- Cisco Community
- Technology and Support
- Networking
- Switching
- VPN routing
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-13-2013 04:55 AM - edited 03-07-2019 11:03 AM
Sorry in advance if I'm not asking this in the right area. Just point me to where I should post it if this is not the right area.
I have 3 Cisco ASA 5510's in my company's future network configuration, and in addition to being firewalls, they're also acting as routers for my internal networks. I have EIGRP set up on all 3, and they're configured to allow static and connected routes amongst themselves.
Below is a general idea of my company's network design/layout. Yes, I know HP switches are listed. I'm working on getting Cisco replacements.
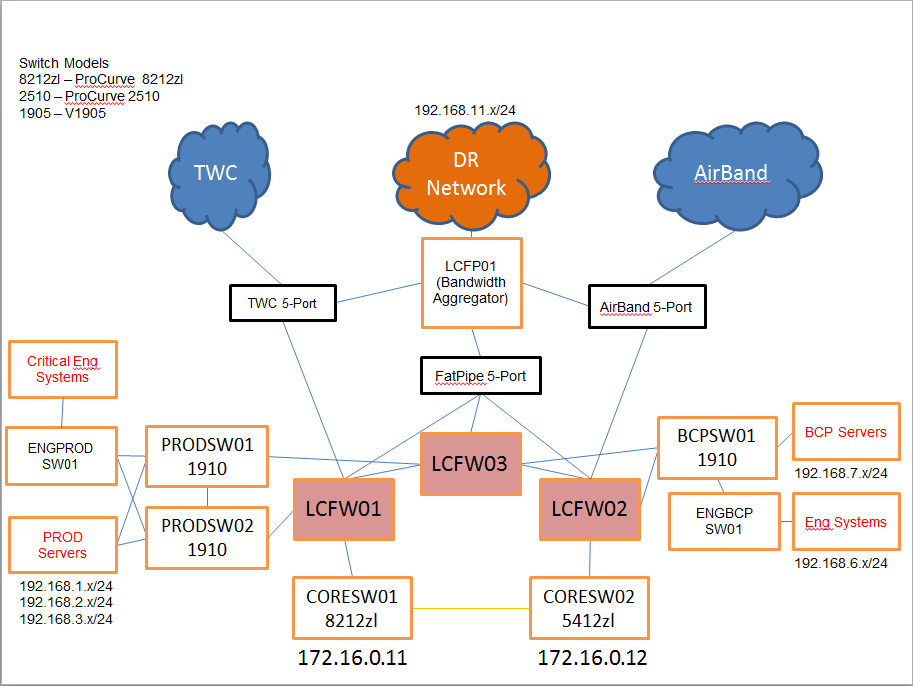
Currently, LCFP01 (a bandwidth aggregator from FatPipe Networks, Inc.) sends all VPN traffic to LCFW03. I don't yet have the right licenses for LCFW01 and LCFW02 to support VPN clustering, so I had put static routes on LCFW01 and LCFW02 to point to LCFW03, the problem I'm running in to now is that those static routes are shared to LCFW03, and LCFW03 believes that it should send the traffic to either LCFW01 or LCFW02. How can I fix this, short of having the correct license to do VPN clustering?
Solved! Go to Solution.
- Labels:
-
Other Switching
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-13-2013 05:33 AM
Hi,
Why don't you put static route to VPN subnet just on LCFW03 instead of LCFW01 and LCFW02? Then redistribute it to LCFW01/LCFW02 as you are already running EIGRP between them.
Hope it will help.
Best regards,
Abzal
Abzal
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-13-2013 05:33 AM
Hi,
Why don't you put static route to VPN subnet just on LCFW03 instead of LCFW01 and LCFW02? Then redistribute it to LCFW01/LCFW02 as you are already running EIGRP between them.
Hope it will help.
Best regards,
Abzal
Abzal
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-13-2013 05:57 AM
Thanks. This gave me the idea to check my company's current firewall for how the routing entry existed, and determined that this is a system-generated static entry. Since I'm already set up for EIGRP sharing static and connected networks on the ASAs, and I'm allowing traffic from all internal networks to pass through (different issue, quite the pain to set up when you're learning the device as you go), I don't think I'll have any problems.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

