to configure any extra routes.
If there was a single router doing the routing instead of the switches, the single router would be connected to a trunk port on one of the switches, and would be configured with subinterfaces for both VLANs, for example:
interface GigabitEthernet0/0 no shutdown ! interface GigabitEthernet0/0.10 encapsulation dot1q 10 ip address 10.0.1.1 255.255.255.0 ! interface GigabitEthernet0/0.20 encapsulation dot1q 20 ip address 10.0.2.1 255.255.255.0
Again, the situation would be the same - no need to configure additional static routes because this single router (called router-on-stick) has both IP subnets directly attached, and so it knows about them automatically.
Static routes would be necessary only if there were two routers, one handling VLAN 10, another one handling VLAN 20 (although notice that there is no reason to need 2 routers for that). In this case, with R1 handling VLAN 10 and R2 handling VLAN 20, there would need to be another connection between the two routers which would be an IP network in its own right. It could be another dedicated inter-router VLAN, or a dedicated physical link connecting those two routers together. In that case, you would need to configure static routing there because R1 doesn't know about 10.0.2.0/24 automatically (it's not directly connected to it), and R2 doesn't know about 10.0.1.0/24; you would need to tell both routers how to reach those remote networks.
I hope this clarifies the issue a bit. Keep those questions coming!
Best regards,
Peter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2021 12:15 PM
You are correct once again, the plot thickens. This thread is beginning to mimic another threaded with great, great help from our community which has been left, by me, unresolved and was thinking maybe this approach on a confirmation issue would resolve it. I by no means meant to create this thread in reference to the other with a different facade. I was hoping that maybe the topic was simply my issue. BUT since we are getting more involved I will re-hash.
R1 (Cisco ASA 5508-X)
207.108.x.182 WAN
10.0.1.1 GE 1/3 (10.0.1.0 Subnet)
R2 (D-Link Router behind VPN so no “wan” access)
207.108.x.179 WAN
10.0.2.1 LAN (10.0.2.0 Subnet)
Switch 1 (Catalyst)
Switch 2 (SG350X)
Assuming you know the configurations as such.
the Switch/es are used to connect 2 separate subnets being “hosted” on their own Routers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2021 12:32 PM
My friend,
May I ask you, at this point, to
- Create a simple diagram showing your topology, networks, possibly the VLANs too
- Reiterate the current question or focus so that it is clear what needs to be answered
?
It would help immensely.
Thank you!
Best regards,
Peter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2021 02:56 PM
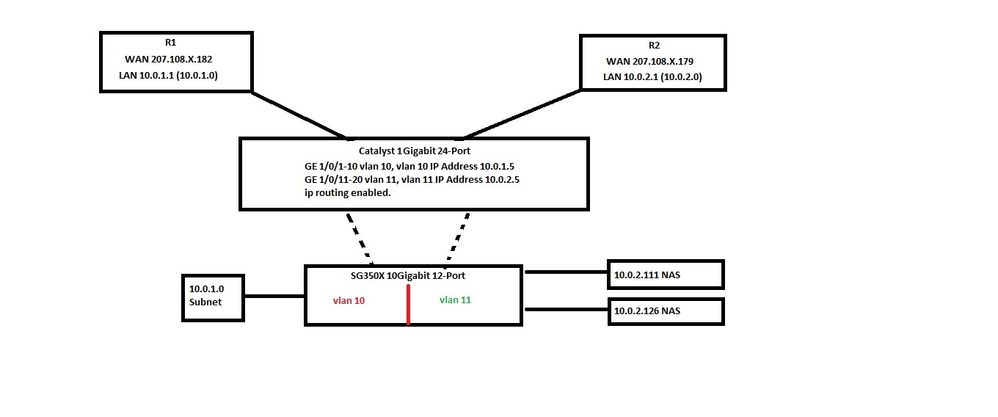
Here is a less specific topology of my network.
The main question to ask here is, should R1 (10.0.1.0 Devices) be able to communicate with R2 (10.0.2.0 Devices) as shown without static Routes as the topology shows, or does it (either switch or either router) need routes to each other? If it does need routes, can you specify which? I.E. The Routers or the Switch? If in theory everything from R1/2 to Catalyst should indeed talk to each other via Catalyst through ip routing and vlan ip addresses then let us continue to to adding the SG350X into the mix. Would this be left in L2 and get it's routing from the Catalyst vlan IP's or would I have to add vlan 10/11 IP addresses onto the SG350X as well with ip routing enabled?
Also, would this require any Static Routes?
My head; PC on 10.0.1.0 will see 10.0.2.0 because Catalyst has ip routing enabled and both subnets have a vlan ip address and not need static routes anywhere.. If this is correct then as I mentioned, does SG350X need a vlan ip as well.
If I am completely wrong here, I hope my description and depiction are accurate enough for the holes to be filled in for me.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-27-2021 07:28 PM
In the picture in above post I would have to assume that No vlan had an interface with an IP address as the SG350X Switch is connected to the Catalyst which already had vlan interface ip addresses and would use that as the Routing? I mean under the impression the SG350 was just L2 ports coming from the Catalyst with the corresponding vlans.
If the SG has no interface ip and vlan 11 talked to vlan 10, and this would get its routing from the Catalyst, how does the routing work? Would the SG know that the vlans can talk through that router? My meaning is, SG is 10gig…. Catalyst is 1gig. Would the data from vlan 10 and 11 just utilize the 10gig SG ports or would it still route back through the 1gig then to the 10gig port?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-28-2021 10:38 AM
Based on the picture it is certainly possible for the SG350X to be configured and operate as a layer 2 only switch. Ports in vlan 10 on SG350X would communicate with vlan 10 on the Catalyst, vlan 11 ports on the SG350X would communicate with vlan 11 on the Catalyst, and with vlan interfaces on the Catalyst for vlans 10 and 11, with appropriate ip addresses on the vlan interfaces, and with ip routing enabled on the Catalyst it could provide inter vlan routing. In this situation vlan 10 and vlan 11 could communicate and no static routes would be needed - as long as you are only considering the 2 vlans. In this scenario it would be logical for devices in each of the subnets to use the vlan interface of the Catalyst as their default gateway.
If you consider access to other networks, especially to the Internet, then a default route would be needed and would probably be done using a static default route. And that brings up a question - which router would the Catalyst use to reach the Internet?
There is also a question of whether you want routing to the Internet to be done on the Catalyst or done on the routers. In the previous discussion you specified that vlan 10 was on R1 and would use that router to reach the Internet and vlan 11 was on R2 and would use that router to reach the Internet. That is possible to achieve if you do these things:
- Internet routing and inter vlan routing on the routers, and only inter vlan routing on the Catalyst.
- Catalyst has ip routing enabled and does local vlan routing but Catalyst does not have a default route.
- Each router has a default route to reach the Internet.
- Each router would communicate to devices in its subnet going through the Catalyst on its vlan
- Each router would communicate with the other subnet by having a static route for the other subnet and with the Catalyst vlan interface as the next hop.
- Devices in both of the vlans would have their default gateway as the router interface address rather than use the Catalyst vlan interface as their default gateway.
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-28-2021 04:22 PM
This is most likely the path I will take as I do require each vlan to have its own Internet access via their Router. It is interesting how I can achieve the same thing but without internet access by not using a Gateway, or by assigning all vlans internet access using a default gateway to whichever Router has Internet. Either way, I will choose this method.
- Internet routing and inter vlan routing on the routers, and only inter vlan routing on the Catalyst.
- Catalyst has ip routing enabled and does local vlan routing but Catalyst does not have a default route.
- Each router has a default route to reach the Internet.
- Each router would communicate to devices in its subnet going through the Catalyst on its vlan
- Each router would communicate with the other subnet by having a static route for the other subnet and with the Catalyst vlan interface as the next hop.
- Devices in both of the vlans would have their default gateway as the router interface address rather than use the Catalyst vlan interface as their default gateway.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide