- Cisco Community
- Technology and Support
- Networking
- Switching
- I cannot see why the ping to
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco 4331 router: port forwarding, outside nat not pinging
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2017 10:46 AM - edited 03-08-2019 10:06 AM
Hi folks,
I've been working on this issue for two days now and I can't solve the issue. I've looked at the following pages: here and here, but I can't seem to get port forwarding working.
My issue resembles the one in the following diagram (from the links above):
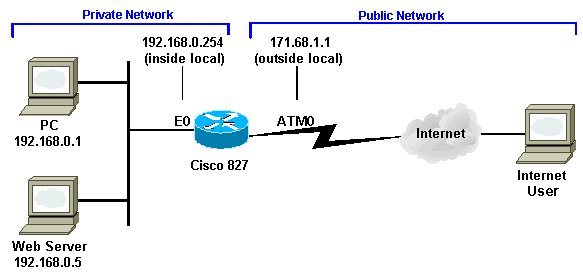
Users in the public network are to hit the outside interface (which in my case is GigabitEthernet0/0/0) on port 9777 and are suppose to get forwarded into the private network (GigabitEthernet0/0/1) on the ssh port.
My config is as follows (sanitized for security)
------------------
interface GigabitEthernet0/0/0
description link to ISP
ip address xxx.xxx.xxx.11 255.255.255.0
ip nat outside
ip access-group 120 in
negotiation auto
ip virtual-reassembly
!
interface GigabitEthernet0/0/1
description inside network
ip address yyy.yyy.yyy.5 255.255.255.128
ip nat inside
negotiation auto
ip virtual-reassembly
!
interface GigabitEthernet0/0/2
no ip address
shutdown
negotiation auto
!
interface GigabitEthernet0
vrf forwarding Mgmt-intf
ip address xxx.xxx.xxx.10 255.255.255.0
negotiation auto
!
ip default-gateway xxx.xxx.xxx.1
ip nat inside source list 107 interface GigabitEthernet0/0/0 overload
ip nat inside source static tcp yyy.yyy.yyy.30 22 xxx.xxx.xxx.11 9777 extendable
ip forward-protocol nd
no ip http server
no ip http secure-server
ip route 0.0.0.0 0.0.0.0 xxx.xxx.xxx.1
ip route vrf Mgmt-intf 0.0.0.0 0.0.0.0 xxx.xxx.xxx.1
ip ssh time-out 99
!
!
logging trap debugging
logging facility local6
access-list 107 permit ip xxx.0.0.0 0.255.255.255 any
access-list 107 deny ip any any log
access-list 120 permit gre host xxx.xxx.xxx.11 any
access-list 120 permit ip xxx.0.0.0 0.255.255.255 any
access-list 120 permit ip any xxx.0.0.0 0.255.255.255
access-list 120 permit gre any any
access-list 120 permit udp any any eq ntp
access-list 120 deny ip any any log
!
!
!
....
end
-------------------------------
What I'm finding is that when ever I put "ip nat outside" on GigabitEthernet0/0/0, the outside interfaces stops being pingable.
It looks like the router sees the translations:
cisco-4331#sh ip nat trans
Pro Inside global Inside local Outside local Outside global
tcp 172.18.195.11:9777 172.18.198.30:22 --- ---
Total number of translations: 1
but the config isn't forwarding.
Any help would be appreciated. I'm sure I'm missing the obvious, but I just can't see it.
Thanks!
- Labels:
-
Other Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2017 10:52 AM
It's a bit difficult as you have blanked out too much ie. your acl 107 references the same network as acl 120 but obviously they cannot be the same.
So the obvious question is does acl 120 allow the traffic through ?
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2017 11:55 AM
Hi Jon,
Thanks for responding. Sorry my security hat got the better of me. Let me provide a bit more info.
access-list 107 permit ip 172.0.0.0 0.255.255.255 any
access-list 107 deny ip any any log
access-list 120 permit gre host 172.xx.xxx.11 any
access-list 120 permit ip 172.0.0.0 0.255.255.255 any
access-list 120 permit ip any 172.0.0.0 0.255.255.255
access-list 120 permit gre any any
access-list 120 permit udp any any eq ntp
access-list 120 deny ip any any log
Both the public (outside) and private (inside) interfaces of the cisco 4331 are on the172.0.0.0 0.255.255.255 networks.
For example: outside int (GigabitEthernet0/0/0) is say... 172.1.1.11
inside int (GigabitEthernet0/0/1) is say... 172.1.2.5
I also tried the config using
access-list 107 permit ip any any
access-list 120 permit ip any any
just to see if I could get something to work. Epic fail on my part.....
I'll attached a less sanitized version with my ip addresses replaced with some numbers:
------
interface GigabitEthernet0/0/0
description link to ISP
ip address 172.1.1.11 255.255.255.0
ip nat outside
ip access-group 120 in
negotiation auto
ip virtual-reassembly
!
interface GigabitEthernet0/0/1
ip address 172.1.2.5 255.255.255.128
ip nat inside
negotiation auto
ip virtual-reassembly
!
interface GigabitEthernet0
vrf forwarding Mgmt-intf
ip address 172.1.1.10 255.255.255.0
negotiation auto
!
ip default-gateway 172.1.1.1
ip nat inside source list 107 interface GigabitEthernet0/0/0 overload
ip nat inside source static tcp 172.1.2.30 22 172.1.1.11 9777 extendable
ip forward-protocol nd
no ip http server
no ip http secure-server
ip route 0.0.0.0 0.0.0.0 172.1.1.1
ip route vrf Mgmt-intf 0.0.0.0 0.0.0.0 172.1.1.1
ip ssh time-out 99
!
!
logging trap debugging
logging facility local6
logging host 172.1.2.65
access-list 107 permit ip 172.0.0.0 0.255.255.255 any
access-list 107 deny ip any any log
access-list 120 permit gre host 172.1.1.11 any
access-list 120 permit ip 172.0.0.0 0.255.255.255 any
access-list 120 permit ip any 172.0.0.0 0.255.255.255
access-list 120 permit gre any any
access-list 120 permit udp any any eq ntp
access-list 120 deny ip any any log
---------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2017 12:08 PM
What is the source IP you are trying to access the internal server from ?
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2017 12:12 PM
It is also a 172 address. Let's say 172.10.10.7
Sorry I omitted that info.
What I find puzzling is that GW0/0/0 isn't pingable from other networks when i add the line "ip nat outside". If that line is removed, the interface is pingable.
Thanks for your help. It's appreciated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2017 12:30 PM
That IP 172.10.10.7 is not in the same subnet as 172.1.1.11. Is it meant to be ?
What I was wanting to do was not use the interface IP as a test ie. instead of 172.1.1.11 in your NAT statement try a spare 172.1.1.x IP and see if that works.
As far as I can tell there is nothing wrong with your configuration but although I have not used the ISR you are using I have seen a few NAT related issues with them. I checked the configuration guide and cannot see anything obvious that would explain what you are seeing.
With your configuration you should be able to ping the interface which is why I wanted to try using a different IP in your static NAT statement.
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2017 12:35 PM
Hi Jon,
No, the ip address of the desktop systems aren't meant to be on the same network as the outside interface of the router. I'll have folks accessing the router from several networks and VPNs.
I had a suspicion it was a routing issue that I couldn't figure out.
I'll try using a spare 172.1.1.x ip and let you know how it goes.
Thanks for going over the config. An extra pair of eyes helps.
Cheers,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2017 01:26 PM
Hi,
I changed my nat statement from:
ip nat inside source static tcp 172.1.2.30 22 172.1.1.11 9777 extendable
to:
ip nat inside source static tcp 172.1.2.30 22 172.1.1.12 9777 extendable
I then put a laptop on the same network on the same vlan as the outside interface of the router.
I tried to ping 172.1.1.11 and 172.1.1.12 from the laptop (ip=172.1.1.100) and it still fails.
this is a head scratcher!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2017 01:35 PM
I cannot see why the ping to 172.1.1.11 does not work, that makes no sense to me. The ping to 172.1.1.12 would fail with that NAT statement.
Can you debug NAT and try to connect to 172.1.1.12 on the specific port number and see if it tells you anything.
I did find another thread which suggested using route maps with the NAT translations but I couldn't find this mentioned as a requirement in the configuration guides and can't see any reason why you would need to.
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-10-2017 09:23 AM
Hi Jon,
I wanted to give you an update. Thanks for the suggestion about debugging the nat. While the nat was fine, I did a debug ip packet detail and noticed some traffic going out my management interface that shouldn't.
It seems the issue was the fact that I put a route on the management interface, and a default route on the router. The fact that there were basically the same was causing traffic to be misdirected.
I put the management interface into another vlan and all worked.
Thanks for looking at my config. Your suggestion is what got me looking in the right direction.
Cheers,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-10-2017 09:50 AM
No problem, thanks for letting me know it is working.
Jon
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide