- Cisco Community
- Technology and Support
- Networking
- Switching
- Thanks Cofee - super busy at
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Routing Internet/external INBOUND to a network using Router-on-a-Stick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-05-2016 12:03 AM - edited 03-08-2019 08:26 AM
Hi All,
hopefully this is the right place for this question -
I'm trying to configure my 2811 ROUTER, which is on its own network (172.16.0.0/16) so I can access it from ADSL routers network (192.168.1.0/24) e.g. ssh from my 192.x addresses INTO the 172.16.x addresses. This sounds easy enough (and might be after someone answers it) but I've tried various STATIC NAT and ROUTE-MAP config examples from the forums and blogs online and I think I'm just confusing myself.
So I'm here to ask the experts cos my networking (and cisco) skills aren't the greatest.
The gear is old gear I just use to do and learn some networking/cisco - so what I'm working with is
1 x 2811 ROUTER
1x 3550XL SWITCH
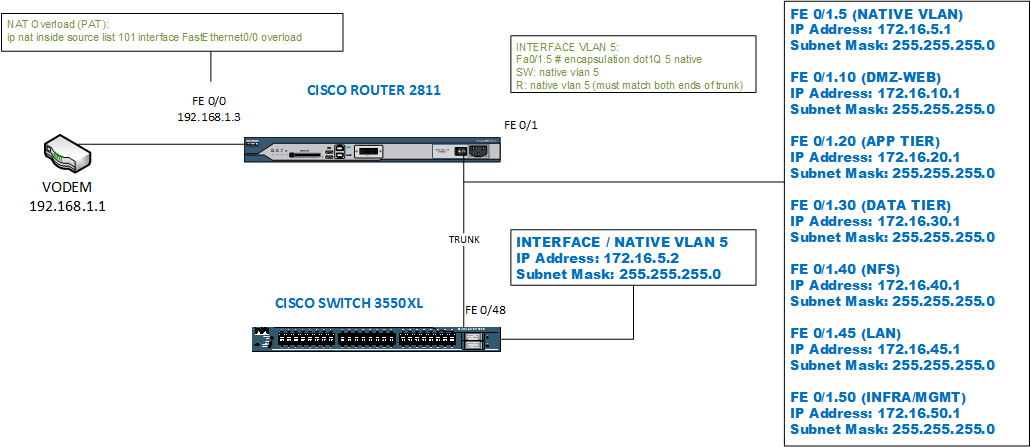
I'm using the ROUTER-ON-A-STICK setup with a trunked switchport from switch-->router, which does my INTER-VLAN routing on FE0/1
Objective: to be able to sit out here in 192.168.x.x land and network INBOUND to the various VMs and devices that live in 172.16.x.x land
Diagram of current (working) setup - everything in 172.16.x.x land can reach the internet happily:
DHCP exclusions & Pools
ip dhcp excluded-address 172.16.5.1 172.16.5.10
ip dhcp excluded-address 172.16.10.1 172.16.10.10
ip dhcp excluded-address 172.16.20.1 172.16.20.10
ip dhcp excluded-address 172.16.30.1 172.16.30.10
ip dhcp excluded-address 172.16.50.1 172.16.50.10
ip dhcp excluded-address 172.16.40.1 172.16.40.10
ip dhcp excluded-address 172.16.45.1 172.16.45.10
!
ip dhcp pool WEB-DMZ
network 172.16.10.0 255.255.255.0
update dns
default-router 172.16.10.1
dns-server 192.168.1.1
!
ip dhcp pool APP-TIER
network 172.16.20.0 255.255.255.0
default-router 172.16.20.1
!
ip dhcp pool DATA-TIER
network 172.16.30.0 255.255.255.0
default-router 172.16.30.1
!
ip dhcp pool NFS
network 172.16.40.0 255.255.255.0
default-router 172.16.40.1
!
ip dhcp pool LAN
network 172.16.45.0 255.255.255.0
default-router 172.16.45.1
!
ip dhcp pool MANAGEMENT
network 172.16.50.0 255.255.255.0
default-router 172.16.50.1
Interfaces
interface FastEthernet0/0
description WAN interface
ip address 192.168.1.3 255.255.255.0
ip nat outside
ip virtual-reassembly
duplex auto
speed auto
!
interface FastEthernet0/1
description Transparent LAN interface
no ip address
duplex auto
speed auto
!
interface FastEthernet0/1.5
description Native VLAN interface
encapsulation dot1Q 5 native
ip address 172.16.5.1 255.255.255.0
no cdp enable
!
interface FastEthernet0/1.10
description DMZ VIF
encapsulation dot1Q 10
ip address 172.16.10.1 255.255.255.0
ip access-group 100 in
ip nat inside
ip virtual-reassembly
no cdp enable
!
interface FastEthernet0/1.20
description APP VIF
encapsulation dot1Q 20
ip address 172.16.20.1 255.255.255.0
ip nat inside
ip virtual-reassembly
no cdp enable
!
interface FastEthernet0/1.30
description DATA VIF
encapsulation dot1Q 30
ip address 172.16.30.1 255.255.255.0
ip nat inside
ip virtual-reassembly
no cdp enable
!
interface FastEthernet0/1.40
description NFS VIF
encapsulation dot1Q 40
ip address 172.16.40.1 255.255.255.0
ip nat inside
ip virtual-reassembly
no cdp enable
!
interface FastEthernet0/1.45
description LAN VIF
encapsulation dot1Q 45
ip address 172.16.45.1 255.255.255.0
ip nat inside
ip virtual-reassembly
no cdp enable
!
interface FastEthernet0/1.50
description MGMT VIF
encapsulation dot1Q 50
ip address 172.16.50.1 255.255.255.0
ip nat inside
ip virtual-reassembly
no cdp enable
!
interface ATM0/0/0
no ip address
shutdown
no atm ilmi-keepalive
!
interface FastEthernet1/0
shutdown
!
interface FastEthernet1/1
shutdown
!
IP NAT and DNS
ip dns server
ip nat inside source list 10 interface FastEthernet0/0 overload
ip nat inside source static tcp 172.16.45.14 22 interface FastEthernet0/1.45 22
ip route 0.0.0.0 0.0.0.0 192.168.1.1
!
access-list 10 permit 172.16.40.40
access-list 10 permit 172.16.45.0 0.0.0.255
access-list 10 permit 172.16.10.0 0.0.0.255
dialer-list 1 protocol ip permit
dialer-list 1 protocol ipx permit
no cdp run
I've tried to adapt this example to my setup http://www.cisco.com/c/en/us/support/docs/security/ios-firewall/5143-cbac4.html#diag - to no avail.
This guy had a simple solution that looked like it worked - https://www.youtube.com/watch?v=8WVWoW86Uhw - but couldn't get it to work on my setup.
And then tried this http://www.cisco.com/c/en/us/support/docs/ip/network-address-translation-nat/13773-2.html
It's definitely not for a lack of trying, and troubleshooting things as best I can, but I think I'm not understanding exactly what's happening in my config and what each piece means to get it to work.
Any help would be greatly appreciated.
- Labels:
-
Other Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-05-2016 04:05 AM
You can create an ACL and allow traffic from 192.168.1.0/24 on SSH port and apply it on VTY interfaces , how are you connected to 192.168.1.0 since it is not defined inside? And it will be getting Nated to public IP so you may have to allow that in ACL
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-05-2016 12:37 PM
Hi Junaid, thanks for your answer!
I'm directly connected to 192.168.1.0/24 network via the FE0/0 interface (literally physically connected)
[modem]-------[FastEthernet 0/0 | ROUTER | FastEthernet 0/1.x]-------[FE 0/48 | SWITCH |]
the 192.x network is defined on the OUTSIDE interface Fe0/0:
interface FastEthernet0/0
description WAN interface
ip address 192.168.1.3 255.255.255.0
ip nat outside
ip virtual-reassembly
duplex auto
speed auto
do you have an example of what I can try?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-07-2016 02:46 AM
**Create an ACL
ip access-list extended VTY_ACCESS
10 permit tcp 192.168.1.0 0.0.0.255 any eq 23
20 permit tcp 192.168.1.0 0.0.0.255 any eq 22
**Apply ACL on VTY
line vty 0 4
transport input all
login local
access-class VTY_ACCESS in
exit
***Please rate helpful posts.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2016 04:22 PM
Thanks for your reply Junaid,
From that config it looks like its setting up access to the device (router) itself, which I already have access to via SSH.
What I'm looking for is how to setup the router to expose the internal network (172.16.x.x) to the 192.168.x.x network so I can reach those services.
From my previous diagram the point where these 2 networks meet is the ROUTER, which has an 2 interfaces configured:
fastethernet 0/0 - 192.168.1.3 [external]
fastethernet 0/1 - 172.16.1.2 [internal]
with VLANS on the 172. side [172.16.10/20/30.x] all my interVLAN is working fine and I can reach the internet on any VLAN I add to my access list which gets overloaded on the 0/0 interface...
So here's a scenario, if I'm running a webserver on 172.16.20.80 on port 80 - and I'm sitting on my laptop with IP 192.168.1.34 - How do I configure the ROUTER so my laptop can view this website on 172.16.20.80?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2016 04:44 PM
I think you will need to use conditional nat and route map to resolve this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2016 11:53 PM
Hi Cofee, I think you've put me on the right track!
So I've started working my way through the example on this page:
http://www.ciscozine.com/using-route-maps-for-conditional-nat/
and forgive my ignorance, but I don't understand where the IP 172.16.100.5 comes from in this explanation:
When the client (172.16.0.5) on siteA tries to connect to the server Web (10.0.1.100), the source ip address will be translated in 172.16.100.5
I'm trying to adapt my config to their example
ip nat inside source static 172.16.0.5 172.16.100.5 route-map route-client-serverssh
ip nat inside source static 172.16.0.5 172.16.200.5 route-map route-client-serverweb
My understanding of this is:
"ip nat inside source static <client's ip address> <mapped-to-ip-on-this-mystery-subnet> using route-map route-client-serverssh to figure out destination"
So I think I know where to plug in my 192.16.x.x address (client ip) but don't know what this 172.16.100/200.x IP is?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-18-2016 05:47 AM
You can try the configuration below and see if it works:
permit ip host 192.168.1.34 172.16.0.0 255.255.0.0 log
match ip address client-serverweb
* I am assuming that you will be initiating traffic from your laptop that's sitting on your wan interface and has an ip address 192.168.1.34. So based on this access list whenever the destination address is within 172.16.0.0 block it will trigger the ACL and then it will do an identity NAT, you will be getting translated to the same address.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-21-2016 12:41 AM
Thanks Cofee - super busy at work but I will try to implement this very soon and let you know how I go!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide