Ospf route in database not in routing table when standby takes over
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2016 08:09 AM - edited 03-08-2019 08:27 AM
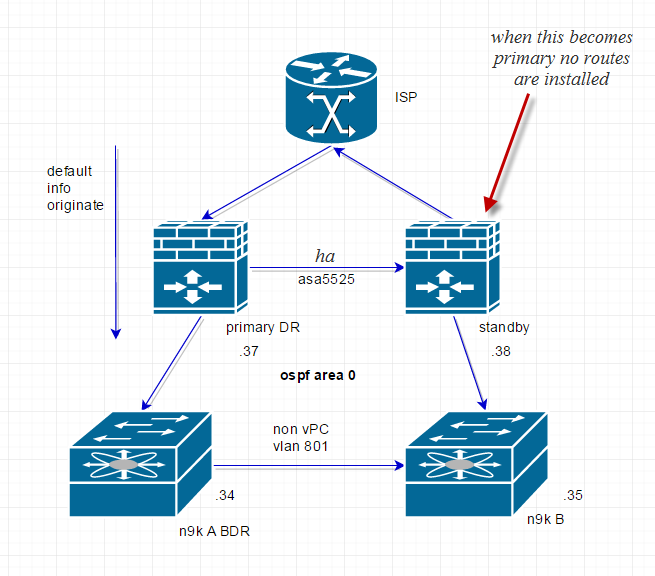
hello, guys... im having a problem setting up this network. im wanting to advertise a default from my asa to my switches, it works fine my primary asa is the one doing it but when i force a failover to the other side. my ospf routes are not being installed in the routing table. i can see them in the database but nothing else. i noticed that when this happens my database router info of the asa changes from transit to stub.... any thoughts??
n9k-A # show ip ospf database router 192.168.5.37 detail (good output)
OSPF Router with ID (192.168.0.1) (Process ID 215 VRF default)
Router Link States (Area 0.0.0.0)
LS age: 10
Options: 0x22 (No TOS-capability, DC)
LS Type: Router Links
Link State ID: 192.168.5.37
Advertising Router: 192.168.5.37
LS Seq Number: 0x80000007
Checksum: 0x7f75
Length: 36
AS border router
Number of links: 1
Link connected to: a Transit Network
(Link ID) Designated Router address: 192.168.5.34
(Link Data) Router Interface address: 192.168.5.37
Number of TOS metrics: 0
TOS 0 Metric: 10
n9k-A # show ip ospf database router 192.168.5.37 detail (bad output)
OSPF Router with ID (192.168.0.1) (Process ID 215 VRF default)
Router Link States (Area 0.0.0.0)
LS age: 18
Options: 0x22 (No TOS-capability, DC)
LS Type: Router Links
Link State ID: 192.168.5.37
Advertising Router: 192.168.5.37
LS Seq Number: 0x80000005
Checksum: 0x46c4
Length: 36
AS border router
Number of links: 1
Link connected to: a Stub Network
(Link ID) Network/Subnet Number: 192.168.5.32
(Link Data) Network Mask: 255.255.255.248
Number of TOS metrics: 0
TOS 0 Metric: 10
- Labels:
-
Other Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2016 02:25 PM
Hi,
Questions:
Does vlan 801 span between both 9ks and the firewalls?
What does OSPF peering show after the fail-over?
What happens if you shut down n9k-A?
Is there OSPF peering between 9ks?
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2016 02:30 PM
yes vlan 801 is shared between both switches.
when i failover the OSPF still up but none of the routes is the DB are installed on neither 9k or ASA.
i havent tried shutting it down.
and yes OSPF is running between both 9k
output of 9k-B
n9k-B # show ip ospf neighbors
OSPF Process ID 215 VRF default
Total number of neighbors: 4
Neighbor ID Pri State Up Time Address Interface
192.168.0.1 100 FULL/DR 1d00h 192.168.5.34 Vlan801
192.168.5.37 200 EXSTART/BDR 00:00:11 192.168.5.37 Vlan801 <--- asa
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-09-2016 06:53 AM
here is an update from TAC.
Due to the topoolgy and the OSPF network between nexusAB and the active firewall being broacast, DR and BDR must be selected. if we set the firewall as DR and failover occurs the secondary firewall (now active) loses the DR role and it goes to one of the BDR nexus, if that nexus is not directly connected to the current active firewall , the routes do not get installed because the DR is 2 hops "ttl=253" away from the firewall
"192.168.5.37 200 EXSTART/BDR 00:00:11 192.168.5.37 Vlan801"
to fix this we must get both switches to have a stable neighbor relationship with any of the ASA's.
This is a common issue on the nexus platform. on the 7k it can be fixed by excluding the vlan from the vpc peer link " peer-gateway exclude vlan xxx" but this option is not available in 9k. the work around for this is to setup a normal trunk uplink between both switches allowing only vlan801 and removing it from the vPC peerlink.
or stop using OSPF between them and use static routes with HSRP running on the nexus side.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-09-2016 07:43 AM
Thanks for the update Tomas!
So, basically you need an additional physical connection from N9kA to stand-by firewall and one from N9kB to primary firewall all in the same vlan right?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2016 08:38 AM
well i just removed the vlan from the peer link and added a new non vpc trunk but it get the same problem. i dont know why the ttl is reduced.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2016 09:35 AM
How about connecting them in full mesh, where N9k-A and B peer with both firewalls.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-15-2016 08:05 AM
update: verified the vPC, excluded the VLAN from the vPC and then found that the OSPF on both switches are peering with the same MAC address, causing the upstream Nexus unable to form neighbour with the ASA. by manuall setting MAC addresses in each Switch SVI the OSPF came up right away.