- Cisco Community
- Technology and Support
- Networking
- Switching
- Need Helping Fixing "Enable" Password & VPN Access
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Need Helping Fixing "Enable" Password & VPN Access
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-20-2017 09:16 AM - edited 03-08-2019 12:26 PM
PROBLEM #1
I have 2 identical Cisco 3650 switches. I was trying to reset enable password on switch #1. Followed up tips in an older forum post I made and it ended up removing the pre-authentication that required I log in via privileged user first and then enter "enable" mode with enable password. Now, it logs in directly to enable mode instead. I cannot figure out how to re-add the user back so it requires that method first for extra security.
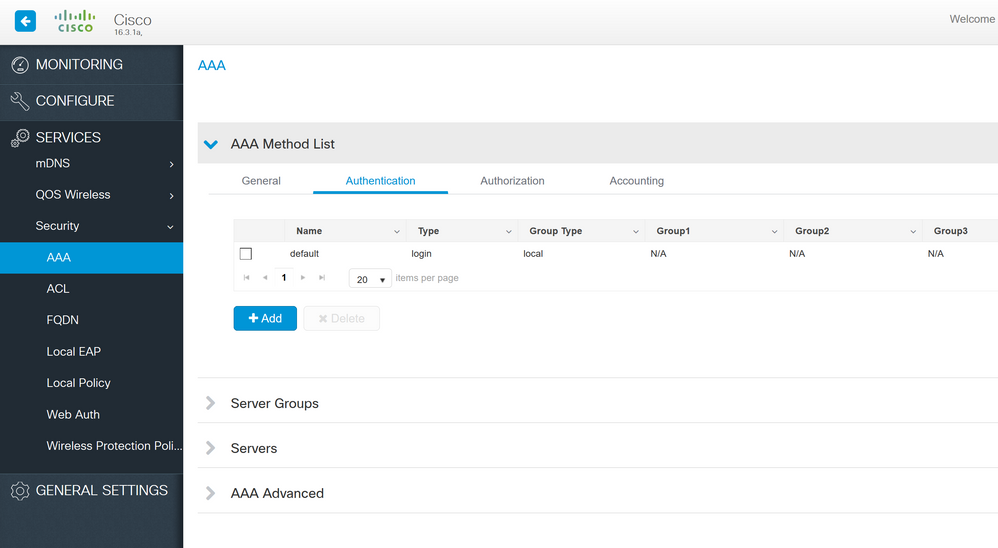
I'm using SecureCRT SSH2 protocol. I was able to access primary switch #1 via web gui using myusername still. I think I might be able to fix the issue via the interface there. See attached, not 100% sure though. Looks like the options are there, but I'd rather not fiddle until someone can clarify.
This is the only thing I see from the moment I log in (goes directly into enabled mode) and running that command, nothing else.
Cisco3650# Cisco3650#conf t Enter configuration commands, one per line. End with CNTL/Z. Cisco3650(config)#no aaa new-model Cisco3650(config)# Cisco3650(config)#end Cisco3650#wr Building configuration... Compressed configuration from 24401 bytes to 9027 bytes[OK] Cisco3650#
Here's a comparison of the 2 switches.
Switch #1 (main one trying to fix)
version 16.3 no service pad service timestamps debug datetime msec service timestamps log datetime msec service password-encryption service compress-config no service password-recovery no platform punt-keepalive disable-kernel-core ! hostname Cisco3650 ! ! vrf definition Mgmt-vrf ! address-family ipv4 exit-address-family ! address-family ipv6 exit-address-family ! ! no aaa new-model clock timezone EST -5 0 facility-alarm critical exceed-action shutdown switch 1 provision ws-c3650-24ts
Switch #2 (works correctly by logging into myusername first and manually having to enter "en" mode)
version 16.3 no service pad service timestamps debug datetime msec service timestamps log datetime msec service compress-config no service password-recovery no platform punt-keepalive disable-kernel-core ! hostname Switch2 ! ! vrf definition Mgmt-vrf ! address-family ipv4 exit-address-family ! address-family ipv6 exit-address-family ! no logging console enable secret 5 xxxxxxxxxxxxxxxx enable password TLNsxxxxxxxxxxxxxxxx ! no aaa new-model clock timezone EST -5 0 facility-alarm critical exceed-action shutdown switch 2 provision ws-c3650-24ts
PROBLEM #2
So in addition to the enable mode password issue on switch #1 I'm having this odd issue with switch #2 where it works fine (logs into myusername first, then into enable mode). However, it doesn't work with new enable password I set when I log in via VPN IP address which is already whitelisted in ACL and worked fine before I reset enable password. It's crazy, I log in just fine directly via SSH2 but via the VPN IP it no longer works. It works on myusername/pw but enable pw won't work. Same one works directly into switch. ACL config is 100% identical on switches #1 and #2 as well.
- Labels:
-
Other Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-01-2017 10:02 AM
How would I enable "aaa new-model"?
Since it is working, you do not need to.
I tried to access via another IP, a VPN IP and it correctly authenticated with user/pw and then enable mode. Odd, not sure why it won't do that from my local IP (both are whitelisted in config).
The SSH login info associated with your IP could be cached in your computer. If you try it from a different computer, it might work with your IP as well. Make sure you have the correct enable password. One way to be sure is to add the password as follows: "enable secret 0 ENTER_PASSWORD" where ENTER_PASSWORD is unencrypted password.
HTH,
Meheretab
Meheretab
- « Previous
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide