- Cisco Community
- Technology and Support
- Networking
- Switching
- Routing with multiple WAN connections
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Routing with multiple WAN connections
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-29-2024 12:19 PM
We have made some change to our network and I can't seem to get the traffic to flow as I need it.
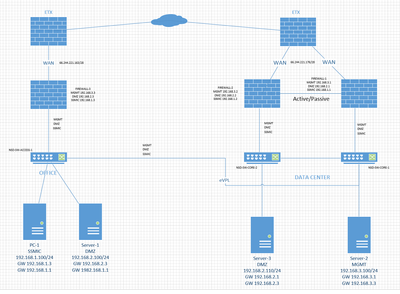
We have two sites - our Data Center and our Office. We connect the two sites using a VPLS.
We are changing to an eVPL connection and at the same time we have added a WAN connection to our Office location. At least for now we need to have the vlans extend accross the two sites. The issue I am having is accessing systems from the Office that in the Data Centre but on a different vlan. I have been looking for some documentation on how to set this up but haven't found anything. Any recommendations would be greatfully accepted.
Here is a basic diagram of what we are trying to accomplish
Thanks
- Labels:
-
LAN Switching
-
WAN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-29-2024 02:09 PM
Hello,
are you using the WAN link or the eVPL ? The ETXs are RADs ? The edge devices are firewalls (which type/brand) ? Post the full running configs of these edge devices...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2024 05:11 AM - edited 01-30-2024 05:22 AM
The WAN connections are just used for outgoing traffic. All traffic between the sites uses the eVPL. The ETXs are RADs but are provided by our ISP and I don't have access to them. The firewalls are Firepower 1140 in the DC and 1120 in the office. The configs from the firewalls are huge. Also, being our security appliances I hesitate to post the configs for everyone to read.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2024 11:22 AM
So I have been doing some testing on this using wireshark. When I try to ping from 192.168.1.100 to 192.168.2.110 sometimes the traffic uses Firewall-1 and sometimes Firewall-3. If it uses Firewall-1 it works. If it uses Firewall-3 it doesn't. I do have a statement on the all the switches ip route 0.0.0.0 0.0.0.0 192.168.1.1 - I am wondering if this is the issue. Definitely seems to be related to routing. Is this something that using EIGRP and modifying path selection would fix?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2024 09:21 PM
Hello
That design does not look correct, you have 3 fws all running the same L3 network and it looks like no visible redundancy for the default-gateway of those networks.
If you keep the interlvan routing just on the DC fws and then used the office Fw/wan connection as only a local internet break out that would work, However any inter vlan traffic will need to traverse the vpls link which is not ideal for hosts in different vlans located at the office site.
Alternatively you could have Office/DC fws become active/active with dual contexts so they both supply fail-over to each other whilst both providing active D/G resiliency, this will provide "local" D/G reach ability whilst resiliency over the vpls in case either FW fails
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2024 06:25 AM
Having the intervlan traffic use the vpls is not an issue. The majority of the traffice not going to the internet is going to cross that link anyway. The majority of the systems in the office are backups for the DC.
As far as having the fws become active/active I don't believe these versions of the firepower fws support that.
Back to the design phase.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2024 09:03 AM - edited 01-31-2024 09:14 AM
Hello,
I understand that you cannot post the full configs, but at least post the relevant parts of the configs that relate to routing, as that seems to be the problem...
EDIT: since the firewalls are not involved, you can post the configs of the three core switches where the eVPL is configured ? All addresses are private anyway...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2024 11:35 AM
Here are the configs. NSD-SW-ACCESS-2 is the office switch. The other two are the DC switches. The IP addresses are different than the original diagram. I removed some of the unnecessary configuration. Let me know if you have any questions.
Thanks for all your help.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide