- Cisco Community
- Technology and Support
- Security
- VPN
- AnyConnect - Issue accessing Network
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
AnyConnect - Issue accessing Network
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-12-2021 12:39 PM
Hello all,
Very new here and with ASA's, so bare with me.
I followed some videos, and got to the point where I get a successful AnyConnect VPN Tunnel however I cannot ping anything on the network.
The local network is 10.10.10.0/24 and the AnyConnect VPN DHCP is: 10.10.30.0/24
When Connected, I do see I am getting a 10.10.30.XXX Address from the VPN DHCP Pool, however I am assuming my issue is between the VPN Subnet (10.10.30.0/24) and the Local Subnet (10.10.10.0/24)
When I am using the AnyConnect App on my laptop, I see route details for my local network so I am not sure really why I cant ping anything on 10.10.10.XXX
Any help would be appreciated.
- Labels:
-
Routing Protocols
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-12-2021 12:58 PM - edited 10-12-2021 12:58 PM
You need split tunnel and NAT checks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-12-2021 12:58 PM - edited 10-12-2021 01:05 PM
You probably need a NAT exemption rule, to ensure traffic is not unintentially translated.
Example:
object network RAVPN
subnet 10.10.30.0 255.255.255.0
object network LAN
subnet 10.10.10.0 255.255.255.0
nat (INSIDE,OUTSIDE) source static LAN LAN destination static RAVPN RAVPN no-proxy-arp
Create another NAT exemption rule for the other network 10.10.11.0/24 that is a secured route in your split tunnel ACL if required.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-13-2021 06:21 AM
I ran the commands you mentioned:
object network RAVPN
subnet 10.10.30.0 255.255.255.0
object network LAN
subnet 10.10.10.0 255.255.255.0
nat (INSIDE,OUTSIDE) source static LAN LAN destination static RAVPN RAVPN no-proxy-arp
object network RAVPN
subnet 10.10.30.0 255.255.255.0
object network LAN
subnet 10.10.11.0 255.255.255.0
nat (INSIDE,OUTSIDE) source static LAN LAN destination static RAVPN RAVPN no-proxy-arp
However I am not sure what you mean by "that is a secured route in your split tunnel ACL if required."
From my Remote VPN PC: 10.10.30.6 I am still not able to ping the PC at my office of: 10.10.10.200
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-13-2021 06:34 AM
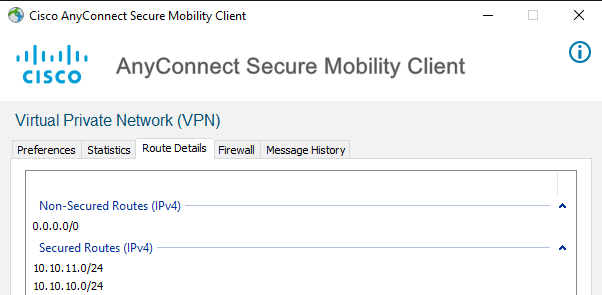
@dsm600rr have a look at your screenshot, it states the 2 networks that are referred to as secured routes.
You've used the same object name (LAN) for both networks (10.10.10.0/24 and 10.10.11.0/24) so if you copied and pasted in the order above you've only got 1 NAT exemption rule for the 10.10.11.0/24 network. So yes you'd not be able to ping 10.10.10.200 as you don't have the NAT exemption rule for that network.
I just provided an example of what you could do, assuming you'd modify to fit your environment.
If you just want to copy and paste:-
object network RAVPN
subnet 10.10.30.0 255.255.255.0
object network LAN-1
subnet 10.10.10.0 255.255.255.0
object network LAN-2
subnet 10.10.11.0 255.255.255.0
nat (INSIDE,OUTSIDE) source static LAN-1 LAN-1 destination static RAVPN RAVPN no-proxy-arp
nat (INSIDE,OUTSIDE) source static LAN-2 LAN-2 destination static RAVPN RAVPN no-proxy-arp
I assume you've got an inside interface called INSIDE and an outside interface called OUTSIDE, you may need to amend accordingly.
Regardless this is assuming that NAT is your issue, if you still have a problem run packet-tracer from the CLI to simulate traffic and provide the output for review.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide