- Cisco Community
- Technology and Support
- Networking
- Switching
- mac-based Authentication
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2022 01:15 AM
does Cisco 3750 switch support IEEE 802.1x mac-based Authentication?how to confiure mac-based Authentication
Solved! Go to Solution.
- Labels:
-
Other Switches
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2022 08:02 AM
Cisco has 2 type :
1. 802.1x with supplicant you can login using supplicant.
2. if there is no supplicant, then need to use MAB, mac address bypass ( that is mac based authentication)
=====Preenayamo Vasudevam=====
***** Rate All Helpful Responses *****
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2022 01:21 AM
what is the version of IOS code running on 3750
below guide help you understand how it can be configured :
=====Preenayamo Vasudevam=====
***** Rate All Helpful Responses *****
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2022 06:52 AM
Both the 802.1X client and the access device can initiate 802.1X authentication.If the client as a initiator,it sends an EAPOL-Start packet to the access device to initiate 802.1X authentication , then the access device will sends an EAP-Request/Identity packet out of the receiving port to the client and the EAP-Request/Identity packet's destination mac address(unicast) is the client's mac address.
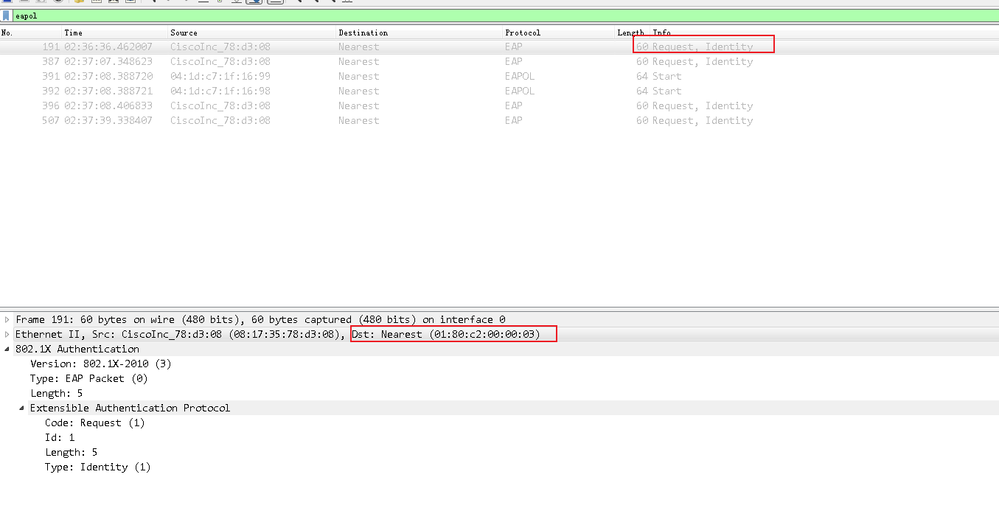
If the access device as a a initiator, it multicasts EAP-Request/Identity packets to initiate 802.1X authentication at the identity request interval,and the EAP-Request/Identity packet's destination mac address is 0x0180.C200.0003.
I use wireshark to catch packet and find that cisco 3750 switch does not handle the EAPOL-Start packet send by client and send EAP-Request/Identity packet to the client and the EAP-Request/Identity packet's destination mac address is 0x0180.C200.0003. so i think cisco switch is as a initiator and initiate 802.1X authentication.,is that right ?
is there command to make 3750 switch not multicasts EAP-Request/Identity packets to initiate 802.1X authentication and not as a initiator ?
Looking forward to your reply!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2022 07:11 AM
I read H3C switch's security configuration guide and find that
H3C implements port-based access control as defined in the 802.1X protocol, and extends the protocol to support MAC-based access control.
· Port-based access control—Once an 802.1X user passes authentication on a port, any subsequent user can access the network through the port without authentication. When the authenticated user logs off, all other users are logged off.
· MAC-based access control—Each 802.1X user is separately authenticated on a port. When a user logs off, no other online users are affected.
H3C switch support two mode , i test in 3750 switch and it seem that 3750 switch only support Port-based access control,is that right?
is there command to specify an access control method ,for example port based or mac based?
H3C switch ,for example
dot1x port-method { macbased | portbased }
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2022 08:02 AM
Cisco has 2 type :
1. 802.1x with supplicant you can login using supplicant.
2. if there is no supplicant, then need to use MAB, mac address bypass ( that is mac based authentication)
=====Preenayamo Vasudevam=====
***** Rate All Helpful Responses *****
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-12-2022 08:51 AM
I read H3C switch's security configuration guide(https://www.h3c.com/en/d_202109/1470055_294551_0.htm) and find that
802.1X authentication initiation
Both the 802.1X client and the access device can initiate 802.1X authentication.
802.1X client as the initiator
The client sends an EAPOL-Start packet to the access device to initiate 802.1X authentication. The destination MAC address of the packet is the IEEE 802.1X specified multicast address 01-80-C2-00-00-03 or the broadcast MAC address. If any intermediate device between the client and the authentication server does not support the multicast address, you must use an 802.1X client that can send broadcast EAPOL-Start packets. For example, you can use the iNode 802.1X client.
Access device as the initiator
If the client cannot send EAPOL-Start packets, configure the access device to initiate authentication. One example is the 802.1X client available with Windows XP.
The access device supports the following modes:
· Multicast trigger mode—The access device multicasts EAP-Request/Identity packets to initiate 802.1X authentication at the identity request interval.
· Unicast trigger mode—Upon receiving a frame from an unknown MAC address, the access device sends an EAP-Request/Identity packet out of the receiving port to the MAC address. The device retransmits the packet if no response has been received within the identity request timeout interval. This process continues until the maximum number of request attempts set by using the dot1x retry command is reached.
The authentication trigger feature enables the access device to initiate 802.1X authentication when 802.1X clients cannot initiate authentication.,and then the access device as the initiator.
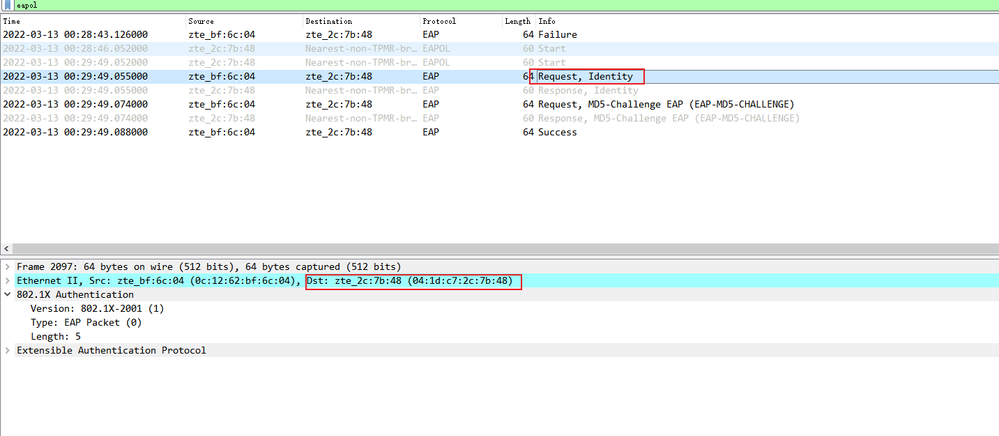
my cilent device can send EAPOL-Start packets,so i want cisco 3750 switch do not multicast EAP-Request/Identity packets just started.
3750 should wait to receive a EAPOL-Start packet and then unicast EAP-Request/Identity packet(EAP-Request/Identity packet'3 destination mac address is client device's mac address ) to client device,
So can 3750 achieve this application scenario?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide