- Cisco Community
- Technology and Support
- Networking
- Switching
- setup a small private (isolated) network within the current network
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2019 07:40 AM - edited 03-08-2019 04:56 PM
brain freeze.... need help
How can i setup a small network with private ip range within existing network which have public ip range.?
That small network would be on separate switch and would be used to control industrial ovens remotely(over the internet)
As of today web server is in our dmz which can be accessed from outside.
Solved! Go to Solution.
- Labels:
-
LAN Switching
-
Other Switching
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2019 09:50 AM
If the DMZ and the web server are local to your environment (not going over the Internet) you just need to configure the routing for them to communicate but if the server needs to be accessed over the internet than you need NAT.
Here is a link with the example for configuring NAT:
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2019 09:56 PM
if you like to use private IP address as suggeted other post you need to do NAT.
If you like to use Public IP in the same Switch, then extend the DMZ VLAN to new Switch.
So new Devices have Public IP address also.
If possible can you make small network topology of your network, so we get clear picture what devices are in the network and how they connected.
if simple as mentioned other post URL, then that is the bestway for your requirement.
=====Preenayamo Vasudevam=====
***** Rate All Helpful Responses *****
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2019 07:42 AM
You can do with another VLAN configured in the exiting network and extend that VLAN to new Switch.
is this make sense ?
=====Preenayamo Vasudevam=====
***** Rate All Helpful Responses *****
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2019 08:09 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2019 08:14 AM
The private network will not communicate with anything on the Internet unless you configure NAT on your edge router or firewall.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2019 08:54 AM
Devices in the private network just need to communicate on some port with the webserver living on a public ip address in the dmz. Nat between the private network and webserver?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2019 09:50 AM
If the DMZ and the web server are local to your environment (not going over the Internet) you just need to configure the routing for them to communicate but if the server needs to be accessed over the internet than you need NAT.
Here is a link with the example for configuring NAT:
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2019 10:07 AM
The webserver has a public ip open for https from internet.
Devices which will connect with the new switch will get ip addresses from that new switch and will get a gateway in the same private ip range.
If i connect that new switch with existing switch in the network with runs all public subnets, what are my options to make the devices on the new switch communicate with the webserver?
Devices do not need to go to internet. They just need to connect with webserver(locally) on some port to be managed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2019 09:56 PM
if you like to use private IP address as suggeted other post you need to do NAT.
If you like to use Public IP in the same Switch, then extend the DMZ VLAN to new Switch.
So new Devices have Public IP address also.
If possible can you make small network topology of your network, so we get clear picture what devices are in the network and how they connected.
if simple as mentioned other post URL, then that is the bestway for your requirement.
=====Preenayamo Vasudevam=====
***** Rate All Helpful Responses *****
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-06-2019 05:49 AM - edited 01-06-2019 10:57 PM
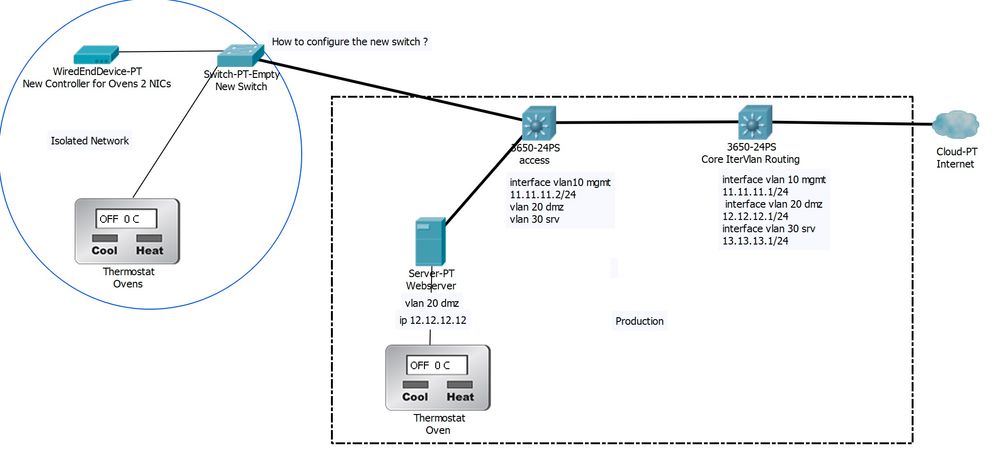
This is the current topology:
- Webserver in dmz is connected to ovens which is accessible from internet to control them i.e temp, start/stop etc...
Required :
- New switch was needed to connect more ovens.
- New controller would be connected for better controls.( not managed by me).
-Keep the Ovens network as isolated as possible from production while web server still be accessible from the internet for remote mgmt.
- Web server can me moved
Hope this makes things clearer...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-05-2019 03:37 AM
Hello Mateensaadatbaig,
Greetings,
Usually the DMZ is a zone that have a middle security level between the Private ( INSIDE Zone) that should have the highest security and the Public (OUTSIDE Zone) that should have the least security!
The idea, that the highest security zone can reach any less security zone while the opposite is not!
Usually we are doing such a job by means of a firewall.
Through that firewall, we are arranging the areas as well as the policies where you can define what host or network can be reached from what host or network, etc.
Maybe I don't fully understand what you are planning to do! so if you will provide us more details including what devices you have in your project so that we can set the hardware limitations or features availability in our account during the designing!
Please, don't forget to rate any helpful responses!
Bst Rgds,
Andrew Khalil
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide