- Cisco Community
- Technology and Support
- Networking
- Switching
- Should the connection between Distribution Layer and Edge Routers be Layer2 or Layer3
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Should the connection between Distribution Layer and Edge Routers be Layer2 or Layer3
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-09-2017 05:56 AM - edited 03-08-2019 11:15 AM
I'm modeling a small collapsed core network, and keep confused about the edge routers (R1/R2) to core/distribution layer (L3S0/L3S1) connection:

- Layer2, using HSRP on the edge routers and HSRP on the collapsed core pair
- Layer3, using OSPF between the edge routers pair and the collapsed core pair
- Is an access layer required ?
- Should it better be Layer2 or Layer 3
- Labels:
-
Other Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-09-2017 06:07 AM
Hi
The recommendation is use layer 3 HSRP between the routers and firewalls and Layer 2 between Multilayer switches to server switch.
My personal point of view, is use static routes between Internet firewalls and Core/Distribution devices, it will not increase the CPU routing process, the firewall can work as Active-Standby.
Now a collapsed model refers to a device who can work how core and distribution switch at the same time, so you will have 2 (core, access) layer instead 3 (core, distribution, access), example:
It shows just a device but you can have high-availability with 2 devices as core/distribution.

>> Marcar como útil o contestado, si la respuesta resolvió la duda, esto ayuda a futuras consultas de otros miembros de la comunidad. <<
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-09-2017 06:19 AM
If the firewall are working as active and standby
you can configure 1 ip on the firewall and it will replicated to the other, so you could use a /29 subnet to interconnect the 4 devices, it is an example:
IP Plan
192.168.10.4 255.255.255.248 - Firewall 1 so it will be replicated to firewall 2.
HSRP Virtual gateway - 192.168.10.1 255.255.255.248
HSRP Active - 192.168.10.2 255.255.255.248
HSRP Active - 192.168.10.3 255.255.255.248
Remember the HSRP Active - Standby must have communication between each other, so you can use a routing protocol like OSPF or EIGRP.
Now the configuration on the routers should be:
Main router
interface Fastethernet0/0
ip address 192.168.10.2 255.255.255.248
standby 10 ip 192.168.10.1
standby 10 priority 105
standby 10 preempt
no shutdown
ip route 0.0.0.0 0.0.0.0 192.168.10.4 name Internet
Backup router
interface FastEthernet0/0
ip address 192.168.10.2 255.255.255.248
standby 10 ip 192.168.10.1
standby 10 preempt
ip route 0.0.0.0 0.0.0.0 192.168.10.4 name Internet
Firewall
Now how the configuration is the same on the firewall, you need to add the return routes on the firewall pointing to the IP .1
example to reach internal networks
route INSIDE 172.16.2.0 255.255.255.0 192.168.10.1
route INSIDE 172.16.3.0 255.255.255.0 192.168.10.1
route OUTSIDE 0.0.0.0 0.0.0.0 <public next hop IP>
Now take in consideration if you are going to use a multilayer switch how collapsed device you can use layer 3 ports or SVI.
>> Marcar como útil o contestado, si la respuesta resolvió la duda, esto ayuda a futuras consultas de otros miembros de la comunidad. <<
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-09-2017 07:00 AM
Thanks for your answer :-) . I edited my post for clarity.
The recommendation is use layer 3 HSRP between the routers and firewalls
What is 'Layer3 HSRP' ? Do you mean 'Layer3 routed ports'+HSRP ?
Also, should I run a double HSRP, ie HSRP on the Edge Routers + HSRP on the collapsed core pair? Isn't that too much of HSRP ? ;-)
On the posted picture is written 'Layer 3 Rounded Port'. What is it? I googgled in vain for that expression. Is it a typo for'Layer 3 routed port' ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-09-2017 07:24 AM
Yes that is correct, you can use layer 3 ports to working along with HSRP to have high availability so the routers will have one virtual HSRP IP, it will be the next hop IP to the internal company networks.
The idea is have a redundancy on these devices. For example for each internal company use HSRP, imagine the attached scenario, if the active device is down, the traffic will not be impacted because the standby device will be the new active device and it has the same virtual IP who is the gateway for the users.
>> Marcar como útil o contestado, si la respuesta resolvió la duda, esto ayuda a futuras consultas de otros miembros de la comunidad. <<
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-09-2017 08:17 AM
Generally speaking you run HSRP for end devices not for interconnections between network devices.
So the core/distro switches should connect to the routers with L3 links not HSRP.
However if the routers were removed and the firewalls connected directly to the switches and the firewalls were a pair then you cannot use L3 links, you need to use a common vlan so the firewalls can see each other.
Note also ASA firewalls do not run HSRP but they do support a VIP.
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-09-2017 08:10 AM
Just to point out that the routers in your design are serving no purpose as far as I can see and I would remove them and connect the firewalls directly to the core/distro switches.
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-09-2017 10:30 AM
Thanks for your inputs !!
Yes, I know the network map makes no sense with ASA+Edge routers. I removed the ASAs from the picture and replaced them with DSL modems for clarity. My question was purely about the Edge Routers/Core Switches Relationship :-)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-14-2017 01:49 AM
Hi !
Thanks to your inputs, and after some more modeling, I'd like to propose a solution:
(collapsed) core to edge routers conection
Question 1: Should the edge routers (R1/R2) to collapsed (core) or distribution layer (L3S0/L3S1) connection better be L2 or L3?
1. Best choice: L3 point-to-point links, using OSPF:
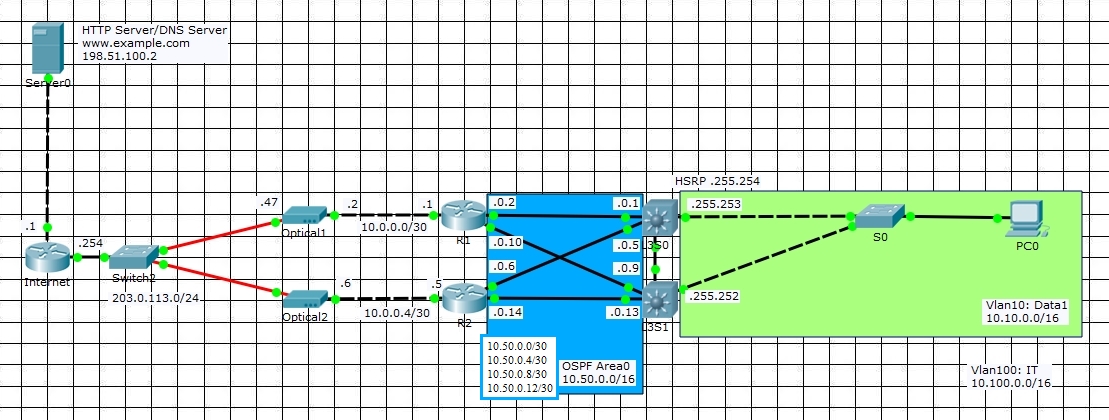
2. Cisco ASA option: in case a pair or Cisco ASA is used, the only solution is to use VIP failover for the ASAs, and HSRP on the (collapsed) core pair:

3. Worst choice: L2 with back-to-back HSRP:

Isn't this double back-to-back HSRP kinda eerie ?
Yes, but there is no other solution if you absolutly have to go the Layer2 road
What are the Pros/Cons of L2 vs L3 solution
- L3 with OSPF: Pros: Fast convergence, easy to troubleshoot, less error-prone. Cons: many IP blocks to carve
- L2 with HSRP: Pros: Easier to design IP-wize. Cons: Slow convergence, harder to troubleshoot, more error-prone
Question2: Should the (collapsed) core to Servers use Layer 2 or Layer3
This is the best I managed to formulate so far. Should I mark this as 'Correct Answer?'
Thanks for any input !!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

