- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
VLAN membership in a VRF over a trunk
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2017 11:32 AM - edited 03-08-2019 09:47 AM
Struggling w/ VLANs/VRFs in a virtualized environment and am hoping that someone can provide a little guidance. My experience with VRFs is in a true MPLS environment, but VRF-lite is confounding me.
The architecture is pretty straightforward: establishing a DMZ in a virtualized environment. Port is set up in the core switch:
ip vrf DMZ
description DMZ
interface GigabitEthernet1/1/13
description TO FIREWALL
no switchport
no ip address
interface GigabitEthernet1/1/13.19
description DMZ
encapsulation dot1Q 19
ip vrf forwarding DMZ
ip address 172.19.1.1 255.255.255.0
interface Vlan19
ip vrf forwarding DMZ
no ip address
ip route vrf DMZ 0.0.0.0 0.0.0.0 172.19.1.2
To the virtual environment we have a trunk set up with the necessary VLANs:
interface Port-channel50
switchport
switchport mode trunk
switchport trunk allowed vlan 10,19,100-104
end
And while this is probably obvious to most of you by now, virtual machines that are configured on the Vlan19 vSwitch can't access anything in the DMZ vrf environment. What didn't I configure properly - or will this not even work? Simply, can I make a specific VLAN a member of the VRF environment?
Any help would be greatly appreciated.
- Labels:
-
LAN Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2017 11:44 AM
To answer your question yes you put the L3 interface for the vlan into the VRF.
But it's not clear from the rest of your post exactly how it is setup. A quick diagram perhaps ?
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2017 12:02 PM
Jon,
I'm not the world's best diagrammer, so don't laugh. I'm not sure this will even convey the information that is needed.
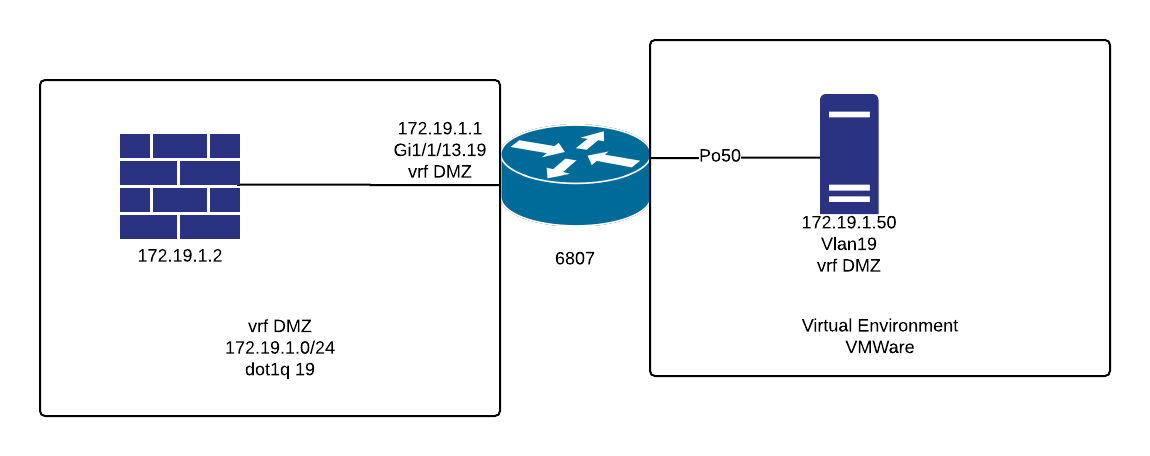
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2017 12:07 PM
Do you want the default gateway of the servers in vlan 19 to be the firewall ie. 172.19.1.2 ?
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2017 12:11 PM
Yes sir. It's just a /24 subnet, 172.19.1.2 is the firewall interface. We can ping from .1 to .2 and vice versa. Nothing from 172.19.1.50 in the virtual environment, and no success pinging .1 or .2 if we set a port to access Vlan19 only.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2017 12:16 PM
You can't have the link between the firewall and the switch as a L3 link if you want the default gateway of the servers to be the firewall.
If that link between the 6800 and the firewall is just for this then you need to simply put the 6800 end into vlan 19. In this case there is no need for a VRF as all traffic from the DMZ servers has to go to the firewall to get anywhere.
If the link is an existing one and in use already or you need to route between other vlans in the same VRF please provide details.
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2017 12:24 PM
Jon,
I'm sorry.. I'm sure I'm not explaining this in enough detail. If we just assign the switchport to be a member of Vlan19, wouldn't servers in the DMZ have the ability to access other Vlans if the gateway was changed? Vlan19 will be part of the global routing policy, and will have routes to all of the other sub-nets. Although unlikely, changing the gateway of Vlan19 from .2 (the firewall) to .1 (the SVI) would allow the machine to access any other resource on the network.
It seems to me that we need a VRF as a best practice, don't we? We have to ensure that there is no inter-vlan routing, and that all traffic goes to the firewall by default. The gateway of last resort in the VRF is set for 172.19.1.2.
Is there a better way to isolate the DMZ traffic and force it through the firewall with no opportunity whatsoever to jump vlans?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2017 12:44 PM
It's probably me who isn't explaining this very well.
You don't have an SVI for vlan 19, the only L3 interface is on the firewall so there is no other gateway to use. The 6800 simply has a route to the DMZ subnet pointing to the firewall and the firewall has routes for the internal subnets pointing back to the switch.
So no need for a VRF. Where you would need a VRF is if you had multiple vlans in the same VRF you wanted to route between on the 6800 which I don't think you do by the sounds of it or if you had multiple VRFs you perhaps wanted to route between.
But as far as I can tell you don't need either of those but if I am misunderstanding what you want let me know.
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2017 12:46 PM
Thanks, Jon.
So if I just configure Vlan 19 as "no ip address" and add a static route to the global table "ip route 172.19.1.0/24 172.19.1.2" that's it? There's no possibility for inter-vlan routing or hopping that I'm not thinking of?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2017 12:49 PM
You simply do not create an SVI on the 6800 for vlan 19.
The route information was wrong, see my last post but in brief I assume you have another connection between the firewall and the switch ?
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2017 12:46 PM
Made a slight mistake in previous answer.
The 6800 would not have a route for the vlan 19 subnet pointing to 172.19.1.2, but it would have a route for the 172.19.1.0/24 subnet pointing to the firewall. I am assuming that there is another connection between the switch and firewall, or if not then the connection in your diagram needs to be a trunk.
Apologies for confusing the issue.
Jon
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
