- Cisco Community
- Technology and Support
- Networking
- Switching
- Communication of two different VLANs(Layer 2 switch) without the help of Layer 3 devices.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-21-2019 10:58 AM - edited 08-21-2019 11:11 AM
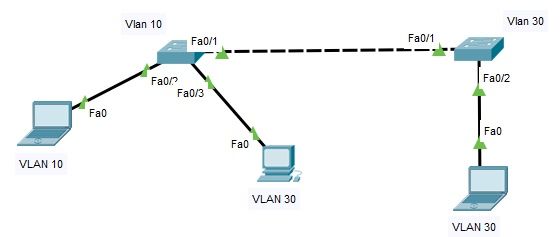
I have created two VLANs(as shown in images)respectively to two switches, Switch1 has VLAN 10 and Switch2 has VLAN 30,the switches are directly connected, my question is that how the two different VLAN's are communicating without the help of layer3 devices?(pinging images is also attached),so,if two different VLANs are communicating then why we use layer3 device?(when we do it straightway)
P.S. : 1.Normal layer2 switch(Manageable)
2.The port which connects the two switches is not trunk.(hence,no trunking is done).
3. I have given IP's as 192.168.1.1/24 and 192.168.1.2/24 (192.168.1.x /24)
also,what is the use of VLANs, if two different are communicating(like in terms of security {security flaws} ).
Thanks in advance :)
Solved! Go to Solution.
- Labels:
-
Other Switching
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-21-2019 11:59 AM
Hi,
Like if we have created vlan 10 in sw1 and vlan 20 in sw2 with same subnet/network, they will communicate?(no trunking)
That is correct as long as the connection between the 2 switches is access configured as access port.
I'm asking what is the use of trunking then,if different vlans are communicating(i guess,if a switch holds more than one vlan then, same network/subnet is also not applicable,in this case trunking is useful?)
So, you need trunking when have multiple vlans crossing the same link. So, say you have vlan 10 and 20 on one switch and you configure the same 2 vlans in the second switch and create an svi for each vlan with IP. Now, if you have a host in one of the vlans connected to the first switch and need to communicate with a different host in a different vlan on the second switch you would need a trunk between the 2 switches. In this case you would also need to enable routing on the second switch as you would have 2 vlans and they need to communicate with each other.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-21-2019 01:27 PM - edited 08-21-2019 01:42 PM
Hi @YamanBelwal0505 ,
If only one VLAN is used on a switch, packets are broadcast on all UP ports (except for which the packet arrived).
If several VLANs are used on a switch, packets will be broadcast only to ports that have the same number of vlan.
The vlan information is not shared between switch, so when configuring a number of vlan in the interface that connects the switches, the device tags that package with the number configured in that port.
Step by step (from left to right):
1-The packet that arrives at the switch from your PC is tagged with the number 10 (f0/2).
2-The packet is retransmitted to the ports with the tag 10 configured (f0/1).
3-The packet is received by the right switch and is tagged with the number 30 (this number is configured in the f0/1).
4-The packet is retransmitted to the ports with the tag 30 configured (f0/2).
5-The process is repeated on the way back.
I suggest you take this test:
1-Generate a ping
2- Immediately, execute this command on the switch to which the PC that generates the ping is connected:
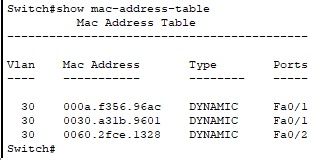
Switch#show mac-address-table
If you execute the command immediately after the ping is generated, it will give you a result like this:
In this picture:
The first MAC is from the neighboring PC
The second MAC is from the fa0/1 interface of the neighboring switch
The third MAC is from the PC that generated the ping
This proves that for this switch, these 3 devices are being tagged with the number of vlan configured on the port that receives the packet.
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-21-2019 08:20 PM
Hi @YamanBelwal0505 ,
So, when the ports are access(access ports, more precisely) they will share single vlan information
The switch tags the packets that reach them with the number of vlan configured.
That tagged packet is relayed only to ports that have the same vlan number.
, but if more than one vlans(for instance, vlan 10 on sw1 and vlan 20 on sw2, they will share info.
Not really.
In your topology, the ping is successful because when the packets arrive from one switch to the other they are re-tagged with a new vlan number, which can be retransmitted to the destination port.
But sw1 has, say, 10 and 20 vlan and sw2 has 40 and 50 vlans, then they will not communicate, if the ports are access too, and in this case we have to use trunking) are created then it will not, we have to use trunking?
The detail, as I mentioned above, is in the number of vlan that you configure in the interfaces of the link that connects the switches.
If you leave the interfaces that connect the switches in trunk mode, then the packets are not re-tagged, keeping the number of vlan so they were labeled by the first switch.Not being re-tagged, the packet is not retransmitted to the port with a different number of vlan, so the ping is no longer successful.
This can be checked in your original topology if you leave the link that connects the switches in trunk mode.
Make these changes:
Switch0
Switch(config)#interface fastEthernet 0/1
Switch(config-if)#no switchport access vlan 10
Switch(config-if)#switchport mode trunk
Switch1
Switch(config)#interface fastEthernet 0/1
Switch(config-if)#no switchport access vlan 30
Switch(config-if)#switchport mode trunk
After these changes the ping is no longer successful, because the packets are no longer re-tagged.
Note that the ping is no longer successful even if the PCs belong to the same network.
Finally, the usefulness of the vlan is to achieve separate the diffusion domains, making only the devices belonging to the same diffusion domain can communicate with each other.
Regards
Remember to mark the correct answers as solved, because that helps other users with similar questions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-21-2019 08:37 PM
Hi @YamanBelwal0505 ,
I have one more question, then what us the use of this type of topology (Which I uploaded at first). Take an instance, in a company there is two departments namely, Sales and Engineering. Like sw1 has VLAN "Sales" and Sw2 has VLAN "Engineering", switches are connected, then it will share the information? Then what's the use?
Also, Is this a Bug? Or It happens for a reason?
If in your topology you have more than one vlan, the correct thing is to configure the links that connect the switches in trunk mode.
That prevents the packets from being re-tagged and achieves the purpose of the vlan, that is, that the packets are only retransmitted to the ports with the same vlan number configured.
Also, take another instance, sw1 has VLANs 10 and 20 and sw2 has VLANs 50 and 60 then, they will not share information(ignore trunking) even if they share same network/subnet whereas if, both switches has VLAN 10 in one and VLAN 20 in other, they will communicate.
I give you an example:
Switch1(vlan 10, 20, 30) <- trunk mode link -> Swtich2 (vlan 10, 40, 50)
In this topology, there will only be successful ping among the vlan10 PCs.
In order to have connectivity between PCs of different vlan, you will need a layer 3 device that does intervlan routing.
Regards
Remember to mark the correct answers as solved, because that helps other users with similar questions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-21-2019 11:30 AM
2.The port which connects the two switches is not trunk.(hence,no trunking is done).
Since you are using one vlan per switch, there is no need for a trunk and the vlan id can and are different (10 and 30). So everything works as expected. Now, if you configure 2 vlans per switch say 10 and 20 on one switch and 30 and 40 on the other than you would need a trunk and the vlan ids much match.
3. I have given IP's as 192.168.1.1/24 and 192.168.1.2/24 (192.168.1.x /24)
You have 2 vlans (10 and 30) but they are both in the same subnet. So, there is no need for routing as you only have 1 subnet.
also,what is the use of VLANs, if two different are communicating(like in terms of security {security flaws} ).
not sure if I understand but vlans/subnets are used to segment traffic.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-21-2019 11:52 AM
Sir/Mam
Thank You for the immediate reply.
Like if we have created vlan 10 in sw1 and vlan 20 in sw2 with same subnet/network, they will communicate?(no trunking)
and if I do trunking,then it will not communicate(which is obvious).so, I'm asking what is the use of trunking then,if different vlans are communicating(i guess,if a switch holds more than one vlan then, same network/subnet is also not applicable,in this case trunking is useful?)
Also I didn't understand much precisely like different vlan(although one vlan per switch is communicating) are communicating?(how)?
Thank You. :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-21-2019 11:59 AM
Hi,
Like if we have created vlan 10 in sw1 and vlan 20 in sw2 with same subnet/network, they will communicate?(no trunking)
That is correct as long as the connection between the 2 switches is access configured as access port.
I'm asking what is the use of trunking then,if different vlans are communicating(i guess,if a switch holds more than one vlan then, same network/subnet is also not applicable,in this case trunking is useful?)
So, you need trunking when have multiple vlans crossing the same link. So, say you have vlan 10 and 20 on one switch and you configure the same 2 vlans in the second switch and create an svi for each vlan with IP. Now, if you have a host in one of the vlans connected to the first switch and need to communicate with a different host in a different vlan on the second switch you would need a trunk between the 2 switches. In this case you would also need to enable routing on the second switch as you would have 2 vlans and they need to communicate with each other.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-21-2019 12:06 PM - edited 08-21-2019 12:20 PM
Sir/Mam
I got it about the trunking part.
But in the scenario where one switch has one vlan 10 and the other has vlan 20 and one-one host is connected to it,so the vlan's communicate(share data),i don't understand that one.(so what's different in it{vlans}).(we know different vlans dosen't communicate using l3 devices).
Note: I'm using same subnet(192.168.1.x /24)(that's why they are communicating?I GUESS)
I think when switches are connected through access port and having same subnet/network then the data ignore's the vlan and passes the information( Is it so?)
Although the vlans are different but subnet/network are same? Is this enough to communicate VLANs? If, it is, then what is the use of different vlan?
Thanks :) for helping
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-21-2019 12:35 PM
I recommend you take a look at this video. It explains trunk port, access port, routing, etc...
https://www.youtube.com/watch?v=jg0IECQmUjE
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-21-2019 12:47 PM
I'm using same subnet(192.168.1.x /24)(that's why they are communicating?I GUESS)
That is correct. Your 2 vlans are in the same subnet and goes across an access port and that is why it works fine.
I think when switches are connected through access port and having same subnet/network then the data ignore's the vlan and passes the information( Is it so?)
Correct. It is just untagged frame. So, it doesn't care about the vlan id.
Although the vlans are different but subnet/network are same? Is this enough to communicate VLANs? If, it is, then what is the use of different vlan?
In most designs each vlan comes with a corresponding subnet. for example:
vlan 10 10.10.10.0/24
vlan 20 10.10.20.0/24
vlan 30 10.10.30.0/24
etc... So, in this case for example; you can put the accounting department in vlan 10 and engineering in vlan 20 and isolated them from each other, so engineering does not have access to accounting/fiance information or say you want to apply QOS to vlan 30, you can only apply it to that vlan and not the other vlans. So, vlans/subnets breakdown the broadcast domain into smaller segment and give you flexibility to apply a policy to one or 2 vlans and not the others.
HTH
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-21-2019 11:31 AM
Hi @YamanBelwal0505 ,
Could you compress your pkt exercise (winzip) and attach it for testing?
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-21-2019 11:58 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-21-2019 11:59 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-21-2019 01:27 PM - edited 08-21-2019 01:42 PM
Hi @YamanBelwal0505 ,
If only one VLAN is used on a switch, packets are broadcast on all UP ports (except for which the packet arrived).
If several VLANs are used on a switch, packets will be broadcast only to ports that have the same number of vlan.
The vlan information is not shared between switch, so when configuring a number of vlan in the interface that connects the switches, the device tags that package with the number configured in that port.
Step by step (from left to right):
1-The packet that arrives at the switch from your PC is tagged with the number 10 (f0/2).
2-The packet is retransmitted to the ports with the tag 10 configured (f0/1).
3-The packet is received by the right switch and is tagged with the number 30 (this number is configured in the f0/1).
4-The packet is retransmitted to the ports with the tag 30 configured (f0/2).
5-The process is repeated on the way back.
I suggest you take this test:
1-Generate a ping
2- Immediately, execute this command on the switch to which the PC that generates the ping is connected:
Switch#show mac-address-table
If you execute the command immediately after the ping is generated, it will give you a result like this:
In this picture:
The first MAC is from the neighboring PC
The second MAC is from the fa0/1 interface of the neighboring switch
The third MAC is from the PC that generated the ping
This proves that for this switch, these 3 devices are being tagged with the number of vlan configured on the port that receives the packet.
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-21-2019 06:54 PM
Thanks for the help. :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-21-2019 01:42 PM
Hi @YamanBelwal0505 ,
In your current topology, if you add a third PC with the opposite vlan number, it will not be able to communicate with any PC, as the switch will not have another port through which to retransmit the packet.
To get a switch port to relay more than one vlan, you must configure both ends of the link in trunk mode.
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-21-2019 06:58 PM - edited 08-21-2019 07:00 PM
So, when the ports are access(access ports, more precisely) they will share single vlan information, but if more than one vlans(for instance, vlan 10 on sw1 and vlan 20 on sw2, they will share info. But sw1 has, say, 10 and 20 vlan and sw2 has 40 and 50 vlans, then they will not communicate, if the ports are access too, and in this case we have to use trunking) are created then it will not, we have to use trunking?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-21-2019 08:20 PM
Hi @YamanBelwal0505 ,
So, when the ports are access(access ports, more precisely) they will share single vlan information
The switch tags the packets that reach them with the number of vlan configured.
That tagged packet is relayed only to ports that have the same vlan number.
, but if more than one vlans(for instance, vlan 10 on sw1 and vlan 20 on sw2, they will share info.
Not really.
In your topology, the ping is successful because when the packets arrive from one switch to the other they are re-tagged with a new vlan number, which can be retransmitted to the destination port.
But sw1 has, say, 10 and 20 vlan and sw2 has 40 and 50 vlans, then they will not communicate, if the ports are access too, and in this case we have to use trunking) are created then it will not, we have to use trunking?
The detail, as I mentioned above, is in the number of vlan that you configure in the interfaces of the link that connects the switches.
If you leave the interfaces that connect the switches in trunk mode, then the packets are not re-tagged, keeping the number of vlan so they were labeled by the first switch.Not being re-tagged, the packet is not retransmitted to the port with a different number of vlan, so the ping is no longer successful.
This can be checked in your original topology if you leave the link that connects the switches in trunk mode.
Make these changes:
Switch0
Switch(config)#interface fastEthernet 0/1
Switch(config-if)#no switchport access vlan 10
Switch(config-if)#switchport mode trunk
Switch1
Switch(config)#interface fastEthernet 0/1
Switch(config-if)#no switchport access vlan 30
Switch(config-if)#switchport mode trunk
After these changes the ping is no longer successful, because the packets are no longer re-tagged.
Note that the ping is no longer successful even if the PCs belong to the same network.
Finally, the usefulness of the vlan is to achieve separate the diffusion domains, making only the devices belonging to the same diffusion domain can communicate with each other.
Regards
Remember to mark the correct answers as solved, because that helps other users with similar questions
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide