- Cisco Community
- Technology and Support
- Networking
- Switching
- Re: End to End Routing design / routing convergence with Firewalls / NAT / ACL engines and State tab...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
End to End Routing design / routing convergence with Firewalls / NAT / ACL engines and State tables
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-31-2017 07:36 AM - edited 03-08-2019 12:34 PM
Gday Cisco folks,
we use BGP internally, internal to perimeter Firewalls and on the outside due to running a Public ASN.
We only receive two default routes from each ISP and are not running partials or full tables.
The end to end routing design works great, as convergence works pretty well across what ever path is still available, also having said that we have two DC locations with two independent firewall clusters.
Now if failing over from one DC to the other, obviously we loose our state information and users have to reconnect. But this is not the topic of this discussion.
What I am after is, is there any way that modern Firewalls can influence their routing behavior / revoke routes if they notice an issue with their NAT translation process going wrong and also the ACL filtering process failing or being stopped.
It seems like routing protocols is one domain, while NAT and ACL engines can fail on the firewall, causing full outages to the customer due to it dropping packets on NAT/ACL side, while BGP can still see the default routes from the border routers towards the firewalls on the core routers.
BGP peering is done on a hop by hop basis, interface to interface, not using multihop.
Core BGP ASN 65000 - Firewalls BGP ASN 65001 - Border routers ASN xxxx (public)
Has anyone come across the similar need to have the Firewalls be able to remove IGP/BGP routes if their ACL / NAT engines fail to work? It seems like these are still handled as independent tasks rather than combine the two worlds..
If so, how do you handle this?
And if there is a Cisco guy watching this one, please pass on to the correct BU.
THX
Colin
- Labels:
-
Other Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-31-2017 12:43 PM
Hello,
the Cisco ASA firewalls are capable of doing stateful failover (that feature has been around for quite a while). Is that what you are after ? You can even configure a High Availability (HA) cluster with both firewalls forwarding traffic (active/active) and stateful failover (the only thing that doesn't work in that setup is IPSec and SSL VPN)...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-03-2017 11:37 PM
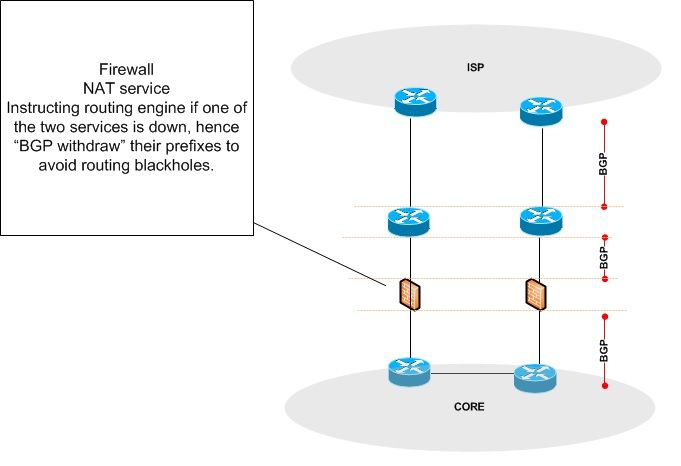
I think 1 picture explains it way better/easier than a 1000 words could :) what I am after to see from vendors in future:
Please let me know if this already exists and I will back off :)
In some cases I have had the occasion that the "firewall product" had an issue with its NAT or Firewall / filtering binary and halted those processes, as the routing process usually is a different, its unaware that the Firewall appliance or one of those two services is actually dropping traffic and is still attracting BGP routes for example.
Hence the firewalls failed NAT/Filtering services has cause traffic "blackholes" as such..
Hence I am looking for a feature / design to account for this issue. Potentially raising this idea to Cisco developers if this is a reasonable thing to do.
Thanks
Colin - www.flashcardguy.ch
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide