- Cisco Community
- Technology and Support
- Networking
- Switching
- how to create an ACL for dynamic nat
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-28-2011 07:50 PM - edited 03-07-2019 03:38 AM
hi
i want to setup a ACL to deny a certain access from a particular ip range.
bu this ip range shares same addresses from same nat pool.
in this case how do i write ACL? since i can not specify the source address.
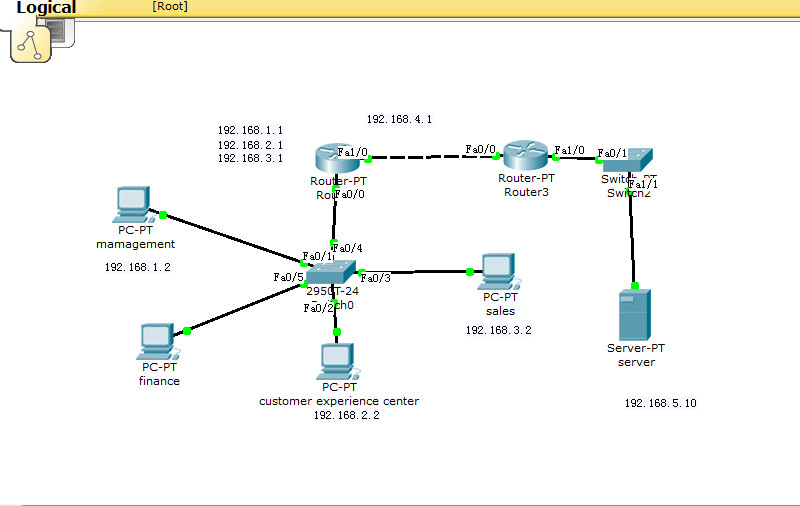
here is brief config file:
!
ip dhcp excluded-address 192.168.1.1 192.168.1.10
ip dhcp excluded-address 192.168.2.1 182.168.2.10
ip dhcp excluded-address 192.168.3.1 192.168.3.10
ip dhcp excluded-address 192.168.99.1 192.168.99.10
!
ip dhcp pool managment
network 192.168.1.0 255.255.255.0
default-router 192.168.1.1
ip dhcp pool finance
network 192.168.99.0 255.255.255.0
default-router 192.168.99.1
ip dhcp pool sales
network 192.168.3.0 255.255.255.0
default-router 192.168.3.1
ip dhcp pool customer_exp
network 192.168.2.0 255.255.255.0
default-router 192.168.2.1
!
interface FastEthernet0/0
no ip address
duplex auto
speed auto
!
interface FastEthernet0/0.1
encapsulation dot1Q 10
ip address 192.168.1.1 255.255.255.0
ip nat inside
!
interface FastEthernet0/0.2
encapsulation dot1Q 20
ip address 192.168.2.1 255.255.255.0
ip nat inside
!
interface FastEthernet0/0.3
encapsulation dot1Q 30
ip address 192.168.3.1 255.255.255.0
ip nat inside
!
interface FastEthernet0/0.10
encapsulation dot1Q 99
ip address 192.168.99.1 255.255.255.0
ip access-group 1 out
ip nat inside
!
interface FastEthernet1/0
ip address 192.168.4.1 255.255.255.0
ip nat outside
duplex auto
speed auto
!
interface Serial2/0
no ip address
shutdown
!
interface Serial3/0
no ip address
shutdown
!
interface FastEthernet4/0
no ip address
shutdown
!
interface FastEthernet5/0
no ip address
shutdown
!
router rip
version 2
network 192.168.4.0
no auto-summary
!
ip nat pool my_nat 192.168.4.10 192.168.4.200 netmask 255.255.255.0
ip nat inside source list 2 pool my_nat
ip classless
!
!
access-list 1 deny 192.168.2.0 0.0.0.255
access-list 1 deny 192.168.3.0 0.0.0.255
access-list 1 permit 192.168.1.0 0.0.0.255
access-list 1 permit any
access-list 2 permit 192.168.1.0 0.0.0.255
access-list 2 permit 192.168.2.0 0.0.0.255
access-list 2 permit 192.168.3.0 0.0.0.255
access-list 2 permit 192.168.99.0 0.0.0.255
!
if i want to deny the access of 192.168.2.0 /24 to 192.168.5.10 ,how do i write ACL and place it on the f0/0 of router 3 ?
thanks in advance .
Solved! Go to Solution.
- Labels:
-
Other Switching
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2011 01:29 AM
Hi Dannan,
You can do like below what I have in my router and working as desired.
ip nat pool NONAT 192.168.4.10 192.168.4.200 netmask 255.255.255.0
ip access-list extended NONAT
deny ip 192.168.2.0 0.0.0.255 host 192.168.5.10
permit ip any any
Please rate the helpfull posts.
Regards,
Naidu.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2011 08:47 AM
Hi,
yes you can do it like this as this tells the router which traffic to nat depending on a match with a permit statement in the ACL.
Regards.
Alain
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2011 04:14 AM
Nat happens after acl
So simply use acl like the below and apply it to fa0/0
Access-list 100 deny ip 192.168.2.0 0.0.0.255 192.168.5.0 0.0.0.255
Access-list 100 permit ip any any
Interface fa0/0
Ip access-group 100 in
Or you can apply it under fa0/0.2
Hope this help
If helpful rate
Sent from Cisco Technical Support iPhone App
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2011 09:17 AM
Hi Dannan,
Please see the attached link, which shows the Order of Operation of NAT on Cisco IOS devices.
An INBOUND access-list (ip access-group ACL in) is checked Before NAT
An OUTBOUND access-list (ip access-group ACL out) is checked After NAT
So this gives you options for matching against 'Real' or Translated IP addresses.
Hope that Helps,
Nick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2011 01:48 PM
thanks for your help, but i am wondering if i can do it with dynimic nat ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2011 12:21 AM
Hi,
why don't you just configure an extended ACL for the dynamic NAT:
access-list 199 deny ip 192.168.2.0 0.0.0.255 host 192.168.5.10
access-list 199 permit ip any any
ip nat inside source list 199 pool my_nat
This way as traffic from 192.168.2.0 to host 192.168.5.10 will not get natted you are preventing communication between this subnet and this host.
Regards.
Alain
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2011 01:29 AM
Hi Dannan,
You can do like below what I have in my router and working as desired.
ip nat pool NONAT 192.168.4.10 192.168.4.200 netmask 255.255.255.0
ip access-list extended NONAT
deny ip 192.168.2.0 0.0.0.255 host 192.168.5.10
permit ip any any
Please rate the helpfull posts.
Regards,
Naidu.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2011 09:21 AM
thanks naidu, appreciate your help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2011 08:44 AM
thank you for your help guys. but if i want only deny www service to the 192.168.2.0/24 .
can i write
access-list 199 deny tcp 192.168.2.0 0.0.0.255 host 192.168.5.10 eq www
access-list 199 permit ip any any
ip nat inside source list 199 pool my_nat
??
i am not so sure if i can do that because the way nat works is to change the IP header , if my access-list is based on the tcp then it probably won't work , but it is just my assumption. correct me if i am wrong .
regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2011 08:47 AM
Hi,
yes you can do it like this as this tells the router which traffic to nat depending on a match with a permit statement in the ACL.
Regards.
Alain
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2011 09:20 AM
thanks alain, you are the man.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide