- Cisco Community
- Technology and Support
- Networking
- Switching
- Re: port-security behavior after moving to a non security port
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-28-2023 06:37 AM
Hello all,
I would just like to ask, if the described port-secuity behaviour is expected by that feature.
A cisco switch catalyst 9200 or 9300 with IOS-XE 17 (behaviour seen on IOS XE 17.3.5 and 17.6.5). Some ports configured with port-security and some of them - not. All of them are access ports with access vlan1. A client with mac "aaa.aaa.aaa" is connected over a small desktop bridge to a cisco switch port 1 with port-security enabled. The port-security config on port contains also max mac address 100, violation restrict and no aging time. The "show port-security address" and "show mac address table" show both the mac "a.a.a.a" on Port1 and vlan 1.
After that the client is diconnected from the port 1 and connected to port 2, that does not have port-security config on it. It just has "switchport access vlan1". Because the client was connected to the port 1 over a bridge, the port 1 stays "Up" (brige is still conencted to port 1). The port-security address table still shows the mac "aaa.aaa.aaa" on port1. The switch mac address table shows the mac "aaa.aaa.aaa" during 5 minutes on port 1 till the mac is aged out.
Now the mac address forwarding table of the switch does not have the mac address "aaa.aaa.aaa" any more, but the client is connected to port 2 and the port shows status "Up". The client does not have access to the network. The switch logs do not show any security violation entries. But the switch silent does not allow the packets from "aaa.aaa.aaa"on port 2 through. The port-security address table still has the mac "aaa.aaa.aaa" on port 1.
I'm clear, that such configuration does not make much sence, but a customer of us has it and cannot change the config because of internal security policy.
Is it a normal and expected behaviour?
Thanks.
best regards,
Solved! Go to Solution.
- Labels:
-
Catalyst 9000
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-27-2023 04:08 PM
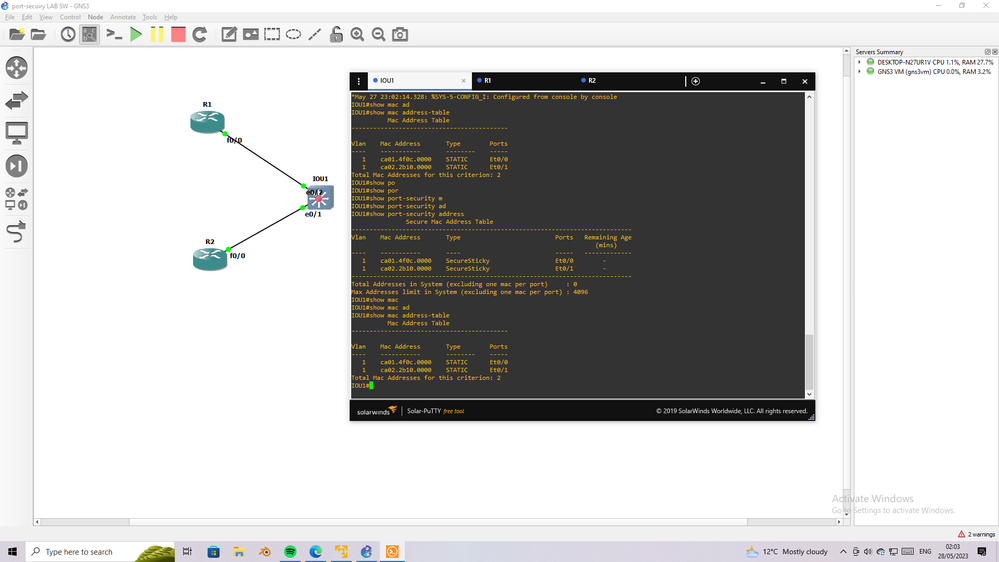
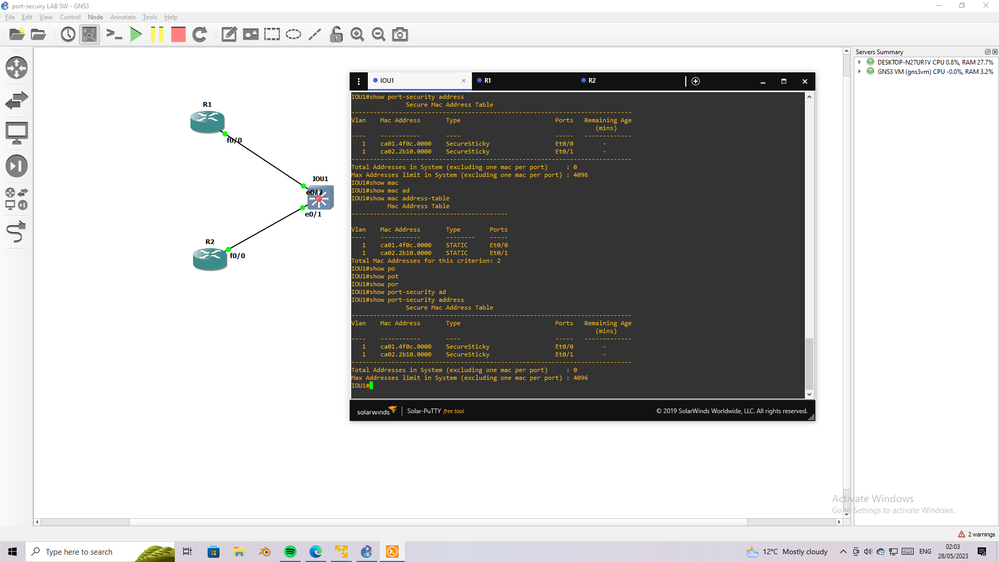
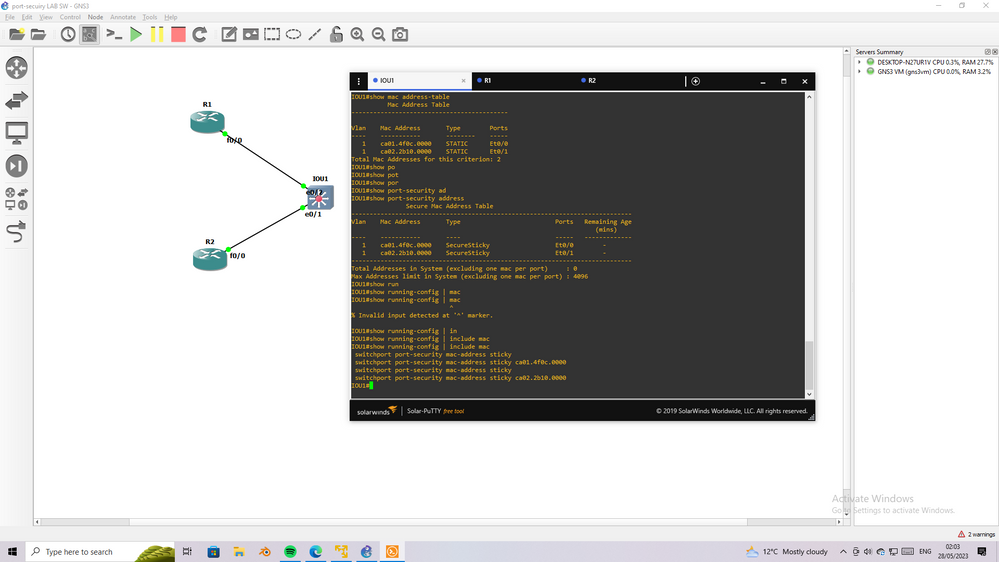
Yes this expected behave,
I run lab and show you how the R2 can not ping to R1 anymore when R1 change it connect port to SW (it was connect to port with security and move to connect to port without port-security)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-28-2023 06:42 AM - edited 04-28-2023 07:46 AM
if you use dynamic port-security learn then use aging for port-security this will clear the mac after predefined time.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2023 12:09 AM
Hello,
it is clear, what you wrote about the aging time. The question was, if it is a expected behaviour, that a mac address known on a port with configured with port-security will be blocked on another port of teh same switch, where the port security is not not configured.
Thanks in advance,
Best regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-27-2023 04:08 PM
Yes this expected behave,
I run lab and show you how the R2 can not ping to R1 anymore when R1 change it connect port to SW (it was connect to port with security and move to connect to port without port-security)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-28-2023 07:45 AM
Hello
Any specific restriction from your customer to not use Aging time? It seems this could minimize or fix the problem.
mac address-table aging-time [0 | 10-1000000] [routed-mac | vlan vlan-id]
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide