- Cisco Community
- Technology and Support
- Networking
- Switching
- VLAN Tagging
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-02-2019 08:39 PM - edited 03-08-2019 04:55 PM
Dear Community,
currently I'm trying to separate our internal networks in a couple of VLANs. In this regards we are using one single Layer-3-Switch (Cisco SG 300). The switch itself is connected to an ASA firewall and the ASA to the internet.
In this regards I just would have a question about the VLAN setup on cisco sg 300 switch.
The following steps I already performed:
1. Separating the switch into several VLANs
2. Creation of specific IP-Interfaces (one interface for each VLAN):
=> VLAN 1 => 192.168.1.254
=> VLAN 22 => 10.0.2.254
=> VLAN 33 => 10.0.3.254
...
3. Assigning the specific ports to the specific VLAN
Mode = "Access" and "Untagged"
Port 1 => VLAN 1 (Upstream)
Ports 2-5 => VLAN 22
Ports 6-10 => VLAN 33
In general everything is working now, but my problem is, that the subnetworks/VLAN can communicate to each other. It makes sense for the following two connections, since internet access is required for the connected clients:
VLAN 22 <=> VLAN 1
VLAN 33 <=> VLAN 1
On the other hand site the VLAN 22 <=> VLAN 33 communication is critical and must be limited.
My question is how to change the VLAN settings to ensure that no packages are routed between VLAN 22 <=> VLAN 33?
In this regards I have to point to the fact, that the clients (connected to the SG-300 ports) do not have a separate VLAN-ID / Handling (entry is empty or set to "0"). That means the idea would be that the SG-300 is going to tag every package coming from a specific client automatically. In theory that shouldn't be a problem since single clients, for single VLANs are connected to a single switch port in any case. That means one SG-300 port does never ever has two clients connected from different VLANs.
Furthermore we are just using one single Switch (no switch cascade/trunk).
My idea has been to change the VLAN-Type modes from:
"Access" => "General"
"Untagged" => "Tagged"
and to set the PVID equal to the specific VLAN-ID.
Unfortunately this leads indeed to the restriction of the communication between all VLANs, but I still would need package transfer in some cases (e.g. communication between VLAN 33 and VLAN 1). I already tried to assign multiple VLAN to a single port:
e.g. Upstream Port 1 is member of VLAN 1, 22 and 33. Unfortunately the communication was still prohibited.
I hope my point became clear. :-)
Furthermore I'm interested in single port permissions. Is there a possibility to forbid every communication between VLAN 22 and VLAN 33 instead of a single port? (e.g. for DHCP)?
Greetings,
niLuxx
Solved! Go to Solution.
- Labels:
-
LAN Switching
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-02-2019 10:16 PM
Hi,
to do this you can use access control option.
1- create IPV4-based ACL
2 - create IPV4-based ACE with drop action and relevant source , destination IP addresses which are need to block.
3 - create ACL binding to specific port with newly created ACL as required.
refer,
regards,
*** Pls rate all useful responses ***
Good Luck
Good luck
KB
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2019 05:31 AM
Hello Niluxx,
Greetings,
Actually we are configuring intervlan routing, to make different vlans communicate with each other, but sometimes we need a specific vlan to communicate with another while others will be restricted, or even 1 PC within a vlan communicate with 1 PC in another vlan while all others not! at this case we configure inter-vlan routing in addition to ACL!
when you type on the L3 switch #ip routing, any vlan or any interface has an IP address, will be routed and seen by others, after that we create the ACL!
You configuration is good and this is the normal way of configuring routing with some restriction! otherwise you will need routers to preform the same application using other features like route mapping and filtering etc.
Your best way, is to apply some ACL! it's too much easy to configure and accurate to work!
I usually use it!
Please, don't forget to rate my replies if it have been helpful, and mark as a solution if it's helping to solve your issues, it will be SO NICE from you!
Thanks in advance!
Andrew Khalil
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2019 07:25 AM
Hello Niluxx,
Greetings,
Yes, your configuration steps are enough to configure Inter-vlan routing (there is no check boxes),
and you verify your job is done or not, you should check your IPv4 Routes page, it should look like the following: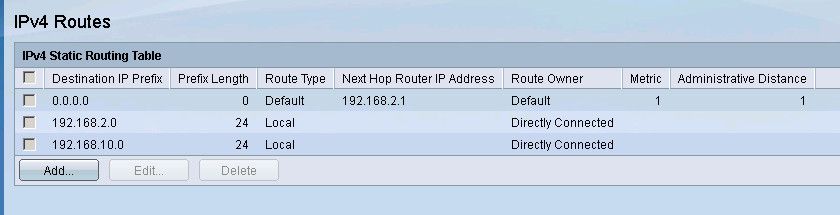
Your all vlan ip address should be Directly connected as shown per the picture!
But if you use the CLI, you can issue the command #show ip route, to verify!
Best of luck,
Please, don't forget to rate the helpful replies, and mark it as a solution!!
Thanks in advance!
Bst Rgds!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2019 12:29 PM
Hello Niluxx,
I am happy to help you,
also, it's nice to get solved and helpful for each helpful reply, this is an appreciation of our effort plus it's helping people who have the same question to track the helpful replies and solution in their search and solve their problems easier as well! So, before I answer the last question)))) please don't forget to mark EACH helpful reply as a HELPFUL and mark it as a solution! and again Thanks in advance!
Regarding your last )))) question, it's a very interesting question! but the answer needs some concentration!
let's start from the part of "Untagged and Access"
Look, usually switch will be connected to host or to another network device (i.e another switch or router or firewall ...) in case of a host, each host should be only in 1 vlan, so imagine we we have in 1 switch (SW1) 3 vlans and 3 hosts, 1 host per each vlan, and another switch (SW2) connected to the first one has the same 3 vlans and 3 hosts, 1 host per each vlan, actually, the ports of the hosts should be ACCESS and Untagged, access is 1 of 2 modes of the switch port, and it's for the hosts connection, the second mode is called TRUNK, and it's for switch to switch (or another network device) connection,
but let's think if 1 host in vlan 10 for example in the SW1 sent a frame to 1 host in the same vlan in SW2, how SW2 knows each frame received from SW1 belongs to which vlan so that it can give it to the required host! at this moment comes the meaning and the use of tagging!
Tagging is to assign a vlan id on each packet, like a mark, to mark each frame belongs to which vlan, in the normal sequence, any host port should be untagged, because any sent data or recieved data on this port will be untagged, the sent is untagged because the PC willl not tag any packet, and when the port will receive an untagged frame the switch will mark it to pass through the tagged port (which is connecting the 2 switches together "the trunk port") and when the tagged port on the another switch will receive this frame, it will know to which vlan it should send it but after removing the tag!
So, simply the host port, should be access and untagged
while the port the connecting the switch with another one, should be trunk and tagged!
Now for PVID, The PVID of a port is the VLAN id that will be assigned to any untagged frames entering the switch on that port (assuming the switch is using port-based VLAN classification). This is a concept that is defined in IEEE 802.1Q.
For example, if you intend to connect a PC or a printer to a port, you would set the port as untagged in VLAN 10 and excluded from all other VLANS. The switch knows to only send VLAN 10 stuff to that port and to remove the VLAN tagging information before sending anything out.
But, what about untagged frames entering the switch from the PC or printer (They’ll be untagged because the PC or printer doesn’t know about VLAN). This is where PVID comes in. PVID tells the switch what to do with those untagged incoming frames. In this example, if the PVID doesn’t match the VLAN id, the PC won’t be able to communicate with anybody because the frames it sends into the switch will end up on the wrong VLAN.
On some switches, if you set a port as untagged on VLAN 10 and excluded from all others, the switch will automatically take care of tagging the untagged incoming frames with the same VLAN id (because what else would you want?) without requiring you to set the PVID. Other switches require you to manually set the PVID. Some of the switches that don’t require you to set the PVID manually will allow you to set the PVID even if you don’t have to.
In Cisco IOS switches you will (probably) never need to set a PVID (although you can) because the Cisco port configuration categories (and other configured parameters) take care of this automatically.
In order to determine your responsibility regarding PVID, you’ll have to consult your switch’s documentation or experiment.
Finally and as a conclusion, Set the ports that are connected to PCs or printers etc.. to Access (in vlan 10 for example) and untagged while ports that are connected to another network device to trunk (for the all allowed vlans to pass to another network device) and tagged!
Usually, and according my experience with cisco, I never use the pvid as configuring access or trunk and untagged or tagged, is enough and the pvid will be done automatically.
But when I work with ZTE for example managed switch, for ports connected to PCs or printers, I should configure these ports to be untagged fo vlan 10 and with pvid 10! while ports that connect to another switch, I configure it to be tagged for vlan 10, 20, 30 and with pvid 1 (the native vlan)!
I hope it's not confusing and crystal clear!
Happy again to help!
Bst Rgds,
Andrew Khalil
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-02-2019 10:16 PM
Hi,
to do this you can use access control option.
1- create IPV4-based ACL
2 - create IPV4-based ACE with drop action and relevant source , destination IP addresses which are need to block.
3 - create ACL binding to specific port with newly created ACL as required.
refer,
regards,
*** Pls rate all useful responses ***
Good Luck
Good luck
KB
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-02-2019 10:23 PM - edited 01-02-2019 10:26 PM
Dear Niluxx,
Greetings,
According to what I understood from your post, that the 2 vlans (22 and 33) are routed by the means of the switch, and as a result clients within these 2 different vlans are communicating, while you want to stop this kind of communication and only keep each vlan communicating with vlan 1!
If so, the solution is so easy, you just need to apply an access-list (Access control list)
and it will enable you to prevent the communication to the entire vlan as you want!
Just let me know, are you configuring the switch using GUI or the command line?
In command line I would configure the following:
ip access-list extended 120
deny ip 10.0.2.0 0.0.0.255 10.0.3.0 0.0.0.255
permit ip 10.0.2.0 0.0.0.255 any
exit
ip access-list extended 130
deny ip 10.0.3.0 0.0.0.255 10.0.2.0 0.0.0.255
permit ip 10.0.3.0 0.0.0.255 any
exit
int vlan 22
ip access-group 120 in
exit
int vlan 33
ip access-group 130 in
exit
if you are using the GUI,
Apply the same policy that I have mentioned in the command line, by using the following guide
Best of luck, and with pleasure to support!
Please rate any helpful replies and mark it as a solution if it's helping you to solve your issues, it will be so nice from you!
Thanks in advance!
Andrew Khalil
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-02-2019 10:53 PM - edited 01-02-2019 10:54 PM
Hello all,
thanks for the fast reply. I think that makes sense and I assume this information will be quite useful to me. :-) Thanks a lot. Nevertheless I wonder about the role of VLANs in my network, since I would have a security basing on ACL and not a security basing on sub-networks that are separated by VLAN.
Wouldn't it be the correct procedure to:
1. Setting up different VLANs (nothing can communicate to each other)
2. Setting up inter-VLAN-routes for specific VLANs (e.g. VLAN 33 => VLAN 1)
3. Limit the communication with the help of ACL (only specific ports are permitted)
Best greeting and thanks once more,
niLuxx
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-02-2019 11:24 PM
Dear Niluxx,
Happy to help you!
Actually, access-lists are so much useful, it can allow or disallow even a specific host within a vlan to communicate with another host in another vlan! not only limited to that but also you can control what protocol can be used this communication!
At any case, if you will need anymore support, you are welcome all the time!
Please, don't forget to rate my reply if it was helpful for you, also MARK it as a solution if it's helping to solve your issue! I will be so nice from you!
Bst Rgds,
Andrew Khalil
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2019 04:08 AM
Hello Andrew,
thanks for you answer. I will definitely take a closer look to the ACL and ACE topic. Nevertheless, isn't there an error in my config if VLAN can communicate to each other? How I would have to change the settings to restrict the communication and enable Inter-VLAN-Routing?
Greetings,
niLuxx
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2019 05:31 AM
Hello Niluxx,
Greetings,
Actually we are configuring intervlan routing, to make different vlans communicate with each other, but sometimes we need a specific vlan to communicate with another while others will be restricted, or even 1 PC within a vlan communicate with 1 PC in another vlan while all others not! at this case we configure inter-vlan routing in addition to ACL!
when you type on the L3 switch #ip routing, any vlan or any interface has an IP address, will be routed and seen by others, after that we create the ACL!
You configuration is good and this is the normal way of configuring routing with some restriction! otherwise you will need routers to preform the same application using other features like route mapping and filtering etc.
Your best way, is to apply some ACL! it's too much easy to configure and accurate to work!
I usually use it!
Please, don't forget to rate my replies if it have been helpful, and mark as a solution if it's helping to solve your issues, it will be SO NICE from you!
Thanks in advance!
Andrew Khalil
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2019 06:01 AM - edited 01-04-2019 06:12 AM
Hello Andrew,
thanks for your message. That is exactly the way I want to use it. We have about 5 VLAN and some will communicate to each other (over pre-defined ports), other VLAN will not communicate.
That means the steps are required:
1. Set up VLAN
2. Set up Inter-VLAN Routing
3. Set up static ipv4 routes
3. Restrict specific communication via ACL and ACE
But I'm still not sure if step one was correctly done by me. As I said I did the following config:
1. I have created all VLANs and assigned the specific port with:
Mode = Access/Untagged
2. I have created IPv4 Interface, one for each VLAN
3. I have set up specific IPv4-Route
Does that mean, that I already configured VLAN (step 1) and Inter-VLAN Routing (step 2/3) correctly? That means Inter-VLAN option is only enabled with the creation of a IPv4 Interface for the specific VLAN-group? No "Inter-vlan enable"-check box or something?
Than it would make sense to continue with ACL and ACE. Nevertheless I wonder if I have to use the PVID. Or is that more a "nice to have" than a requirement for the usage of VLANs.
Best greetings,
niLuxx
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2019 07:25 AM
Hello Niluxx,
Greetings,
Yes, your configuration steps are enough to configure Inter-vlan routing (there is no check boxes),
and you verify your job is done or not, you should check your IPv4 Routes page, it should look like the following:
Your all vlan ip address should be Directly connected as shown per the picture!
But if you use the CLI, you can issue the command #show ip route, to verify!
Best of luck,
Please, don't forget to rate the helpful replies, and mark it as a solution!!
Thanks in advance!
Bst Rgds!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2019 09:15 AM
Hello Andrew,
thanks again for your answer. I really appreciate your effort and the topic becomes clearer and clearer to me. The settings are correctly set (i checked few seconds ago) and everything should be fine.
In this regards one last question (afterwards you get your "Solved" for sure :-) ). If VLANs are working with this setup, what is the use case for using PVID and General mode instead of "Untagged" and Access?
Best regards,
niLuxx
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2019 12:29 PM
Hello Niluxx,
I am happy to help you,
also, it's nice to get solved and helpful for each helpful reply, this is an appreciation of our effort plus it's helping people who have the same question to track the helpful replies and solution in their search and solve their problems easier as well! So, before I answer the last question)))) please don't forget to mark EACH helpful reply as a HELPFUL and mark it as a solution! and again Thanks in advance!
Regarding your last )))) question, it's a very interesting question! but the answer needs some concentration!
let's start from the part of "Untagged and Access"
Look, usually switch will be connected to host or to another network device (i.e another switch or router or firewall ...) in case of a host, each host should be only in 1 vlan, so imagine we we have in 1 switch (SW1) 3 vlans and 3 hosts, 1 host per each vlan, and another switch (SW2) connected to the first one has the same 3 vlans and 3 hosts, 1 host per each vlan, actually, the ports of the hosts should be ACCESS and Untagged, access is 1 of 2 modes of the switch port, and it's for the hosts connection, the second mode is called TRUNK, and it's for switch to switch (or another network device) connection,
but let's think if 1 host in vlan 10 for example in the SW1 sent a frame to 1 host in the same vlan in SW2, how SW2 knows each frame received from SW1 belongs to which vlan so that it can give it to the required host! at this moment comes the meaning and the use of tagging!
Tagging is to assign a vlan id on each packet, like a mark, to mark each frame belongs to which vlan, in the normal sequence, any host port should be untagged, because any sent data or recieved data on this port will be untagged, the sent is untagged because the PC willl not tag any packet, and when the port will receive an untagged frame the switch will mark it to pass through the tagged port (which is connecting the 2 switches together "the trunk port") and when the tagged port on the another switch will receive this frame, it will know to which vlan it should send it but after removing the tag!
So, simply the host port, should be access and untagged
while the port the connecting the switch with another one, should be trunk and tagged!
Now for PVID, The PVID of a port is the VLAN id that will be assigned to any untagged frames entering the switch on that port (assuming the switch is using port-based VLAN classification). This is a concept that is defined in IEEE 802.1Q.
For example, if you intend to connect a PC or a printer to a port, you would set the port as untagged in VLAN 10 and excluded from all other VLANS. The switch knows to only send VLAN 10 stuff to that port and to remove the VLAN tagging information before sending anything out.
But, what about untagged frames entering the switch from the PC or printer (They’ll be untagged because the PC or printer doesn’t know about VLAN). This is where PVID comes in. PVID tells the switch what to do with those untagged incoming frames. In this example, if the PVID doesn’t match the VLAN id, the PC won’t be able to communicate with anybody because the frames it sends into the switch will end up on the wrong VLAN.
On some switches, if you set a port as untagged on VLAN 10 and excluded from all others, the switch will automatically take care of tagging the untagged incoming frames with the same VLAN id (because what else would you want?) without requiring you to set the PVID. Other switches require you to manually set the PVID. Some of the switches that don’t require you to set the PVID manually will allow you to set the PVID even if you don’t have to.
In Cisco IOS switches you will (probably) never need to set a PVID (although you can) because the Cisco port configuration categories (and other configured parameters) take care of this automatically.
In order to determine your responsibility regarding PVID, you’ll have to consult your switch’s documentation or experiment.
Finally and as a conclusion, Set the ports that are connected to PCs or printers etc.. to Access (in vlan 10 for example) and untagged while ports that are connected to another network device to trunk (for the all allowed vlans to pass to another network device) and tagged!
Usually, and according my experience with cisco, I never use the pvid as configuring access or trunk and untagged or tagged, is enough and the pvid will be done automatically.
But when I work with ZTE for example managed switch, for ports connected to PCs or printers, I should configure these ports to be untagged fo vlan 10 and with pvid 10! while ports that connect to another switch, I configure it to be tagged for vlan 10, 20, 30 and with pvid 1 (the native vlan)!
I hope it's not confusing and crystal clear!
Happy again to help!
Bst Rgds,
Andrew Khalil
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-06-2019 09:05 PM - edited 01-06-2019 09:05 PM
Hello Andrew,
Thanks for your message and the detailed explanation. I will now mark your answers as "helpful" and "Solution" for sure :-)
Greetings,
niLuxx
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide


