- Cisco Community
- Technology and Support
- Networking
- Switching
- Unable to switch pass a VLAN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-05-2021 06:16 AM - edited 01-08-2021 01:16 AM
Hi guys,
I'm having a really weird situation whereby my netflow traffic just got stuck at my switch vlan 100 when i view using wireshark using the commands below:
monitor session 1 source vlan 100 both
monitor session 1 destination interface g1/0/20
When i monitor the source of vlan 60 both, there are no netflow traffic at all.
So in my C9300 switch, when i check show ip route, i see that i do have routes to reach networks or host that i want to reach, and the NTP is working. However, the netflow traffic doesn't seem to pass over to the external network.
As you can see from the ping test i've done, it seems that traffic sourcing from vlan 100 cannot route to the external network or vlan 60.
Also, i've turned on debugging for IP ICMP but when i ping, there wasn't any debugging logs when i ping with the source of 192.168.1.250 OR vlan 100 (i've turned on logging console debugging and check show logs too). Does this mean that the ping did not even happen and got "dropped" immediately?
When i do a normal ping to 192.168.1.254, there are debugging logs.
Anyone have any steps or idea that i can try for troubleshooting this issue? It was previously working, and it just suddenly stop working (i was informed by a SOC team monitoring the netflow traffic)
Solved! Go to Solution.
- Labels:
-
Catalyst 9000
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-08-2021 03:24 AM
Hello,
have you tried to remove:
ip verify unicast source reachable-via rx
from the Vlan SVIs ? Maybe that is somehow interfering with NetFlow...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-05-2021 07:45 AM
You have routes in Cat 9300, Do you have same route back to Cat 9300 from external FW and Internal FW ?
=====Preenayamo Vasudevam=====
***** Rate All Helpful Responses *****
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-05-2021 07:50 AM
The netflow traffic is suppose to be one-way and its a UDP traffic. Its weird that i am unable to ping the external FW interface with the source from vlan 100.
Also, the i can see that internal FW works perfectly fine as i can see UDP traffic getting allowed. For external firewall, the stakeholder mentioned that they did not touch it since it was deployed and working previously.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-05-2021 08:30 AM
somewhting might have changed if that was working as expected - hence this post is here to identify the issue, we need to look all the config where it dropping.
first routes to start and any ACL
=====Preenayamo Vasudevam=====
***** Rate All Helpful Responses *****
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-05-2021 08:43 AM
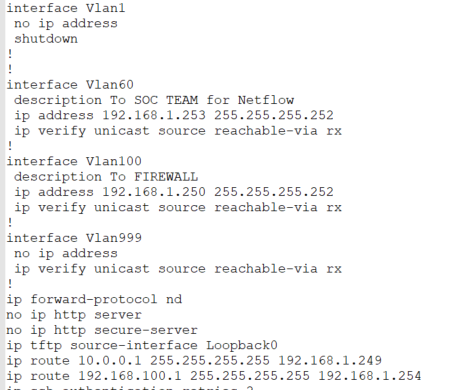
There are only 2 routes on the c9300 switch.
Which is in the picture listed. One to reach the NTP server and another to reach the netflow destination at the external network.
And no ACL at all on all interfaces
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-05-2021 08:48 AM
Hello,
all your IP addresses are /32 host addresses, is that a typo, or for real ? If that is the case, the links are on different subnets. That means you have to change your static routes to point not to the next hop IP address, but the outgoing interface (which causes them to ARP for the next hop).
--> ip route 192.168.100.1 255.255.255.255 outgoing_interface
Also, on the outgoing interfaces, you might need to enable proxy arp.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-05-2021 04:49 PM
Hi Georg,
Haha, thats a typo. It should be /30 instead. Thanks for pointing that out.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-05-2021 09:37 PM
by changing the mask did the solve the issue ?
=====Preenayamo Vasudevam=====
***** Rate All Helpful Responses *****
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-06-2021 07:32 AM
Hi Balaji,
Sorry for the late response. It was a typo in the diagram. the actual configuration is correct.
However, still not working with the /30 mask.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-06-2021 07:56 AM
can we have more information which i was requested before please.
=====Preenayamo Vasudevam=====
***** Rate All Helpful Responses *****
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-06-2021 05:55 PM
Hi balaji,
Please refer to the configurations below:
interface GigabitEthernet1/0/1
switchport trunk native vlan 999
switchport trunk allowed vlan 100
switchport mode trunk
switchport nonegotiate
spanning-tree portfast
spanning-tree bpduguard enable
spanning-tree guard root
interface GigabitEthernet1/1/4
switchport trunk allowed vlan 60
switchport mode trunk
interface Vlan60
description for Netflow
ip address 192.168.1.253 255.255.255.252
ip verify unicast source reachable-via rx
!
interface Vlan100
description To FIREWALL
ip address 192.168.1.250 255.255.255.252
ip verify unicast source reachable-via rx
!
interface Vlan999
no ip address
ip verify unicast source reachable-via rx
switchport nonegotiate
ip route 10.0.0.1 255.255.255.255 192.168.1.249
ip route 192.168.100.1 255.255.255.255 192.168.1.254
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-08-2021 01:19 AM
Hi Balaji,
I've included some screenshots in the initial post.
Please have a look. Let me know what else you will need to help. Thanks in advance!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-08-2021 03:24 AM
Hello,
have you tried to remove:
ip verify unicast source reachable-via rx
from the Vlan SVIs ? Maybe that is somehow interfering with NetFlow...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-08-2021 06:08 AM
Good call Georg. I can try that.
I have tried removing only for vlan 60. But it didnt work. This time let me try removing it from vlan 100.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-08-2021 06:31 AM
Hello,
remove that line from BOTH interfaces at the same time.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide